Author: Beosin
Introduction
This research report is initiated by the Blockchain Security Alliance and co-authored by alliance members Beosin and Footprint Analytics. It aims to comprehensively explore the global blockchain security landscape in 2025. Through analysis and assessment of the current state of blockchain security worldwide, the report will reveal the security challenges and threats faced today, and provide solutions and best practices. Blockchain security and regulation are key issues in the development of the Web3 era. Through in-depth research and discussion in this report, we can better understand and address these challenges to promote the security and sustainable development of blockchain technology.
1. Overview of Web3 Blockchain Security Landscape in 2025
According to monitoring by Beosin's Alert platform, a blockchain security and compliance technology company, the total losses in the Web3 sector due to hacker attacks, phishing scams, and project rug pulls reached $3.375 billion in 2025. There were a total of 313 major blockchain security incidents, including 191 hacker attacks, with total losses amounting to approximately $3.187 billion; project rug pulls resulted in total losses of about $11.5 million; and there were 113 phishing scams, with total losses of approximately $177 million.
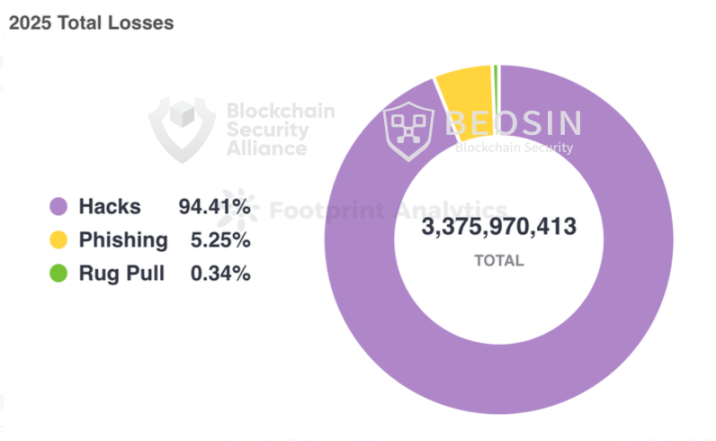
The losses in Q1 2025 were the most severe, with the majority stemming from the Bybit hacking incident. The amount lost due to hacker attacks decreased each quarter, but saw a significant increase compared to 2024, with a rise of 77.85%; losses from phishing scams and project rug pulls significantly decreased compared to 2024, with phishing scam losses dropping by approximately 69.15% and rug pull losses decreasing by about 92.21%.
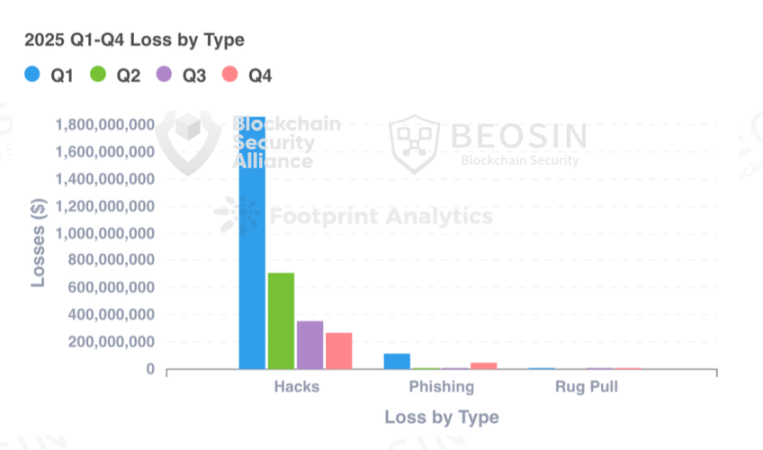
The types of projects attacked in 2025 included various categories such as DeFi, CEX, public chains, cross-chain bridges, NFT, Memecoin trading platforms, wallets, browsers, third-party code packages, infrastructure, and MEV bots. DeFi remained the most frequently attacked project type, with 91 attacks resulting in losses of approximately $621 million. CEX had the highest total loss amount, with 9 attacks resulting in losses of about $1.765 billion, accounting for 52.30% of the total losses.
In 2025, Ethereum continued to be the public chain with the highest losses, with 170 security incidents on Ethereum causing approximately $2.254 billion in losses, representing 66.79% of the total annual losses.
In terms of attack methods, the Bybit incident caused losses of approximately $1.44 billion due to a supply chain attack, accounting for 42.67% of the total losses, making it the most damaging attack method. Additionally, contract vulnerability exploitation was the most frequently occurring attack method, with 62 out of 191 attack incidents stemming from contract vulnerabilities, accounting for 32.46%.
2. Top 10 Security Incidents of 2025
In 2025, there were 3 security incidents with losses exceeding $100 million: Bybit ($1.44 billion), Cetus Protocol ($224 million), and Balancer ($116 million). Following these were Stream Finance ($93 million), BTC Whale ($91 million), Nobitex ($90 million), Phemex ($70 million), UPCX ($70 million), Ethereum users ($50 million), and Infini ($49.5 million).
Unlike previous years, this year’s top 10 security incidents included 2 cases of significant losses for individual users, caused by social engineering/phishing attacks. Although such attacks were not the most damaging in terms of loss amount, their frequency has been on the rise each year, becoming a major threat faced by individual users.
3. Types of Attacked Projects
Centralized exchanges became the project type with the highest losses
The project type with the highest losses in 2025 was centralized exchanges, with 9 attacks resulting in approximately $1.765 billion in losses, accounting for 52.30% of the total losses. The exchange with the largest loss was Bybit, with losses of about $1.44 billion. Other exchanges with significant losses included Nobitex (approximately $90 million), Phemex (approximately $70 million), BtcTurk ($48 million), CoinDCX ($44.2 million), SwissBorg ($41.3 million), and Upbit ($36 million).
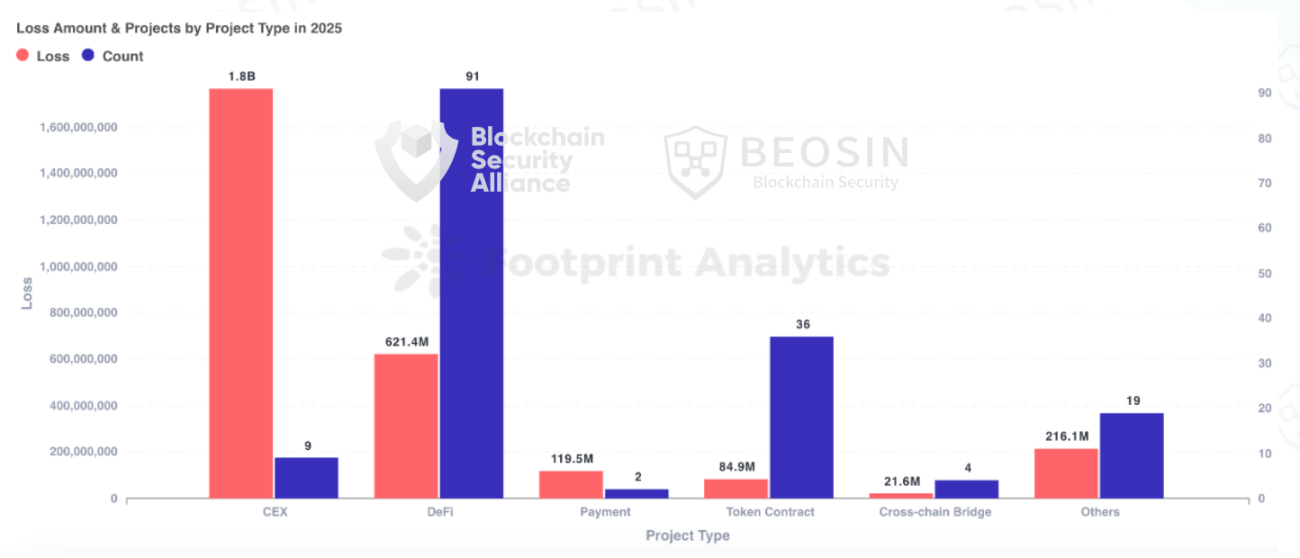
DeFi was the project type with the highest frequency of attacks, with 91 attacks resulting in losses of approximately $621 million, ranking second in terms of loss amount. Among them, Cetus Protocol was hacked for about $224 million, accounting for 36.07% of the stolen funds in DeFi. Balancer suffered losses of approximately $116 million, while other DeFi projects with significant losses included Infini (approximately $49.5 million), GMX (approximately $40 million), Abracadabra Finance ($13 million), Cork Protocol (approximately $12 million), Resupply (approximately $9.6 million), zkLend (approximately $9.5 million), Ionic (approximately $8.8 million), and Alex Protocol (approximately $8.37 million).
4. Loss Amounts by Chain
Ethereum is the chain with the highest losses and the most security incidents
As in previous years, Ethereum remained the public chain with the highest losses and the most security incidents. 170 security incidents on Ethereum caused approximately $2.254 billion in losses, accounting for 66.79% of the total annual losses.

The second-ranked public chain in terms of the number of security incidents was BNB Chain, with 64 incidents resulting in approximately $89.83 million in losses. BNB Chain experienced many on-chain attacks, with relatively smaller loss amounts, but compared to 2024, both the number of security incidents and the loss amounts increased significantly, with losses rising by 110.87%.
Base ranked third in terms of the number of security incidents, with a total of 20 incidents. Solana followed closely with 19 incidents.
5. Analysis of Attack Methods
Contract vulnerability exploitation was the most frequently occurring attack method
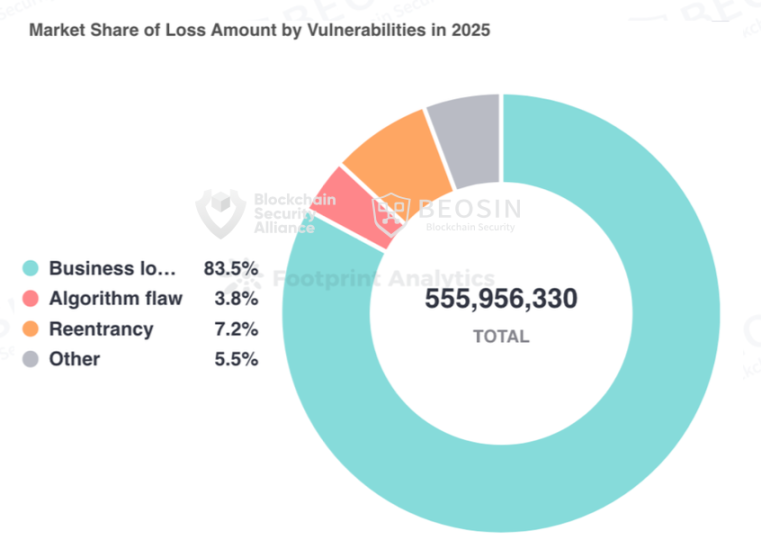
Out of 191 attack incidents, 62 were due to contract vulnerability exploitation, accounting for 32.46%, resulting in total losses of $555.6 million, making it the second most damaging type of attack after the Bybit supply chain attack.
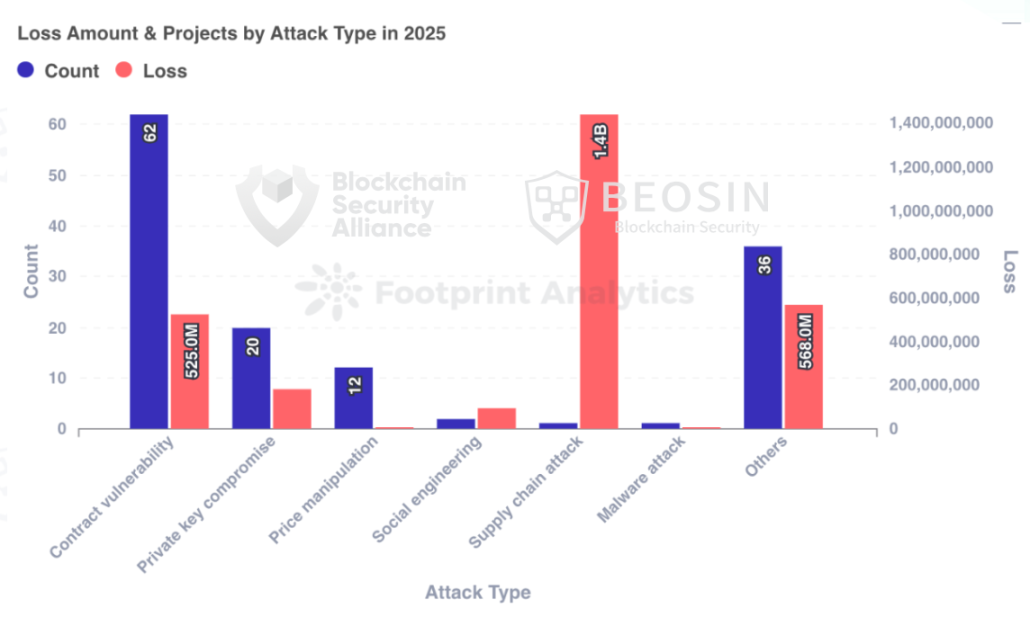
In terms of specific contract vulnerabilities, the most damaging vulnerability was the business logic flaw, with total losses amounting to $464 million. The top three most common contract vulnerabilities were business logic flaws (53 incidents), access control flaws (7 incidents), and algorithmic defects (5 incidents).
This year, there were a total of 20 private key leakage incidents, with total losses of approximately $18 million, significantly reduced in both frequency and loss amounts compared to last year. Exchanges, project teams, and users have shown improved awareness of private key protection.
6. Analysis of Typical Security Incident Attacks
6.1 Cetus Protocol $224 Million Security Incident Analysis
Incident Overview
On May 22, 2025, the DEX Cetus Protocol on the Sui ecosystem was attacked, with the vulnerability stemming from an implementation error in the left shift operation in the open-source library code. Taking one of the attack transactions (https://suivision.xyz/txblock/DVMG3B2kocLEnVMDuQzTYRgjwuuFSfciawPvXXheB3x?tab=Overview) as an example, the simplified attack steps are as follows:
Enable flash loan: The attacker borrowed 10 million haSUI through a flash loan.
Create liquidity position: A new liquidity position was opened with a price range of [300000, 300200].
Increase liquidity: Only 1 unit of haSUI was used to increase liquidity, but it gained a liquidity value of up to 10,365,647,984,364,446,732,462,244,378,333,008.
Remove liquidity: Immediately remove liquidity from multiple transactions to deplete the liquidity pool.
Repay flash loan: Repay the flash loan and retain approximately 5.7 million SUI as profit.
Vulnerability Analysis
The root cause of this attack was an implementation error in the checkedshlw function within the getdelta_a function, leading to a failure in overflow checks. The attacker only needed a small amount of tokens to exchange for a large amount of assets in the liquidity pool, thus executing the attack.
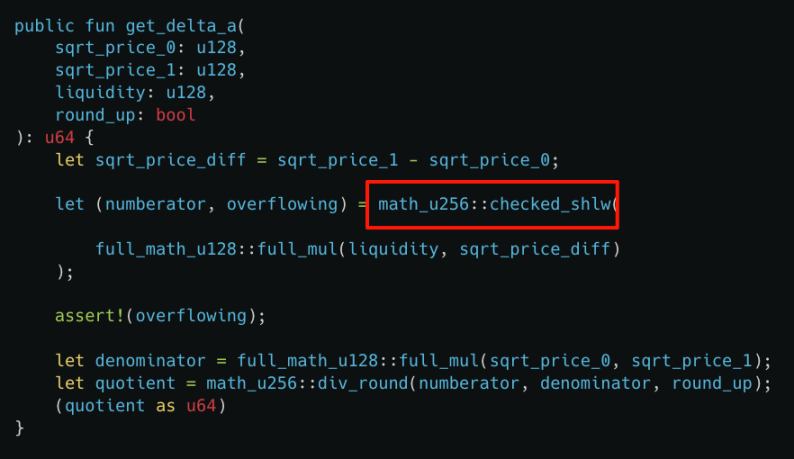
As shown in the figure, checked_shlw is used to determine whether left-shifting a u256 number by 64 bits will cause an overflow. Input values less than 0xffffffffffffffff can bypass the overflow check, but the input value may exceed the maximum u256 value (overflow) after being left-shifted by 64 bits, while checked_shlw will still output that no overflow has occurred (false). This can lead to a serious underestimation of the required token amount in subsequent calculations.
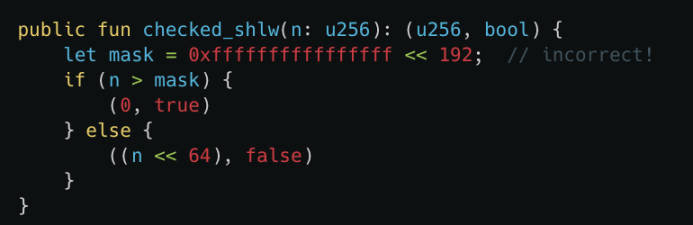
Additionally, in Move, the safety of integer operations is designed to prevent overflow and underflow, as these can lead to unexpected behavior or vulnerabilities. Specifically, if the result of addition and multiplication is too large for the integer type, it will cause the program to abort. If the divisor is zero, division will abort.
The uniqueness of left-shifting is that it does not abort when an overflow occurs. This means that even if the number of shifted bits exceeds the storage capacity of the integer type, the program will not terminate, potentially leading to erroneous values or unpredictable behavior.
6.2 Balancer $116 Million Security Incident Analysis
On November 3, 2025, the Balancer v2 protocol was attacked, resulting in losses of approximately $116 million across multiple projects, including its fork protocol, on various chains. Taking the attack transaction by the attacker on Ethereum as an example: 0x6ed07db1a9fe5c0794d44cd36081d6a6df103fab868cdd75d581e3bd23bc9742
The attacker first initiated the attack transaction through the batch swap function, using BPT to exchange a large amount of liquidity tokens from the pool, causing the liquidity token reserves of the pool to become very low.
The attacker then began swapping liquidity tokens (osETH/WETH).
The attacker then swapped the liquidity tokens back to BPT tokens and repeatedly performed the above operations across multiple pools.
Finally, the attacker withdrew the funds to realize profits.
Vulnerability Analysis
ComposableStablePools uses Curve's StableSwap invariant formula to maintain price stability between similar assets. However, scaling operations performed during invariant calculations can introduce errors.
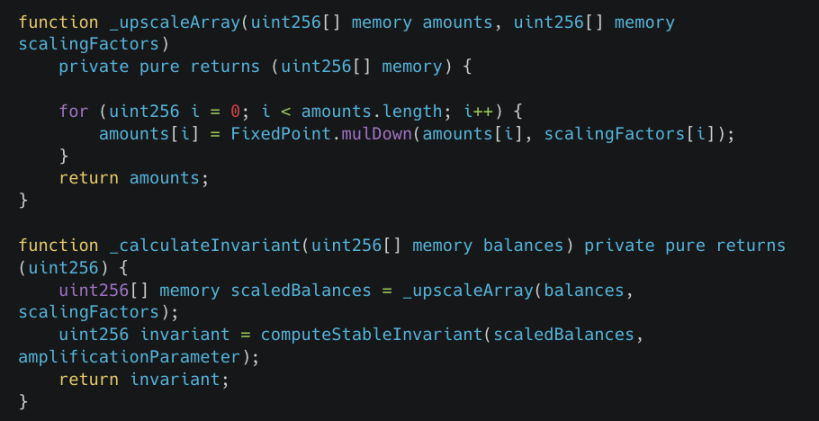
The mulDown function performs integer division with rounding down, and this precision error propagates into the invariant calculations, leading to a significant reduction in computed values, thus creating profit opportunities for the attacker.
7. Anti-Money Laundering Case Analysis
7.1 U.S. Sanctions Against Drug Trafficking Group Led by Ryan James Wedding
According to information disclosed by the U.S. Treasury Department, Ryan James Wedding and his team smuggled several tons of cocaine through Colombia and Mexico to be sold in the United States and Canada. Their criminal organization utilized cryptocurrency for money laundering to clean large amounts of illegal wealth.
Using Beosin's on-chain tracking and investigation tool, Beosin Trace, an analysis of cryptocurrency addresses associated with Wedding's drug trafficking group was conducted, with the results shown below:
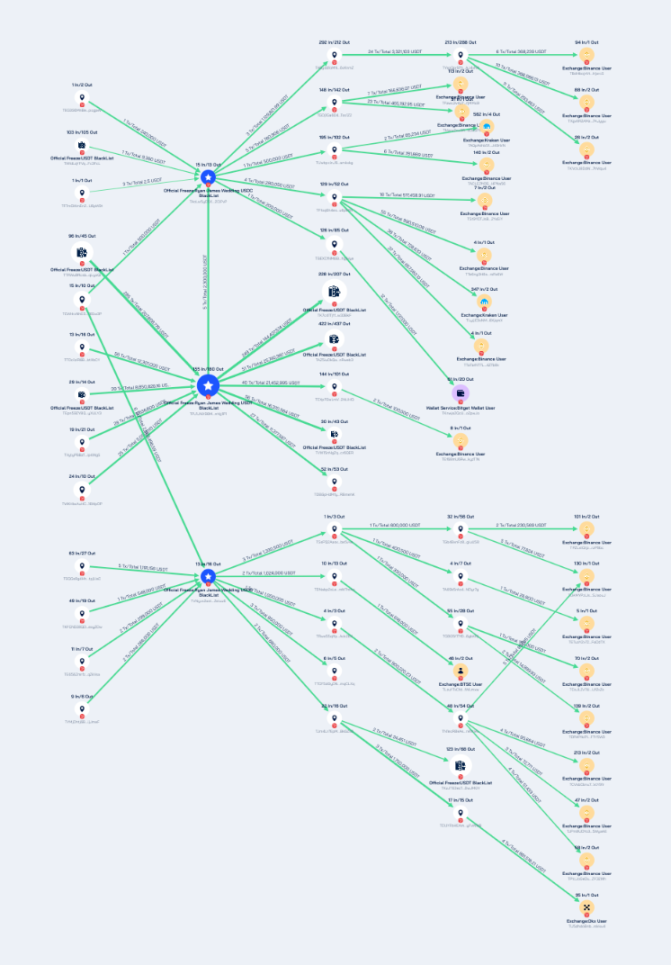
The three addresses held by Wedding, TAoLw5yD5XUoHWeBZRSZ1ExK9HMv2CiPvP, TVNyvx2astt2AB1Us67ENjfMZeEXZeiuu6, and TPJ1JNX98MJpHueBJeF5SVSg85z8mYg1P1, transacted a total of 266,761,784.24 USDT, with some assets frozen by Tether officials, but most assets were laundered through high-frequency trading addresses and multi-level transfers, deposited into platforms such as Binance, OKX, Kraken, and BTSE.
Their gang member Sokolovski held addresses across multiple blockchain networks (BTC, ETH, Solana, TRON, BNB Beacon Chain), and the analysis of fund flows can be viewed in the full report.
7.2 GMX $40 Million Theft Case
On July 10, 2025, GMX was attacked due to a reentrancy vulnerability, resulting in the hacker profiting approximately $42 million. Beosin Trace tracked the stolen funds and found that the attacker's address 0x7d3bd50336f64b7a473c51f54e7f0bd6771cc355 exchanged various stablecoins and altcoins for ETH and USDC through a DEX protocol after profiting, and transferred the stolen assets to the Ethereum network via multiple cross-chain protocols.
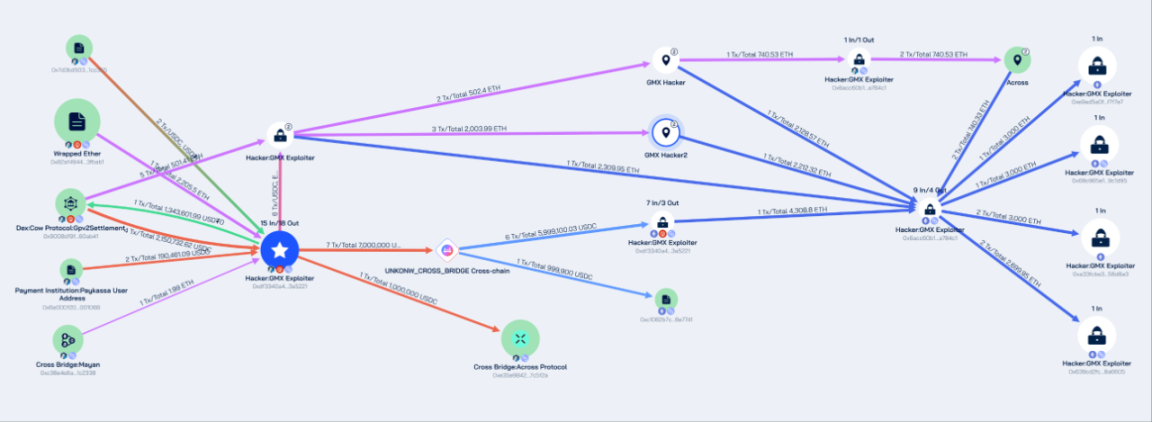
Subsequently, approximately $32 million worth of ETH from the stolen GMX assets was stored in the following four Ethereum network addresses:
0xe9ad5a0f2697a3cf75ffa7328bda93dbaef7f7e7
0x69c965e164fa60e37a851aa5cd82b13ae39c1d95
0xa33fcbe3b84fb8393690d1e994b6a6adc256d8a3
0x639cd2fc24ec06be64aaf94eb89392bea98a6605
Approximately $10 million worth of assets were stored in the Arbitrum network address 0xdf3340a436c27655ba62f8281565c9925c3a5221.
The fund laundering path in this incident is very typical, as the hacker obscured and hid the path of the funds through DeFi protocols, cross-chain bridges, etc., to evade tracking and freezing by regulatory agencies and law enforcement.
8. Summary of the Web3 Blockchain Security Landscape in 2025
In 2025, the monetary losses caused by phishing scams and project rug pulls significantly decreased compared to 2024; however, hacker attacks were frequent, with losses exceeding $3.1 billion, and the project type with the highest losses remained exchanges. Meanwhile, security incidents related to private key leaks decreased, with the main reasons for this shift including:
After rampant hacker activities last year, the entire Web3 ecosystem has placed greater emphasis on security this year, with efforts made by project teams and security companies in various aspects, such as internal security operations, real-time on-chain monitoring, increased focus on security audits, and actively learning from past contract vulnerability exploitation incidents, thereby enhancing security awareness in private key management and project operational security. As the difficulty of exploiting contract vulnerabilities and stealing private keys has increased, hackers have begun to deceive users into transferring assets to hacker-controlled addresses through other means, such as supply chain attacks and front-end vulnerabilities.
Additionally, with the integration of the crypto market and traditional markets, attack targets are no longer limited to DeFi, cross-chain bridges, and exchanges, but have shifted towards attacking payment platforms, gambling platforms, crypto service providers, infrastructure, development tools, MEV bots, and various other targets, with the focus of attacks also shifting towards more complex protocol logic flaws.
For individual users, social engineering/phishing attacks and potential violent coercion have become significant threats to personal asset security. Currently, many phishing attacks involve smaller amounts and target individual users, which have not been publicly reported or recorded, leading to an underestimation of loss data; however, users should enhance their awareness of such attacks. Moreover, physical methods of coercion, such as kidnapping targeting crypto users, have occurred multiple times this year, necessitating that users protect their personal identity information and minimize the public exposure of their crypto assets.
Overall, the Web3 security landscape in 2025 still faces severe challenges, and both project teams and individual users must remain vigilant. In the future, supply chain security may become a top priority for Web3 security. How to continuously protect various infrastructure service providers in the industry and monitor and alert threats present in the supply chain is a significant challenge that all parties in the industry need to address together. Furthermore, AI-driven social engineering/phishing attacks may continue to increase, necessitating the establishment of a multi-layered, real-time, dynamic defense system that spans from personal awareness to technical barriers and community collaboration to respond effectively.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




