Original Title: "GMX Hacked for $42 Million, How Should DeFi Security Be Ensured?"
Original Author: ChandlerZ, Foresight News
On July 9, the V1 system of the decentralized trading platform GMX was attacked on the Arbitrum network. The attacker exploited a vulnerability within the contract to transfer approximately $42 million in assets from the GLP liquidity pool. GMX has since suspended trading on the platform and blocked the minting and redemption functions of GLP. The attack did not affect GMX's V2 system or its native token, but the incident has once again sparked discussions about the internal asset management mechanisms of DeFi protocols.
Attack Process and Fund Flow
Security firms PeckShield and SlowMist analysis indicate that the attacker exploited a flaw in GMX V1's logic for calculating AUM. This flaw caused the contract to immediately update the global average price after opening a short position. The attacker used this to construct a targeted operation path, achieving token price manipulation and arbitrage redemption.
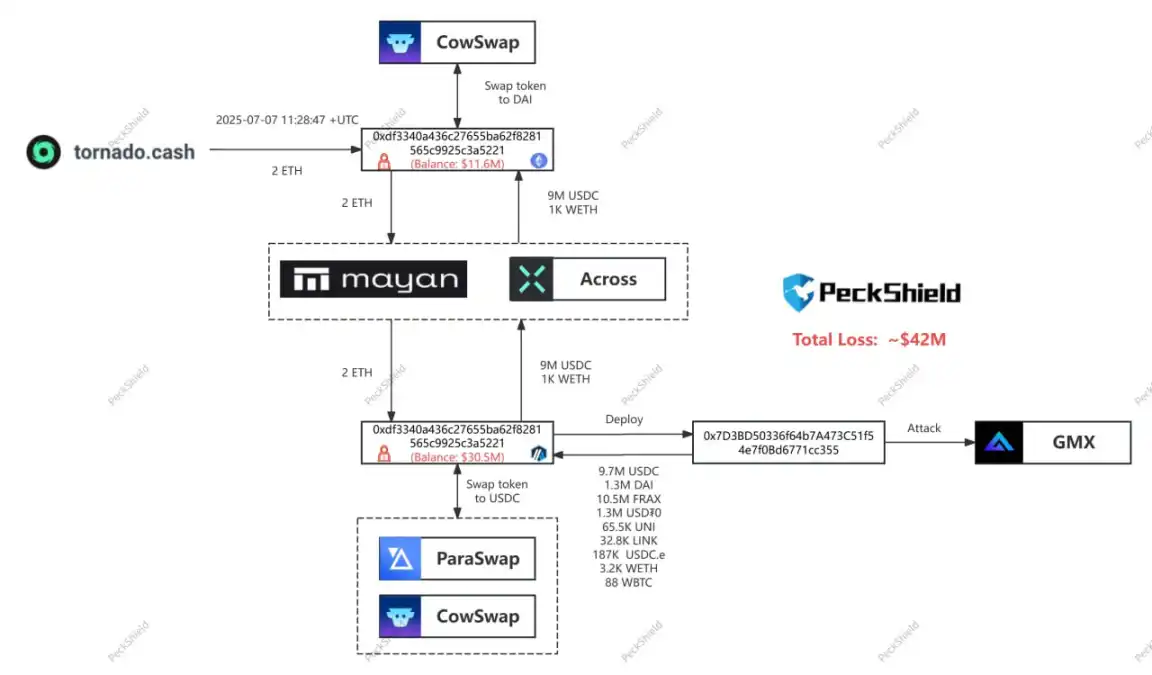
The attacker transferred approximately $9.65 million in assets from Arbitrum to Ethereum, then exchanged them for DAI and ETH. Some of the funds flowed into the mixing protocol Tornado Cash. About $32 million in assets remain on the Arbitrum network, involving tokens such as FRAX, wBTC, and DAI.
After the incident, GMX publicly addressed the hacker on-chain, requesting the return of 90% of the funds and offering a 10% white hat bounty. However, according to the latest on-chain data, the GMX hacker has already exchanged the stolen assets from the GMX V1 pool for ETH.
The stolen assets include WBTC/WETH/UNI/FRAX/LINK/USDC/USDT, and currently, all assets except FRAX have been sold for 11,700 ETH (approximately $32.33 million) and dispersed into four wallets for storage. Therefore, the GMX hacker now holds 11,700 ETH (approximately $32.33 million) and $10.495 million in FRAX across five wallets, totaling approximately $42.8 million.
Analysis from SlowMist suggests that the hacker's actions likely indicate a rejection of GMX's proposal to return the assets in exchange for a 10% white hat bounty.
Flaw in Contract Logic
Security firms point out that the attacker did not rely on unauthorized access to the contract or bypassing permission controls, but rather directly operated based on expected logic functions and repeatedly called functions during the execution period by exploiting the state update time difference, which is a typical reentrancy attack.
SlowMist states that the root cause of this attack lies in a design flaw in GMX V1, where the operation of short positions immediately updates the global short average price (globalShortAveragePrices), directly affecting the calculation of asset management scale (AUM) and leading to the manipulation of GLP token pricing. The attacker exploited the "timelock.enableLeverage" function during order execution (a prerequisite for creating large short positions) to take advantage of this design flaw. Through a reentrancy attack, the attacker successfully established a large number of short positions, manipulated the global average price, artificially raised the GLP price in a single transaction, and profited through redemption operations.
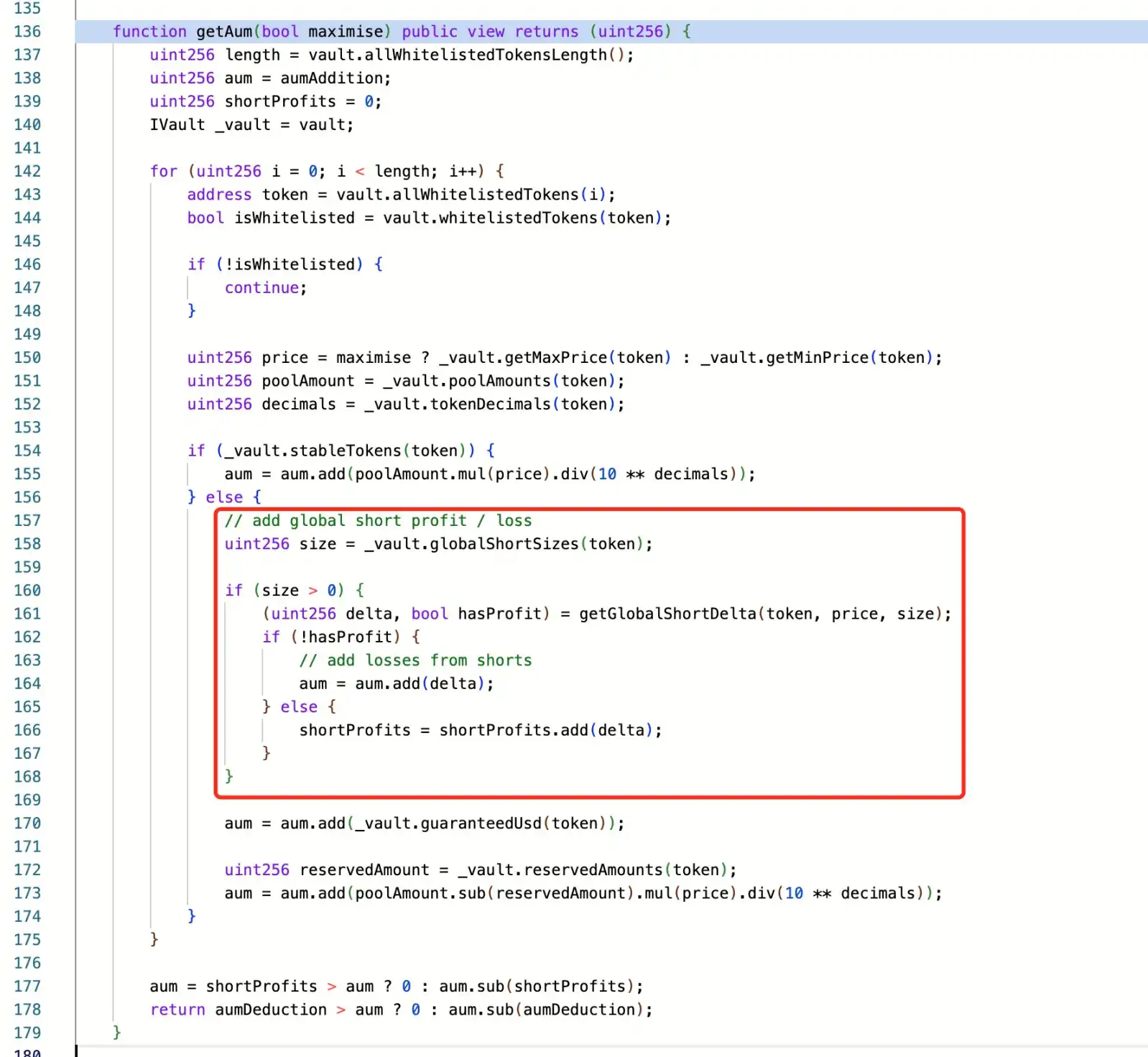
Such attacks are not new in DeFi projects. When contract handling of balances or position updates lags behind asset minting or redemption, it may expose a temporary inconsistent state, allowing attackers to construct operation paths and extract uncollateralized assets. GMX V1 uses a shared fund pool design, composed of multiple user assets forming a unified vault, with the contract controlling account information and liquidity status. GLP is the representative LP token of this pool, and its price and exchange rate are dynamically calculated based on on-chain data and contract logic. This type of synthetic token system has observable risks, including amplified arbitrage opportunities, formation of manipulation spaces, and lag in state cross-calls.
Official Response
GMX officials quickly released a statement after the attack, stating that the incident only affected the V1 system and its GLP fund pool. GMX V2, the native token, and other markets were not affected. To prevent potential subsequent attacks, the team has suspended trading operations on V1 and disabled GLP minting and redemption functions on Arbitrum and Avalanche.
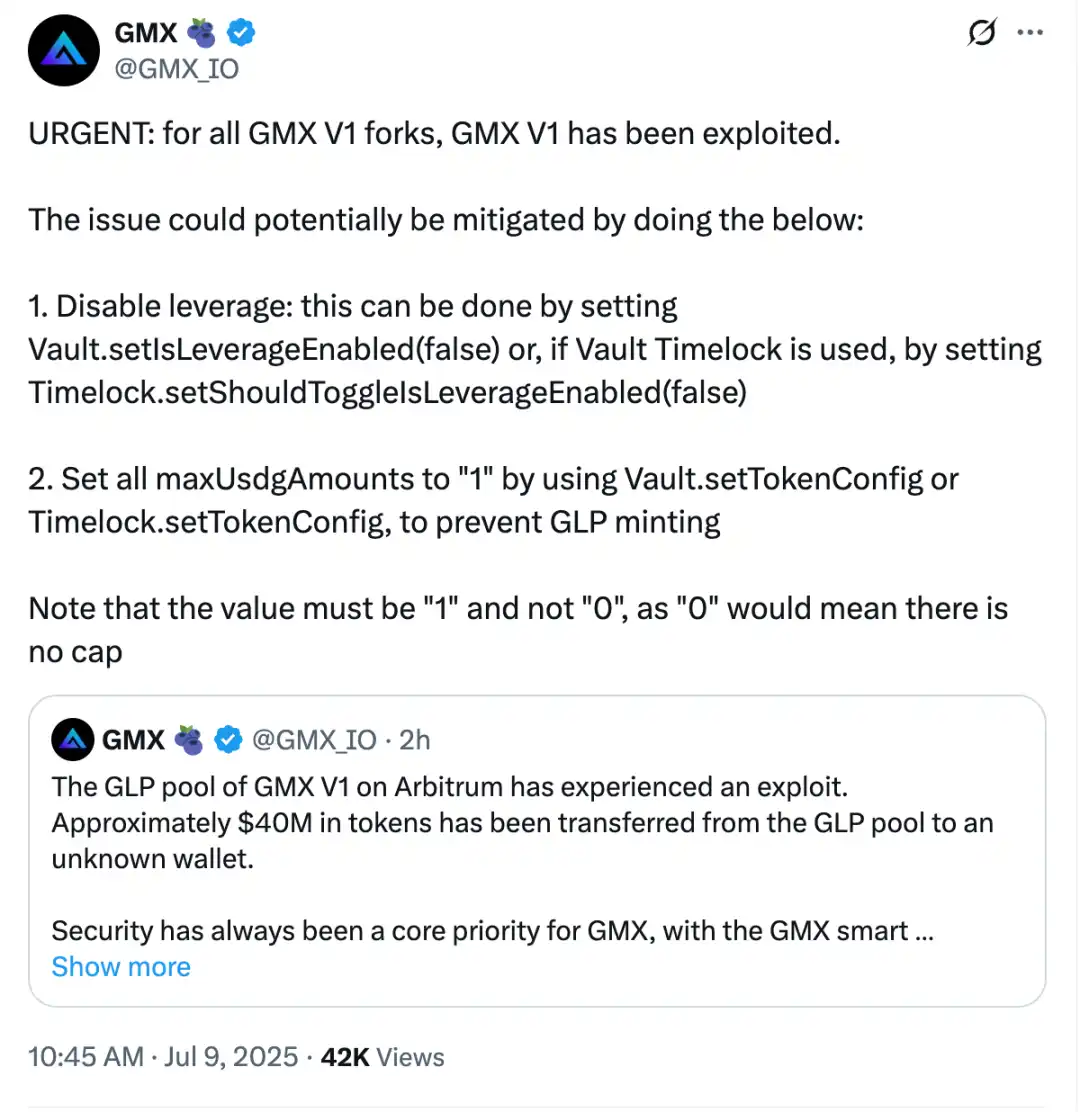
The team also stated that their current focus is on restoring operational security and auditing the internal mechanisms of the contract. The V2 system does not inherit the logical structure of V1 and employs different liquidation, pricing, and position handling mechanisms, with limited risk exposure.
The GMX token fell more than 17% within 24 hours after the attack, dropping from about $14.42 to a low of $10.3, and has slightly rebounded to $11.78. Before the incident, GMX's total trading volume exceeded $30.5 billion, with over 710,000 registered users and an open contract size exceeding $229 million.
Cryptocurrency Asset Security Under Continuous Pressure
The GMX attack is not an isolated incident. Since 2025, the cryptocurrency industry has suffered cumulative losses exceeding last year's levels due to hacker attacks. Although the number of incidents decreased in the second quarter, this does not mean that risks have eased. A CertiK report indicates that in the first half of 2025, total losses caused by hackers, scams, and exploits exceeded $2.47 billion, a nearly 3% increase compared to the $2.4 billion stolen in 2024. The theft of Bybit's cold wallet and the invasion of Cetus DEX resulted in a total loss of $1.78 billion, accounting for the majority of all losses. This concentration of large-scale thefts indicates that high-value assets still lack sufficient isolation and redundancy mechanisms, and the vulnerabilities in platform design have not been effectively addressed.
Among the types of attacks, economic losses from wallet intrusions are the most severe. A total of 34 related incidents occurred in the first half of the year, resulting in approximately $1.7 billion in assets being transferred out. Compared to technically complex exploits, wallet attacks are mostly achieved through social engineering, phishing links, or permission deception, with a lower technical threshold but high destructiveness. Hackers are increasingly targeting user-end asset entry points, especially in scenarios where multi-factor authentication is not enabled or where hot wallets are relied upon.
At the same time, phishing attacks continue to grow rapidly, becoming the most frequent method of attack. A total of 132 phishing attacks were recorded in the first half of the year, causing cumulative losses of $410 million. Attackers guide users into making erroneous operations through fake web pages, contract interaction interfaces, or disguised transaction confirmation processes, thereby obtaining private keys or authorization permissions. Attackers are continuously adjusting their strategies, making phishing behaviors harder to identify, and user-end security awareness and tool equipping have become key defenses.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




