Written by: Kevin, Movemaker Researcher
In 2026, the cryptocurrency industry stands at a new crossroads. With deep institutional capital involvement, the settling of regulatory frameworks, and the growth of AI in the on-chain economy, the privacy track is undergoing an unprecedented paradigm shift. Over the past decade, blockchain privacy technology has often been misunderstood as a tool for money laundering or a haven for hackers. This early form of "indiscriminate anonymity" has repeatedly faced setbacks due to its inherent opposition to the global financial regulatory system. However, a Privacy 2.0 paradigm centered on "programmable compliance" has emerged and is becoming the cornerstone of the next generation of Web3 infrastructure.
1. The "Lost Decade" of the Privacy Track and the Logic of Potential Explosion
1.1 The Misconception of Indiscriminate Anonymity
Looking back over the past decade (2014-2024), the development of the blockchain privacy track has been filled with idealism, but it has also fallen into the quagmire of commercial implementation. Early privacy projects, such as Monero and early Zcash, were heavily influenced by the Cypherpunk spirit, with a core design philosophy of "adversarial privacy." This mindset holds that privacy should be absolute and indiscriminate, and any form of regulatory backdoor or audit interface is a betrayal of the spirit of privacy.
However, this technical path has proven to be a fallacy in practice. The core contradiction lies in its attempt to build a completely black-box value transfer network in a system that needs to interact with the real-world financial system.
Deviation in Technical Path: Most Privacy 1.0 projects equated privacy with "hiding transaction graphs." For example, mixers break the connection between senders and receivers by obscuring the flow of funds. This "privacy for the sake of privacy" technical approach, while mathematically achieving anonymity, creates significant obstacles at the compliance level.
Deadlock in Business Expansion: Due to a lack of compliance boundaries, early privacy coins struggled to be accepted by mainstream exchanges and payment gateways. Under anti-money laundering compliance pressure, leading exchanges like Coinbase and Binance delisted privacy coins in multiple jurisdictions. This meant that privacy assets lost their liquidity entry, becoming niche speculative tools or black market mediums, unable to support large-scale commercial activities.
1.2 The Lost Decade: Mismatch Between Technology and Market
The past decade is referred to as the "lost decade" for the privacy track because the industry invested too many resources in the wrong direction. The excessive emphasis on "permissionless anonymity" led to most technological innovations (such as early ring signatures and simple zk-SNARKs transfers) focusing on how to hide data more deeply rather than how to manage data more flexibly.
This mismatch resulted in two outcomes:
Lack of Application Scenarios: Apart from transfers and speculation, privacy coins have hardly built a rich ecosystem similar to DeFi, NFTs, or DAOs. This is because building complex financial applications on privacy chains that do not support programmability is extremely difficult.
Failure of Regulatory Arbitrage: Attempts to evade regulation through decentralized architecture have completely failed. Regulatory agencies easily curtailed the expansion of these protocols by cracking down on deposit and withdrawal channels and infrastructure service providers.
1.3 Defining "Programmable Compliance"
Entering 2025, the privacy track welcomed a structural revival. This was not due to an increased market demand for "anonymity," but rather because the connotation of privacy technology underwent a qualitative change. A new generation of privacy projects is building what is called Privacy 2.0, characterized by "programmable compliance."
"Programmable compliance" refers to embedding compliance logic (such as identity verification, blacklist screening, transaction limits, and audit report generation) directly into the underlying code or smart contracts of privacy protocols. It allows users to prove the legality of their actions to specific regulatory parties or counterparties while keeping their data confidential from the public.
This paradigm shift is reflected in three aspects:
Optional Privacy: The system may default to transparency or allow users to selectively enable privacy protection, moving away from a "one-size-fits-all" mandatory anonymity.
Auditability: Users possess a "view key," which they can voluntarily share with tax authorities, allowing them to decrypt and verify the transaction history of specific accounts without disclosing it to the entire network.
Rule Embedding: Compliance rules can be enforced at the protocol level. For example, a privacy stablecoin contract could stipulate: "Only addresses holding a compliant DID (Decentralized Identity) can receive transfers," or "Transfers exceeding $10,000 require additional compliance proof."
1.4 The Urgent Need for Tokenization of Real-World Assets (RWA)
The tokenization of real-world assets (RWA) is one of the biggest growth points for the crypto industry in 2026. However, the large-scale on-chain integration of RWA faces an irreconcilable "paradox."
Institutional Pain Points: Financial giants like BlackRock and Goldman Sachs would never conduct transactions on a completely public ledger like Ethereum. Not only would it leak trade secrets, but it could also lead to market front-running and targeted short/long squeezes.
Regulatory Contradictions: Regulatory agencies (such as the SEC and ESMA) require that financial transactions be traceable and monitorable (to meet AML requirements), but at the same time, data protection regulations (such as the EU's GDPR) strictly prohibit the public disclosure of sensitive personal data on immutable blockchains.
Privacy 2.0 is the only solution. Only through "programmable compliance" privacy technology can we achieve "public confidentiality and regulatory transparency."
1.5 The Underlying Architecture of the AI Agent Era: Protecting Algorithms and Strategies
2026 is considered the inaugural year of the "AI Agent Economy." Thousands of autonomous AI Agents will conduct transactions, arbitrage, and resource scheduling on-chain. For these AI Agents, privacy is no longer an option but a foundation for survival.
Strategy Protection: The core competitiveness of AI Agents lies in their algorithms and trading strategies. If executed on a public ledger, their intentions and patterns can be instantly recognized and targeted by MEV bots (sandwich attacks). Only in a privacy environment (such as Anoma's encrypted intent pool) can Agents safely publish trading intentions without exposing their strategies.
Model Privacy: Future AI Agents may carry proprietary model weights or inference logic. Through zkVM (such as the service provided by Boundless), Agents can generate "proof of inference," demonstrating that their outputs are derived from specific model calculations without disclosing the model itself. This is known as zkML and is key to the assetization of AI models.
1.6 Shift in Regulatory Attitudes: From Suppression to Regulation
The attitude of regulatory agencies has also undergone subtle but significant changes between 2025 and 2026. Represented by the EU's AMLR and MiCA, major jurisdictions worldwide are beginning to distinguish between "anonymity-enhancing tools" and "privacy-enhancing technologies (PETs)."
The former is viewed as a money laundering tool and faces ongoing suppression.
The latter is seen as a compliance infrastructure and is encouraged. Discussions by institutions like the U.S. Treasury indicate that regulators are beginning to realize that the data leak risks posed by completely public ledgers are also a form of systemic risk. Therefore, technologies supporting "selective disclosure" are gradually gaining recognition.
2. Three Sub-Directions of the Privacy Track
Thus, the explosion of the privacy track is no longer a past hype concept but an inevitable result of industry evolution. Following this line of thought, we look at the strategic positioning of the following three projects:
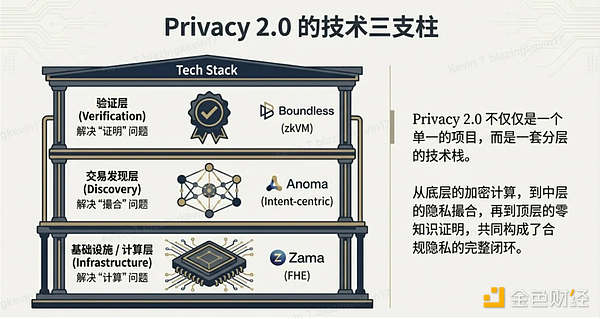
2.1 Infrastructure/Computing Layer: Zama
In the landscape of Privacy 2.0, Zama occupies the core position at the lowest layer—the computing layer. ZK solves the "verification" problem, while fully homomorphic encryption (FHE) addresses the "computation" problem.
FHE allows applications to run business logic (such as lending, exchange matching, voting) in a completely encrypted state, where node validators have no idea what transactions they are processing, thus completely resolving MEV and data leakage issues.
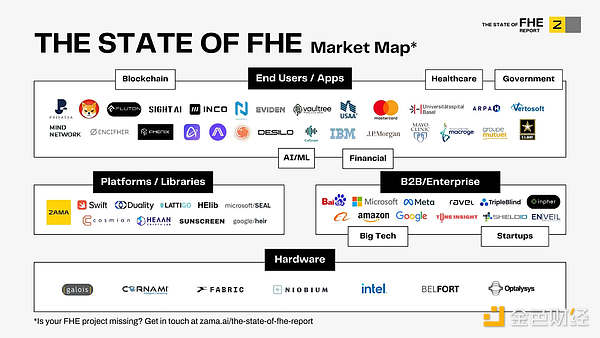
Zama's approach is to create a "privacy plugin" for the entire industry rather than launching a new chain. It aims to enable major public chains like ETH and Solana to directly handle encrypted data.
Currently, their biggest bet is on hardware, collaborating with Fabric Cryptography to develop acceleration chips to solve the issues of slow speed and high costs. If this hardware solution can be implemented, the operational efficiency of FHE will experience a qualitative leap, allowing this technology to be truly used by the public rather than remaining confined to laboratories.
Zama is no longer just a theoretical exercise. The recently concluded auction was essentially a "live-fire exercise" for FHE—utilizing an encrypted sealed bidding mechanism to allow all bids to be matched "blindly" on-chain, directly reducing the front-running and MEV chaos seen in traditional auctions. With the TGE scheduled and mainnet staking initiated, Zama has officially completed its leap from "academic terminology" to "financial infrastructure."
Additionally, with the previous acquisition of KKRT Labs, Zama is attempting to bridge ZK and FHE, and once this "privacy + computation + verification" closed loop is operational, it will no longer be just a crypto project.
2.2 Transaction Matching Layer: Anoma
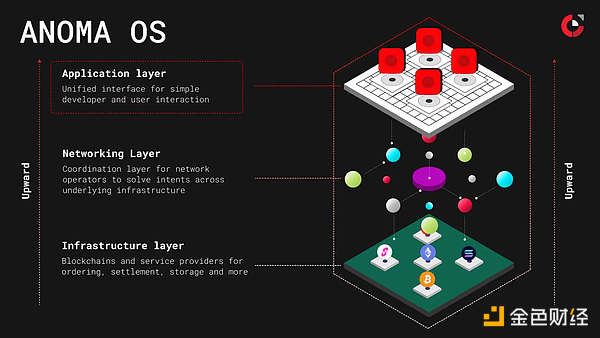
If Zama addresses data confidentiality, then Anoma is dedicated to solving the discovery and matching mechanism of transactions.
Traditional DeFi users often have their transactions exposed in the Mempool, with their intentions fully visible to MEV bots. Anoma focuses on privacy in counterparty discovery, allowing users to publish encrypted intents, while Solvers match transactions without decrypting them (using FHE or TEE).
It is evident that this solution addresses privacy issues at a basic level; it also tackles the problems of multi-chain fragmentation and interaction complexity.
Once a user's transaction intent is made public in the Mempool, it becomes prey for MEV bots. Anoma introduces an "Intent Center" architecture. Users no longer sign transactions but instead sign "intents." Intents can be encrypted. They will only be decrypted and executed when specific conditions are met. This means that MEV bots cannot peek at the user's hidden cards, thus preventing front-running attacks.
Anoma recently completed integration with the Base mainnet, extending its intent settlement layer to the EVM ecosystem, thereby accessing a broader liquidity market. The current technical focus is on the final activation of the "protocol adapter." As the core component connecting user intents with Solver execution, the launch of this adapter will mark the completion of the network's functional closed loop—at that point, $XAN will transition from a mere governance token to a utility token for paying network settlement fees, and its ability to effectively support multi-chain transaction matching will be worth watching.
2.3 Verification Layer: Boundless
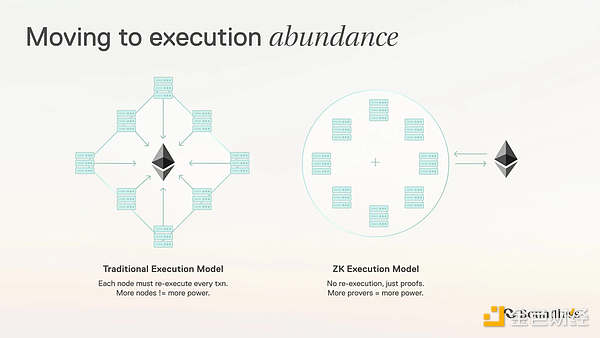
With the explosive growth of ZK Rollups and various privacy applications, the "Proving" phase, which is computation-intensive, has become the biggest roadblock. Boundless was born to specialize in the large-scale production of "general privacy proofs."
Boundless transforms the generation capability of ZK proofs into a tradable computing power commodity, modularly embedding it into all scenarios that are hungry for ZK verification.
Operational Mechanism: This is a free market for computing power. Developers throw out computing demands (such as verifying privacy ledgers or running AI models), and Provers in the network come in with GPU/FPGA computing power to bid, generate proofs, and ultimately put them on-chain.
Unified Interface: It acts like Chainlink in the ZK computing field, providing a standardized proof service layer for all blockchains. Any chain can "outsource" the heavy ZK load simply by calling an API.
As the demand for ZK-Rollups and ZK Coprocessors experiences exponential growth, Boundless will become the decentralized engine that processes massive amounts of ZK proofs. It completely opens up the imaginative ceiling for privacy applications: whether it’s on-chain identity, credit assessment, compliance review, or strategy validation for AI Agents, zkVM can provide them with privacy protection armor.
Boundless utilizes BitVM to upgrade Bitcoin into the ultimate settlement layer for ZK proofs. This is not just a technical upgrade but a strategic elevation: it is no longer limited to the Ethereum ecosystem's coprocessors. Once this decentralized Prover Market is operational, Boundless will anchor high-load AI reasoning and complex financial model calculations on the absolute security of Bitcoin.
3. If the Privacy Track Were to Be Renamed, the Moat Effect Could Be Doubled
After understanding the layouts of Zama, Anoma, and Boundless, we need to examine the ultimate outcome of the privacy track from a higher dimension. Privacy will create the most powerful "chain-locking" effect.
3.1 Differences in Network Effects Between Public Chains and Privacy Chains
On public chains, the migration costs for users and assets are extremely low. Since all data is publicly transparent, cross-chain bridges can easily verify states and transfer assets. This leads to competition among public chains, other than Ethereum, Solana, and BNB, becoming purely a competition of performance and fees, resulting in shallow moats. Users are "mercenaries," going wherever the profits are highest.
However, the situation is entirely different on privacy chains.
3.2 "Chain-Locking" Mechanism: Why Privacy is Difficult to Cross-Chain
"Cross-chain tokens are easy, but cross-chain privacy is hard."
When a user accumulates a large amount of encrypted state (such as encrypted credit records, private transaction histories, and undisclosed holding strategies) in a privacy ecosystem (like a chain based on Zama's fhEVM), it becomes very difficult to migrate these "secrets" to another chain.
Metadata Leakage Risk: Even if it is technically possible to cross-chain, the migration process itself generates metadata. Monitors can infer the user's true identity by analyzing the timing, amount, and frequency of fund inflows and outflows. This is known as the "de-anonymization risk of deposits and withdrawals."
Non-portability of State: Encrypted data often relies on the key management system of a specific chain (such as Zama's threshold decryption network). To migrate data, it must first be decrypted (exposing risk) and then re-encrypted on another chain. This high-risk cost creates a significant barrier to conversion.
This characteristic of "easy to enter, hard to exit" (or "afraid to exit") creates strong user stickiness.
Stronger Network Effects: In privacy networks, the more users there are, the larger the anonymity set becomes, and the stronger each user's privacy protection is. This creates a positive feedback loop: better privacy -> more users -> even better privacy.
Winner Takes All: Due to the extremely high migration costs and strong network effects, it is unlikely that the privacy track will see a "hundred flowers blooming" scenario; it is more likely to evolve into a "winner takes all" situation. A few leading privacy infrastructures will capture the vast majority of the value.
The privacy track in 2026 is an essential path for Web3 to mature into a financial system. Rising from the ruins of Tornado Cash is a new generation of Privacy 2.0 legion equipped with FHE (computation), Intents (intent), and zkVM (proof). The core driving force behind this transformation is "programmable compliance," which aligns with the era's demand for RWA asset tokenization and the explosion of AI Agents.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。

