Bitcoin has once again broken its historical high, approaching $99,000, closing in on the $100,000 mark. Looking back at historical data, scams and phishing activities in the Web3 space have been rampant during bull markets, with total losses exceeding $350 million. Analysis shows that hackers primarily target the Ethereum network, with stablecoins being the main target. Based on historical trading and phishing data, we conducted an in-depth study of attack methods, target selection, and success rates.
Crypto Security Ecosystem Map
We have categorized the crypto security ecosystem projects for 2024. In the field of smart contract auditing, established players include Halborn, Quantstamp, and OpenZeppelin. Smart contract vulnerabilities remain one of the main attack vectors in the crypto space, and projects providing comprehensive code reviews and security assessment services each have their strengths.
In the DeFi security monitoring section, there are specialized tools like DeFiSafety and Assure DeFi, which focus on real-time threat detection and prevention for decentralized finance protocols. Notably, the emergence of AI-driven security solutions is worth mentioning.
Recently, meme trading has been extremely popular, and security check tools like Rugcheck and Honeypot.is can help traders identify potential issues in advance.
USDT is the Most Stolen Asset
According to bitsCrunch data, attacks based on Ethereum account for about 75% of all attack events, with USDT being the most attacked asset, with thefts amounting to $112 million, averaging about $4.7 million per attack. The second most affected asset is ETH, with losses of approximately $66.6 million, followed by DAI, with losses of $42.2 million.

It is noteworthy that lower market cap tokens also experience a high volume of attacks, indicating that attackers are on the lookout for less secure assets to steal. The largest incident was a complex fraud attack that occurred on August 1, 2023, resulting in a loss of $20.1 million.
Polygon is the Second Most Targeted Chain by Attackers
While Ethereum dominates all phishing events, accounting for 80% of phishing transaction volume, theft activities have also been observed on other blockchains. Polygon has become the second most targeted chain, accounting for about 18% of transaction volume. Often, theft activities are closely related to on-chain TVL and daily active users, with attackers making judgments based on liquidity and user activity.
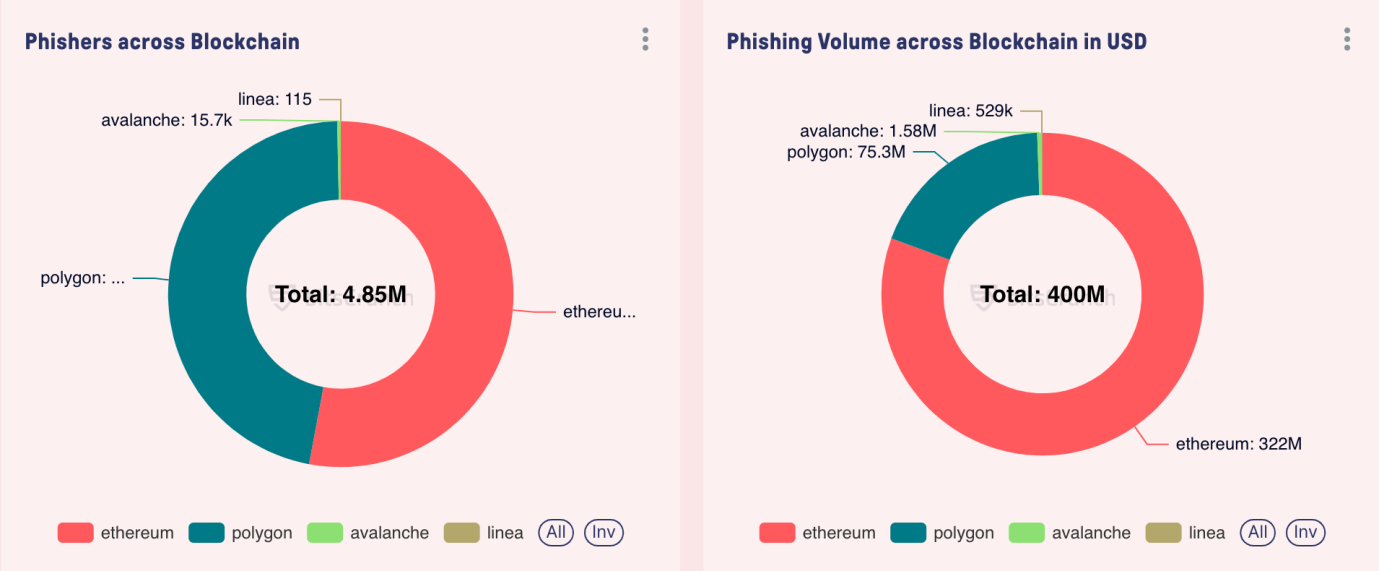
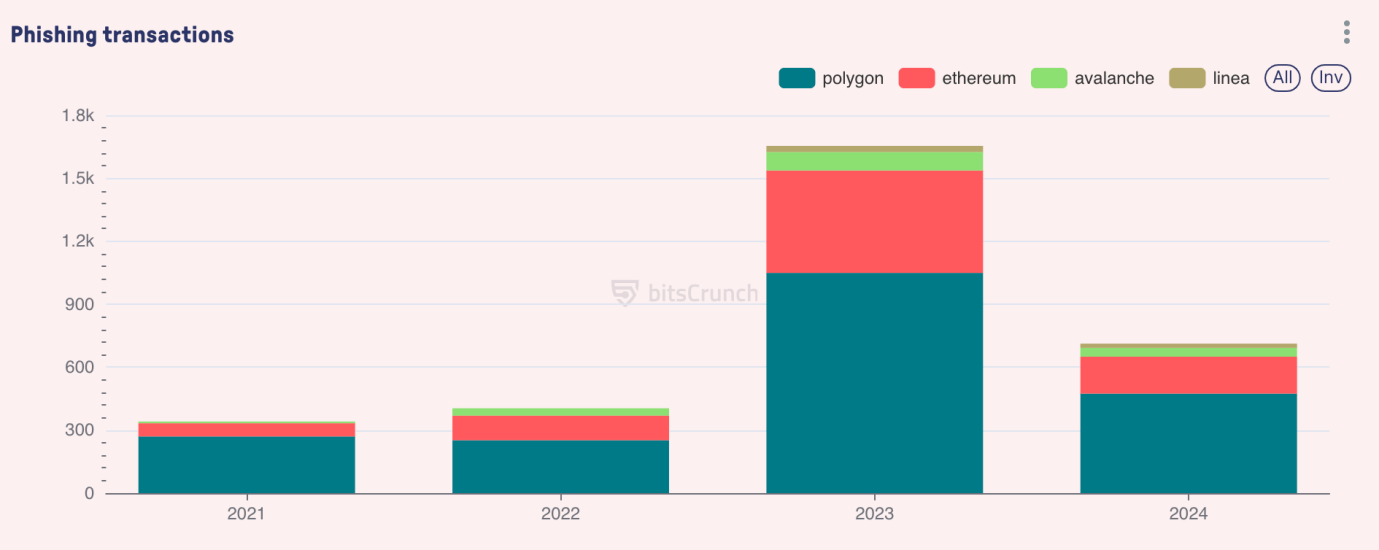
Time Analysis and Attack Evolution
Attack frequency and scale exhibit different patterns. According to bitsCrunch data, 2023 was the year with the highest concentration of high-value attacks, with multiple incidents valued over $5 million. At the same time, the complexity of attacks has gradually evolved from simple direct transfers to more complex approval-based attacks. The average time between major attacks (over $1 million) is about 12 days, primarily concentrated around significant market events and new protocol releases.
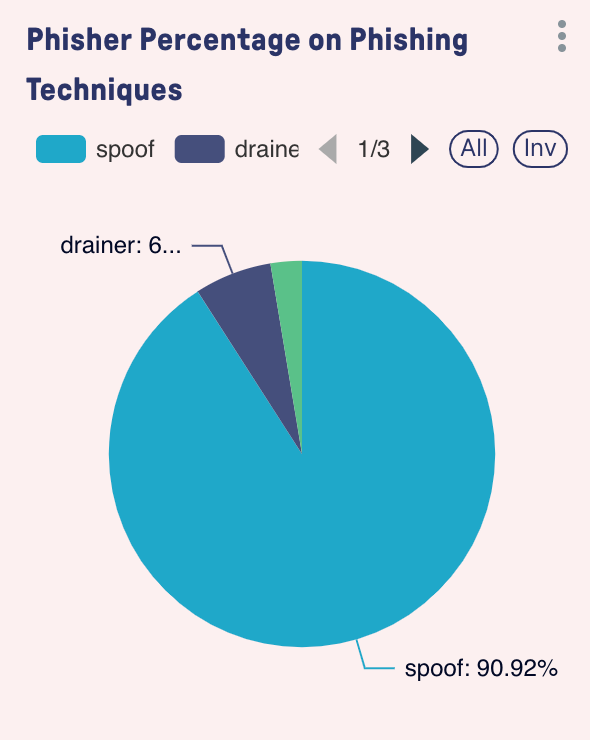
Types of Phishing Attacks
Token Transfer Attacks
Token transfer is the most direct attack method. Attackers manipulate users into transferring their tokens directly to accounts controlled by the attackers. According to bitsCrunch data, these types of attacks often have a very high single-transaction value, leveraging user trust, fake pages, and scam tactics to persuade victims to voluntarily initiate token transfers.
These attacks typically follow this pattern: establishing trust by creating similar domain names that completely mimic certain well-known websites, while creating a sense of urgency during user interactions and providing seemingly reasonable token transfer instructions. Our analysis shows that the average success rate of these direct token transfer attacks is 62%.
Approval Phishing
Approval phishing primarily exploits the smart contract interaction mechanism and is a technically more complex attack method. In this approach, attackers trick users into providing transaction approvals, thereby granting them unlimited spending rights over specific tokens. Unlike direct transfers, approval phishing creates long-term vulnerabilities, allowing attackers to gradually deplete funds.
Fake Token Addresses
Address poisoning is a comprehensive multi-faceted attack strategy where attackers create transactions using tokens with the same name as legitimate tokens but different addresses. These attacks exploit users' negligence in checking addresses to gain profits.
Zero-Cost NFT Purchases
Zero-cost purchase phishing specifically targets the digital art and collectibles market within the NFT ecosystem. Attackers manipulate users into signing transactions, significantly reducing the price or even selling their high-value NFTs for free.
During our research, we identified 22 significant zero-cost NFT purchase phishing incidents, with an average loss of $378,000 per incident. These attacks exploit the inherent transaction signature processes of the NFT market.
Distribution of Stolen Wallets
The data in this chart reveals the distribution pattern of stolen wallets across different transaction price ranges. We found a clear inverse relationship between transaction value and the number of affected wallets— as the price increases, the number of affected wallets gradually decreases.
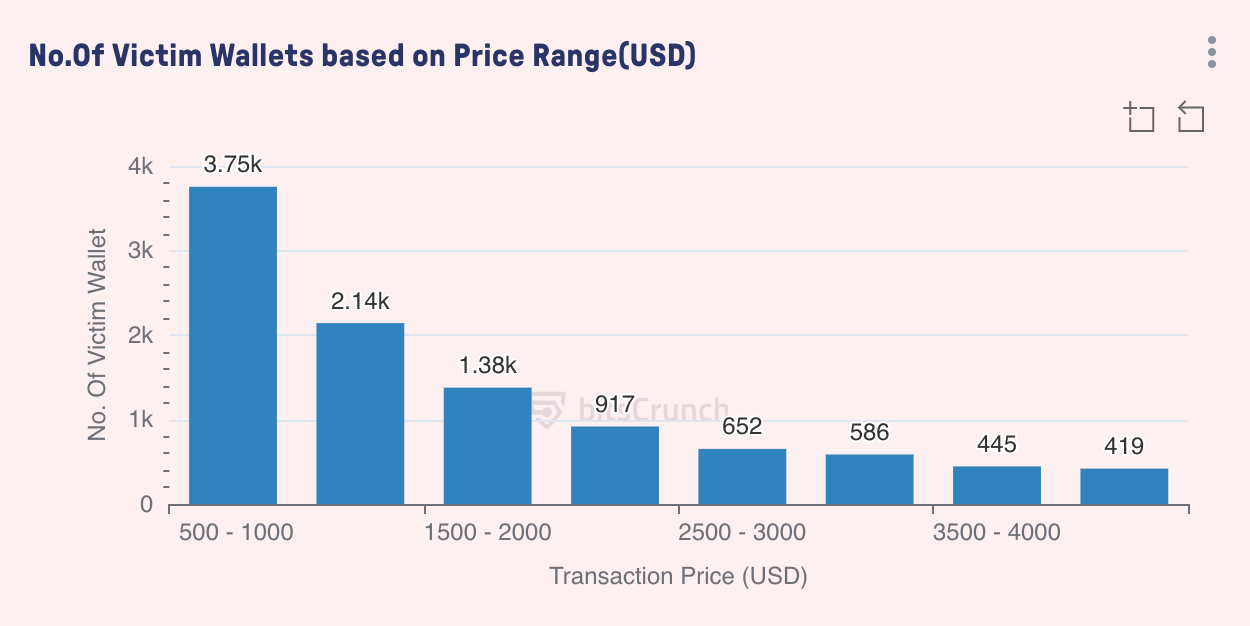
The number of affected wallets for transactions between $500 and $1,000 is the highest, with about 3,750 wallets, accounting for over one-third. Victims of smaller transactions often do not pay attention to details. The number of wallets for transactions between $1,000 and $1,500 drops to 2,140. Transactions over $3,000 account for only 13.5% of the total affected. This indicates that the larger the amount, the stronger the security measures, or victims consider more carefully when dealing with larger sums.
By analyzing the data, we reveal the complex and evolving attack methods within the cryptocurrency ecosystem. As the bull market arrives, the frequency of complex attacks will increase, and average losses will also grow, significantly impacting the economy of projects and investors. Therefore, not only do blockchain networks need to strengthen security measures, but we must also be more vigilant during transactions to prevent phishing incidents.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




