Bybit Official: "Bybit's assets are still guaranteed 1:1, and we can bear the losses."
Written by: Wenser, Odaily Planet Daily
At 11:20 PM Beijing time on February 21, ZachXBT posted, "Suspicious fund outflows from Bybit have been detected, amounting to as much as $1.46 billion." According to Beosin Trace monitoring, a total of 514,723 ETH and derivatives were stolen from Bybit, with the total amount exceeding $1.5 billion. Subsequently, Bybit co-founder Ben Zhou confirmed that Bybit's official cold wallet had been hacked and began taking security measures.
The funds involved are mainly ETH, with the scale exceeding $1.5 billion
At 11:20 PM, ZachXBT issued a warning, confirming that the hacker's related address was 0x47666Fab8bd0Ac7003bce3f5C3585383F09486E2; after stealing the funds, they quickly exchanged mETH & stETH for ETH on a DEX.
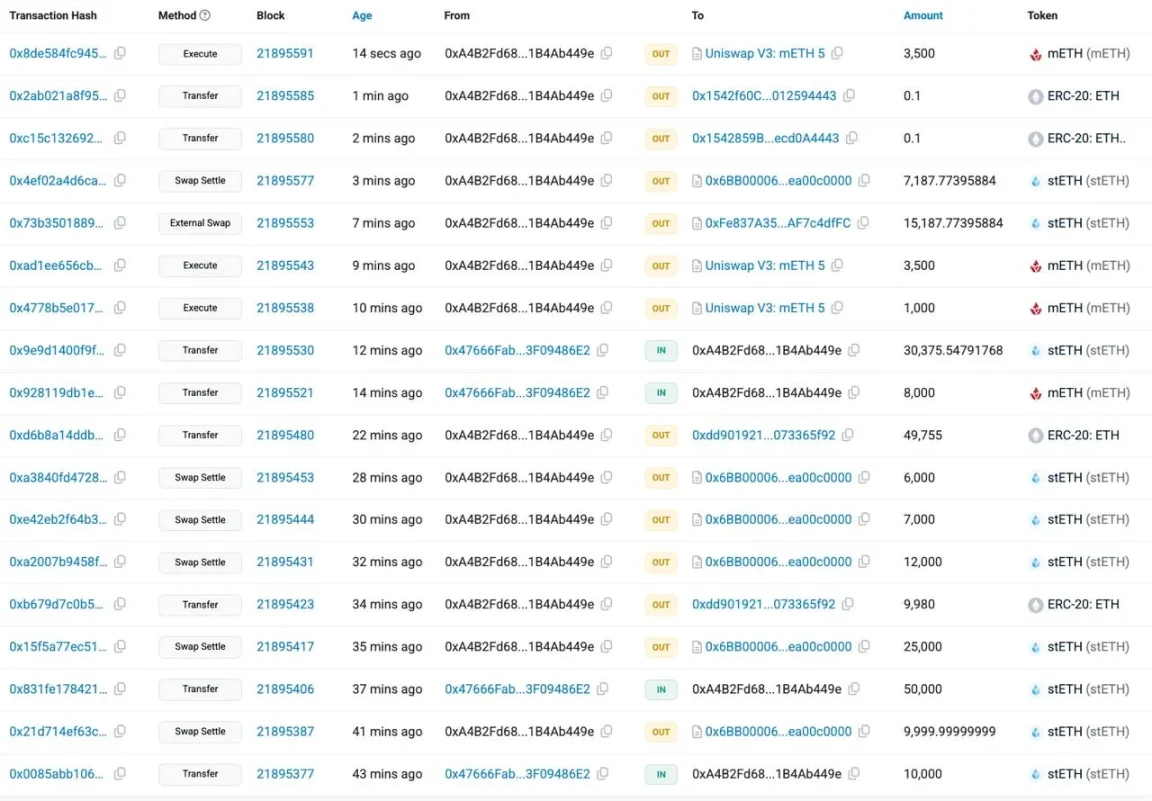
Hacker quickly performed a swap exchange
While the outside world was still speculating whether "the movement of such a large amount of funds was for Bybit's official wallet organization or for other purposes," ZachXBT quickly provided a new hint: "My sources confirm that the outflow of Bybit funds is a security incident."
Additionally, ZachXBT reminded major exchanges and service providers: "It is recommended to blacklist the following EVM addresses—
0x47666fab8bd0ac7003bce3f5c3585383f09486e2;
0xa4b2fd68593b6f34e51cb9edb66e71c1b4ab449e;
0x36ed3c0213565530c35115d93a80f9c04d94e4cb;
0x1542368a03ad1f03d96D51B414f4738961Cf4443;
0xdD90071D52F20e85c89802e5Dc1eC0A7B6475f92."
This move aims to immediately cut off the hacker's channels for laundering funds through CEX, preventing further loss of Bybit's stolen funds.
According to Beosin Trace monitoring statistics, a total of 514,723 ETH and derivatives were stolen, including:
401,347 ETH, worth $1.12 billion;
90,376 stETH, worth $253.16 million;
15,000 cmETH, worth $44.13 million;
8,000 mETH, worth $23 million.
Currently, the funds are divided into groups of 10,000 ETH and are deposited in over 40 Ethereum addresses. All hacker addresses have been added to the Beosin KYT label database, and Beosin KYT will issue alerts for all fund transfers involving hacker addresses. The Beosin security team analyzed that the attack method in this incident is similar to that of WazirX, where the front-end UI was used to deceive and led the multi-signature wallet to sign malicious content, altering the logic of the multi-signature wallet's smart contract, resulting in the transfer of funds from the multi-signature wallet.
Bybit Official Response: Multi-signature wallet transaction was attacked and altered, other cold wallet assets are safe, and withdrawals from the exchange are normal
Bybit co-founder Ben Zhou spoke out on X platform: "About an hour ago, Bybit's ETH multi-signature cold wallet made a transfer to Bybit's hot wallet. This specific transaction may have been altered, and all multi-signature wallet signers saw the altered UI displaying the correct transfer address, with the website link coming from @safe. However, the signature information was meant to change the smart contract logic of our ETH cold wallet. This allowed the hacker to control our specific ETH cold wallet signed by multi-signature and transfer all ETH from the cold wallet to an unknown address. Please rest assured that other cold wallets of Bybit are safe, and all withdrawals within CEX are operating normally."
Additionally, Ben Zhou immediately issued a call for help: "We will keep everyone updated on the latest developments of this incident. We would greatly appreciate any team that can help us track the stolen funds."
On-chain fund movements: Hacker quickly sold $200 million in ETH, nearly 500,000 ETH dispersed into 51 addresses
At 11:35 PM, Arkham detected that the $1.4 billion in ETH and stETH flowing out of Bybit had already been transferred to new addresses for sale. By that time, the hacker had sold $200 million worth of stETH. The on-chain tracking address is https://intel.arkm.com/explorer/address/0x47666Fab8bd0Ac7003bce3f5C3585383F09486E2.
At 12:00 PM on the 21st, ZachXBT updated the latest on-chain fund movements, noting that 10,000 ETH had been dispersed by the hacker into 39 addresses, and the hacker also transferred another 10,000 ETH into 9 additional addresses. At 12:18 PM, according to Arkham's monitoring statistics, approximately $100 million worth of ETH (about 400,000 ETH) has now been transferred from the hacker's original address to a new wallet.
According to the latest monitoring information from on-chain analyst Yu Jin, it is suspected that due to the very shallow liquidity pool of cmETH, the 15,000 cmETH stolen from Bybit had their unstaking requests returned by the cmETH withdrawal contract, which may be successfully intercepted to avoid further losses. Additionally, the amount of ETH stolen from Bybit is 499,000 ETH (worth about $1.37 billion), which has been dispersed by the hacker into 51 addresses.
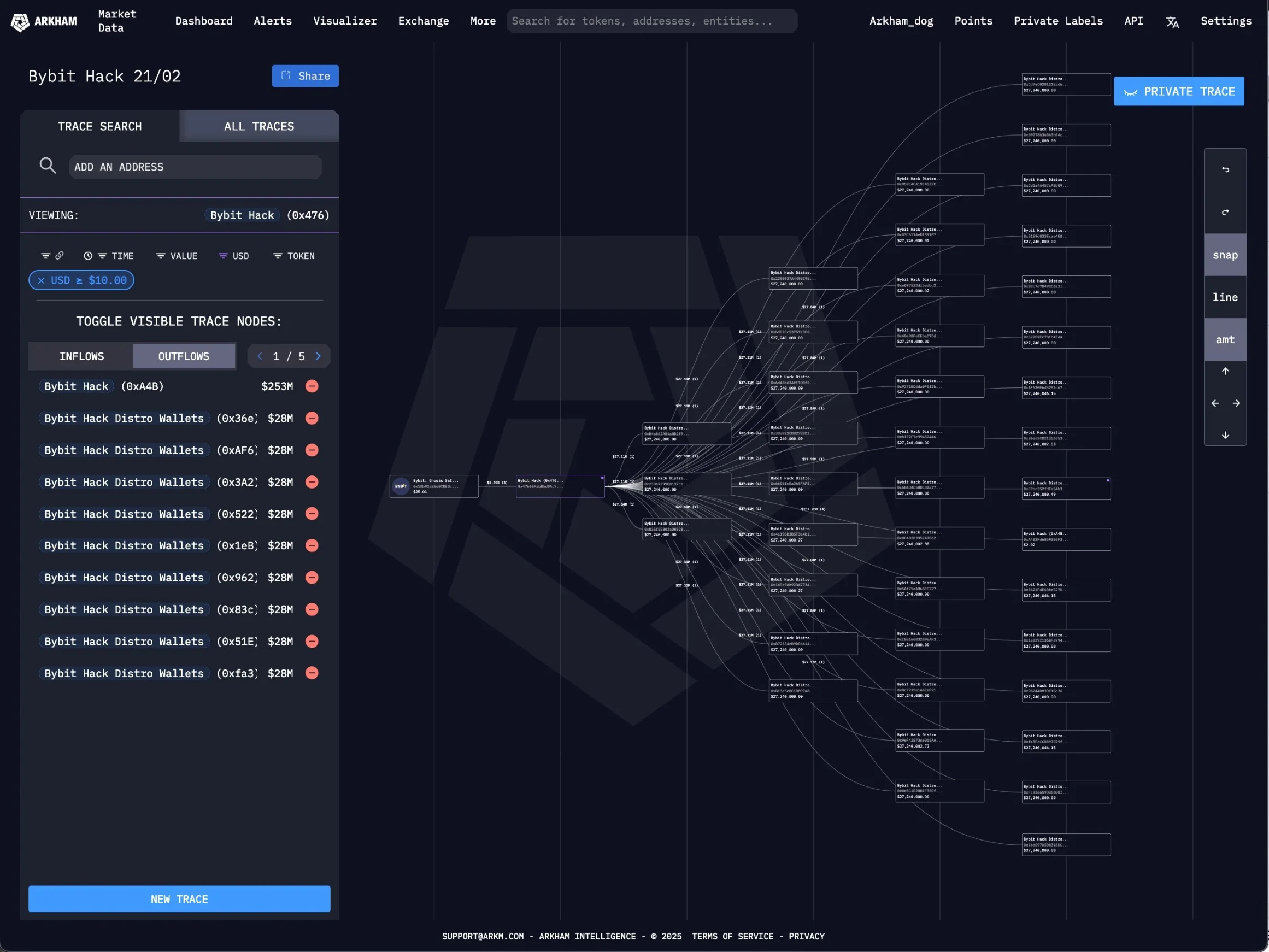
On-chain fund movements
As of the time of writing, the hacker's original address only has $3.669 million in assets remaining, with the ETH holding dropping sharply to 1,346 ETH.
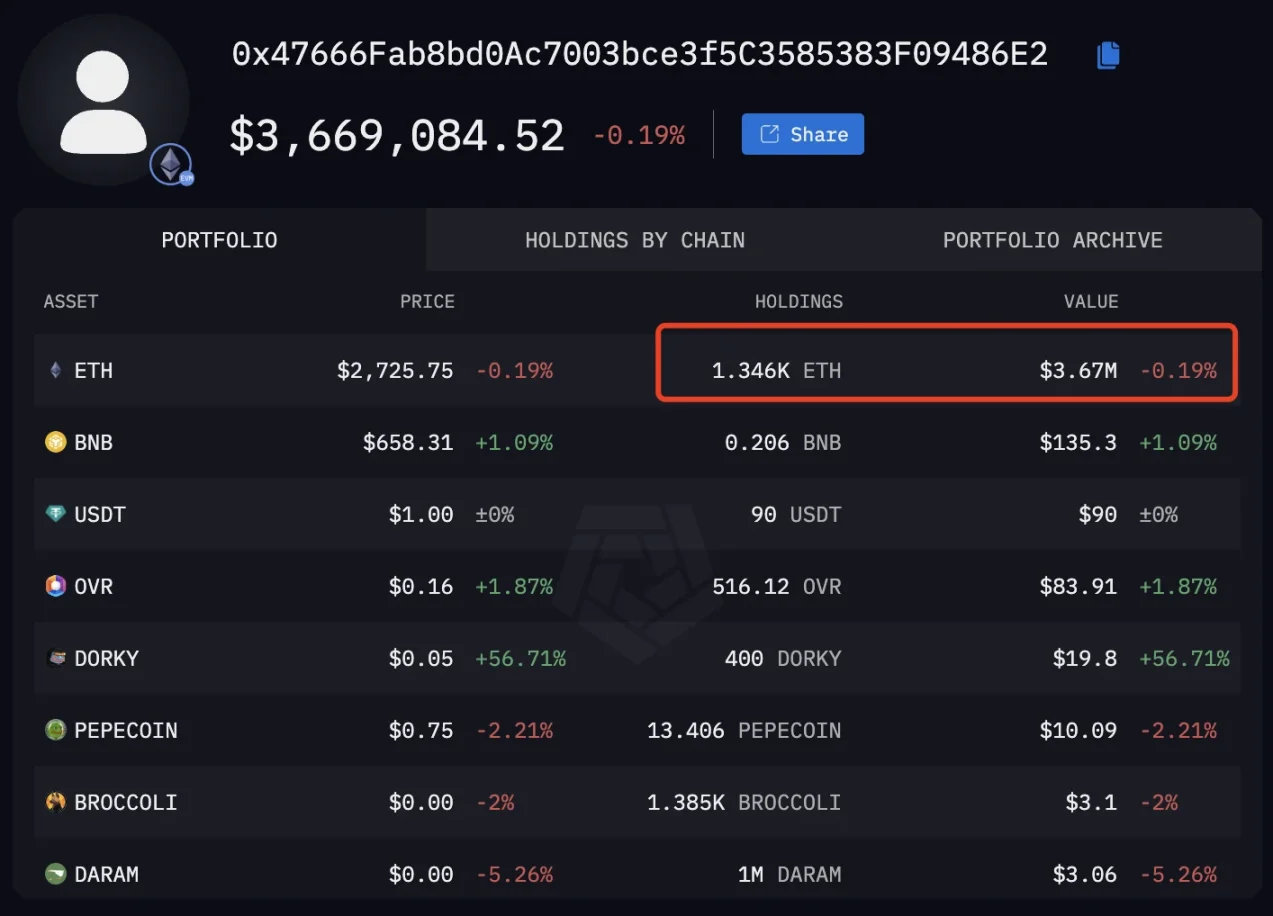
On-chain information
According to a small-scale investigation by the founder of the security company Slow Mist, Yu Xian, it is initially suspected that this incident may have been carried out by North Korean hackers, based on the methods used in the Safe multi-signature and the current money laundering techniques, with specific information still pending further tracking.
Slow Mist subsequently released the technical details of the Bybit hacker's operations:
A malicious implementation contract was deployed at UTC 2025-02-19 7:15:23: https://etherscan.io/address/0xbdd077f651ebe7f7b3ce16fe5f2b025be2969516
At UTC 2025-02-21 14:13:35, the attacker used three owners to sign the transaction, replacing the Safe implementation contract with a malicious contract: https://etherscan.io/tx/0x46deef0f52e3a983b67abf4714448a41dd7ffd6d32d32da69d62081c68ad7882
The attacker then used the backdoor functions "sweepETH" and "sweepERC20" in the malicious contract to steal from the hot wallet.
Bybit Hacking Incident Aftermath: Currently within controllable range
The theft of over $1.5 billion in ETH-related assets marks the largest security incident in 2025, and even in 2023, and in the history of the financial industry, further intensifying market concerns about ETH price performance and Bybit's asset security.
Regarding the former, there is indeed some short-term risk. However, in the medium to long term, market concerns should be alleviated. Some believe that this is because ETH is the most decentralized asset after BTC, and the hacker is likely to hold the majority of ETH rather than directly dumping it at a low price. Additionally, the conversion of ETH to stablecoins will also be closely monitored and restricted.
Regarding the latter, Bybit's official response came promptly. At 12:07 AM on the 22nd, Bybit co-founder Ben Zhou stated: "Even if the losses from this hacker attack cannot be recovered, Bybit's assets are still guaranteed 1:1, and we can bear the losses." This reflects the confidence and stability of a well-established exchange.
On this point, in addition to the common Merkle tree reserve proof on-chain, information previously mentioned by Bybit co-founder and CEO Ben Zhou in an interview can also serve as evidence. He mentioned that "about 80% of Bybit's company assets are in stablecoins, with the remaining portion in fiat currency. The core goal of this configuration is to ensure the financial stability of the exchange, rather than pursuing asset appreciation."
Multiple Statements: CZ, He Yi, Sun Yuchen, Bitget CEO, Kucoin CEO express support and assistance
After the incident, CZ replied to Ben Zhou's tweet, stating: "This is not an easy situation to handle. It is recommended to temporarily stop all withdrawals as a standard security precaution. We will provide any assistance if needed." Binance co-founder He Yi responded to Bybit CEO Ben Zhou, saying, "We will provide support if needed."
TRON founder Sun Yuchen stated, "We are closely monitoring the Bybit security incident and will do our utmost to assist our partners in tracking the relevant funds and provide all possible support."
KuCoin CEO BC Wong also expressed support for Bybit and stated that they have initiated work to assist in monitoring fund flows and freezing suspicious assets.
Additionally, on-chain analyst @ai_9684xtpa analyzed: "Ethena has 21% of USDe executing delta-neutral hedging strategies on Bybit, with the ETH portion valued at $227 million, uncertain if it will be affected. After Bybit confirmed the theft, ENA has dropped 11.5% and has recouped today's gains." Ethena Labs subsequently stated that they have noted the Bybit incident, and all spot assets supporting USDe are held through over-the-counter custody solutions, with no spot value reserve funds stored in any exchange (including Bybit). Currently, the unrealized profit and loss of Bybit's hedging positions total less than $30 million, which is less than half of the reserve fund, and USDe has sufficient collateral balance, with more information to be provided promptly after receiving updates.
In the early hours of the 22nd, Bybit CEO Ben Zhou communicated with the outside world via Bybit's live streaming platform, mentioning:
First, Bybit typically conducts internal asset transfers every three weeks, depending on the balance in our hot wallet. Whenever the hot wallet reaches a benchmark that we believe needs replenishing, a transfer transaction occurs, and I am the last signer of the transfer transaction. At that time, I checked the link, UI, target address, code, and other information, but I did not check thoroughly. The hacker somehow successfully manipulated the UI of all signers' computers. We then confirmed that the hacker attack and the signed code wallet were from the Ethereum cold wallet under the secure wallet, and other cold wallets were not affected. Bitcoin is our main reserve and is very secure.
Secondly, Bybit is contacting our partners to provide us with loans. Even if we want to buy, we will not immediately purchase Ethereum. Currently, we are considering obtaining bridge loans from partners to make up for the stolen funds, with 80% already secured.
Finally, Ben emphasized: "All products and services are operating as usual. We will not stop withdrawals for now; we are still processing withdrawals."
After the incident, Bitget promptly transferred 40,000 ETH to Bybit, valued at over $100 million, to provide maximum support through action.
Bitget CEO Gracy Chen later expressed support for Bybit on the X platform, stating: "Bybit is a respected competitor and partner. Although this loss is significant, it is just their annual profit. I believe customer funds are 100% safe, and there is no need to panic or rush to withdraw."
Around 9 AM on the 22nd, another exchange, MEXC, began transferring 12,652 stETH (approximately $33.75 million) from its hot wallet to Bybit's cold wallet. According to on-chain analyst Yu Jin's monitoring, Bybit has currently received support in the form of 64,452 ETH (approximately $170 million) in loans. This support mainly comes from Bitget, a certain institution withdrawing from Binance, and MEXC.
Bybit Official's Latest Response: Sufficient Reserve Funds, 99.994% of Withdrawal Requests Processed
Around 3 AM, in response to the earlier asset theft, Bybit officially released a detailed announcement about the incident for the first time: At 8:30 PM Beijing time on February 21, Bybit detected unauthorized activity in the Ethereum cold wallet during a routine transfer. This transfer was part of Bybit's official plan to move ETH from the multi-signature cold wallet to the hot wallet. Unfortunately, the transaction was manipulated by a complex attack that altered the smart contract logic and hid the signature interface, allowing the attacker to control the ETH cold wallet. As a result, over 400,000 ETH and stETH, valued at more than $1.5 billion, were transferred to unknown addresses.
Stolen funds: ETH and stETH valued at over $1.5 billion.
Main cause: Malicious manipulation of the transfer process during a planned routine transfer of the ETH multi-signature cold wallet.
Bybit reiterates the following key points: All other cold wallets under Bybit are in a secure state, customer funds have not been affected, and please be wary of other scams; despite a surge in withdrawal requests, the high volume of requests may cause delays in withdrawals, but all withdrawals are being processed normally, with 70% of pending requests already handled; Bybit's reserves are substantial and supported 1:1, ensuring that all customer assets are fully protected, and users can view relevant information on the proof of reserves (PoR) webpage.
Meanwhile, Bybit is working with leading blockchain forensic experts to track the stolen funds and resolve the situation; its security team is investigating the root cause, particularly focusing on potential vulnerabilities in the Safe.global platform's user interface that may have been exploited during the transaction. Bybit's asset management scale exceeds $20 billion, and if necessary, bridge loans will be used to ensure user funds are available. The Bybit platform and all other services, including trading products, cards, and P2P, are operating normally.
Bybit CEO: 99.994% of Withdrawal Requests Processed, All Functions and Products Operating Normally
At 8:54 AM, Bybit co-founder and CEO Ben Zhou posted on the X platform: "Since the hacker attack (10 hours ago), Bybit has experienced the highest number of withdrawals we have ever seen. We have received over 350,000 withdrawal requests, and currently, about 2,100 withdrawal requests are pending. Overall, 99.994% of withdrawal requests have been successfully completed. If your withdrawal has been completed, please leave a message here. Although we may have encountered the most severe hacker attack in history (including banks, crypto, and finance), all Bybit functions and products are still operating normally. The entire team has been awake all night, handling and responding to customer questions and concerns. Everyone is on deck. Rest assured, we are with you."
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




