In October 2025, the U.S. District Court for the Eastern District of New York disclosed an unprecedented case of cryptocurrency asset seizure, with the U.S. government confiscating 127,271 bitcoins, valued at approximately $15 billion at market prices.
Cobo co-founder Shen Yu stated that law enforcement agencies did not obtain the private keys through violent cracking or hacking but rather exploited a randomness vulnerability. Some forums also claimed that law enforcement directly seized the wallet's mnemonic phrases or private key files from servers and hardware wallets controlled by Chen Zhi and his family, executives of the Prince Group, but the specific facts have not yet been publicly reported.
These hardware wallets were subsequently transferred to a multi-signature cold storage managed by the U.S. Marshals Service (USMS) under the U.S. Department of the Treasury. The transfer of 9,757 BTC to the official custody address on October 15, 2025, signed by USMS, originated from this seizure. The U.S. Department of Justice described Lubian as part of the money laundering network of the Cambodian Prince Group, emphasizing that the criminal group attempted to launder scam funds using "new coins" mined from pools.
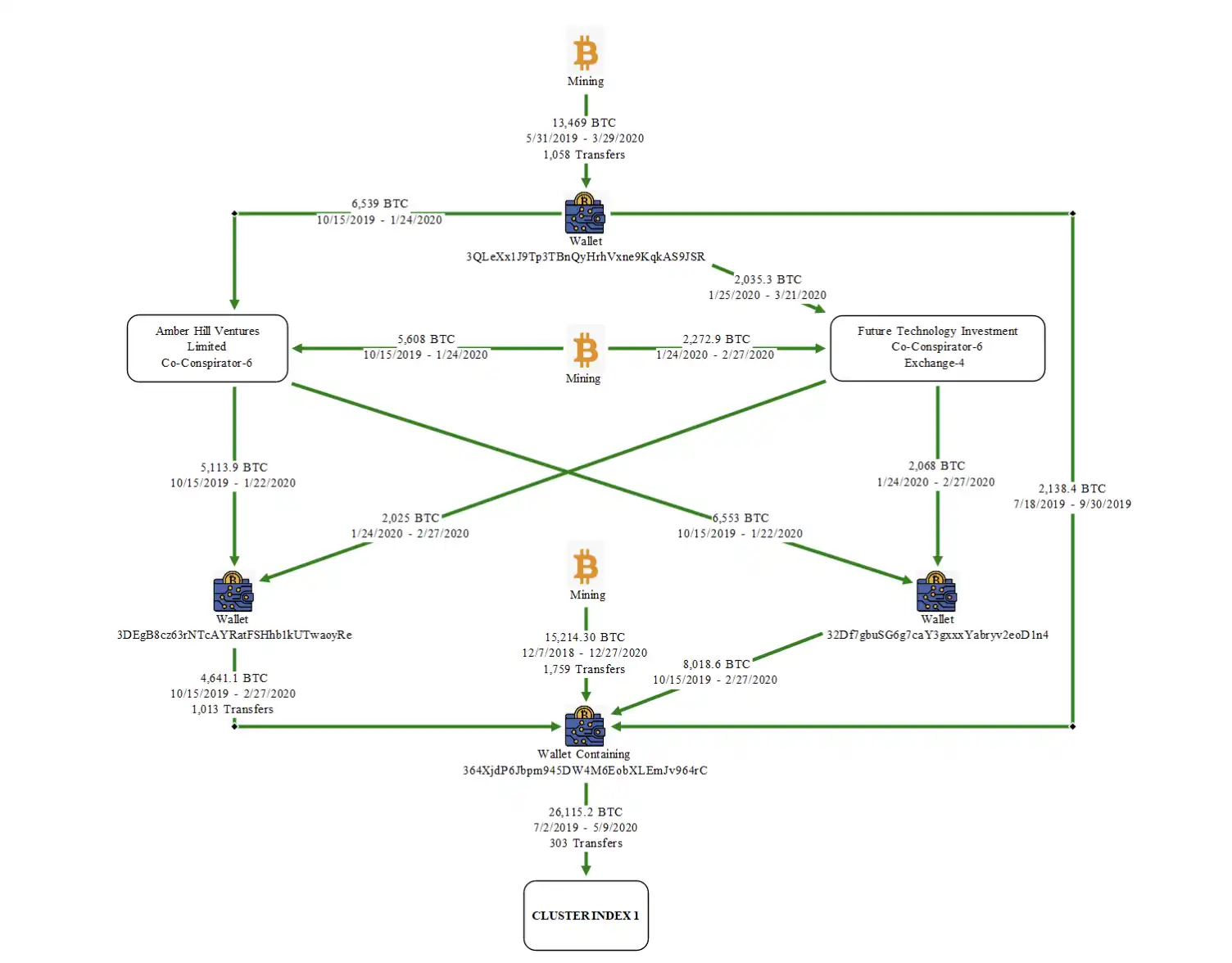
Some community members tracked on-chain data and determined that this was the batch of bitcoins stolen due to vulnerabilities in the Lubin mining pool at the end of 2020. The Lubin mining pool suddenly appeared in 2020 without any team background information or disclosed operational model, yet its hash rate quickly ranked among the top 10 mining pools in the world, at one point accounting for nearly 6% of the global hash rate.
The report mentioned that Chen Zhi boasted to others in the Prince Group about "considerable profits because there are no costs," but it is still unclear whether this was established by Chen Zhi or later controlled by him. However, this case has brought the dormant whale back to the surface, prompting a reevaluation of the wallet private key security disaster that lurked around 2020.
In subsequent investigations, researchers found that the first two words of the mnemonic from the damaged key generation process were "Milk Sad," which later became known as the Milk Sad incident.
Hidden Dangers of Weak Randomness
Everything stems from the Mersenne Twister MT19937-32, a pseudo-random number generator.
Bitcoin private keys should consist of a 256-bit random number, theoretically allowing for 2^256 combinations. To generate an identical sequence, one would need to perfectly match 256 "coin tosses," which is not impossible but extremely unlikely; the security of a wallet does not come from luck but from this vast space of possibilities.
However, tools like the Lubian mining pool used the Mersenne Twister MT19937-32 random number generator, which is not a truly fair "coin toss machine" but rather a device that consistently selects numbers within a limited and patterned range.
Once hackers grasped this pattern, they could quickly enumerate all possible weak private keys through brute force, thereby unlocking the corresponding Bitcoin wallets.
Due to some wallet or mining pool users' misunderstandings about security, between 2019 and 2020, many Bitcoin wallets generated using this "weak random algorithm" accumulated astonishing wealth, with a significant influx of funds into this vulnerable area.
According to statistics from the Milk Sad team, between 2019 and 2020, these weak key wallets held over 53,500 bitcoins at one point.
The sources of funds included whale-level concentrated transfers; in April 2019, four weak wallets received approximately 24,999 bitcoins in a short period. There were also regular mining rewards, with certain addresses receiving over 14,000 bitcoins marked as "lubian.com" within a year. Currently, it is found that there are a total of 220,000 such wallets, and the holders clearly did not realize the risks in the private key generation process, continuing to invest assets into them to this day.
Mass Withdrawal at the End of 2020
The long-standing security vulnerabilities erupted at the end of 2020. On December 28, 2020, abnormal transactions appeared on-chain, with a large number of wallets in the Lubian weak key range being drained within hours, approximately 136,951 bitcoins were transferred out in one go, valued at about $3.7 billion at the then price of around $26,000 per bitcoin.
The transaction fee was fixed at 75,000 sats, remaining consistent regardless of the amount, indicating that the operator was well-versed in Bitcoin network operations. Some of the funds subsequently flowed back to the Lubian mining pool for future mining rewards, suggesting that not all transferred assets fell into the hands of hackers. However, for the victims, the losses were already a fact.
Even more bizarrely, some on-chain transactions carried messages such as "To the white hat saving our assets, please contact 1228btc@gmail.com." Since the weak private key addresses had already been exposed, anyone could send transactions with messages to these addresses, and this information did not necessarily come from actual victims.
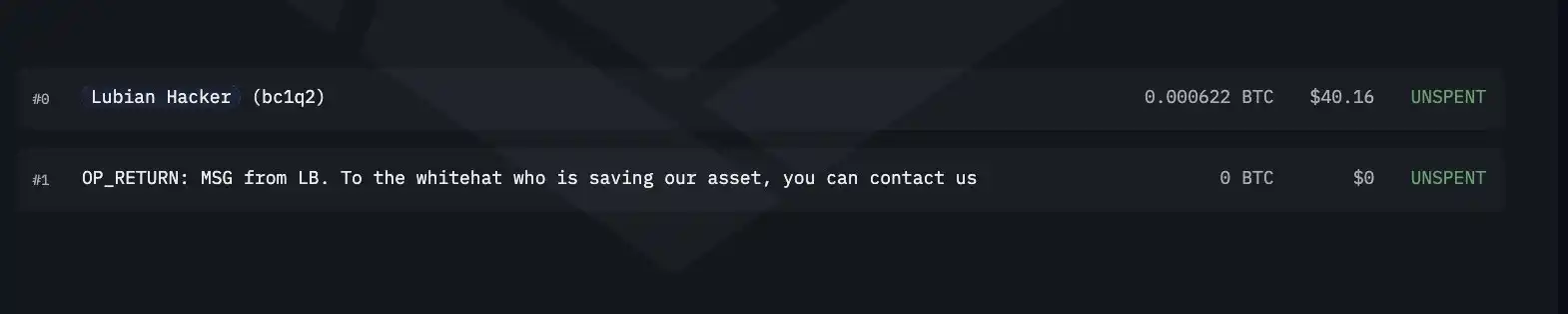
It remains unclear whether this was a hacker's mockery or a victim's plea for help. The fatal issue was that this massive transfer was not immediately recognized as theft.
Researchers from Milk Sad later admitted in their analysis that at the time, Bitcoin prices were soaring, and mining pool revenues had stopped. They were uncertain whether it was the work of hackers or if the Lubian management sold at a high point and reorganized the wallets. They pointed out, "If the theft occurred in 2020, it would have been earlier than the confirmed timeline of the Mersenne Twister weak key attack, but we cannot rule out this possibility."
Due to this uncertainty, the fund withdrawal at the end of 2020 did not trigger industry alarms, and the massive bitcoins remained dormant on-chain for years, becoming an unresolved mystery.
Thus, it was not just Lubian that was affected, but also the old version of Trust Wallet. On November 17, 2022, the security research team Ledger Donjon first disclosed the random number vulnerability in Trust Wallet to Binance. The team responded quickly, pushing a fix to GitHub the next day and notifying affected users in succession.
However, it was not until April 22, 2023, that Trust Wallet officially disclosed the vulnerability details and compensation measures. During this period, hackers had launched several attacks exploiting the vulnerability, including stealing about 50 bitcoins on January 11, 2023.
Delayed Alarm
Meanwhile, the vulnerability was brewing in another project.
The bx seed command of Libbitcoin Explorer version 3.x used the MT19937 pseudo-random number algorithm combined with 32-bit system time as a seed, generating a key space with only 2^32 combinations.
Hackers quickly began exploratory attacks, and from May 2023, multiple small thefts appeared on-chain. On July 12, the attacks peaked, with a large number of wallets generated by bx being drained simultaneously. On July 21, Milk Sad researchers found the root of the problem while helping users investigate losses; it was indeed the weak randomness of bx seed that allowed private keys to be brute-forced. They promptly reported this to the Libbitcoin team.
However, since this command was regarded as a testing tool by the official team, initial communication was not smooth. The team ultimately bypassed the project party and publicly disclosed the vulnerability on August 8, applying for a CVE number.
It was only after this discovery in 2023 that the Milk Sad team began to reverse-engineer historical data. They were astonished to find that the weak key range that had accumulated massive funds between 2019 and 2020 was linked to Lubian and that the significant transfer mentioned earlier occurred on December 28, 2020.
At that time, approximately 136,951 bitcoins resided in these weak wallets, and the large-scale outflow that day was valued at about $3.7 billion, with the last known movement being a wallet consolidation in July 2024.
In other words, the suspicious aspects of the Lubian incident only emerged after the weak randomness vulnerability was exposed. The missed alarm window has long passed, and the whereabouts of the bitcoins at that time have vanished without a trace. Five years later, it was only when the U.S. Department of Justice (DOJ) and British authorities jointly prosecuted the Prince Group and Chen Zhi that things began to take shape.
For us, the phrase "Not your Wallet, Not Your Money" can only take effect under the premise of randomness.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。


