Original Title: Crypto's Privacy Powerhouses
Original Author: @blocmates
Translated by: Peggy, BlockBeats
Editor's Note:
In the technological evolution of the crypto world, privacy has never truly left the stage. Today, as on-chain activities become more frequent and the user base continues to expand, privacy has once again become an unavoidable core issue.
From the idealism of cypherpunks to the implementation of technologies like zero-knowledge proofs, fully homomorphic encryption, and multi-party computation, to the gradual maturation of a series of user-oriented privacy applications, we are witnessing an era of "privacy reformation."
This article attempts to answer a simple yet important question: In a world where all actions may be recorded, analyzed, and tracked on-chain, how do we retain our own space?
Here is the original text:
Privacy in Crypto: The Starting Point of Freedom
If history can provide a reference, freedom always finds a way to win. In the realm of crypto, betting on privacy is essentially betting on freedom.
Hey, let's be real, as long as you have on-chain investigative capabilities (and patience) like ZachXBT, crypto transactions can be tracked—you already knew that, right?
Nowadays, we can even find out who emptied your wallet: it could be a 78-year-old grandmother or those North Korean hacker groups that keep the entire crypto community on edge.

Yes, the aforementioned "bad cases" do exist, but they can be exposed because on-chain activities are public.
That's right, the so-called "public ledger" is indeed public.
While today's younger generation may not fully understand, those "old crypto folks" know well: the origin of Bitcoin and the entire crypto world actually stems from the cypherpunk movement—a vision built on privacy to create an open society.
It was this ideology that gave birth to David Chaum's privacy-oriented digital currency Digicash, which utilized blind signature technology; it also led to Wei Dai's proposal of the anonymous, decentralized payment system b-money (sounds like a rapper's name, right?).
Later, Satoshi took a step further by embedding a degree of privacy design within a completely transparent ledger. Bitcoin relies on pseudonymous addresses and cryptographic hashes, rather than real names or identity information, creating an illusion of "anonymity."
But this illusion did not last long. With the rise of smart contracts, attention began to shift towards programmability, and privacy gradually became marginalized.
Now, with the resurgence of crypto, we return to the initial question: Is privacy still a core principle of the crypto world?
Discussions about privacy are no longer limited to "sending and receiving funds on a public ledger," but have extended to various layers of on-chain applications.
In today's article, we will explore what privacy means in the crypto world, what dimensions it encompasses, what products are built around privacy, what we should pay attention to, and our thoughts on the future of crypto privacy.
Buckle up, let's get started.
What Does Privacy Mean in Crypto?
The best way to understand privacy is to look at it from the perspective of traditional finance (TradFi).
In the traditional financial system, privacy means that your personal data will not be made public, and only authorized institutions can view it. This includes your biometric information, transaction records, account balances, and more.
In the crypto world, the core idea of privacy is: to protect users' personal data in on-chain transactions. True privacy means that data is only visible and understandable to the user themselves or their authorized parties.
Many people confuse "privacy" with "anonymity." In crypto culture, anonymity is indeed closely related to privacy, but the two are technically distinct.
For example, privacy focuses on hiding transaction details, such as transfer amounts, the parties involved, and other relevant information; whereas anonymity refers to hiding the identities of the transaction participants.
A clear comparison is Zcash and Monero. Zcash uses cryptographic techniques (like zk-SNARKs) to hide transaction amounts; while Monero employs stealth addresses and ring signature technology to pseudonymize identity information.
However, for the purpose of this article, we will consider privacy as a broader concept that also includes anonymity.
Why is Privacy an Important Issue in the Crypto World?
As mentioned earlier, the foundation of the crypto industry comes from the spirit of cypherpunk—a pursuit of privacy and decentralization aimed at escaping state-level control and achieving true freedom.
But today, with the rapid expansion of private surveillance companies, the increasing influence of finance, and the risks of data abuse brought about by AI technology, the alarm bells regarding privacy are ringing louder than ever.

Without privacy protection, data on the blockchain could expose users' spending habits, wealth distribution, political donation records, and transaction relationships—once this information falls into the wrong hands, it could be used for extreme manipulation or exploitation.
Another crucial reason why privacy is vital in the crypto space is that without privacy technology, crypto cannot truly achieve censorship resistance.
Privacy can protect individuals and organizations from coercion, allowing them to participate freely in the on-chain financial system without permission.
Privacy also ensures users' safety in real life and the security of on-chain data. Especially in cases where public transaction graphs may expose high-value targets, users face risks of being hacked, extorted, or even threatened—such incidents have become increasingly common in recent years.
Privacy-Enhancing Technologies (PETs)
There are many ways to achieve privacy, with each technology designed for specific use cases, but their ultimate goal is the same: to provide privacy protection and data security for end users.
Different technologies have their own advantages, trade-offs, and levels of adoption. Below, we introduce several mainstream privacy-enhancing technologies (PETs) and their working principles in non-technical language:
1. Zero-Knowledge Proofs (ZK)
As the name suggests, zero-knowledge proofs are a technology that can "prove something is true without revealing specific details."
This mechanism involves two roles: the prover is responsible for proving a statement is true; the verifier confirms its validity without accessing the underlying data.
ZK is a cryptographic privacy-enhancing technology, mainly in two forms: zkSNARKs (succinct non-interactive zero-knowledge proofs); zkSTARKs (scalable transparent zero-knowledge proofs).
ZK technology supports various privacy application scenarios, such as: confidential transactions (hiding transaction amounts); asset proofs (without exposing addresses or sensitive data); privacy verification in decentralized identity systems; private smart contracts, etc.
2. Ring Signatures / Ring Confidential Transactions (RingCT)
If you've heard of privacy-focused cryptocurrencies that have privacy protection enabled by default, they likely use ring signature technology. The most typical example is Monero, a so-called "dinosaur-level" privacy coin.
The principle of ring signatures is: users can initiate transactions within a group without revealing the specific signer, thus hiding the sender's identity through mixed transactions.
This method is very suitable for achieving anonymity, allowing users to transact on-chain without worrying about being tracked by a ZachXBT-like on-chain detective.
Because of this, Monero has faced several compliance challenges, such as being delisted by exchanges and facing regulatory pressure. In contrast, Zcash offers both transparent addresses (t-address) and privacy addresses (z-address), allowing exchanges to support only transparent transactions to meet compliance requirements.
3. Fully Homomorphic Encryption (FHE)
If you ever passed notes in high school that contained encrypted characters only your friends could decipher, you have already encountered the basic concept of FHE.
FHE is a cryptographic technology that allows computation to be performed without decrypting the data.
This means users can send sensitive data without worrying that the verifier will see the specific content.
Although FHE leans more towards privacy protection rather than anonymity, it is one of the most powerful technologies for on-chain privacy currently available.
4. Trusted Execution Environments (TEE)
If you are a long-time reader of blocmates, you may already be familiar with TEE. We previously wrote an article explaining its principles.
TEE is a hardware-based privacy-enhancing technology that protects data through secure isolation areas (enclaves) in processors or networks, using encryption keys to ensure data confidentiality and integrity.
A common example is the facial recognition feature on smartphones:
When you set up facial recognition, the device captures your facial features through the camera, encrypts them, and transmits them to the TEE for processing. The raw data does not leave the TEE in plaintext. Inside the TEE, this data is converted into a mathematical template and securely stored for subsequent identity verification.
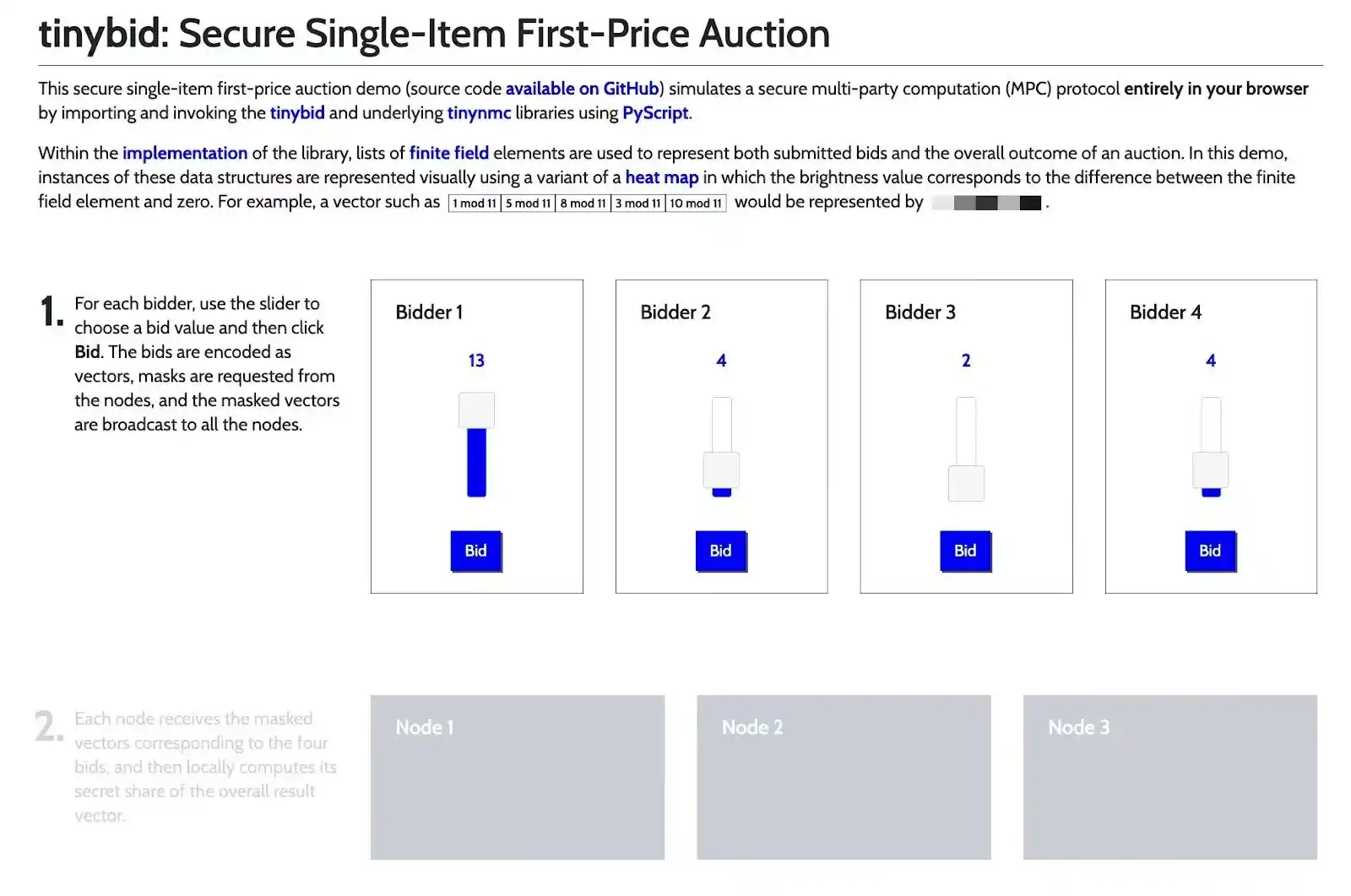
5. Multi-Party Computation (MPC)
In the crypto world, some operations require collaboration among multiple parties. MPC is specifically designed for this purpose.
For example, an AI product may need multiple models to collaborate in reasoning to optimize results; a DAO may want to make governance decisions without exposing each member's vote; or an on-chain auction may need to complete bidding without revealing the bids—these are typical application scenarios for MPC.
MPC allows multiple participants to jointly compute a function (such as signing transactions or verifying balances) without exposing their individual input data.
In addition to the previously mentioned privacy-enhancing technologies (PETs), there are other methods, such as coin mixers, homomorphic encryption, and composable privacy. The latter combines multiple privacy tools to achieve stronger protection.
Some projects focus on directly building products based on these cryptographic technologies, while others are dedicated to establishing underlying privacy infrastructure to support crypto applications.
Key Privacy Infrastructure Projects
The ways to achieve crypto privacy are diverse, and there is no one-size-fits-all solution for all scenarios.
This means that different projects or teams will focus on different dimensions of PETs, building for specific applications and use cases. Here are some noteworthy privacy infrastructure projects:
1. Nillion
We previously wrote an article introducing Nillion's technology and application scenarios, which you can explore if you're interested.
In simple terms, @nillion's infrastructure is dedicated to decentralized trust mechanisms for sensitive data. Its core technology, the "Blind Computer," achieves data security through various PETs, specifically including multi-party computation (MPC) for NilDB and trusted execution environments (TEE) for AI inference (NilAI/NilCC).
Nillion is also developing some very interesting consumer applications on its infrastructure, which we will introduce later.
2. Succinct
The airdrop from @SuccinctLabs may have changed the fate of some people and left others dissatisfied, but their technology is indeed worth paying attention to.
Succinct Labs promotes zero-knowledge proofs (ZK), allowing for proofs of any software. While this is not focused on privacy, its core product—the SP1 ZK virtual machine—can be used for client-side privacy protection.
For example, Hibachi uses this technology to achieve privacy processing of order flow: while the central operator (Hibachi) can still see the data, external observers cannot access it.
3. Zama
@zama_fhe is a leader in FHE (fully homomorphic encryption) technology, focusing on supporting confidential applications.
Zama has built a confidential blockchain protocol that can integrate with Solidity networks, supporting privacy-focused DEX trading, confidential lending protocols, and tokenized applications with built-in privacy.
4. Zcash
To be honest, Mert is successfully "waking up" @Zcash (ZEC) and is campaigning for the annual KOL.
Zcash is one of the OG projects in the crypto privacy space, being the first to use ZK encryption for peer-to-peer confidential payments. It employs zkSNARKs to enable optional privacy transactions (shielded transactions).
The technology itself is not complex, but combined with a token economic model similar to Bitcoin, Zcash has gained renewed attention as privacy becomes a focal point again, especially among those who still believe in the cypherpunk spirit.
5. Monero
In addition to having a "believer" community due to its token (XMR), @monero itself is also a privacy technology project worth noting.
Monero achieves complete transaction privacy through three cryptographic techniques:
(1) Ring signatures: mixing the real signer with a group of decoy signers to hide the sender's identity;
(2) Stealth addresses: generating a one-time address for each transaction to avoid linking the receiving address with the wallet;
(3) Ring Confidential Transactions (RingCT): hiding transaction amounts through cryptographic commitments and range proofs while ensuring inputs equal outputs to prevent minting out of thin air.
Unlike Zcash, Monero's privacy is mandatory, with no concept of "optional shielding." This has led to significant compliance pressure, resulting in many centralized exchanges delisting it.
6. Arcium
Remember we mentioned that privacy is not a "one-size-fits-all" solution, especially at the infrastructure level?
@Arcium understands this very well.
Arcium is a multi-party computation network that has built several protocols. One of the general protocols is called Cerberus, which employs a very interesting security model.
Cerberus operates under a "non-honest majority" trust model, featuring cheat detection and identifiable abort mechanisms. This means that as long as one node is honest, privacy can be guaranteed. The system can also identify dishonest nodes, expelling and punishing them.
This contrasts sharply with most protocols that require an "honest majority" (i.e., more than 51% of nodes being honest).
Another protocol called Manticore is designed specifically for AI scenarios. Although its security assumptions are not as strong as Cerberus, it is suitable for environments with access control, such as AI training in trusted settings.
Like Nillion, Arcium also supports some very interesting consumer applications, which we will introduce in the next section.
Consumer Projects Built on Privacy Infrastructure
One of the charms of crypto privacy is that it is not just an abstract concept at the technical level, but also products that users can genuinely experience.
We don't need to operate the underlying code like developers, but we can directly use these applications built on privacy infrastructure and feel the experiences they bring.
Here are some noteworthy consumer privacy applications:
1. Hibachi: Privacy-Focused Contract Trading
Not everyone is willing to have their holdings or liquidation records made public.
Remember the James Wynn incident? Whether he was a pawn in a larger game or it was indeed the case, he was "hunted" and liquidated because his holdings on Hyperliquid were made public. This indicates that on-chain contract trading indeed requires privacy protection.
@hibachi_xyz is using Succinct's ZK technology (SP1) and Celestia's data availability (DA) module to create a new architecture that integrates on-chain and off-chain, verifying CLOB (central limit order book) on Celestia's blob.
As a privacy project, Hibachi has also optimized execution speed, with a latency of only 5 milliseconds. It has not yet issued tokens and is worth keeping an eye on.
2. NilGPT: Privacy-First AI Chatbot
To be honest, AI can sometimes be a bit unsettling… especially when it starts referring to itself as "I."
But the technology itself is indeed cool, especially with the various tricks people play with prompts.
However, many people tend to "overshare" when using AI chatbots, forgetting that behind these conversations are the "watchful eyes" of centralized systems like ChatGPT, Gemini, and Grok.
NilGPT is an AI chatbot supported by Nillion's privacy infrastructure, designed to protect users' conversation privacy. Users can interact with the AI with peace of mind, without worrying about their data being collected or analyzed by third parties.

This is exactly @nilgpt_'s positioning—a privacy-focused AI chatbot built on Nillion's confidential computing infrastructure, aimed at ensuring the security of user conversations and data, without collecting or exposing any personal information.
NilGPT uses Nillion's Blind Compute Layer to encrypt and process data across distributed nodes, ensuring that no single entity can access plaintext inputs or outputs.
3. Railgun: On-Chain Anonymity Shield
If you want to achieve true anonymity on the blockchain, Railgun is a choice worth considering (quietly, it is also one of the privacy projects supported by Vitalik).
@RAILGUN_Project is an on-chain privacy ecosystem based on zero-knowledge encryption, designed as a smart contract system suitable for Ethereum-compatible chains, supporting private transactions and DeFi operations without sacrificing security or composability.
Railgun is fully decentralized, governed by the Railgun DAO, and uses zk-SNARKs technology to encrypt balances, transactions, and smart contract executions on-chain, currently supporting chains like Ethereum, Polygon, BSC, and Arbitrum.
It is important to note that, unlike traditional coin mixers, Railgun achieves complete anonymity through ZK encryption while seamlessly integrating with existing dApps and liquidity systems.
4. Privy Home: Privacy-Friendly Wallet Management Hub
To be honest, Privy may be one of the projects in the crypto space that is closest to "product-market fit."
Developed by @privy_io, Privy Home is a secure control layer and unified management hub for managing embedded wallets across different crypto applications. It provides foundational wallet infrastructure for on-chain experiences, helping users securely manage identities and assets across multiple applications.

Privy allows users to track, recharge, and manage assets from multiple applications on a single platform, employing key sharding and trusted execution environment (TEE) technology to ensure security.
It enhances the self-custody experience and cross-application interoperability, making wallet management smoother while avoiding exposing keys to the applications themselves.
5. Umbra: Stealth Mode on Solana
This year, Solana has become the main stage for on-chain entertainment—capital flows are active, and opportunities abound. But with this comes increasing attention, surveillance, and scrutiny of user behavior.
This is precisely why products like @UmbraPrivacy have become important.
Umbra is a privacy protocol that provides "stealth mode" for Solana, enabling on-chain private transfers through Arcium's confidential network, allowing users to truly have financial privacy on Solana.
Currently, Umbra has launched its private transfer feature and will continue to build a more complete Solana privacy DeFi hub, including private swaps, a Solana-Zcash cross-chain bridge, and an SDK for native integration of privacy features in wallets and other programs.
If you are a wallet observer, you might hate it; but if you are someone truly participating in on-chain games, Umbra is worth your anticipation.
6. Zashi App: Privacy Gateway for Zcash Users
If you have been "woken up" by the "red pill" and are seriously considering purchasing $ZEC, the next step is to download and use @zashi_app.
Zashi is a mobile wallet developed by Electric Coin Co. (ECC), the founding team of Zcash in 2016. Zashi is specifically designed for Zcash, focusing on shielded, privacy-protecting transaction experiences.
It is a self-custody wallet, allowing users to freely send, receive, and use $ZEC without relying on intermediaries, governments, or corporations, avoiding activity tracking.
Zashi has the shielding feature enabled by default, utilizing Zcash's zero-knowledge encryption technology to achieve end-to-end privacy protection for peer-to-peer payments, making it the most convenient entry tool for Zcash users.
To be honest, I downloaded this app myself, and the interface is very clean and smooth, definitely worth a try.
7. Privacy is Not an Add-On, but the Core of Crypto
The walls of traditional systems are tightening, and the migration on-chain has quietly begun.
While the adoption may seem slow, the transition from 0 to 1 is always the hardest stage, and the leap from 1 to 10 will be much faster. In other words, as progress continues, even your grandmother starts going on-chain, privacy—whether hers or yours—becomes increasingly important.
We believe that privacy is not just a "nice-to-have" feature. It is foundational and must be treated as a core value. This should also be the way you view it in the short and long term.
Related infrastructure is being built, some of which are already online and have proven their feasibility through practical applications.
To stay in the loop, it might be worth following these integrated solutions to see which can solve your practical needs like AWS, or at least allow you to truly become an "anonymous user" on-chain.
If history can serve as a reference, freedom always finds a way to prevail. And in the crypto world, betting on privacy is essentially betting on freedom.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




