Case Summary
On the evening of February 21, 2025, Beijing time, the Bybit exchange suffered an APT attack, where a forged "blind signature" bypassed the multi-signature mechanism, resulting in the theft of nearly $1.5 billion in assets from the cold wallet. As of 8 AM on the 22nd (Beijing time), the stolen assets were distributed across 51 addresses.
Bit Jungle, as a professional tracing company in the industry, reveals the panoramic details of the hacker attack through public data.
Revelation 1: Hacker Attack Method
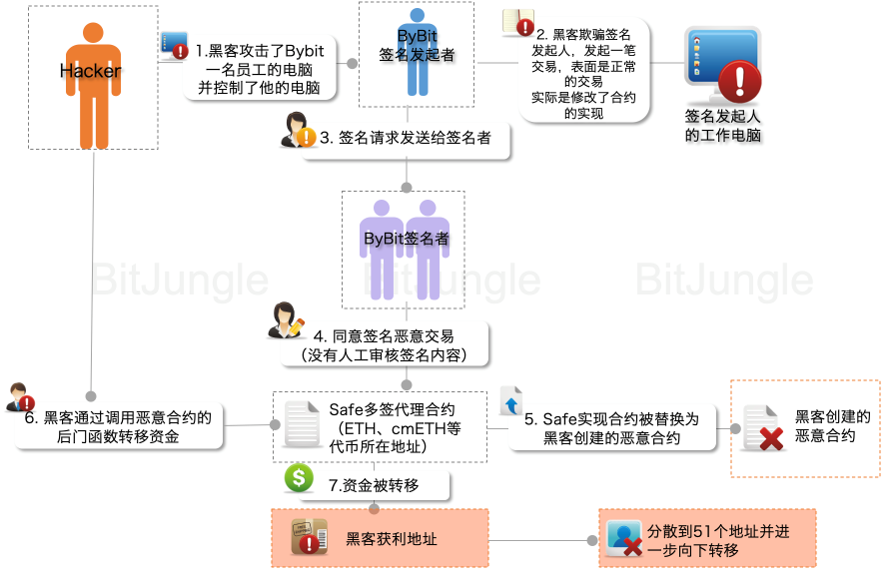
The hacker gained access to Bybit employees' computers through an APT attack.
The hacker lurked for a long time, observing the process of Bybit's coin transfers.
The hacker deployed a malicious Safe contract: 0xbdd077f651ebe7f7b3ce16fe5f2b025be2969516
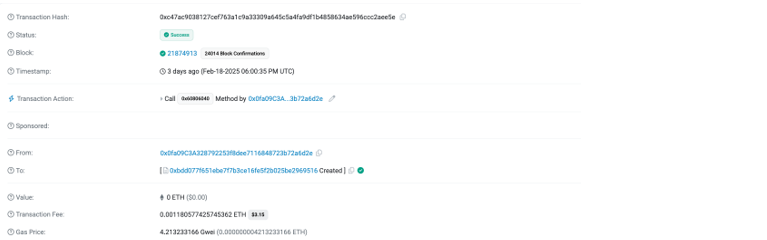
- The hacker forged Safe front-end transaction prompts, deceiving Bybit employees into multi-signing, replacing the safe implementation contract with a malicious contract.
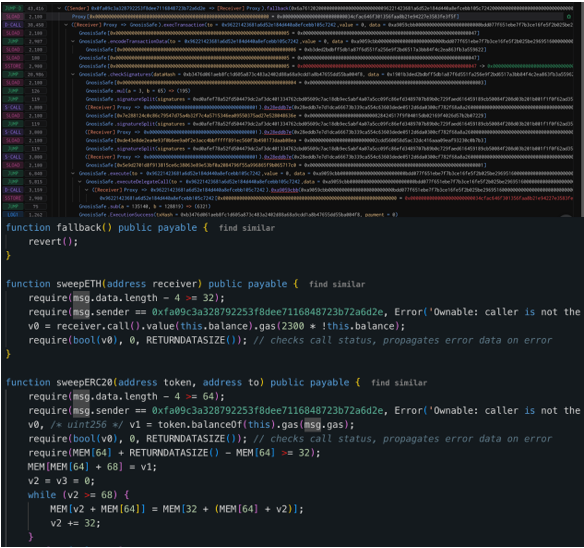
- The hacker transferred the cold wallet assets through the malicious contract.
Revelation 2: Fund Transfer and Attacker Profile
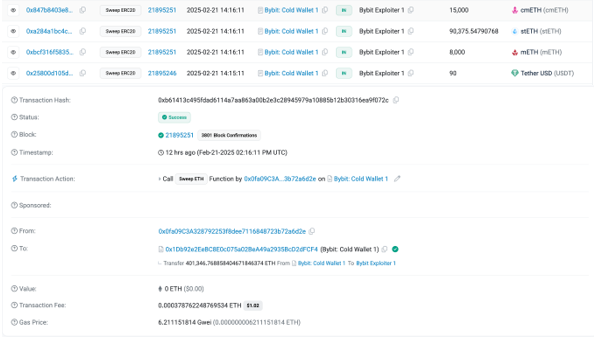
As of 8 AM on the 22nd (Beijing time), the stolen assets were distributed across 51 addresses (the yellow addresses in the image).

At the same time, according to the latest information, the stolen funds from Bybit and the initial hacker address from Phemex have now been mixed together and transferred to the same address. This address has been in use since November 2024 and has executed multiple exchanges and cross-chain transactions, confirming it is also linked to North Korean hackers.
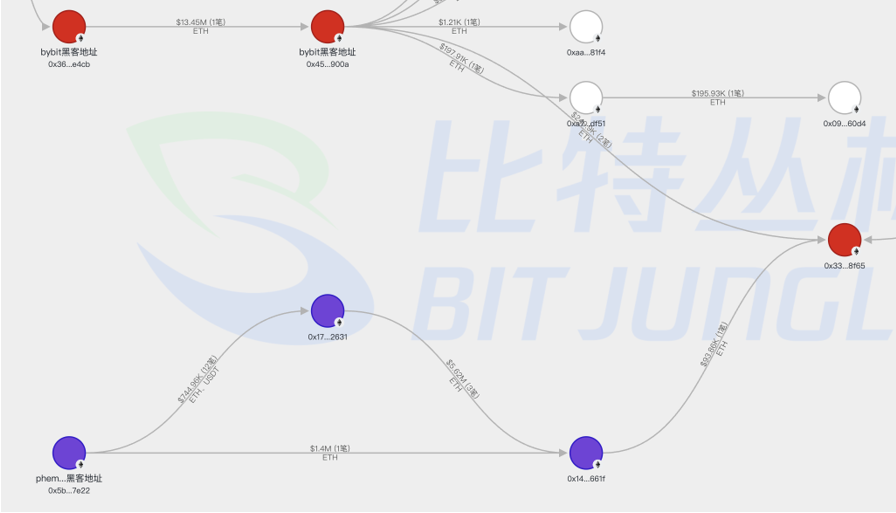
Revelation 3: Potential Financial Secondary Risks
The hacker's sell-off or market panic could trigger a run on users, potentially leading to a surge in withdrawals at Bybit, putting pressure on the capital chain, necessitating urgent measures to stabilize confidence.
As a highly volatile asset, ETH's price is significantly influenced by market sentiment, supply and demand relationships, and macroeconomic factors. This theft incident may lead to ETH price fluctuations, exacerbating losses.
Revelation 4: Preventive Measures
Train employees to enhance their defenses against advanced phishing and social engineering, reducing the introduction of cybersecurity risks internally.
Ensure network and device isolation, with dedicated machines for specific purposes. Important machines or those related to finance should be separated from regular office or personal computers to reduce the attack surface.
Diversify asset storage across multiple cold wallets to minimize the impact of a single point of theft and enhance overall security.
Establish a professional security team and collaborate with Web3 security companies like Bit Jungle to combat hackers together.
Purchase insurance to mitigate losses from security incidents.
Revelation 5: The Security Mechanism of Safe Wallet Multi-Signature Remains Unbroken
Safe (formerly Gnosis Safe) is a widely used multi-signature solution in the industry, whose security relies on the multi-signature and the immutability of smart contract logic.
This attack indicates that the hacker did not break the multi-signature mechanism of Safe or exploit any code vulnerabilities, but rather obtained sufficient signing authority through phishing methods.
Revelation 6: What Bit Jungle Can Do
Uncover the truth and restore the complete intrusion path of the hacker, identifying other hidden security risks.
Bit Jungle has established connections with more than a dozen large exchanges and organizations. Through the Zhong Kui system, it can automatically freeze stolen assets, helping users recover losses as quickly as possible.
Utilize professional technology and extensive experience to quickly locate and assist law enforcement in capturing suspects.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




