⚠️ Beware of the Latest Scam: How Hackers Use "Pig Butchering + Frontrunning" to Precisely Empty Your Crypto Wallet —
One authorization, assets reduced to zero: Are you still clicking "Approve"?
The following tweet reveals a complex cryptocurrency scam technique:
It combines "Pig Butchering," token authorization abuse, and frontrunning technology.
The scam group implements long-term, efficient fraud by building trust, inducing authorization, monitoring accounts, and quickly stealing funds.
From @GoPlusSecurity @GoPlusZH
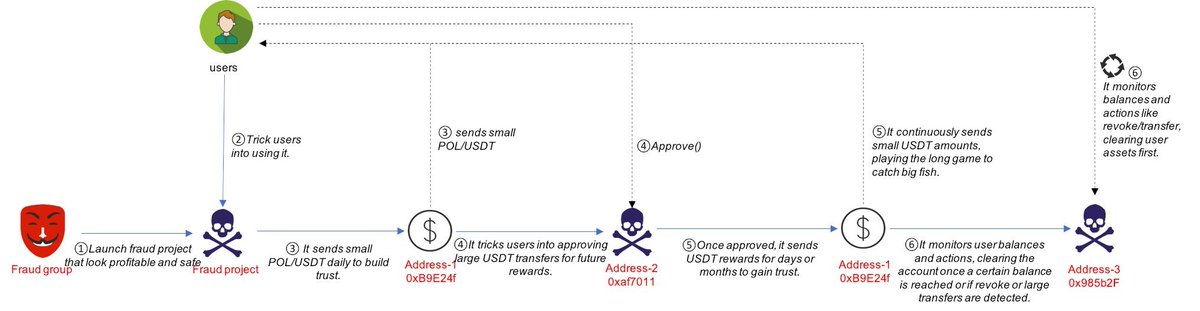
1️⃣ Scam Steps:
1) Create a Fake Project to Attract Users:
The scam group first creates a seemingly "perfect" project, promoting "zero cost, low risk," and promises users that they can continuously earn USDT rewards by completing simple tasks. This high-return, low-risk promise is a typical scam bait aimed at attracting users looking for small profits.
2) Widespread Promotion to Expand User Base:
They widely promote this project through various channels (possibly social media, group chats, etc.) to ensure they reach more potential victims.
The second reply to the tweet includes an image showing that the scammers have made small transfers through numerous addresses to attract user participation.
3) Small Rewards Build Trust:
In the following days or weeks, the scammers send users small amounts of the main token (here it is POL) and USDT rewards.
These small rewards are low-cost but sufficient to make users believe that the project is "real and reliable." This technique aligns with the "fattening" phase in "Pig Butchering," where small returns gradually lower the victims' guard.
4) Induce Users to Authorize Large USDT Transfers:
The scammers use the bait of "greater rewards in the future" to induce users to authorize (approve) large USDT transfer permissions for the smart contract.
Authorization is a mechanism on the blockchain that allows a certain address to transfer a specified amount of tokens on behalf of the user.
Once users authorize, the scammers can transfer the users' USDT at any time in the future without needing to confirm again.
5) Long-term Trust Accumulation, Waiting for the Right Moment:
After authorization, the scammers continue to send USDT rewards, sometimes for several months. This "long-term fishing for big fish" strategy is designed to make users completely trust the project while encouraging them to invest more funds or maintain a high balance, preparing for subsequent fund plundering.
6) Monitor User Accounts, Waiting for Action:
The scam group continuously monitors the users' account balances and behaviors.
If they find that a user's account balance reaches a certain amount, or if the user attempts to revoke authorization or make a large transfer, the scammers will act immediately to quickly transfer the user's funds.
7) Use "Frontrunning" Tools to Quickly Steal Funds:
The scammers use "frontrunning" techniques by paying high gas fees to ensure their transactions are confirmed by the blockchain before the users' transactions. For example, when a user tries to revoke authorization, the scammers' transaction will execute first, directly transferring the user's funds away.
@GoPlusSecurity has tagged three malicious addresses:
0xaf70114597d8E2327663497d58a9989E9bd24aaa
0x985b2F2B4ec4375Df8Dd9a91143Dd98d6D53F6F4
0xB9E24f79Ed5a535C1Bf5CDB2E1D38B1Cb2a6F4Bd
2️⃣ Security Recommendations —
1) Do not believe in "free money";
There is no free lunch. Any project claiming "easy money" should be regarded as high risk, especially those involving cryptocurrency.
2) Manage Token Authorizations Cautiously;
Avoid authorizing easily, especially for EOA (Externally Owned Accounts, i.e., regular wallet addresses).
If authorization is necessary, try to limit the authorized amount to the minimum required.
Additionally, regularly check and revoke unnecessary authorizations (tools like Etherscan's Token Approval Checker can be used).
Wallet authorization revocation tools:
https://revoke.cash (supports multiple chains) https://etherscan.io/tokenapprovalchecker
https://bscscan.com/tokenapprovalchecker
https://polygonscan.com/tokenapprovalchecker
https://snowtrace.io/tokenapprovalchecker
https://cronoscan.com/tokenapprovalchecker
3) Use Professional Security Tools:
Use professional security tools like GoPlus to protect assets, detect malicious addresses, and smart contracts.
Lastly, aside from these methods;
We also need to stay vigilant, continuously learn, understand the basic mechanisms of blockchain (such as token authorization, frontrunning, etc.), operate cautiously, and avoid becoming victims of such scams.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




