Written by: Yue Xiaoyu
If you want to survive in the cryptocurrency industry for a long time, you must choose the right wallet and use it correctly!
Wallets are the most important infrastructure products in our industry, and it cannot be overstated how crucial they are.
Hackers often take advantage during bear markets; for instance, Trust Wallet, a well-known wallet under Binance, was hacked for 7 million dollars, and recently, the famous trading bot DeBot also reported being hacked.
As ordinary users, what should we do?
As a product manager who has been working on wallets for many years, I would like to share a few important principles:
- When choosing a wallet, you must recognize leading platforms and pay special attention to whether they have compensation guarantees!
This does not mean that wallets from small teams are unusable, but leading platforms like Binance, OKX, and Bitget generally have dedicated security compensation funds.
For example, in the case of the Trust Wallet hack, the official team has clearly stated that they will fully compensate users for their losses using the SAFU fund.
However, small team wallets simply do not have this safety net; if you lose money, the likelihood is that there will be no compensation at all.
To be honest, creating a wallet is a tough and labor-intensive job, suitable for companies with resources and technical strength.
Of course, the rewards can be quite substantial, as they directly control user traffic entry.
- The security of browser extension wallets is significantly lower; do not store large assets in them!
The recent hack involved the extension version, as the private keys are stored locally in the browser, and the permissions between extensions are highly interconnected, making them vulnerable to malicious code and phishing websites.
Attackers only need to lure users to visit a malicious website to exploit the architectural flaws of the browser extension and trigger vulnerabilities to steal assets;
Apps require users to actively download malicious installation packages, which raises the attack threshold.
Therefore, extension wallets should only be used as small interaction tools, containing just enough gas fees for a few DApp interactions.
- Avoid using pseudo-decentralized wallets and trading tools that require you to entrust your private keys!
This point directly corresponds to the DeBot hacking incident.
As a well-known trading bot, DeBot's core issue was that many users entrusted their private keys to the platform for so-called automated efficient trading.
This is actually very susceptible to security attacks, leading to asset losses.
Remember, whether it's a wallet or a trading bot, as long as it requires you to entrust your private keys, the security level is extremely low.
This is akin to handing your wallet keys directly to someone else, which maximizes the risk; such tools must be used with caution.
Based on industry experience, I would like to share the most core and reliable protection scheme: a three-layer wallet system of cold, warm, and hot wallets.
This is currently the most verified method to protect asset security to the greatest extent, and many institutions are configured this way.
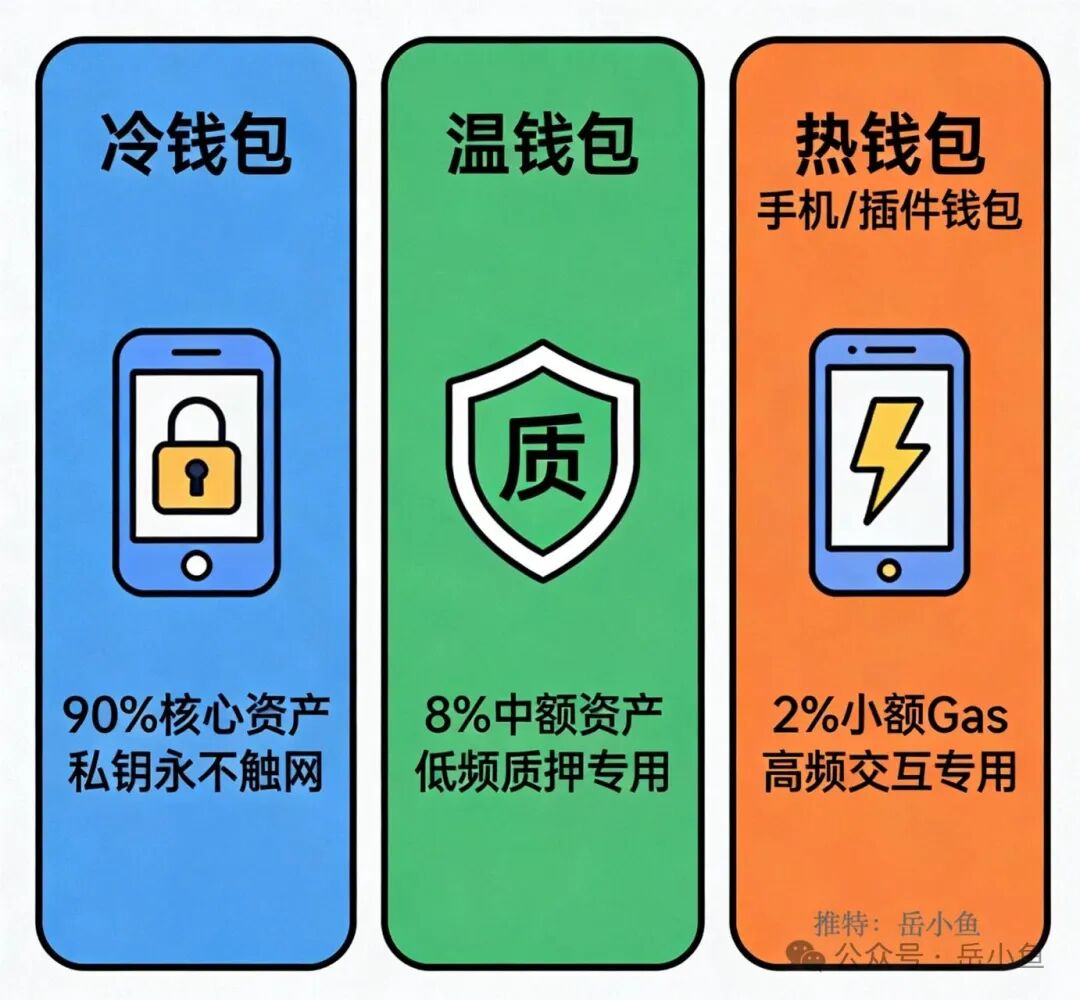
First layer: Cold wallet, which can serve as a storage for large assets.
It is recommended to store over 90% of your core assets here, preferably using leading hardware cold wallets like Ledger or Trezor.
Its core advantage is physical isolation; the private keys are never connected to the internet, making it impossible for hackers to steal the private keys online.
A reminder: when backing up your mnemonic phrase, be sure to use a medium like a metal plate that is resistant to drops and loss, and store it in secure locations. Never keep it on your phone or take photos to store in the cloud!
Second layer: Warm wallet, serving as a medium-sized staking storage.
Create a dedicated wallet solely for staking and locking operations, which are low-frequency actions.
The key point is that this wallet must not be imported into any third-party platforms, and do not click on unknown DApp links; maintain a low activity status to reduce risk exposure.
After all, the funds staked usually have long cycles, and safety is the top priority.
Third layer: Hot wallet, which is for small interaction storage.
Common mobile wallets and the aforementioned browser extension wallets fall into this category.
Only a small amount of gas fees should be stored here for daily DApp interactions and small transfers, which are high-frequency operations.
Even if this wallet is hacked, the small amount will not affect our core assets, effectively trading a small amount of money for safety.
Finally,
In the Web3 industry, asset security comes first; otherwise, you end up making a gift for hackers.
Choose leading wallets with compensation, treat extension wallets as small tools, avoid using tools that require you to entrust your private keys, and implement a three-layer system of cold, warm, and hot wallets for asset isolation. This way, you can minimize the risk of falling into traps.
If anyone has additional security experiences, feel free to share!
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



