⚠️ Today is also a historic moment, as Monero has encountered a significant risk —
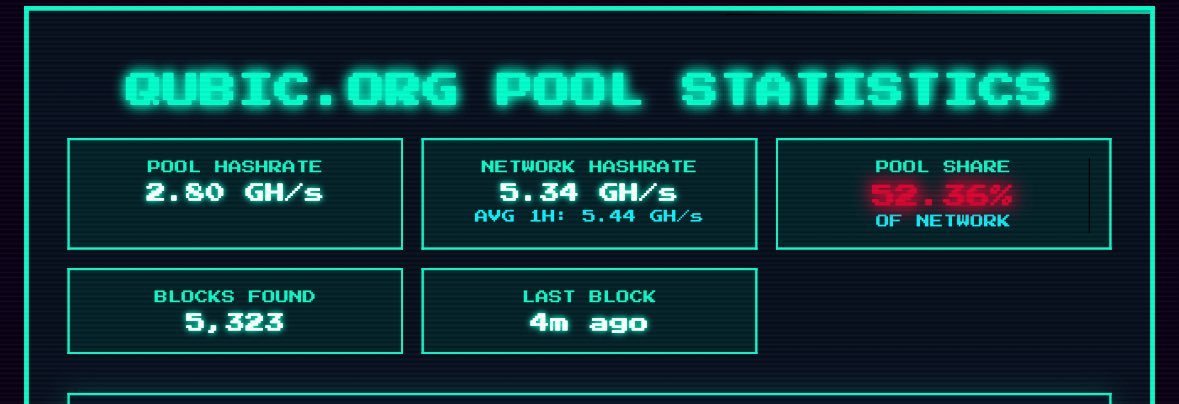
Qubic briefly controlled 52.72% of Monero's hash rate, theoretically enabling a double-spending attack.
A double-spending attack means that the same amount of money can be spent twice. Let me briefly explain the logic and principles —
1⃣ The attacker sends one coin to their own account, using a forked new chain to record this transaction;
2⃣ Then, they send the same coin to the exchange, waiting for the public blockchain (the original blockchain) to record the transaction. Once the exchange confirms this transaction, the attacker quickly sells the coin, withdraws, and leaves.
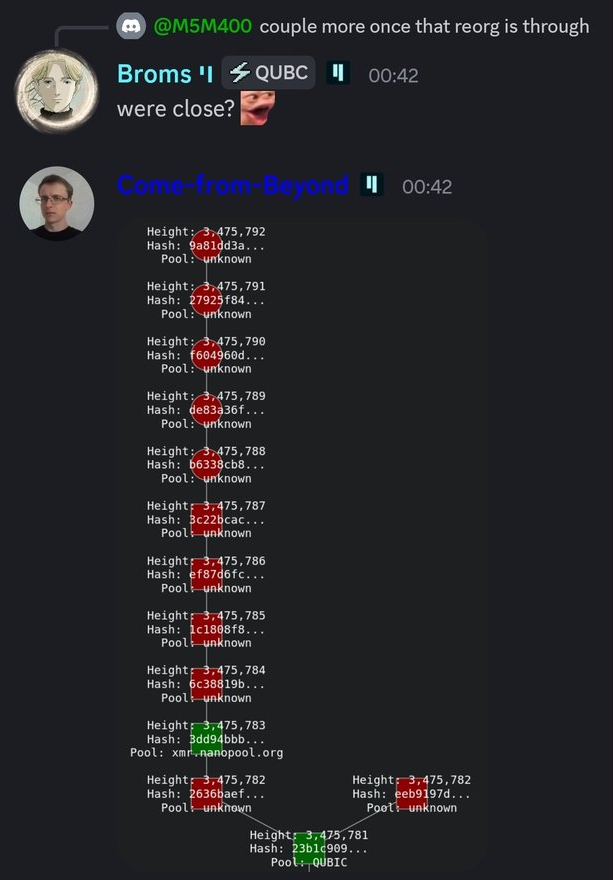
3⃣ The attacker publicly forks the new chain, and since they control 51% of the hash power, the new chain becomes longer than the public blockchain, forcing the entire network to recognize the new chain, rendering the original public blockchain invalid.
This means that the transaction recognized by the entire network is that the attacker sent the coin to themselves, rather than the transaction sent to the exchange;
However, at this point, the Bitcoin at the exchange has already been withdrawn, but the attacker's coins have not decreased at all, as they have already been confirmed on the new chain.
So, if you control 51% of the hash power, you can do whatever you want, and the entire blockchain becomes untrustworthy.
Although Qubic claims there was no malicious intent and it was just a test, who can say for sure in this dark forest!
This serves as a serious wake-up call for all POW systems!
You can check out a previously released report titled "Qubic's Threat Analysis Report on Monero's Hash Power," which goes into detail: https://www.scribd.com/document/896285564/Qubic%E5%AF%B9Monero%E7%AE%97%E5%8A%9B%E5%A8%81%E8%83%81%E5%88%86%E6%9E%90
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




