Original source: Beosin
On the evening of February 21, 2025, the cryptocurrency trading platform Bybit suffered a massive hacker attack, with over 400,000 ETH and stETH, valued at more than $1.5 billion, transferred to unknown addresses. This incident not only shocked the entire cryptocurrency industry but also sparked profound reflections on anti-money laundering (AML) and the security of decentralized finance platforms.
Today, Beosin Trace detected that the Infini project also suffered an attack, with estimated losses of $50 million, and the incident is currently under investigation. The Infini hacker has exchanged 49.5 million DAI for approximately 17,700 ETH and transferred it to the new address 0xfcc8a…6e49.
In the Bybit incident, as the hacker laundered money through cross-chain exchange platforms and DeFi protocols, how to effectively track and intercept these illegal funds became the focus of industry attention.

Bybit Incident Review: Hacker Attack and Money Laundering Behavior
On the evening of February 21, Beijing time, the Bybit platform was hacked, and the attackers successfully transferred over $1.5 billion worth of ETH and stETH. Subsequently, the hackers began to exchange the stolen assets for other cryptocurrencies (such as BTC) through cross-chain exchange platforms and DeFi protocols like Chainflip, THORChain, LiFi, DLN, and eXch, attempting to cover their tracks through complex fund flow paths.
Although Bybit's official team quickly took action after the incident, collaborating with multiple parties to freeze part of the stolen funds (totaling $42.89 million), the speed of the hackers' fund transfers was extremely fast, and laundering was conducted through multiple addresses and cross-chain protocols, posing significant challenges for tracking and interception. As of February 24, 2025, BeosinTrace tracked that the hackers were still continuously transferring assets, with funds flowing to OKX DEX and Thorchain:Router and other cross-chain exchange protocols.
The Dilemma of Anti-Money Laundering in the Crypto Industry
Hackers utilize the liquidity of cross-chain exchange platforms and DeFi protocols to disperse funds across multiple addresses and blockchain networks, making traditional blacklist mechanisms and simple fund tracking tools inadequate. Here are the main challenges currently faced in the field of anti-money laundering:
1. Complexity of Cross-Chain Transfers
Hackers transfer stolen assets to other blockchain networks through cross-chain exchange platforms (such as THORChain, Chainflip, etc.), increasing the difficulty of fund tracking. The anonymity and decentralized nature of cross-chain technology make the flow paths of funds more obscure, making it difficult for traditional anti-money laundering tools to cover multi-chain environments.
2. Address Dispersion and Rapid Changes
Hackers use a large number of new addresses for fund transfers, and traditional blacklist mechanisms cannot be updated in time, resulting in some funds successfully escaping monitoring. Additionally, hackers can automatically generate new addresses in bulk through scripts, further complicating tracking.
3. Anonymity of DeFi Protocols
The anonymity and decentralized nature of DeFi platforms allow hackers to easily utilize these protocols for fund transfers. For example, hackers can exchange funds through decentralized exchanges (DEX) for other cryptocurrencies and disperse them across multiple addresses, making it difficult for compliance personnel to distinguish between normal and illegal transactions.
4. Abuse of Non-KYC Exchanges
According to The Block, the non-KYC centralized exchange eXch was accused of assisting hackers in laundering money during the Bybit incident. Although eXch denied this accusation, its ETH trading volume saw an abnormal surge after the incident, skyrocketing from the usual 800 ETH to 20,000 ETH within 24 hours. The eXch team admitted that "a small portion of the funds from the Bybit hacker attack eventually entered our address," but claimed that this transfer was "an isolated case." This incident highlights the lack of anti-money laundering measures at non-KYC exchanges.
How to Build a Firewall for Decentralized Platforms
In the face of increasingly complex hacker attacks and money laundering behaviors, DeFi platforms need more robust tools to identify and intercept risky funds. Tools like KYT (Know Your Transaction), specifically designed for the blockchain industry, can help platforms effectively address challenges similar to those in the Bybit incident. Here are several key measures to build a firewall for DeFi platforms:
1. Automated Risk Fund Identification and Tracking
In the Bybit incident, hackers typically used cross-chain exchange platforms and DeFi protocols for fund transfers, and these platforms' liquidity pools often contain a large amount of normal users' funds. If all related platforms are marked as risky, compliance personnel will face a large number of false positives, which will interfere with normal anti-money laundering work. KYT tools can automatically identify the source of funds for these addresses and mark them as high risk, helping platforms freeze related assets in a timely manner. For example, Beosin KYT can track fund flows in real-time through smart algorithms and on-chain data analysis, identifying addresses and transactions related to hackers, ensuring that risky funds cannot escape monitoring.
2. Accurate Identification of Risk Funds in Cross-Chain and DeFi Transactions
Hackers utilize the liquidity pools of cross-chain exchange platforms and DeFi protocols for fund transfers, making it difficult for compliance personnel to distinguish between normal and illegal transactions. Traditional anti-money laundering tools often fail to accurately identify risk funds in these complex transactions. KYT tools can precisely identify risk funds in cross-chain and DeFi transactions without misclassifying normal funds in liquidity pools as risks. For instance, in the Bybit incident, hackers used THORChain and OKX DEX for fund transfers. Beosin KYT can automatically penetrate the previous sources of funds in these protocols, identifying transactions related to hackers without interfering with normal users' funds. 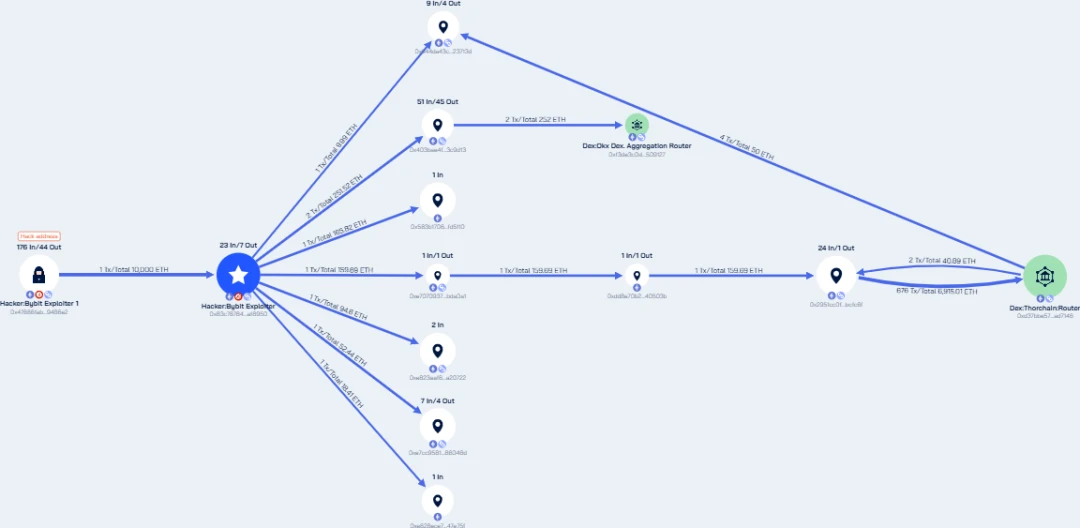
Screenshot of Beosin KYT product
3. Marking and Monitoring High-Risk Exchanges and Addresses
In the Bybit incident, hackers transferred funds through multiple addresses and cross-chain protocols, and traditional blacklist mechanisms could not be updated in time, resulting in some funds successfully escaping monitoring. Beosin KYT has already marked some high-risk exchanges and addresses based on the trading patterns of this incident. By monitoring these high-risk addresses in real-time, platforms can quickly take action to freeze related assets and prevent hackers from further transferring funds.
4. Collaborative Defense: Sharing Risk Address Information
The fund transfer paths of hackers often involve multiple platforms and protocols, making it difficult for a single platform's anti-money laundering measures to cope with complex fund flows. There is a call for on-chain decentralized protocol projects and off-chain exchange platforms to share hacker-related address information through a proprietary internal channel. This collaborative defense mechanism can help platforms timely block hackers' fund flows and freeze related assets. For example, when BeosinTrace tracks that the hacker address 0xfc926659dd8808f6e3e0a8d61b20b871f3fa6465 begins to transfer assets, related platforms can immediately freeze the funds at that address to prevent further movement.
In Conclusion
These security incidents remind us once again that decentralized platforms still face significant challenges in terms of security and anti-money laundering. Hackers utilize cross-chain exchange platforms and DeFi protocols for fund transfers, making traditional blacklist mechanisms and simple fund tracking tools inadequate. Anti-money laundering is not only a regulatory requirement but also the cornerstone of sustainable development in the crypto field. Only through technological innovation and industry collaboration can we truly achieve the goal of "building a firewall together" and provide safer digital asset services for global users.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




