Written by: AiYing AML Peter
Insiders know that there are two types of compliance: one is for regulators to see, and the other is genuinely effective. The former is called "Compliance Theater," while the latter is true risk management. Sadly, the vast majority of institutions, especially those financial technology companies racing on the wind, are unconsciously performing the former.
What is the essence of "Compliance Theater"? It is a carefully constructed stage to cope with inspections, obtain licenses, and appease investors. On this stage, the correctness of processes outweighs everything, and the quality of reports is far more important than the rate of risk identification. The actors (compliance officers) recite pre-written lines (compliance manuals) and operate glamorous props (expensive systems), showcasing a scene of peace and prosperity to the audience (regulatory agencies). As long as the performance is good, the license is obtained, and financing is in place, everyone is happy.
In this grand performance, the most glamorous, expensive, and deceptive prop is the "zombie system," which appears to operate 24/7 but is actually soulless and ineffective. Especially the KYT (Know Your Transaction) system, which should be the sharpest scout on the front lines of anti-money laundering (AML), often "falls" first, becoming a mere shell that consumes budgets and provides a false sense of security. It quietly lies on the server, with green lights blinking and reports being generated, everything seems normal—until a real bomb explodes right under its nose.
This is the biggest compliance trap. You think you have purchased the top-notch equipment and built an impregnable defense, but in reality, you are just feeding a zombie with money and resources. It will not protect you; it will only leave you in the dark when disaster strikes.
So, the question arises: why do the KYT tools we invest heavily in and procure with manpower sometimes become mere walking corpses? Is it a fatal error in technology selection, a complete collapse of process management, or an inevitable result of both?
Today, we will focus on the most popular stage of "Compliance Theater" in the fintech and payment industry, especially in the Southeast Asian market, where the regulatory environment is complex and business growth is rampant. Here, real performances are taking place, and what we need to do is lift the curtain and see the truth behind the scenes.
Act One: Analyzing Zombie Systems—How Your KYT Tool "Dies"
The birth of a "zombie system" does not happen overnight. It does not suddenly die due to a shocking vulnerability or a catastrophic outage; rather, it gradually loses its ability to perceive, analyze, and respond in the day-to-day "normal operation," much like a frog being boiled in water, ultimately becoming an empty shell that only maintains vital signs. We can dissect this process from both technical and process dimensions to see how a fully functional KYT system steps toward "death."
Technical "Brain Death": Single Point of Failure and Data Silos
Technology is the brain of the KYT system. When the neural connections in the brain break, information input is obstructed, and analytical models become rigid, the system enters a "brain death" state. It continues to process data but has lost the ability to understand and judge.
Cognitive Blind Spots of Single Tools: Seeing the World with One Eye
Over-reliance on a single KYT tool is the primary and most common reason for system failure. This is almost common knowledge in the industry, but in the script of "Compliance Theater," this point is often selectively ignored in pursuit of so-called "authority" and "simplified management."
Why is a single tool fatal? Because no single tool can cover all risks. It is like asking a sentry to monitor enemies from all directions; there will always be blind spots. Recently, a research report released by Singapore-licensed digital asset service provider MetaComp revealed this harsh reality through test data. The study analyzed over 7,000 real transactions and found that relying on one or two KYT tools for screening could lead to as much as 25% of high-risk transactions being incorrectly released. This means that a quarter of the risk is directly ignored. This is no longer a blind spot; it is a black hole.
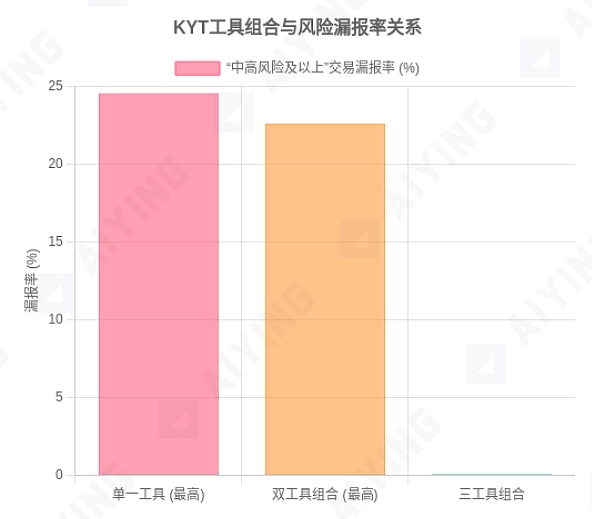
Figure 1: Comparison of "False Clean Rate" under Different KYT Tool Combinations
Data Source: MetaComp Research - Comparative Analysis of On-Chain KYT for AML&CFT, July 2025. The chart shows that when the risk threshold is set to "medium-high risk," the false clean rate of a single tool can be as high as 24.55%, while a combination of two tools can reach a maximum of 22.60%, and a combination of three tools drops sharply to 0.10%.
This enormous risk exposure stems from the inherent flaws in the KYT tool ecosystem. Each tool is built on its proprietary data sets and intelligence-gathering strategies, leading to natural differences and blind spots in the following aspects:
Differences in Data Sources
: Some tools may have close ties with U.S. law enforcement, providing stronger coverage for risk addresses related to North America; others may focus on the Asian market, offering more timely intelligence on localized fraud networks. No single tool can simultaneously be the intelligence king for all regions globally.
Different Focus on Risk Types
: Some tools excel at tracking addresses related to OFAC sanction lists, while others are better at identifying mixing services or darknet markets. If the tool you choose is not adept at recognizing the main risk types your business faces, it is essentially useless.
Update Delays and Intelligence Lag
: The lifecycle of criminal addresses can be very short. A tool that marks a risk address today may take days or even weeks for another tool to synchronize. This time lag in intelligence can allow money launderers to complete several rounds of operations.
Therefore, when an institution places all its hopes on a single KYT tool, it is essentially gambling—betting that all the risks it encounters fall within the "cognitive range" of that tool.
"Malnutrition" Caused by Data Silos: How Can Water Flow Without a Source?
If a single tool is narrow in vision, then data silos represent complete "malnutrition." The KYT system is never an isolated system; its effectiveness is built on a comprehensive understanding of counterparties and transaction behaviors. It needs to continuously obtain "data nutrients" from multiple sources, such as KYC (Know Your Customer) systems, customer risk rating systems, and business systems. When these data channels are blocked or the data quality is poor, the KYT becomes a source-less entity, losing its basis for judgment.
In many rapidly growing payment companies, this scenario is common:
The KYC team is responsible for customer onboarding, and their data is stored in System A; the risk control team monitors transactions, and their data is in System B; the compliance team handles AML reporting, using System C. The three systems belong to different departments and are provided by different vendors, with almost no real-time data interaction between them. The result is that when the KYT system analyzes a real-time transaction, the customer risk rating it relies on may still be static information entered by the KYC team three months ago. This customer may have exhibited various high-risk behaviors in those three months, but that information is trapped in the risk control team's System B, leaving the KYT system completely unaware.
The direct consequence of this "malnutrition" is that the KYT system cannot establish an accurate customer behavior baseline. One of the core capabilities of an effective KYT system is to identify "anomalies"—transactions that deviate from the customer's normal behavior pattern. But if the system does not even know what a customer's "normal" behavior is, how can it identify "anomalies"? Ultimately, it can only regress to relying on the most primitive and crude static rules, producing a large number of worthless "false alerts," bringing it one step closer to becoming a "zombie."
Static Rules' "Searching for the Sword in the Boat": Using Old Maps to Find New Lands
Criminal methods are evolving rapidly, from traditional "smurfing" to using DeFi protocols for cross-chain money laundering, and even conducting fake transactions through NFT markets, with complexity and concealment growing exponentially. However, many "zombie KYT systems" still rely on rule sets that are years out of date, akin to using an old nautical map to search for new lands, destined to yield nothing.
Static rules, such as "alert if a single transaction exceeds $10,000," are trivial in the eyes of today's criminals. They can easily use automated scripts to split a large sum into hundreds or thousands of small transactions, perfectly circumventing such simple thresholds. The real threats are hidden in complex behavioral patterns:
A newly registered account engages in a high frequency of small transactions with numerous unrelated counterparties in a short period.
Funds flow in rapidly and are immediately dispersed through multiple addresses without any pause, forming a typical "peel chain."
The transaction path involves high-risk mixing services, unregistered exchanges, or addresses in sanctioned regions.
These complex patterns cannot be effectively described and captured by static rules. What is needed are machine learning models that can understand transaction networks, analyze funding chains, and learn risk characteristics from vast amounts of data. A healthy KYT system should have dynamic, self-evolving rules and models. In contrast, a "zombie system" has lost this capability; once its rule set is established, it rarely sees updates, ultimately falling far behind in the arms race against criminal activities, leading to complete "brain death."
Process-Level "Cardiac Arrest": From "One-Time Success" to "Alert Fatigue"
If technical flaws lead to "brain death" in the system, then the collapse of process management directly results in "cardiac arrest." Even the most advanced system, if not driven and responded to by the correct processes, is just a pile of expensive code. In "Compliance Theater," failures in processes are often more hidden and more lethal than failures in technology.
The Illusion of "Victory Upon Launch": Mistaking the Wedding for the End of Love
Many companies, especially startups, approach compliance construction with a "project-based" mindset. They believe that the procurement and launch of a KYT system is a project with a clear start and end. Once the system is successfully launched and passes regulatory acceptance, the project is declared a success. This is the most typical illusion of "Compliance Theater"—mistaking the wedding for the end of love, thinking that they can rest easy from then on.
However, the lifecycle of a KYT system begins on the first day of launch. It is not a tool that can be "set and forget," but a "living entity" that requires continuous care and optimization. This includes:
Continuous Parameter Calibration
: The market is changing, customer behaviors are changing, and money laundering techniques are evolving. The monitoring thresholds and risk parameters of the KYT system must be adjusted accordingly. A $10,000 alert threshold that was reasonable a year ago may now be meaningless after a tenfold increase in transaction volume.
Regular Rule Optimization
: With the emergence of new risks, new monitoring rules need to be continuously developed and deployed. At the same time, the effectiveness of old rules should be regularly evaluated, eliminating "garbage rules" that only produce false alerts.
Necessary Model Retraining
: For systems using machine learning models, it is essential to periodically retrain the models with the latest data to ensure their ability to recognize new risk patterns and prevent model decay.
When an organization falls into the illusion of "victory upon launch," these crucial follow-up maintenance tasks are often neglected. No one is responsible, and there is no budget support; the KYT system becomes like a sports car abandoned in a garage—no matter how good the engine is, it will slowly rust and eventually turn into a pile of scrap metal.
"Alert Fatigue" Crushes Compliance Officers: The Last Straw
A poorly configured and poorly maintained "zombie system" has the most direct and disastrous consequence of generating a massive number of false alerts. Industry observations indicate that in many financial institutions, over 95% or even 99% of the alerts generated by the KYT system are ultimately verified as false positives. This is not just an issue of inefficiency; it triggers a deeper crisis—"alert fatigue."
We can imagine a compliance officer's daily routine:
Every morning, he opens the case management system and sees hundreds of alerts waiting to be processed. He clicks on the first one, and after half an hour of investigation, discovers it is a normal business transaction, so he closes it. The second one is the same. The third one is still the same… Day after day, he is overwhelmed by an endless sea of false alerts. The initial vigilance and seriousness gradually give way to numbness and indifference. He starts looking for shortcuts to quickly close alerts, and his trust in the system plummets. Eventually, when a genuine high-risk alert appears among them, he may just glance at it, habitually mark it as a "false positive," and then close it.
"Alert fatigue" is the last straw that breaks the compliance line. It psychologically destroys the combat effectiveness of the compliance team, turning them from "hunters" of risk into "cleaners" of alerts. The entire compliance department's energy is consumed in ineffective battles with a "zombie system," while real criminals swagger through the defenses under the cover of alert noise.
At this point, a KYT system has completely "stopped beating" in terms of processes. It continues to generate alerts, but these "heartbeats" have lost their meaning—no one responds, and no one believes them. It has completely turned into a zombie.
A friend of mine had a company that, in order to obtain a license and please investors, staged a classic "Compliance Theater": they publicly announced the procurement of the industry's top KYT tool and used it as promotional capital for their "commitment to the highest compliance standards." However, to save money, they only purchased services from one vendor. The management's logic was: "We used the best, so don't blame me if something goes wrong." They selectively forgot that any single tool has blind spots.
Additionally, the compliance team was understaffed and lacked technical knowledge, so they could only use the most basic static rule templates provided by the vendor. Monitoring large transactions and filtering a few publicly available blacklist addresses was considered task completion.
The most critical issue arose when business volume increased, and system alerts began to flood in. Junior analysts quickly discovered that over 95% of them were false positives. To meet KPIs, their work shifted from "investigating risks" to "closing alerts." Over time, no one took the alerts seriously anymore.
Professional money laundering gangs quickly caught the scent of decay. They used the simplest yet effective methods to turn this "zombie system" into their ATM: by employing the "smurfing" tactic, they split funds from illegal gambling into thousands of small transactions below the monitoring threshold, disguising them as e-commerce returns. Ultimately, the alert was triggered not by their team members but by their partner bank. When the regulatory agency's investigation letter landed on the CEO's desk, they were left bewildered, and it was later reported that their license was revoked.
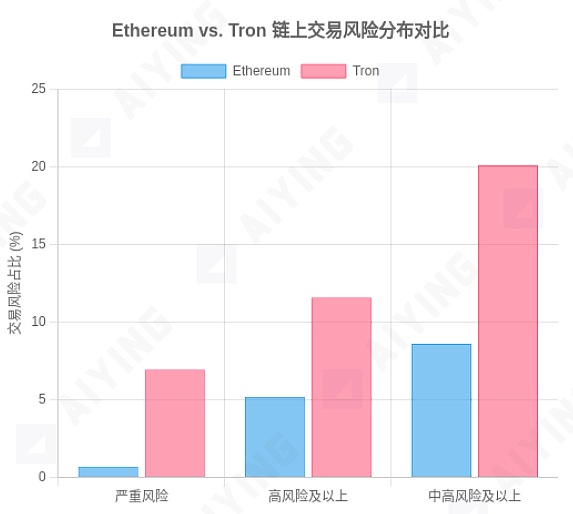
Figure 2: Comparison of Risk Levels Across Different Blockchain Networks
Data Source: MetaComp Research - Comparative Analysis of On-Chain KYT for AML&CFT, July 2025. The chart shows that in the sampled data, the proportion of transactions on the Tron chain rated as "severe," "high," or "medium-high" risk is significantly higher than that on the Ethereum chain.
The stories around us serve as a mirror, reflecting the shadows of countless fintech companies performing "Compliance Theater." They may not have collapsed yet, simply because they have been lucky enough not to be targeted by professional criminal gangs. But ultimately, it is only a matter of time.
Act Two: From "Zombie" to "Sentinel"—How to Awaken Your Compliance System?
After revealing the pathology of "zombie systems" and witnessing the tragedy of "Compliance Theater," we cannot merely dwell on criticism and lamentation. As frontline practitioners, we are more concerned with: how to break the deadlock? How to awaken a dying "zombie" and transform it into a truly effective and defensive "frontline sentinel"?
The answer does not lie in purchasing more expensive and "authoritative" single tools, but in a complete transformation from concepts to tactics. This methodology has long been an unspoken secret among the true practitioners in the industry. MetaComp's research systematically quantifies and publicizes it for the first time, providing us with a clear and executable combat manual.
Core Solution: Say Goodbye to Solo Acts and Embrace a "Multi-Layer Defense System"
First, we must fundamentally abandon the theater mindset of "buying a tool and calling it a day." True compliance is not a solo act; it is a positional battle that requires building a multi-layered defense system. You cannot expect a single sentinel to block an army; what you need is a three-dimensional defense network composed of sentinels, patrols, radar stations, and intelligence centers.
Tactical Core: Multi-Tool Combination Punch
The tactical core of this defense system is the "multi-tool combination punch." The blind spots of a single tool are inevitable, but the blind spots of multiple tools are complementary. Through cross-validation, we can minimize the hiding space of risks.
So, the question arises: how many tools are needed? Two? Four? Or is more always better?
MetaComp's research provides a crucial answer: a combination of three tools is the golden rule for achieving the best balance between effectiveness, cost, and efficiency.
We can understand this "three-piece set" in simple terms:
The first tool is your "frontline sentinel"
: It may have the broadest coverage and can detect most conventional risks.
The second tool is your "special patrol team"
: It may have unique reconnaissance capabilities in a specific area (such as DeFi risks or regional intelligence) and can uncover hidden threats that the "sentinel" cannot see.
The third tool is your "rear intelligence analyst"
: It may possess the most powerful data correlation analysis capabilities, linking the scattered clues discovered by the first two to outline a complete risk profile.
When these three work together, their power is far from a simple sum. Data shows that upgrading from two tools to three tools results in a qualitative leap in compliance effectiveness. MetaComp's report indicates that a well-designed three-tool screening model can reduce the "false clean rate" of high-risk transactions to below 0.10%. This means that 99.9% of known high-risk transactions will be captured. This is what we refer to as "effective compliance."
In contrast, while upgrading from three tools to four tools can further reduce the false clean rate, the marginal benefits become very small, while the costs and time delays are significant. Research shows that screening time for four tools can take up to 11 seconds, while three tools can keep it around 2 seconds. In payment scenarios requiring real-time decision-making, this 9-second difference could be the line between life and death for user experience.
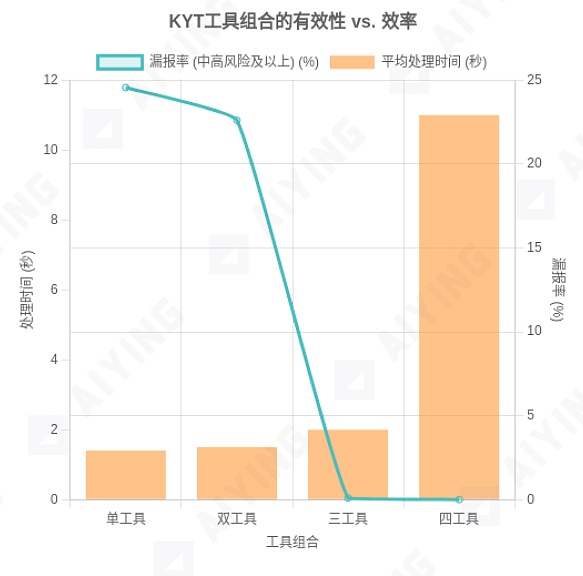
Figure 3: Effectiveness and Efficiency Trade-offs of KYT Tool Combinations
Data Source: MetaComp Research - Comparative Analysis of On-Chain KYT for AML&CFT, July 2025. The chart visually demonstrates the impact of increasing the number of tools on reducing the "false clean rate" (effectiveness) and increasing "processing time" (efficiency), clearly indicating that a three-tool combination is the most cost-effective choice.
Methodology Implementation: Establish Your Own "Rule Engine"
Choosing the right "three-piece set" combination is just the first step in upgrading your equipment. More critically, how to command this multi-unit force to work together. You cannot let the three tools speak independently; you need to establish a unified command center—your own "rule engine," independent of any single tool.
Step One: Standardize Risk Classification—Speak the Same Language
You cannot let the tools lead you by the nose. Different tools may describe the same risk using different labels like "Coin Mixer," "Protocol Privacy," or "Shield." If your compliance officers need to remember the "dialects" of each tool, it would be a disaster. The correct approach is to establish a set of internally unified and clear risk classification standards, then map the risk labels of all integrated tools to your own standard system.
For example, you could establish the following standardized classification:
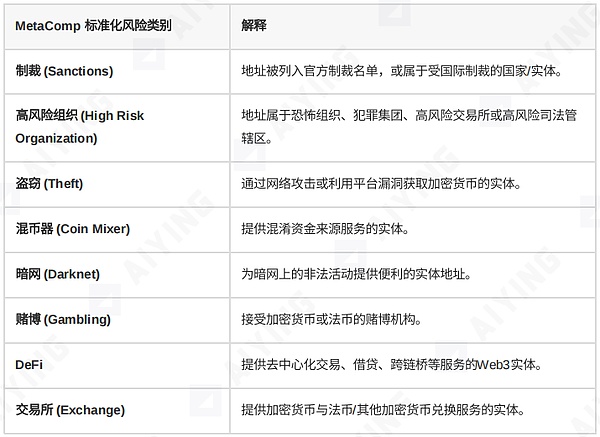
Table 1: Example of Risk Category Mapping
In this way, regardless of which new tool is integrated, you can quickly "translate" it into an internally unified language, enabling cross-platform horizontal comparisons and unified decision-making.
Step Two: Unify Risk Parameters and Thresholds—Draw Clear Red Lines
With a unified language in place, the next step is to establish unified "rules of engagement." You need to set clear, quantifiable risk thresholds based on your own risk appetite and regulatory requirements. This is a crucial step in transforming subjective "risk preferences" into objective, machine-executable instructions.
These rules should not merely be simple monetary thresholds but should be more complex, multi-dimensional parameter combinations, such as:
Severity Level Definition
: Clearly define which risk categories fall under "severe" (such as sanctions, terrorist financing), which fall under "high risk" (such as theft, dark web), and which are considered "acceptable" (such as exchanges, DeFi).
Transaction-Level Taint % Threshold
: Define the percentage of funds in a transaction that indirectly comes from high-risk sources, which, when reached, should trigger an alert. This threshold needs to be scientifically set through extensive data analysis, rather than being arbitrarily decided.
Cumulative Taint % Threshold at Wallet Level
: Define the percentage of funds a wallet has transacted with high-risk addresses throughout its entire transaction history, which, when reached, should mark the wallet as high risk. This effectively identifies "old hands" that have long engaged in gray transactions.
These thresholds are the "red lines" you set for the compliance system. Once touched, the system must respond according to the pre-set script. This makes the entire compliance decision-making process transparent, consistent, and defensible.
Step Three: Design a Multi-Layer Screening Workflow—From Point to Area for Comprehensive Strikes
Finally, you need to integrate the standardized classifications and unified parameters into an automated multi-layer screening workflow. This process should function like a precision funnel, filtering through layers and gradually focusing to achieve precise strikes against risks while avoiding excessive interference with a large number of low-risk transactions.
An effective workflow should include at least the following steps:
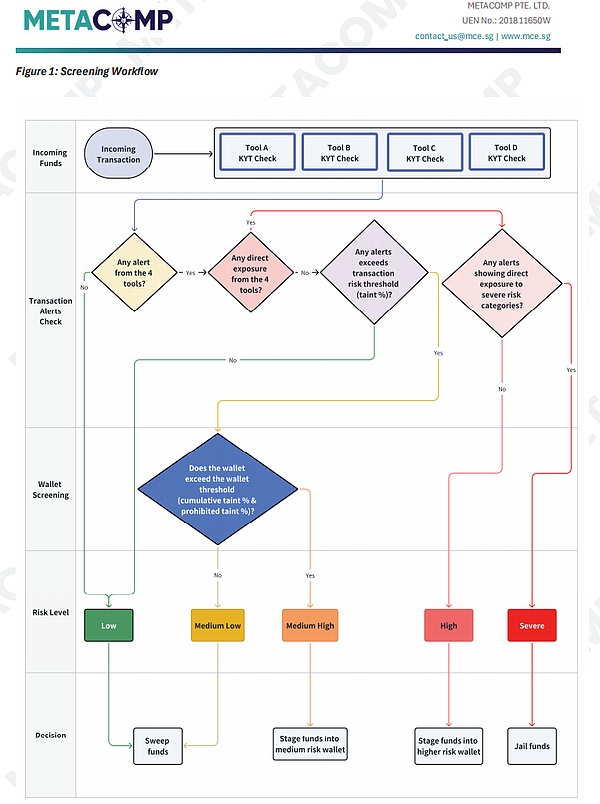
Figure 4: An Example of an Effective Multi-Layer Screening Workflow (Adapted from MetaComp KYT Methodology)
Initial Screening
: All transaction hashes and counterparty addresses are first scanned in parallel using the "three-piece set" tools. If any tool triggers an alert, the transaction moves to the next stage.
Direct Exposure Assessment
: The system determines whether the alert is due to "direct exposure," meaning the counterparty address itself is a marked "severe" or "high-risk" address. If so, this is the highest priority alert and should immediately trigger a freeze or manual review process.
Transaction-Level Exposure Analysis
: If there is no direct exposure, the system begins "fund tracing," analyzing what percentage (Taint %) of the funds in this transaction can be indirectly traced back to risk sources. If this percentage exceeds the pre-set "transaction-level threshold," it moves to the next step.
Wallet-Level Exposure Analysis
: For cases where transaction-level risk is exceeded, the system will further conduct a "comprehensive examination" of the counterparty's wallet, analyzing its overall risk status (Cumulative Taint %). If the wallet's "health" is also below the pre-set "wallet-level threshold," the transaction is ultimately confirmed as high risk.
Final Decision
: Based on the final risk rating (severe, high, medium-high, medium-low, low), the system automatically or prompts manual execution of corresponding actions: release, intercept, return, or report.
The brilliance of this process lies in its transformation of risk identification from a simple "yes/no" judgment into a three-dimensional assessment process that moves from point (individual transaction) to line (funding chain) to area (wallet profile). It effectively distinguishes between "direct hits" of severe risks and "indirect contamination" of potential risks, thereby optimizing resource allocation—responding fastest to the highest-risk transactions, conducting in-depth analysis on medium-risk transactions, and quickly releasing the vast majority of low-risk transactions, perfectly resolving the conflict between "alert fatigue" and "user experience."
Epilogue: Dismantle the Stage and Return to the Battlefield
We have spent a long time dissecting the pathology of "zombie systems," reviewing the tragedy of "Compliance Theater," and exploring the "battle manual" for awakening systems. Now, it is time to return to the starting point.
The greatest harm of "Compliance Theater" is not the budget and manpower it consumes, but the deadly, false "sense of security" it brings. It leads decision-makers to mistakenly believe that risks are under control, while executors become numb in their daily ineffective labor. A silent "zombie system" is far more dangerous than a non-existent system because it can lead you into danger unprepared.
In today's era, where black market technology and financial innovation iterate simultaneously, relying on a single tool for KYT monitoring is akin to running naked on a battlefield filled with gunfire. Criminals have an unprecedented arsenal—automated scripts, cross-chain bridges, privacy coins, DeFi mixing protocols—while if your defense system is still at the level of a few years ago, being breached is just a matter of time.
True compliance has never been a performance to please the audience or to pass inspections. It is a hard battle, a protracted war that requires excellent equipment (multi-layer tool combinations), tight tactics (unified risk methodologies), and outstanding soldiers (professional compliance teams). It does not need a glamorous stage and hypocritical applause; it requires a reverence for risk, honesty with data, and continuous refinement of processes.
Therefore, I call on all practitioners in this industry, especially those with resources and decision-making power: please abandon the fantasy of "silver bullet" solutions. There is no magical tool that can solve all problems once and for all. Building a compliance system has no endpoint; it is a dynamic lifecycle process that requires continuous iteration and improvement based on data feedback. The defense system you establish today may have new vulnerabilities tomorrow; the only way to respond is to remain vigilant, keep learning, and continuously evolve.
It is time to dismantle the false stage of "Compliance Theater." Let us return to the challenging yet opportunity-filled battlefield of real risks with a truly effective "sentinel system." Because only there can we truly safeguard the value we aim to create.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




