First, let's state the conclusion. Firstly, the front end cannot directly steal wallets because it cannot obtain passwords and private keys. Secondly, it is important to distinguish phishing websites and try to find sites that have third-party audit endorsements. Additionally, pay attention to the management of private keys, avoid storing them online, and try to import them offline.
I. Basic Concepts
First, it is necessary to understand the concepts and differences between wallet passwords, private keys, and mnemonic phrases.
In cryptocurrency wallets, the wallet password is a locally set protection key by the user, used to encrypt and unlock the private key stored on the device, and its function is limited to accessing the wallet software; the private key is a 64-byte random number that is the core of controlling wallet assets, directly used to sign transactions, and possessing the private key is equivalent to possessing the assets; the mnemonic phrase (usually consisting of 12 or 24 words) is a backup phrase generated from the private key using the BIP-39 standard, which is easy to remember and restore. Importing the mnemonic phrase can regenerate the private key, thus restoring the wallet—simply put, the password protects the private key, the private key controls the assets, and the mnemonic phrase backs up the private key. The three are interconnected but serve different functions.
The following will take the Phantom wallet as an example for introduction.
II. The Web Cannot Technically Obtain the User's Password
- Password Input Is Isolated from the Web
The interface for entering the password is an independent pop-up generated by the Phantom extension, completely separate from the web page.
(1) As a browser extension, Phantom uses independent UI rendering permissions to generate pop-ups, running in its own execution environment, unrelated to the web page's DOM.
- The Pop-up Is Driven by Independent HTML and JavaScript Files Defined by manifest.json, Isolated from the Web's DOM and Event Listeners (such as Keyboard Input)
(3) The browser's sandbox isolation mechanism ensures that the web page cannot access or manipulate the pop-up's DOM elements, such as being unable to obtain the content of the password input box.
- Passwords Are Processed Locally Only
After entering the password, Phantom unlocks the private key on the local device, and the entire process does not connect to the internet or upload to the web page.
(1) The private key is encrypted and stored in IndexedDB (using the AES-256 algorithm), and the encryption key is derived from the user password using PBKDF2 (with salt and high iteration counts).
(2) After entering the password, Phantom uses PBKDF2 to decrypt the private key in the local JavaScript environment of the extension, and the process does not involve network transmission.
(3) The decrypted private key is loaded into memory, used only for signing, and the password and private key always remain on the device. Even if the device is physically accessed, the wrong password cannot decrypt it.
- Browser Permission Restrictions
The browser manages the web page and Phantom separately, and the web page cannot read Phantom's data.
(1) The web page runs in the HTTP/HTTPS domain, while Phantom runs in the extension domain (chrome-extension://), restricted by the Same-Origin Policy, belonging to different origins.
(2) Based on Chromium's multi-process architecture, the web page and the extension are allocated to independent processes, and sandbox isolation ensures that memory spaces do not share, preventing the web page from reading Phantom data.
(3) The browser restricts the web page from calling the extension's dedicated APIs (such as chrome.storage), and it cannot access Phantom's IndexedDB storage.
- APIs Do Not Transmit Passwords
When the web page interacts with Phantom, it can only obtain the wallet address and signature results, without involving passwords.
(1) When calling window.solana.connect(), Phantom only returns the public key, without involving the password or unlock status.
(2) When calling window.solana.signTransaction(), Phantom receives the transaction data, signs it locally, and returns the result, with the entire process not exposing the password.
(3) These APIs follow the principle of least privilege in Web3, designed to provide only necessary functions, preventing password or private key leakage.
III. The Web Cannot Technically Obtain the User's Private Key
- Private Key Generation and Encrypted Storage Are Completely Localized
The private key is generated by the Phantom wallet and encrypted for storage in the user's local environment, and the web page cannot access it directly.
(1) Generation: When the user installs the wallet, Phantom uses the BIP-39 standard (generating a mnemonic phrase from random entropy, then deriving the private key through HMAC-SHA512) to create the private key (64-byte random number) locally.
(2) Encrypted Storage: The private key is immediately encrypted using AES-256-CBC, with the key derived from the user password (PBKDF2, high-frequency iterations), stored in IndexedDB (path like chrome-extension:///IndexedDB).
(3) Permanence: Once generated, the private key is permanently retained locally unless the user actively deletes the wallet data, which is different from the temporary input of the password (used and discarded).
- Browser Security Model Isolates Private Key Storage
The browser isolates private key storage through sandbox and permission mechanisms, preventing the web page from breaching system-level restrictions. This is similar to reading passwords, as the browser restricts the web page from reading local passwords and private keys.
(1) Sandbox Isolation: The web page runs in the HTTP domain ([like yourwebsite.com](http://like yourwebsite.com)), while the Phantom wallet runs in the extension domain (like chrome-extension://), restricted by the Same-Origin Policy.
(2) Process Separation: The Chromium kernel allocates the web page and the extension to independent processes, with physical isolation of memory and storage space.
(3) Permission Restrictions: The web page's JavaScript cannot access the extension's IndexedDB (indexedDB.open is denied), nor can it read the local file system.
- The Private Key Is Only Temporarily Decrypted for Local Signing
The private key is only temporarily decrypted for local signing, not exposed to the web page or external entities.
(1) Decryption: When the web page calls window.solana.signTransaction(transaction), the Phantom wallet decrypts the private key using the user password (AES decryption), and the decrypted private key is loaded into the extension's memory.
(2) Signing: The transaction data is signed using ECDSA (Ed25519 curve), generating a 64-byte signature value, with the process completed locally.
(3) Destruction: After signing, the private key is cleared from memory (JavaScript garbage collection, delete privateKey or go out of scope).
(4) Data Flow: The web page only receives the signature result, without touching the private key.
- APIs and Network Communication Do Not Involve the Private Key
The APIs and transaction processes of the Phantom wallet ensure that the private key does not enter the web page or network layer.
(1) API Restrictions:
a. window.solana only provides functional interfaces (such as connect() returning the public key, signTransaction() returning the signature), with no getPrivateKey() method.
b. Communication occurs through memory interaction (window object), without generating network requests.
(2) Network Verification:
a. When submitting a transaction, the web page sends the signed transaction to the RPC node via HTTPS request (such as POST https://api.mainnet-beta.solana.com).
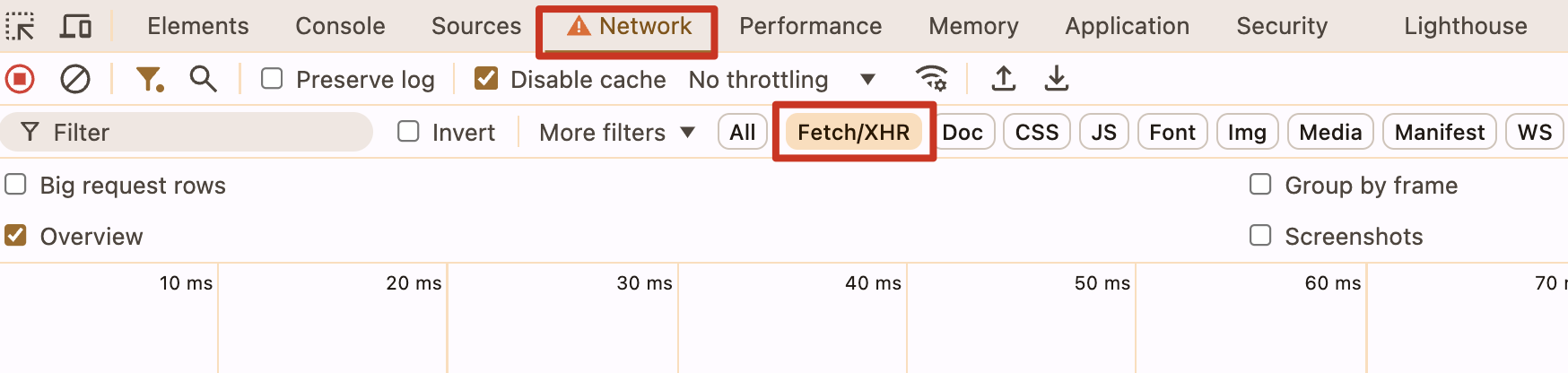
b. Users can verify through the Chrome browser: right-click "Inspect" (click F12) → "Network" → "Fetch/XHR". Initiate a transaction and check the request (excluding requests from third-party RPCs like Helius querying on-chain data).
c. Result: The request body only contains the serialized transaction (public key + signature), with no private key (64 hexadecimal characters).
IV. Situations Where Passwords and Private Keys May Be Stolen
- Malware Attacks
Devices infected with keyloggers, screen recording tools, or memory scanning programs capture the user's input password or extract the private key and mnemonic phrase from memory during transaction signing.
- Phishing Attacks
Users are induced by disguised websites, fake wallet interfaces, or malicious plugins to input passwords, private keys, or mnemonic phrases, directly leaking them to attackers.
- Device Compromise
Devices are physically stolen or remotely hacked, and attackers unlock private keys by brute-forcing weak passwords or read the encrypted private key files in IndexedDB and crack them, even obtaining mnemonic phrases stored insecurely.
- Improper Export
Users actively export private keys or mnemonic phrases (such as copying to the clipboard or saving as plain text files), which may be intercepted by malware or others.
- Malicious DApps
Connecting to malicious decentralized applications that induce users to sign through forged transactions or vulnerabilities, indirectly exposing private keys or mnemonic phrases.
- Unsafe Environments
Operating wallets on public computers or insecure Wi-Fi, where passwords, private keys, or mnemonic phrases may be intercepted or recorded.
- Backup Leaks
Improper backup of mnemonic phrases (such as taking photos and storing them in the cloud, or writing them in insecure places) may lead to others obtaining them and restoring the private key.
- Choosing Third-Party Audit Compliant Websites
Users can use websites that have undergone third-party audit compliance (such as platforms certified by ISO or SOC) to reduce the risk of passwords, private keys, and mnemonic phrases being stolen, as these websites typically adhere to strict security standards and data protection measures.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




