When Data Breaches Reveal the Real Issues

Earlier this week, it was reported that sensitive customer information from several major U.S. banks, including JPMorgan Chase, Citigroup, and Morgan Stanley, was at risk. The cyberattack targeted mortgage technology provider SitusAMC. The leaked content reportedly included accounting documents, legal documents, and, in some cases, financial information related to customers. While the full extent of the incident is still under investigation, it has exposed a deeper issue: the security of modern financial infrastructure depends on the weakest link among the service providers it connects to.
However, what is more concerning than the data breach itself is the universality of this pattern. Systems built for convenience, integration, and automation continue to expand, while privacy protections remain inconsistent and often optional. The result is an unprecedented acceleration in the flow of data, yet a lack of sufficiently robust measures to protect it.
A Wake-Up Call: Privacy is a Hygiene Habit, Not a Feature
Shortly after the news broke, Ethereum co-founder Vitalik Buterin publicly commented:
“Privacy is not a feature; it is a hygiene habit.”
This is not just a reaction—it reflects a cultural shift happening in the Web3 space. For years, privacy has been viewed as a switch or product setting. Users could choose to enable it, install tools, or manually modify wallet behavior. But this model assumes that privacy should be an enhancement rather than a fundamental feature. Buterin's framework upends this expectation: privacy should operate silently, automatically, and by default.
His comment resonates because it reflects an emerging truth: we are moving toward a world where digital ownership has real economic weight. In this world, privacy can no longer be an optional configuration but must become a structural element.
Privacy Protection in Web3: What Problems Does It Aim to Solve?
The design intent of blockchain is transparency. Every transaction, every balance, every flow of funds is visible and verifiable. This makes decentralized systems predictable and trustworthy. However, over time, this transparency can also expose user behavior, address relationships, and financial identities.
The privacy tracks in Web3 exist to resolve this contradiction. They do not aim to eliminate transparency entirely but rather to achieve… selective visibility—where users, protocols, or institutions can disclose necessary information only when needed.
In short, privacy infrastructure aims to answer the following questions:
- How can transactions be verified without exposing the counterparty?
- How do smart contracts operate on encrypted data?
- How can users verify compliance without disclosing confidential information?
- How can institutions use blockchain without exposing their operational models?
As regulatory expectations continue to evolve and the pace of adoption accelerates, privacy is transitioning from a niche feature to a necessary component of scalable digital infrastructure.
Sub-industries within the Privacy Ecosystem
Although the privacy space is often categorized as a single entity, it is actually more diverse than it appears. Today, it can be broadly divided into four emerging layers:
Private Transactions
These protocols enable users to send assets without exposing transaction history or wallet associations. Unlike early mixers, new methods introduce more compliance-friendly proof systems rather than complete anonymity.
A notable example here is privacy pools, which do not hide funds in an indistinguishable pool but allow users to cryptographically prove that their assets are not linked to illicit sources, thereby protecting privacy while maintaining auditability.
Confidential Computing
This technology plays a more fundamental role here. Such protocols do not simply obscure transaction destinations but support encrypted computation—smart contracts can process private data without revealing it to validators.
A leading project in this category is Zama, which focuses on fully homomorphic encryption (FHE). Its goal is simple yet profound: to make the user experience of private smart contracts as seamless as public smart contracts while maintaining compatibility with existing blockchain infrastructure.
Privacy-Preserving Identity
As more users transition from anonymous wallets to on-chain identities and credentials, privacy becomes crucial. Selective disclosure frameworks allow users to prove their qualifications—such as age, nationality, or asset ownership—without disclosing unnecessary personal information.
This category intersects with decentralized identity (DID) frameworks and may become increasingly important for compliance-driven applications like tokenized assets, institutional DeFi, and on-chain credit systems.
Regulated Privacy Infrastructure
Finally, a new category of systems is emerging—these systems are designed from the ground up to align with legal frameworks. Such systems no longer assume that privacy and compliance are at odds but instead seek to unify the two. Vitalik's philosophy is most fully realized here: privacy is a fundamental principle, and transparency is only manifested when necessary.
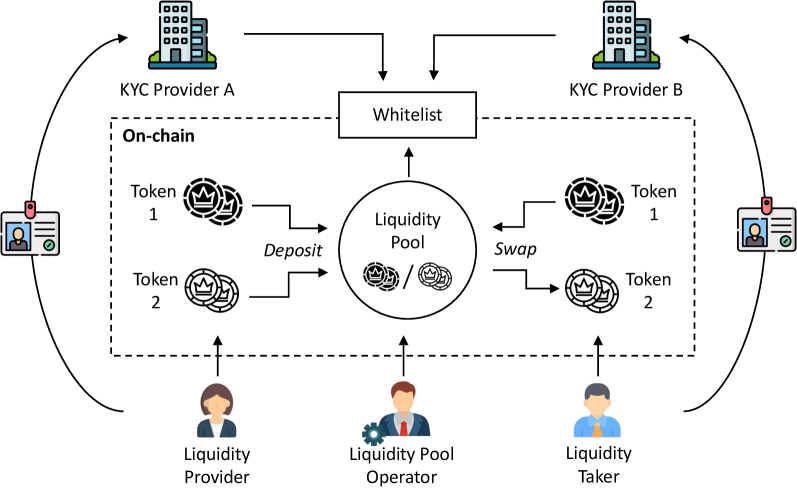
Privacy Leaders Define the Next Phase
As the privacy tech stack matures, some projects have evolved from experimental stages to reference points for on-chain privacy development.
One of the most talked-about examples today is Privacy Pools, built on Ethereum, which serves as an upgraded version of early privacy models. It introduces a new mechanism that allows users to prove their compliance when necessary while protecting transaction privacy. It does not rely on a single, indiscriminate anonymity set but uses cryptographic proofs to classify transaction sources, enabling users to demonstrate that they do not belong to prohibited groups. This design sits between complete anonymity and total transparency, aiming not to evade visibility but to align privacy with regulatory expectations. For this reason, Privacy Pools are frequently mentioned in discussions about "regulated privacy"—a concept that is becoming increasingly significant as institutions enter the Web3 era.
Another important project in this field is Zama, which focuses on fully homomorphic encryption (FHE). While Privacy Pools look at privacy protection at the transaction level, Zama pushes this concept deeper—into the computational layer. With FHE, smart contracts can execute logic directly on encrypted data without decryption, meaning that validators do not need access to the underlying information to verify the correctness of execution. This is fundamentally different from traditional blockchain models, where visibility and verification are inseparable. Zama's work has garnered widespread attention as it provides a pathway for private lending, private voting, crypto financial tools, and enterprise applications with high confidentiality requirements. The project is still actively developing, and its technology is gradually being tested by developers exploring privacy-protecting applications on existing blockchains.

In addition to the two aforementioned solutions, there are several emerging identity-centric protocols that build zero-knowledge verification frameworks, allowing users to selectively disclose information. Users can prove their qualifications, residency, or asset thresholds without revealing unnecessary metadata. These tools are still in their early stages, but they signify an important development direction: privacy in Web3 is no longer limited to transaction protection but extends to how users… exist on-chain.
While the privacy ecosystem has yet to see absolute winners, these projects showcase the trajectory of development in the field. Privacy is shifting from isolated tools to embedded architectures, from niche applications to infrastructure integration. Perhaps most importantly, it is transitioning from a defensive posture (protecting users from data breaches) to a constructive posture, giving rise to many new applications that would not be possible without cryptographic computation and selective disclosure.
As more builders, institutions, and regulators engage in this space, the focus of discussions is gradually shifting. Privacy is no longer seen as an obstacle to compliance or adoption but is becoming a necessary foundational component for responsibly expanding digital ownership.
The Future of Privacy-Based Infrastructure
What we are seeing now is not a set of privacy "tools" but the embryonic form of privacy-native architecture. The narrative is gradually shifting. Privacy is no longer about hiding but about enabling secure participation. It is not a stopgap measure or a niche feature but a fundamental necessity for building a healthy digital economy.
Perhaps the greatest insight we can draw from this bank data breach incident and Vitalik's comments is that privacy breaches rarely stem from the technologies users fear but rather from the systems users trust.
If Web3 is to fulfill its promise of ownership, autonomy, and open systems, then privacy must evolve from a preference to a standard.
Because the future of digital finance depends not just on transparency—
But on balancing what must be public with what should remain confidential.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




