Written by: Xiao Za Legal Team
In the internet era, providing network connectivity, information transmission, resource sharing, platform transactions, and other network technical support has become a common technical service work, which is neutral and harmless in itself and belongs to typical neutral assistance behavior. However, with the addition of the crime of assisting information network criminal activities in the "Criminal Law Amendment (Nine)," the crime of assisting based on technical support has become a significant legal risk faced by network technology operators, and many technical providers have thus been drawn into the vortex of crime.
As criminal patterns evolve, the judicial crackdown chain continues to advance, and the technical neutrality is frequently compromised in trials. This warns us: the neutrality of technology is by no means a "get-out-of-jail-free card" in criminal trials; "behavior patterns" are far more decisive in determining guilt or innocence than "technical content."
How can we avoid the servers and customized software provided from becoming "accomplices" in fraud or money laundering, and clarify the legal boundaries of technical operations? How can we secure sufficient and reasonable development space for technological innovation and industrial development while finding a balance between network security maintenance and network freedom protection? The Xiao Za team will focus on the most critical aspect of the recognition of the crime of assistance, which is the determination of "knowledge," to clarify the punishment boundaries of neutral technical behavior and guide technical providers on the path to compliant operation.
01 "Knowledge" = "Clear Knowledge" = Actual Knowledge + Constructive Knowledge
The specificity of network technology determines that the "knowledge" requirement for the crime of assistance is the key to distinguishing between guilt and innocence. Unlike traditional accomplices who use "conspiracy" as the starting point for establishing and punishing crimes, the concealment and decentralization of cyberspace allow the perpetrator and the helper to connect through virtual identities.
At the same time, with the help of the internet and information-sharing mechanisms, even weak or non-existent intent can objectively become part of criminal activities. Therefore, for legislative purposes and crime governance needs, the recognition of the crime of assistance should not be limited to traditional accomplice theory.
There are generally three different opinions regarding the understanding of "knowledge" in the crime of assistance in theory and practice:
① "Actual Knowledge," meaning clear knowledge;
② Knowledge and should have known;
③ "Clear Knowledge" and "Possible Knowledge."
We support the first viewpoint.
1. The Contradiction of Should Have Known and Possible Knowledge Principles
Through the review of judicial cases, it can be seen that current judicial practice adopts a relatively low standard for determining "knowledge," namely, either② or③, which leads to the continuous expansion of the crime of assistance. This is a result guided by the characteristics of cybercrime. Specifically, due to the wide coverage of information network crimes and the complexity of network technology, there are often difficulties in investigation and evidence collection in judicial practice.
As a result, judicial authorities tend to expand the interpretation of "knowledge," equating it with "should have known" or "possible knowledge" to reduce the difficulty of objective proof. However, this standard is inappropriate. The specific reasons are as follows:
First, at the theoretical level, interpreting knowledge as "should have known" or even "possible knowledge" violates the principle of legality in criminal law and the principle of responsibility, confusing the determination of intent and negligence.
On one hand, knowledge is a form of actual recognition rather than potential recognition, while "should have known" implies that the actor does not actually know; equating the two contradicts objective facts and does not meet the requirements of the principle of responsibility.
On the other hand, "knowledge" means that the actor is already aware of the existence or possible existence of certain facts, which is a situation that has been foreseen, while "should have known" is essentially "not knowing," which is an unforeseen situation. Equating the two expands intentional responsibility into the realm of negligence, which is clearly inappropriate.
Second, at the practical level, expanding the scope of knowledge will unreasonably increase the review obligations of technical providers, hindering technological progress.
For network service providers, the technical actions they provide, such as internet access and server hosting, often have business neutrality; at the same time, the recipients of network services usually present a wide range of "one-to-many" characteristics, which makes it difficult for technical providers to discern and review from a vast amount of information. If it is only required to "should have known" or even "could have known" that others are using the network to commit crimes, it undoubtedly imposes excessively harsh requirements on network service providers.
2. Establishing the Standard of Clear Knowledge
For the above reasons, the Xiao Za team believes that the knowledge requirement for the crime of assistance should be limited to "clear knowledge": first, the actor actually knows and admits to knowing; second, the actor actually knows, which is determined by applying presumptive rules. Only when the actor clearly understands the object of assistance, that the object is using their technology to engage in harmful social behavior, the promoting effect of the assistance on others, and the resulting harmful consequences, can the crime of assistance be established.
As for what kind of crime is being committed, whether it is fraud or money laundering, it is irrelevant. This cognitive deviation does not hinder the establishment of the crime of assistance. The debate over the difficulty of ascertaining subjective intent should be proven by evidence of technological advancement and improvement, rather than deviating from basic principles to broaden the boundaries of knowledge.
02 The Path of Presumption from Objective to Subjective Knowledge
In judicial practice, how to prove the actor's subjective "knowledge" is the key and difficulty in determining the crime of assistance. Given the difficulty of directly obtaining the actor's inner intentions, judicial authorities have further improved the presumption principle of "subjective-objective consistency"—that is, by examining a series of objective external behaviors and individual external characteristics of the actor to infer their subjective cognitive state.
The Xiao Za team summarizes this as follows:
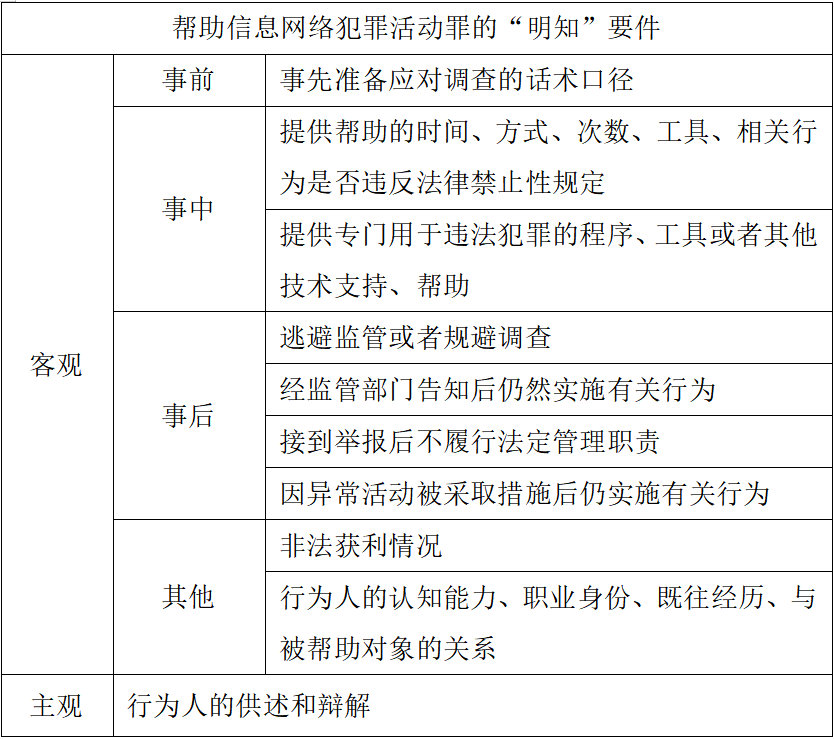
03 Analysis of the Criminal Elements of Typified Technical Behaviors
Defining knowledge solely from a theoretical perspective is far from sufficient to serve as a warning. The Xiao Za team will combine academic theories and practical cases to classify and create three behavioral profiles based on the objective manifestations of behavior and the subjective psychology of the actor, in order to delineate the red lines of neutral technology and the boundaries of criminal punishment.
(1) Technical Assistance Provided for Criminal Activities
Technical assistance provided for criminal activities refers to the act of creating or providing network products or services specifically for the purpose of committing crimes. Typical examples include the creation and sale of malware, viruses, botnets, phishing websites, and illegal technical systems. Such criminal behaviors unique to the technological era have exceeded the scope of technical neutrality and have become tools for crime.
In this case, the actor knows that they are providing assistance for engaging in information network criminal activities, and there is no difficulty in proving this; therefore, as long as the objective circumstances meet the severity requirements, the crime of assistance can be established.
In addition, such malicious behaviors can also be addressed under accomplice theory, treating the crime committed by the assisted party as an accomplice. The existence of intent between the perpetrator and the accomplice does not affect the determination of complicity, meaning that unilateral accomplices still have sufficient grounds for establishment.
(2) Misused Technical Assistance
Misused technical assistance refers to situations where the technology itself is created for legitimate purposes but is used to assist illegal information network criminal activities. It needs to be specifically judged whether the technology is primarily used for legitimate purposes or for illegal activities. Typical examples include providing P2P software, bookmark sites, link sites, or installing GOIP devices and surveillance cameras used for signal transmission, renting, installing, and maintaining "multi-card treasure" devices, and building telephone voice gateways.
This behavior is legitimate and compliant in itself, but it does not exclude the possibility of becoming a tool for crime. In this case, sufficient evidence must be provided to prove that the actor "knows" that others are engaging in information network criminal activities in order to be held liable for the crime of assistance. The judgment standard for knowledge is as previously described.
(3) Occasionally Misused Technical Behavior
Occasionally misused assistance refers to situations where the technology is legal and compliant, and the provider's purpose is legitimate, but it is occasionally used illegally by the user. There is considerable debate regarding the responsibility of network platforms providing server hosting and software services in specific criminal activities. In this case, the violation of obligations by the technical provider is a prerequisite for criminal liability.
Based on the safe harbor rule, developing, selling, renting, providing, and maintaining software services are technically neutral behaviors with legitimate purposes and should not bear civil liability for infringement or criminal liability. In general, network service operators and platform operators do not have a special obligation to supervise users' specific behaviors. As long as operators conduct business and provide services within the framework of laws, regulations, and industry norms, and do not deeply participate in others' criminal activities, maintaining business neutrality, even if they know that others may use the servers they provide to commit crimes, they should not constitute the crime of assistance.
However, if operators violate compliance obligations, establish a close relationship with users, or conspire to provide specific assistance for criminal activities, or refuse to correct after being ordered by regulatory authorities to take corrective measures, they may constitute the crime of refusing to fulfill information network security management obligations or even the crime of assisting information network criminal activities. The specific path for such determinations still requires further research and improvement.
In Conclusion
Technical neutrality does not equate to being above the law; the boundaries of law often lie not in the technology itself but in the purpose and use of the technology. Any behavior of "technical provision" that harbors a fluke and operates in gray areas faces extremely high criminal risks.
For network technology operators, it is essential not only to delineate the boundaries with illegal technical behaviors but also to be vigilant about "misused technical assistance" and "occasionally misused technical behaviors," establishing a sound compliance review mechanism, clarifying service targets and usage scenarios, and avoiding inadvertently becoming a "catalyst" for crime. Only by innovating within compliance and developing within responsibility can we truly find a sustainable path between technological freedom and legal bottom lines.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




