Author: Aki Wu on Blockchain
On October 14, 2025, the Federal Court in Brooklyn, New York unsealed an indictment revealing that the U.S. Department of Justice recently conducted the largest cryptocurrency seizure operation in history, confiscating approximately 127,000 bitcoins worth over $15 billion. The seized bitcoin assets originated from the fraudulent funds of the Cambodian "Prince Group," whose mastermind is known as the "King of Pig Butchering," Chen Zhi. This founder of the Cambodian Prince Group is accused of using forced labor to carry out cryptocurrency investment fraud, commonly known as "pig butchering" scams, earning illegal profits of up to tens of millions of dollars daily. Currently, this massive bitcoin fund is held by the U.S. government. This article will outline the details behind this transnational cryptocurrency enforcement saga from the perspectives of the indictment background, asset sources, and law enforcement efforts.
The Fraud Empire Beneath a Golden Exterior
Chen Zhi is the founder and chairman of the Cambodian "Prince Holding Group," which claims to operate real estate, finance, and other businesses in over 30 countries, but is actually accused of secretly developing into one of Southeast Asia's largest transnational criminal organizations. According to information disclosed by the U.S. Department of Justice and the Treasury Department, Chen Zhi and others have operated at least 10 fraud industrial parks across Cambodia since 2015, luring global victims into false cryptocurrency investments using the notoriously infamous "pig butchering" tactics. U.S. prosecutors claim that Chen Zhi is the mastermind behind this "cyber fraud empire," not only condoning violence against employees and bribing foreign officials for protection but also allowing the group to lavishly spend the proceeds of their fraud, including purchasing yachts, private jets, and even Picasso paintings auctioned in New York.
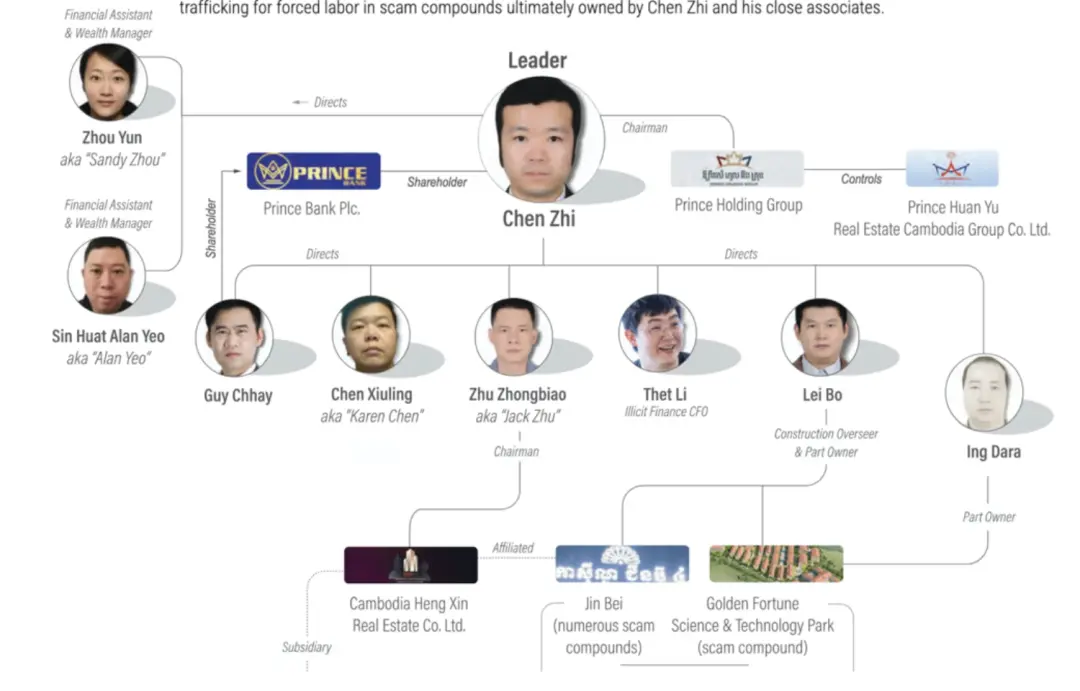
Currently, Chen Zhi himself remains at large, and the U.S. has issued a wanted and sanctions notice against him. His dual nationality of British and Cambodian, along with his deep political and business connections, adds uncertainty to the subsequent extradition process. Such a vast fraud empire naturally requires a systematic money laundering operation.
Therefore, OFAC has implemented comprehensive sanctions against 146 targets, including the Prince Group's transnational criminal organization, to combat the entire profit chain. Among them, the Huione Group, controlled by Chen Zhi and his criminal gang, is recognized as a core link in the Prince Group's main money laundering activities, encompassing HuionePay, a Telegram intermediary market, and more.
According to the U.S. Treasury Department, at least $4 billion in illicit funds were laundered through the Huione network between August 2021 and January 2025, including virtual assets from North Korean-related cyber theft, cryptocurrency investment fraud, and other cyber crimes. In the simultaneous sanctions announcement against the Prince Group's transnational criminal organization, the Treasury emphasized the complete severance of the Huione Group's connections to the U.S. financial system. Regulated financial institutions are now prohibited from directly or on behalf of the Huione Group opening or maintaining agency accounts and must take reasonable measures to avoid processing transactions involving agency accounts of U.S. foreign banking institutions related to the Huione Group to prevent indirect access to the U.S. financial system.

In response, OKX CEO Star stated that the Huione Group has caused serious adverse effects in the cryptocurrency asset field. Given its potential risks, OKX has implemented strict AML control measures for transactions involving this group. Any cryptocurrency deposit or withdrawal transactions related to Huione will undergo compliance investigations. Based on the investigation results, OKX may take measures such as freezing funds or terminating account services.
Source of Assets: Scam Proceeds and Bitcoin Mining
Where did the astonishing figure of 127,000 bitcoins (approximately $15 billion) come from? According to the U.S. Department of Justice's indictment, these funds are the proceeds and tools of Chen Zhi's fraud and money laundering schemes, previously stored in non-custodial cryptocurrency wallets, with him personally holding the private keys. The massive funds obtained from victims needed to be meticulously laundered to evade regulatory scrutiny.
The indictment reveals that Chen Zhi and his accomplices invested the proceeds of their scams into their controlled cryptocurrency mining operations to "wash" out new bitcoins free of criminal taint. In the seemingly legitimate mining process, the original dirty money was converted into newly mined "clean" bitcoin assets, attempting to sever the connection between the funds and the crime. This money laundering strategy allowed the mining operations under the Prince Group to continuously produce bitcoins, becoming one of the important channels for concealing illicit funds.


The indictment specifically names a mining enterprise related to Chen Zhi's money laundering scheme, the "Lubian Mining Pool." Lubian was once a globally renowned bitcoin mining pool headquartered in China, extending its operations to Iran, controlling about 6% of the global bitcoin hash rate at its peak. As part of Chen Zhi's money laundering network, the Lubian Mining Pool helped convert scam funds into vast amounts of bitcoin. However, a bizarre "theft" incident at the end of 2020 embroiled Lubian in mystery. In late December 2020, Lubian reported a hacking attack, resulting in a large amount of bitcoin being stolen. On-chain data shows that 127,426 bitcoins were transferred from Lubian in December 2020, valued at approximately $3.5 billion at the time. The sheer volume of BTC stolen made this incident one of the "largest bitcoin thefts in history."
Shortly after the incident, Lubian vanished from the scene, abruptly shutting down its mining pool operations in February 2021, while the stolen over 120,000 BTC remained untraceable for a long time. On-chain analysis indicates that the stolen 127,426 bitcoins were transferred to a cluster of major wallet addresses, leaving it uncertain whether external hackers stole Chen Zhi's dirty money or if Chen Zhi orchestrated the transfer of the illicit funds out of Lubian. Nevertheless, this valuable batch of bitcoins subsequently went silent on the blockchain, seemingly evaporating. It wasn't until years later that their whereabouts were uncovered.
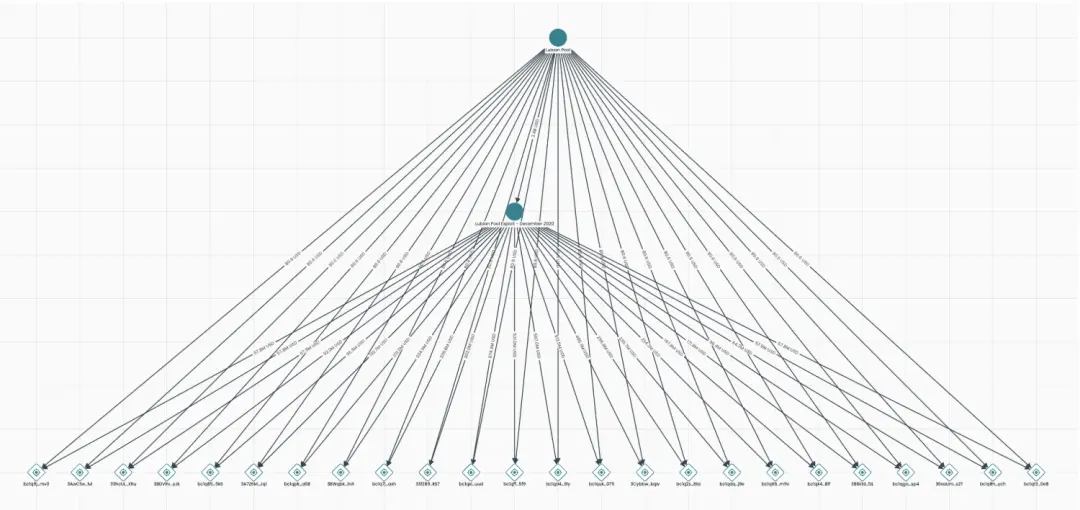
The stolen over 120,000 bitcoins remained static for more than three years, with no significant signs of movement on-chain. On-chain analysis shows that from the time of the theft at the end of 2020 until mid-2024, these BTC stayed in dozens of wallets controlled by hackers, until July 2024, when approximately 127,000 BTC underwent a large-scale concentrated transfer. Since these addresses had already been registered in the community, on-chain intelligence platforms like Arkham quickly identified that these accumulating bitcoins were indeed from the 2020 Lubian mining pool theft. The timing of the transition from dormant to active is particularly intriguing, coinciding with the gradual tightening of the net by transnational law enforcement agencies.
When the U.S. Department of Justice filed a civil forfeiture lawsuit in October 2025, the documents listed 25 bitcoin addresses, indicating that these were the locations where the involved BTC had previously been stored. These addresses matched exactly with the hacker addresses from the Lubian mining pool theft, meaning that U.S. officials identified these 127,000 BTC as the proceeds laundered by Chen Zhi and his accomplices through Lubian, stemming from the same batch of funds that flowed out during the 2020 fake "theft" incident. The lawsuit further pointed out that the private keys for these BTC were originally held by Chen Zhi himself but are now under the supervision of the U.S. government. This implies that the bitcoin accumulation in July was likely conducted by the U.S. government.
Could U.S. Core Technology Simply Be a Brutal Crack?
Due to the early promotion of anonymous transactions in bitcoin cases, the public gradually interpreted bitcoin's "pseudonymity" as strong anonymity, leading to the illusion that bitcoin is easier to launder. In reality, the public and transparent nature of the blockchain ledger provides law enforcement with an unprecedented "view of fund flows." Investigators can use specialized on-chain analysis tools to link scattered transaction addresses into a network, identifying which wallets belong to the same entity and which fund flows exhibit abnormal patterns. For instance, in this case, Arkham had already tagged the wallet addresses of the Lubian mining pool early on. When the massive BTC was stolen and subsequently moved, the analysis system immediately established a connection between the new addresses and the Lubian tags, thereby pinpointing the direction of the stolen bitcoin. The immutable records on the blockchain ensure that even if fraudsters attempt to transfer assets years later, they cannot escape the watchful eyes of trackers.
However, obtaining on-chain addresses does not equate to controlling the assets; the more critical factor is the control of the private keys. Currently, there is no accurate information on how the U.S. government specifically obtained these private keys. According to Arkham's investigation, the Lubian mining pool did not use sufficiently secure random algorithms for wallet private key generation during its operations, and its key generation algorithm had vulnerabilities that could be brute-forced. However, Cobo co-founder Shen Yu stated that law enforcement agencies did not obtain the private keys through brute force or hacking but rather discovered that these private keys had randomization flaws during their generation. Preliminary statistics indicate that over 220,000 addresses were affected by this vulnerability, and a complete list has been made public.
The private keys of these wallets were generated by a flawed pseudo-random number generator (PRNG). Due to the use of fixed offsets and patterns, the predictability of the private keys increased. Users continue to transfer funds to related addresses, indicating that the risk from the vulnerability has not been completely eliminated. U.S. law enforcement and cybersecurity experts speculate that they may also possess similar technologies or clues. However, it is also possible that the U.S. government obtained the mnemonic phrases or signing rights through social engineering, evidence collection, or by infiltrating the fraud group to gradually control the private keys. Regardless, even though Chen Zhi himself remains at large, the "digital gold" that this fraud group prided itself on has already been captured.

Implications for Us and Regulation
Once untouchable fraud lords have now lost their hoarded digital gold; what was once seen as a money laundering tool has now turned into a tool for recovering stolen funds. The incident of "Cambodian Pig Butchering King’s Bitcoin Seized" leaves profound insights for both the industry and regulators. The security of cryptocurrency assets relies on the strength of cryptography; any technical oversight can be exploited by hackers or law enforcement, determining the ultimate ownership of the assets. If readers use wallets that automatically generate private keys, such as imtoken or trust wallet, your wallet may be at risk of being cracked. For this reason, more and more traditional judicial forces are beginning to adopt on-chain tracking and cryptographic cracking technologies, making the fantasy of criminals using encryption technology to evade legal sanctions increasingly untenable.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




