Original | Odaily Planet Daily (@OdailyChina)
_

Last night, the leading on-chain DeFi protocol GMX experienced a major security incident, with over $40 million in crypto assets stolen by hackers, involving various mainstream tokens such as WBTC, WETH, UNI, FRAX, LINK, USDC, and USDT. Following the incident, Bithumb announced that GMX's deposit and withdrawal services would be suspended until the network stabilizes.
As a result of this theft, GMX token fell over 25% in four hours, with the price briefly dropping below $11, currently reported at $11.8. According to DefiLlama data, GMX's TVL dropped from $500 million before the theft to $400 million, with a short-term decline of up to 20%.
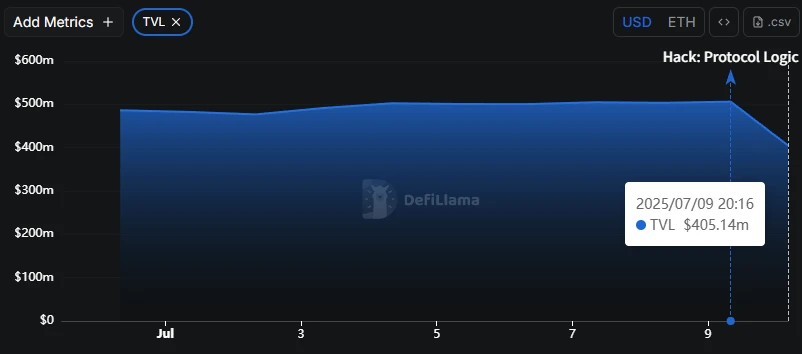
GMX platform TVL affected by the theft incident, briefly dropping to $400 million
Next, Odaily Planet Daily will summarize the reasons for this GMX theft incident, the team's response, and the latest movements of the hackers.
Attackers exploited a reentrancy vulnerability
The fundamental cause of the GMX theft incident lies in the reentrancy vulnerability present in the core function executeDecreaseOrder. The first parameter of this function should have been an external account (EOA), but the attacker passed in a smart contract address, allowing them to re-enter the system during the redemption process, manipulating the internal state, and ultimately redeeming assets far exceeding the actual value of their GLP holdings.
23pds, partner and Chief Information Security Officer at SlowMist, stated on the X platform that in GMX V1, the establishment of short positions immediately updates the global short average price (globalShortAveragePrices), which directly affects the calculation of the total assets under management (AUM), thereby impacting the valuation and redemption amount of GLP tokens.
The attacker exploited the design of GMX enabling the timelock.enableLeverage function during order execution (a prerequisite for opening large short positions) and triggered the reentrancy vulnerability of the executeDecreaseOrder function through contract calls. By leveraging this vulnerability, the attacker repeatedly created short positions, artificially inflating the global short average price without actually changing the market price.
Since AUM relies on this price for calculation, the platform mistakenly included the inflated short losses in the total assets, causing the GLP valuation to be artificially raised. The attacker then redeemed GLP and extracted assets far exceeding their entitled share, realizing huge profits.
Example of the attack transaction: https://app.blocksec.com/explorer/tx/arbitrum/0x03182d3f0956a91c4e4c8f225bbc7975f9434fab042228c7acdc5ec9a32626ef?line=93
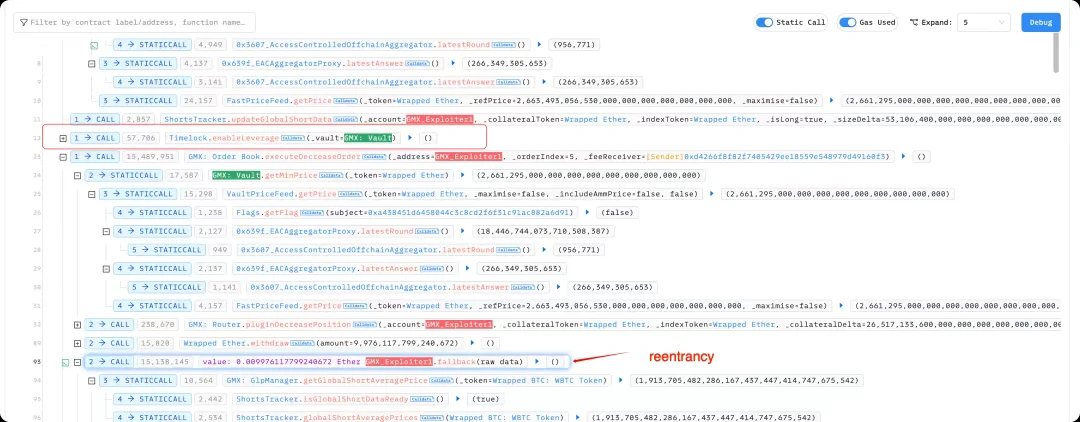
GMX's official response: The GLP liquidity pool of GMX V1 on Arbitrum was attacked due to a vulnerability, GMX V2 is unaffected
In response to this major security incident, the GMX team promptly issued an official statement. They stated on the X platform that the GLP pool of GMX V1 on the Arbitrum platform was attacked due to a vulnerability, with approximately $40 million in tokens transferred from the GLP pool to an unknown wallet, and security partners are involved in investigating this attack.
Currently, trading of GMX V1 on the Arbitrum and Avalanche platforms, as well as the minting and redemption functions of GLP, have been disabled to prevent any further attacks, but this vulnerability does not affect GMX V2 or the GMX token itself.
Since GMX V1 has been attacked, users can take the following actions to reduce risk:
Disable leverage functionality: Call Vault.setIsLeverageEnabled(false) to turn it off; if using Vault Timelock, call Timelock.setShouldToggleIsLeverageEnabled(false).
Set the maxUsdgAmounts of all tokens to "1": Use Vault.setTokenConfig or Timelock.setTokenConfig to prevent further minting of GLP. It is important to note that this value must be set to "1" instead of "0", as setting it to 0 indicates no limit, which would allow the vulnerability to continue to be exploited.
According to the latest updates, the official statement confirms that the attack only targeted GMX V1, while the GMX V2 contract does not use the same calculation mechanism. However, out of caution, GMX has updated the upper limit for GMX V2 tokens on Arbitrum and Avalanche, so the minting of new tokens in most liquidity pools is currently restricted, and this restriction will be lifted as soon as possible.
Additionally, on-chain data shows that GMX has left a message for the hacker address, acknowledging the vulnerability in GMX V1 and offering a 10% white hat bounty, promising not to take further legal action if the remaining 90% of the funds are returned within 48 hours.
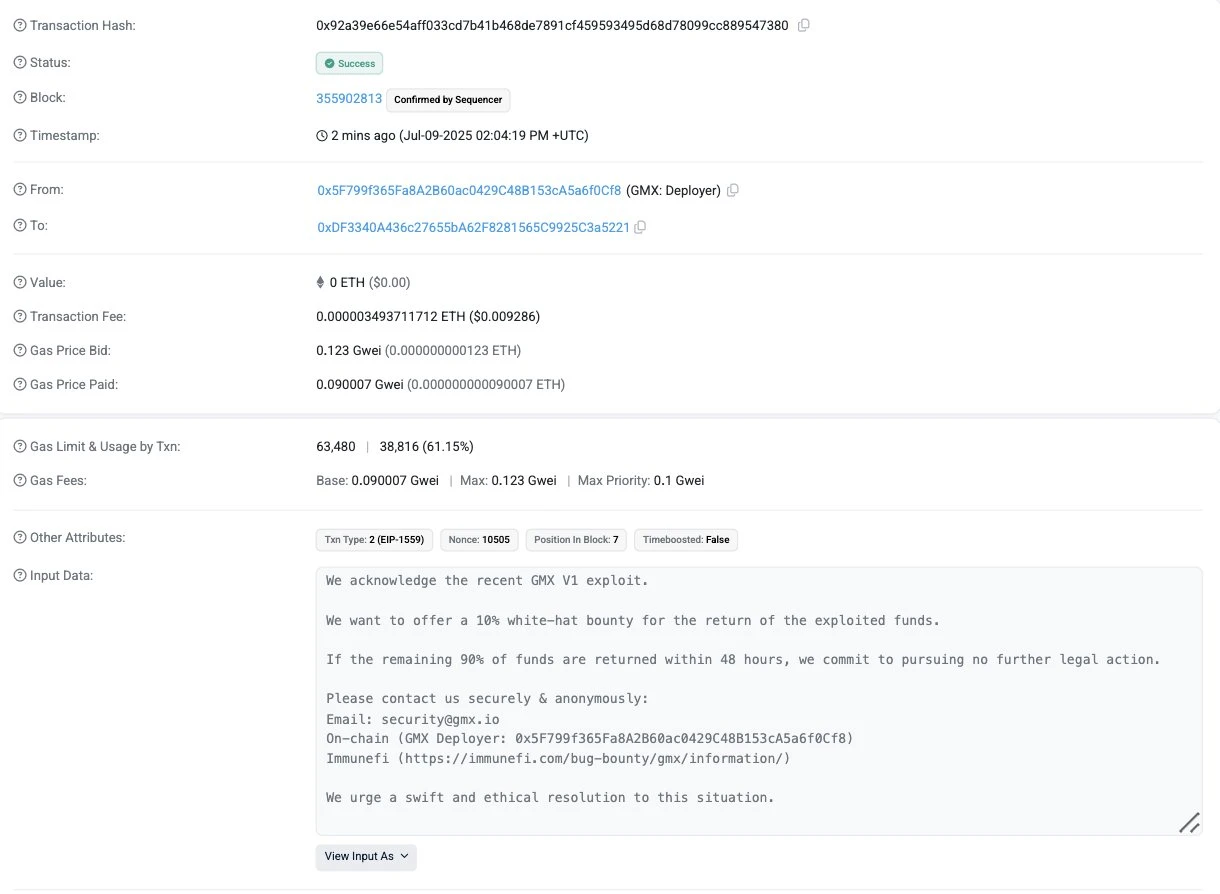
GMX has left a message for the hacker address offering a 10% white hat bounty
Hackers have transferred over $30 million to a new address
On-chain indications suggest that this was a premeditated action, as the hacker's initial funds were transferred from the privacy mixing protocol Tornado Cash days ago, indicating they had long prepared for this attack.
After stealing over $40 million in crypto assets, the hacker quickly transferred over $30 million in assets. According to on-chain data, the GMX hacker's marked address (address: https://debank.com/profile/0xdf3340a436c27655ba62f8281565c9925c3a5221) has transferred 88 BTC (worth about $9.8 million), over 2,200 ETH (worth about $5.85 million), over 3 million USDC, and over 1.3 million DAI to the new address 0x99cdeb84064c2bc63de0cea7c6978e272d0f2dae; and transferred over 4,300 ETH (worth about $11 million) to the new address 0x6acc60b11217a1fd0e68b0ecaee7122d34a784c1. In total, over $30 million has been transferred to other new addresses.
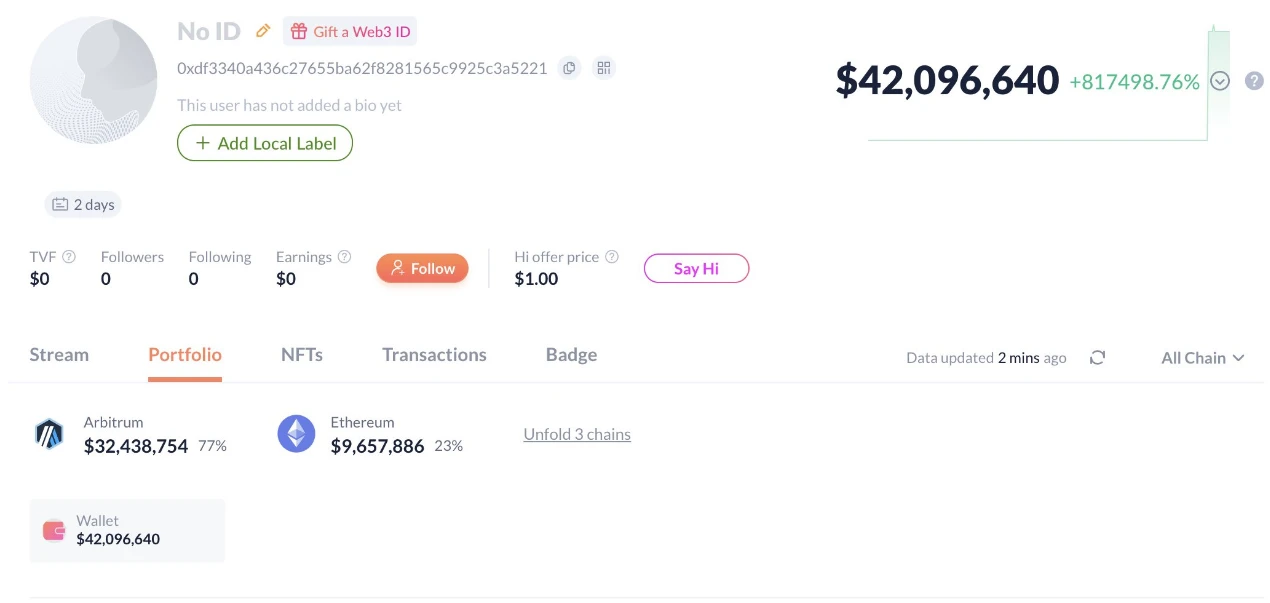
Hackers stole over $40 million in assets
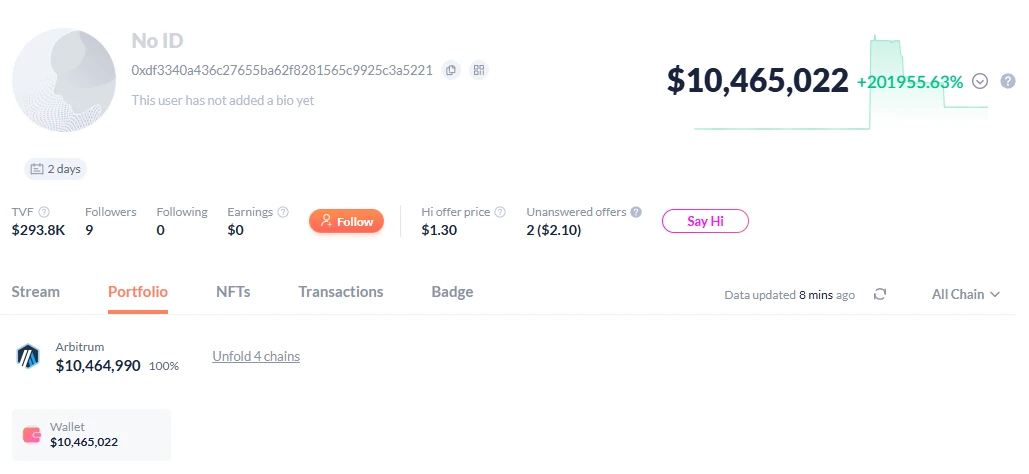
Currently, the hacker address has $10 million remaining that has not been transferred
"On-chain detective" ZachXBT criticized Circle for inaction regarding the hacker's behavior on the X platform, stating that it has been 1 to 2 hours since the GMX attack occurred, but Circle has taken no action against the hacker, who even used Circle's cross-chain transfer protocol CCTP to move the stolen funds from Arbitrum to Ethereum.
Summary
This theft incident not only reveals critical flaws in GMX V1 regarding caller permission verification, state update timing, and leverage mechanism design but also serves as a wake-up call for the entire industry: in systems involving complex financial logic (such as leverage and dynamic pricing) intertwined with contract execution paths, any unprotected entry point can evolve into the starting point of a black swan event.
It is noteworthy that the hacker has exchanged most of the stolen assets for cryptocurrencies that are harder to freeze, especially decentralized assets like ETH and DAI, and has completed fund dispersion through multiple new addresses, further increasing the difficulty of tracking and recovery. Moreover, GMX's proposal of a "10% white hat bounty in exchange for immunity" exposes the current reality of the lack of a unified legal accountability mechanism in the Web3 world.
For DeFi developers, perhaps the more pressing question is not "how did the hacker succeed," but rather—when the system manages real user assets, whether sufficient mechanisms are in place to limit the occurrence of the most extreme attack paths. Otherwise, no matter how perfect the product logic is, once it lacks security boundary design, it will ultimately be difficult to escape the cost of systemic risk.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




