This article is from a submission and does not represent the views of ChainCatcher, nor does it constitute any investment advice.
I. Outlook
1. Summary of Macroeconomic Trends and Future Predictions
Last week, the latest report from the U.S. Department of Labor showed that July employment was far below expectations, compounded by significant downward revisions to the data from the previous two months. Market confidence has been severely impacted, with investors worried that the momentum of economic recovery is fading. Negative news regarding tariffs and employment has heightened uncertainty about when the Federal Reserve will cut interest rates, and Trump's own questioning of the employment data has further intensified market unease. The macroeconomic trend in the U.S. is clearly one of "weak recovery, strong risk." The sharp decline in U.S. stocks on August 1 was driven by worsening employment data and a new round of large-scale tariff policies. The economy may continue to face the dual challenges of slowing growth and high inflation, with policy uncertainty continuing to dominate market sentiment.
2. Market Movements and Warnings in the Crypto Industry
The overall crypto market experienced a sharp correction after a period of high volatility, with Bitcoin's price dropping from a near $120,000 high to about $112,000, indicating a significant rise in short-term risk sentiment. Ethereum and some unlocked tokens have seen increased volatility due to selling pressure, with institutional funds showing mixed performance; some large holders adjusted their positions but still engaged in accumulation. Macroeconomic headwinds such as weak U.S. employment data and escalating tariff policies have intensified market risk aversion, leading to capital flowing out of risk assets. In the short term, it is necessary to be cautious of a deeper correction triggered by the loss of key support levels, while in the medium to long term, attention should be paid to the continued positioning of institutions and the potential for upgrading quality project ecosystems.
3. Industry and Sector Hotspots
Aspecta is a blockchain infrastructure designed to provide intelligent certification and price discovery mechanisms for trillions of dollars in illiquid assets; Datagram is a Global Hyper-Fabric Network aimed at supporting next-generation real-time connection applications and decentralized physical infrastructure networks (DePIN).
II. Market Hotspot Sectors and Potential Projects of the Week
1. Overview of Potential Projects
1.1. Brief Analysis (Led by YZiLabs) Aspecta—A Network for AI Developer Identities Bridging Web2/Web3
Introduction
Aspecta is a blockchain infrastructure aimed at providing intelligent certification and price discovery mechanisms for trillions of dollars in illiquid assets. It unlocks liquidity for the entire lifecycle of pre-TGE shares, locked tokens, unlisted equity, and real-world assets (RWA).
Architecture Overview
- BuildKey: A liquidity entry point for quality assets through bonding curves
The operation of BuildKey is as follows:
- Participate in the issuance of reviewed projects/assets launched by BuildKey;
- Trade BuildKey through the bonding curve mechanism;
- Exchange BuildKey for various assets: pre-TGE shares, locked tokens, NFTs, unlisted equity, etc.
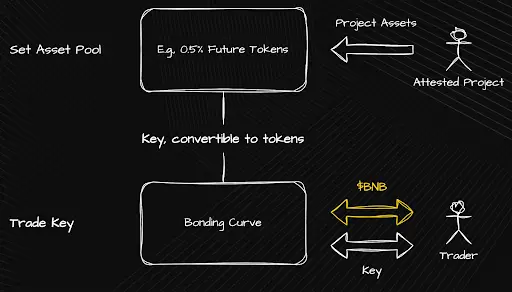
A Fair Launch: Early Key Subscription Mechanism
Aspecta has designed a special launch mechanism aimed at providing everyone with a fair opportunity to purchase early BuildKeys and prevent bot abuse.
Key Points: In the first 30 minutes after a project pool launches (specific timing varies by project), it will be in "Deposit" mode.
During this phase, the system will randomly select transaction executions without considering transaction order, gas price, or payment amount.
Participation in subscriptions, receiving BuildKeys, or refunds requires no permissions; anyone can participate.
To further prevent bots, users verified through Proof of Humanity (PoH) will be eligible to join premium deposit groups.
Mechanism Explanation
In the first 30 minutes after the project pool launches, the pool will be in "Deposit Mode."
Traders must pre-deposit refundable funds to submit subscription orders.
Each address is limited to submitting 1 order, with a maximum of 20-100 BuildKeys per order (specific quantity depends on the project and the subscription group).
All orders will be randomly selected, sorted, and executed. This means that regardless of the gas price of the transaction or the timing of submission, participants will be treated equally.
If subscriptions exceed demand, the number of Keys allocated to each successful order will be dynamically adjusted based on the oversubscription ratio, allowing more users to have the opportunity to obtain early Keys.
After the subscription ends, users will instantly see:
- Total oversubscription ratio
- Number of Keys available for collection
- Amount of refundable funds
Collecting Keys and refunds are permissionless and free of charge; users only need to click the "Claim" button on the subscription results page.
To prevent bots from affecting real community users, those verified through PoH can join the Premium Deposit Group. Ways to complete PoH verification include:
- Manually completing PoH tasks,
- Or obtaining an Aspecta community badge,
- Or completing previous PoH tasks from Aspecta's pre-launch.
B Trading
BuildKey trades using a bonding curve, a mechanism designed to be "upgradable," benefiting both existing holders and new users.
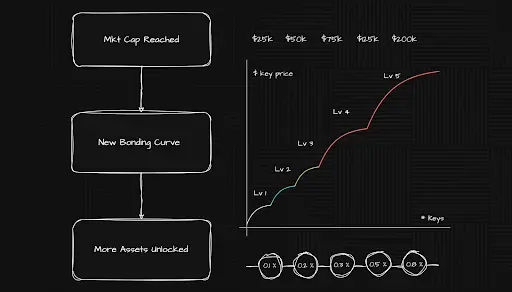
Bonding Curve Mechanism Explanation
Bonding Curve Upgrade When the market value of BuildKey reaches a new milestone, the bonding curve will enter a new phase, creating new price growth opportunities for all users.
Asset Exchange Ratio Upgrade As the market value of the target asset grows, the asset exchange ratio corresponding to BuildKey will also increase.
That is: The more BuildKeys purchased, the higher the asset value that each BuildKey can be exchanged for.
Once the exchange ratio is upgraded, it will automatically apply to all BuildKeys, including those that have already participated in the exchange.Market Value Calculation Method Current market value of BuildKey = Total circulating supply (total number of Keys held by users) × Current price.
Asset Exchange Mechanism
The core idea of BuildKey is to achieve public price discovery of illiquid assets through the trading and holding of Keys. In return, Key holders can gain participation opportunities in the early stages of rapid asset growth.
Project parties and stakeholders can provide assets or rights to BuildKey holders in various ways.
- Types of Assets
The forms of redeemable assets are diverse, including:
- Pre-TGE Shares
- Locked Tokens
- NFTs
- Private Equities, etc.
As these assets further develop and approach potential liquidity events (such as TGE, IPO, etc.), their value typically increases rapidly.
- Ways to Obtain Assets
Users can obtain assets from project parties/stakeholders in two ways:
- 2.1 Exchange assets using BuildKey (supporting upgraded Key-asset exchange ratios)
- 2.2 Hold BuildKey to automatically receive holder benefits
Upgradable Asset Redemption
- Redemption Start:
Click the "Redeem" button to exchange assets using BuildKey. After redemption, BuildKey will be transferred to the wallet address of the project/stakeholder. - Redemption Ends:
The system will take a snapshot. To ensure users can obtain assets at TGE, redemptions typically end before TGE. Unexchanged BuildKeys can still be traded in the market. - Asset Collection:
Users can collect assets on the project page or have them directly transferred to their wallets by the project party. - Redemption Deadline:
If the Redemption Deadline is missed, BuildKey can no longer be exchanged for assets but can still be used for market trading and profit. - Purchase Deadline:
Some projects may have a purchase deadline. After this time, BuildKey can no longer be purchased, but existing BuildKeys can still be used to exchange for assets or trade for profit.
Exchange ratio upgrade:
As the market value of the target asset grows, the exchange ratio corresponding to Keys will also upgrade. Already exchanged BuildKeys will also automatically receive the ratio increase.
Commentary
Aspecta builds a developer identity network through AI technology, combining data from Web2 (such as GitHub, Twitter) and Web3 (such as wallet addresses) to generate quantifiable developer profiles, supporting over 8000 skill dimensions and experience highlights, helping individuals gain higher visibility and credit endorsement in decentralized ecosystems. At the same time, Aspecta also achieves price discovery and early participation opportunities for illiquid assets (such as locked tokens, unlisted equity, etc.) through BuildKey and the bonding curve mechanism. Its advantages lie in integrating AI, identity, and asset mechanisms, bridging multi-chain developer social and financing paths;
However, its disadvantages include that PoH verification, KYC, and other compliance requirements may limit participation from some users, and the reliance on AI models for identity assessment also poses risks of accuracy and bias.
1.2. Interpreting the $4 million funding of Datagram—Decentralized connection infrastructure for real-time applications powered by AI
Introduction
Datagram is a Global Hyper-Fabric Network designed to support next-generation real-time connection applications and decentralized physical infrastructure networks (DePIN). Such applications rely on real-world resources like computing power, bandwidth, and storage. Datagram simplifies the launch and scaling of such applications and networks without the need to build complex infrastructure.
The platform rewards Datagram node operators in the following two main ways:
- Online Duration and Availability: Operators who keep their nodes online and responsive will receive rewards to ensure the stability and reliability of the entire network.
- Actual Usage: Nodes that actively contribute resources (such as computing power, bandwidth, etc.) to support real-time applications will receive corresponding rewards based on their level of contribution.
Datagram is designed for three core user groups:
- Web2 and Web3 Enterprises: Traditional businesses and blockchain projects can access Datagram's decentralized services through simple APIs or SDKs without needing in-depth blockchain technical knowledge.
- Existing DePIN Networks: Projects with established node infrastructure can integrate Datagram through the Datagram Core Substrate (DCS) to expand their bandwidth, computing, and storage capabilities.
- Emerging DePIN Projects: Startups or developers can leverage the one-stop infrastructure provided by Datagram to quickly launch decentralized networks.
Architecture Overview
Datagram is a Layer 1 network built on Avalanche, specifically designed to support real-time applications, providing scalable, decentralized, and cost-effective computing, bandwidth, and storage access services. Its architecture simplifies the complexity of decentralized systems while retaining the advantages of blockchain (such as security, interoperability, and efficiency), offering a Web2-like user experience.
Datagram also supports decentralized physical infrastructure networks (DePIN) through its connection layer, Datagram Core Substrate (DCS), with the core mission of providing easily accessible decentralized infrastructure for applications with high-performance connectivity needs. Currently, it supports EVM-based networks and will expand to non-EVM compatibility in the future.
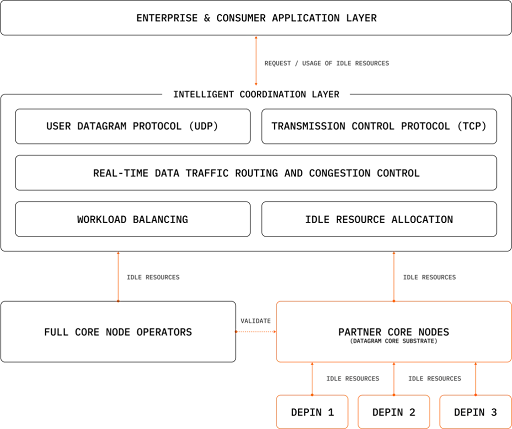
The architecture of Datagram consists of four key components that work together to provide low-latency, secure, and high-throughput infrastructure capabilities:
Datagram Node Network: The backbone of Datagram, composed of distributed nodes (Datagram Cores) responsible for routing, validation, and data transmission, supporting both native and external DePIN projects, providing decentralized computing, bandwidth, and storage resources.
Fabric Networks: Independent DePIN networks integrated with Datagram infrastructure, maintaining specialized operations while sharing resources, achieving scalability and interoperability.
Datagram Core Substrate (DCS): The connection layer that coordinates the computing, bandwidth, and storage resources of the entire network and integrates with the Network Operations Center (NOC) for real-time performance monitoring and reward distribution.
Hyper Network Layer: An AI-driven coordination system that intelligently manages routing, load balancing, and resource allocation in real-time, ensuring low latency and fault tolerance.
Datagram Node Network
The Datagram node network is the core infrastructure of the entire Datagram ecosystem, composed of globally distributed nodes that provide decentralized computing, bandwidth, and storage resources. It supports both native DePIN projects and external projects without the need to build their own infrastructure.
Core Features:
Multiple Node Types (Datagram Cores):
Full Cores: Main nodes responsible for traffic routing and network load optimization, required to hold Core Tokens, supporting high-concurrency scenarios, and rewarded based on performance and resource contribution.
Partner Cores: Assist main nodes in handling peak traffic, ensuring network stability under pressure.
Device Cores: Utilize idle computing power from IoT devices (such as routers, sensors, etc.) to contribute resources, enhancing overall efficiency.
Hardened Cores: Handle communications with high-security requirements, such as government and corporate data, equipped with enhanced encryption and data protection.
Consumer Cores: Operate on personal or small organization devices, temporarily contributing resources to support localized services.
Scalability and Flexibility: Supports rapid deployment and seamless integration with existing DePIN networks without requiring blockchain expertise.
Chain-Agnostic Integration: Built on Avalanche as a Layer 1, currently supports EVM networks, with plans to support non-EVM networks in the future.
High-Performance Data Transmission: Nodes collaboratively build a parallel computing network similar to a Beowulf cluster, ensuring low latency and fault tolerance, suitable for real-time tasks such as video conferencing and AI computing.
- Fabric Networks
Fabric Networks are independent DePIN networks that achieve high-performance operation and rapid expansion of their applications by accessing Datagram's infrastructure (computing, bandwidth, storage).
Key Features:
- Interoperability: Seamlessly connects to the Datagram network through Datagram Core Substrate (DCS), enabling resource sharing and cross-network communication.
- High Customizability: Each Fabric Network can customize its operational logic based on its specific scenario, such as decentralized AI computing or real-time communication, while utilizing Datagram's global infrastructure.
- Independent Execution Environment: Equipped with an independent execution system to avoid resource competition and ensure stable performance.
- Plug-and-Play Expansion: Can immediately use distributed resources upon integration without building infrastructure from scratch.
Role in the Ecosystem:
Fabric Networks allow DePIN projects to focus on their core business logic while leaving the underlying computing and transmission capabilities to Datagram. For example, a decentralized video streaming service could operate as a Fabric Network, leveraging resources provided by Datagram for data transmission and storage while maintaining its brand and user experience.
- Datagram Core Substrate (DCS)
DCS is the core connection layer of the Datagram network, providing underlying support for the decentralized scheduling and coordination of computing, bandwidth, and storage resources, helping any DePIN project to quickly launch and expand without building its own network.
Key Features:
- Resource Coordination: Smartly allocates workloads and network traffic based on real-time demand, optimizing performance while maintaining interoperability with the entire Datagram network.
- Network Operations Center (NOC): Integrated with DCS to monitor node online rates, performance, and resource usage, automatically distributing node rewards.
- Modular Architecture: Utilizes containerized deployment (Docker), allowing developers to deploy custom workloads in parallel with the core network.
- Chain-Agnostic Deployment: Supports deployment on both EVM and non-EVM networks (such as Avalanche, Solana, Ethereum L2), enhancing cross-chain compatibility and flexibility.
- Simple Integration: Abstracts the complexity of the underlying blockchain, allowing developers to focus on application building without managing cumbersome infrastructure.
Core Functions:
DCS essentially serves as a decentralized service mesh, supporting project parties or developers in deploying custom node networks on top of Datagram's global infrastructure.
For example, a company building a decentralized AI training platform can intelligently allocate training tasks to nodes located in different geographical areas worldwide through DCS, while the NOC monitors node status in real-time and automatically distributes rewards to ensure stable operation.
- Hyper Network Layer
The Hyper Network Layer is the AI-driven coordination system of the Datagram network, used to achieve intelligent routing, real-time optimization, and parallel processing across the entire infrastructure. Unlike traditional DePIN networks with static node configurations, it enables dynamic and efficient infrastructure orchestration.
Key Features:
- Adaptive Traffic Routing: Monitors network status in real-time, automatically directing traffic to optimal nodes to avoid congestion and reduce latency.
- Real-Time Load Balancing: Dynamically allocates computing resources based on actual network load, avoiding bottlenecks caused by static configurations.
- Intelligent Resource Allocation: Predicts network usage patterns and pre-allocates computing, bandwidth, and storage resources to prevent resource congestion.
- Automatic Network Recovery: Can immediately reroute when nodes or subnets fail, ensuring uninterrupted service and enhancing network resilience.
- Large-Scale UDP Optimization: Unlike most decentralized networks that only support TCP, Datagram natively supports large-scale UDP, suitable for real-time high-frequency scenarios such as video streaming, multiplayer gaming, and AI processing, with significant performance advantages.
Ecosystem Role:
The Hyper Network Layer is a core component that enables Datagram to outperform traditional DePIN architectures, acting as a dynamic AI controller within the network, allowing enterprises and project parties to customize dedicated subnets within its global network while enjoying built-in security, scalability, and integrability.
Commentary
Datagram, built on Avalanche, provides scalable, low-latency, decentralized support for computing, bandwidth, and storage for real-time applications. It adopts a modular architecture with a Hyper Network AI scheduling layer, DCS connection layer, cross-chain support, and multiple types of node networks, balancing performance and resilience, suitable for Web2/Web3 enterprises and DePIN projects. At the same time, its abstracted design lowers the development threshold, offering a user experience close to Web2. However, its reliance on AI-driven network management and UDP optimization protocols imposes high technical requirements on overall system coordination and scheduling, making initial deployment and maintenance more complex. Additionally, while building on Avalanche Layer 1 enhances performance, it may limit seamless integration with some non-EVM ecosystems, and the actual ecological implementation will still require time to verify its stability and network effects.
2. Key Projects of the Week
2.1. Detailed Analysis of Zypher Network (Raised $7 million, with participation from Hashkey) — Cross-Chain Zero-Knowledge Driven Decentralized AI and Gaming Infrastructure
Introduction
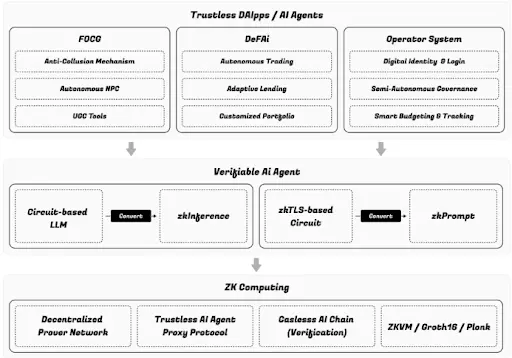
Zypher Network has launched a decentralized cryptographic trust layer designed specifically for autonomous AI agents. By introducing innovative mechanisms such as Proof of Prompt, zkPrompt, zkInference, zkTLS (zero-knowledge transport layer security protocol), and the Zytron AI chain, Zypher enables verifiable, private, and auditable AI interactions across multiple domains.
The network utilizes zero-knowledge proof technology to ensure that AI agents maintain consistency and security without disclosing sensitive data. Its modular infrastructure, which includes a decentralized prover network and multi-execution engine support, provides excellent composability, scalability, and real-world interoperability, making it suitable for various application scenarios such as decentralized finance, gaming, AI compliance, and digital labor.
Feature Analysis
Zypher Network introduces a complete set of cryptographic protocols and infrastructure components aimed at providing verifiability, privacy protection, and integrity assurance for the operation of autonomous AI agents. Each layer of the Zypher technology stack addresses different aspects of AI trust issues: including verifying the integrity of prompts, ensuring the consistency of encrypted communications, implementing scalable proof generation mechanisms, and anchoring these proofs to decentralized infrastructure, thereby building a trustworthy, secure, and auditable AI operating environment.
1. Proof of Prompt Mechanism
Proof of Prompt is the core protocol of Zypher Network, designed to ensure that the prompts sent to AI models and their returned results possess verifiability in terms of authenticity, consistency, and integrity. This mechanism allows external observers to verify that a specific AI agent indeed received a particular prompt and generated the corresponding output—without exposing the specific content of the prompt or the output itself.
This mechanism is achieved through mixed encryption techniques, including:
- Symmetric Encryption (such as AES, ChaCha20): Used for efficient data obfuscation;
- Zero-Knowledge Proofs (ZKP): Used to verify actions without disclosing content;
- Commitment Schemes: Ensure data integrity.
Ultimately, this results in a lightweight, privacy-protecting verification method that can be widely applied in scenarios such as automated finance, DAO governance, Web3 gaming, and identity management.
Proof of Prompt effectively addresses the challenge of "black box operations" in AI systems—it ensures through encryption that the behavior of AI agents indeed originates from a clear, unaltered set of instructions, laying a trustworthy foundation for more advanced applications of Zypher.
- zkPrompt (Zero-Knowledge Prompt Verification)
In large language models (LLMs), prompts are typically divided into system prompts and user prompts. The system prompt is set by developers to define the model's context, tone, and behavioral boundaries, serving as a key factor in guiding the AI's performance style and stability. Therefore, the system prompt has become one of the core capabilities in LLM development, and developers are generally reluctant to disclose its content.
However, since many LLMs operate in a "black box" manner, external users find it difficult to verify the consistency of the system prompt (i.e., whether the model consistently operates based on the same system prompt), making behavior predictability and trust challenging to ensure.
To address this, Zypher proposes zkPrompt—a verification mechanism based on zero-knowledge proofs that can verify whether the system prompt used during model initialization is consistent with the original settings without disclosing the content of the system prompt.
The implementation is as follows:
- Construct the model initialization process as a zero-knowledge circuit;
- Add a commitment module in the circuit to generate a commitment value for the system prompt used;
- Verify that the system prompt used in the model is consistent with the commitment value in the circuit and publicly output that commitment value;
- External users can verify whether the system prompt has been tampered with based on that commitment value, thus determining whether the model's behavior is consistent.
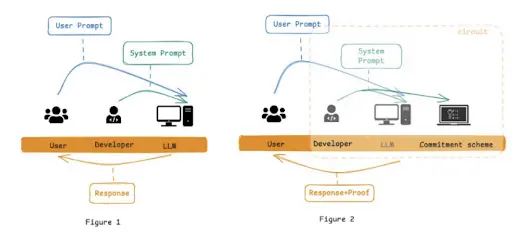
Cryptographic Commitment is a protocol that allows one party to commit to a value without revealing the specific content to the other party until the committing party chooses to disclose it. Common commitment mechanisms include hash commitment and Pedersen commitment.
In zkPrompt, the core value of this mechanism is reflected in two aspects:
- Developers can keep the content of the system prompt confidential (unknown to the outside world);
- Once the commitment is made, the content of the system prompt cannot be changed, thus ensuring the integrity and trustworthiness of the system prompt.
Overall Process:
- Developers make a cryptographic commitment to the system prompt and send the commitment value on-chain;
- Initialize the zk circuit, generating Prover keys and Verifier keys, with the Verifier key also sent on-chain;
- Users submit user prompts;
- The large language model generates response content and the corresponding zero-knowledge proof, sending both to the chain;
- The smart contract verifies the zk proof using the original system prompt commitment value;
If the verification passes, it indicates that the system prompt has not been tampered with since submission.
2.1 zkPrompt System Design
The zkPrompt protocol designs an efficient and feasible way to verify the outputs of large language models (LLMs) using zero-knowledge proofs (ZKP), without requiring users to directly interact with the model service.
The system consists of four key roles: User, Prover, Proxy, and LLM Provider. Even in the presence of untrustworthy intermediaries, zkPrompt ensures the authenticity and integrity of the model's responses.
This system verifies whether the Prover faithfully relays the model output through cryptographic signatures and proof generation mechanisms, while supporting a privacy protection mode that completes verification without disclosing the prompt or response content.
Compared to traditional ZKML frameworks, the zkPrompt architecture significantly reduces computational overhead and aligns more closely with the actual trust models of current mainstream LLM providers.
2.2 zkPrompt Protocol Concept and Comparison
zkPrompt draws inspiration from zkTLS by embedding zero-knowledge proofs (ZKP) into the interaction process between users and large language models (LLMs) to ensure the authenticity and integrity of response data.
In the protocol, the user's request is forwarded to the LLM provider through the Prover and Proxy, and the response is returned along the same path. However, TLS communication only occurs between the Prover, Proxy, and LLM, leaving the user unable to directly participate in verification, creating a trust blind spot.
To address this issue, zkPrompt requires the Prover to provide a zero-knowledge proof to prove that the response indeed comes from a genuine LLM and has not been tampered with.
This mechanism significantly enhances the security and credibility of AI agent responses, especially suitable for high-risk scenarios such as on-chain asset management, trading bots, and financial agents.
2.3 Trust and Security Assumptions
The protocol assumes that there is no collusion between the Proxy and the Prover. To enhance the robustness of the system, it is recommended to decentralize the Proxy in actual deployments to prevent single points of failure or abuse.
The current design also assumes that prompts and responses are stored on-chain in plaintext (a privacy-protecting version will be introduced in the future to address this issue).
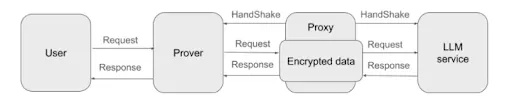
2.4 Technical Challenges and Core Solutions
How to ensure that the encrypted response returned by the Prover indeed comes from the LLM and is not fabricated?
Solution: Proxy Signature + Zero-Knowledge Proof
After the Proxy receives the encrypted response from the LLM, it signs it and sends the encrypted content along with the signature on-chain;
The Prover generates a ZKP (zero-knowledge proof) to prove:
The decrypted content indeed contains the user's prompt;
The response content is authentic and has not been tampered with.
The core of this process is the correct decryption verification of symmetric encryption, which is efficient and can be implemented based on solutions like Dubhe.
Verification Steps (Three Steps)
- Verify the Proxy's signature on the ciphertext;
- Check whether the decrypted content contains the user's prompt;
- Verify the validity of the zero-knowledge proof provided by the Prover.
After completing these steps, anyone (such as miners or nodes) can be assured that the response is authentic and trustworthy.
Privacy Protection
If users wish to protect the privacy of the prompt and response content:
- Only the hash values of the prompt and response are stored on-chain, rather than the original text:
- H1 = Hash(prompt)
- H2 = Hash(response)
- And add the constraint: the response contains a fragment of the prompt
The Proxy still stores the ciphertext on-chain;
The Prover provides ZKP to prove:
- Hash(witness) = H2 (response content is correct);
- Hash(witness[i:j]) = H1 (the response indeed contains the prompt);
- Decrypt(ciphertext) = witness (decryption is correct)
This privacy version can complete verification without exposing any sensitive content, making it very suitable for scenarios with high compliance requirements.
- zkInference Framework: Bringing Verifiability and Fairness to Web3 AI Agents
Currently, many AI agents operate in Web3 as "black boxes," lacking transparent reasoning processes, which makes their behavior difficult to verify, especially in multiplayer competitive games, where there is a risk of AI collusion and cheating.
3.1 zkInference Solution
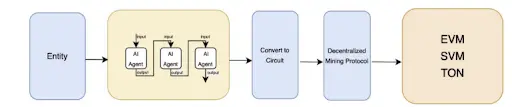
The zkInference framework ensures that AI agents strictly operate according to predefined models and specifications using zero-knowledge proof algorithms, achieving the following goals without disclosing the model and data:
- Verifiability: Verify whether AI decision-making behavior is authentic and compliant with rules;
- Anti-Collusion: Prevent multiple agents from colluding, ensuring fairness in games;
- Infinite Computing Power: Provide a decentralized computing market to support large-scale verifiable AI computations.
3.2 zkTLS (Zero-Knowledge Transport Layer Security Protocol) zkTLS is a protocol that Zypher uses to verify the content and consistency of TLS sessions through zero-knowledge encryption technology. Traditional TLS is confidential but cannot be externally verified; zkTLS addresses this issue.
Three deployment modes:
- TEE (Trusted Execution Environment) mode: High fidelity but requires dedicated hardware;
- MPC (Multi-Party Computation) mode: More decentralized but with high performance overhead;
- Proxy mode: High performance, low hardware requirements, suitable for most practical applications.
Zypher's zkPrompt uses the proxy mode to ensure that prompts and responses between users and models remain consistent in encrypted sessions.
3.3 Zytron: On-Chain AI Execution Engine Zytron is Zypher's on-chain AI computation and verification layer, responsible for distributed coordination and orchestration of zkPrompt and zkTLS proofs.
Features include:
- Efficient routing and load balancing using Kademlia DHT;
- Cross-node coordination for proof generation and verification;
- Task allocation based on node distance and historical performance;
- On-chain recording of immutable verification interactions and AI decisions.
Zytron is the core support for Zypher's verifiable AI system.
3.4 Decentralized Prover Network This network supports the scalable generation and verification of zero-knowledge proofs, avoiding reliance on centralized servers and ensuring trust in a decentralized manner.
Features:
- Any qualified node can contribute computing power;
- Prevent cheating through reputation and staking mechanisms;
- Zytron coordinates task allocation and result verification.
This network ensures that verification is both efficient and decentralized, supporting internet-level AI verification.
3.5 Composability and Integration Zypher's modular protocol stack facilitates cross-domain integration, allowing developers to flexibly combine components to build trustworthy AI applications.
Application examples:
- Embedding zkPrompt into LLM-based API gateways;
- Using zkTLS as a privacy-protecting data integrity layer for AI assistants;
- Utilizing Proof of Prompt for AI governance proposal verification in Web3 DAOs;
- Anchoring AI interactions to on-chain smart contracts through Zytron.
This composability makes Zypher both a foundational protocol layer and a toolkit for developers to build trustworthy AI.
- Zytron AI Chain
Zytron is the high-performance on-chain AI computation execution layer of Zypher Network, supporting scalable, low-latency, and verifiable AI computations, compatible with the Web3 ecosystem. It supports zk proofs, AI agent logic combinations, and flexible state execution.
4.1 Web3 Compatible Interface Zytron provides a dual-interface system, maintaining compatibility with Ethereum while optimizing transaction latency, state addressing, and proof generation. Developers can interact with Zytron using common tools like MetaMask and Hardhat, enjoying its performance and verification advantages.
4.2 Multi-Execution Engine Support Supports the parallel operation of various smart contract execution models:
- EVM-compatible Solidity contracts;
- UTXO model supports lightweight parallel transaction flows.
Different address state groups can be allocated different execution models, with plans to support WASM in the future.
4.3 Zero Gas Transactions Natively supports ERC-4337 account abstraction, allowing zero gas transactions through proxy sponsorship, lowering the interaction threshold between users and AI agents, and supporting customized fee logic.
4.4 Native Cross-Chain Bridge The modular sharding architecture supports efficient and secure cross-chain asset transfers. By locking assets through bridge contracts, Zytron shards map and mint native wrapped assets, enhancing security with zero-knowledge proofs, enabling cross-chain AI agent interactions.
4.5 Data Sovereignty Rollup
- Sequencer is responsible for transaction ordering and packaging, forming Layer 2 blocks and batches, utilizing Merkle trees to broadcast data roots, submitting to a weak data availability layer, and ultimately confirming batches through PBFT consensus.
- External Data Availability Layer (DA) is divided into strong and weak categories, with weak DA used for rapid transmission and strong DA for final on-chain execution verification.
- Sequencer Pending State maintains a local pending state to meet low-latency game requirements, allowing users to continuously submit transactions for a smooth experience.
- Asset zk-Rollup uses Merkle trees to store asset transactions, supporting deposits, withdrawals, and transfers, employing the UTXO model and zero-knowledge proofs to ensure transactions are instant and valid, avoiding long challenge periods.
- Service Sharding enables low-latency game services by executing on-chain contracts through sharding.
- Kademlia Node Data Sharding allocates contract execution tasks based on node distance using the Kademlia DHT algorithm, with nodes registering and synchronizing states to support decentralized collaboration.
- Address State Group execution nodes only store states related to the addresses closest to them, with address state groups updated locally using BFT algorithms to ensure data security for offline nodes.
- Transaction Space Access List requires transactions to include state change information (balance, Nonce, storage, etc.) to ensure correct sharding processing; exceeding access limits results in transaction failure.
- Key Space Estimation provides estimation functionality to help clients mark space access restrictions, simulating execution of contracts to generate access ranges.
- Customized Network optimizes the P2P network, using a UDP-based KCP protocol to reduce latency, designing a stable dual-layer DHT structure and relay algorithm to ensure stable and low-latency node connections, meeting high-frequency game demands.
Conclusion
Zytron, as a high-performance execution layer for decentralized AI computation and gaming applications, excels in supporting multiple execution engines (EVM and UTXO), providing a zero gas transaction experience and native cross-chain capabilities, effectively ensuring low latency and data sovereignty, while employing innovative sharding and decentralized node architectures to enhance scalability and security; however, its complex distributed design and multi-layer data synchronization mechanisms may pose challenges for implementation and operation, resulting in a higher learning cost for developers.
### Industry Data Analysis
1. Overall Market Performance
1.1. Spot BTC vs ETH Price Trends
BTC
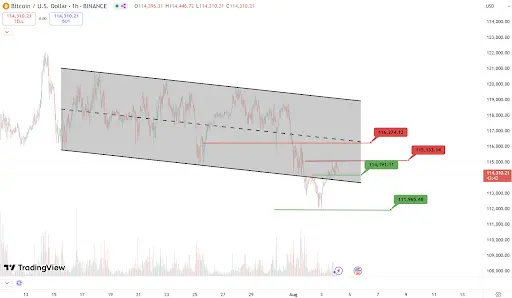
Analysis
Key support this week: $114,000, $111,900
Key resistance this week: $115,100, $116,200
ETH
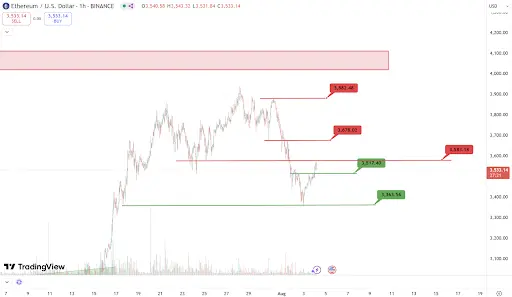
Analysis
Key support this week: $3,510, $3,360
Key resistance this week: $3,580, $3,680, $3,880
2. On-Chain Analysis
2.1. BTC Layer 2 Summary
This week, BTC Layer 2 has broken through the boundaries of Lightning payments and ecosystem entrepreneurship:
- GOAT demonstrated the feasibility of low-latency zk-Rollup technology through the BitVM2 testnet;
- LQWD injects capital and infrastructure into the Lightning network, co-building a global BTC payment channel;
- The Bitcoin Hyper project has strong presales, creating innovative paths for the BTC Rollup new ecosystem;
- The coupling of stablecoins and Lightning accelerates the expansion of mainstream application scenarios for BTC Layer 2;
- Lightning public capacity has reached an all-time high, making the overall ecosystem structure more robust.
2.2. EVM & Non-EVM Layer 1 Summary
Core Event Analysis
Injective's mainnet launch is imminent — As the first native EVM fully compatible new Layer-1, Injective has launched its mainnet testing environment and successfully processed its first transaction. The developer ecosystem is gradually becoming active, and INJ is expected to establish a new generation of high-performance Ethereum-compatible chain market capitalization expectations.
Shardeum testnet is online — Shardeum Unstablenet is its smart contract testing environment, emphasizing elastic scalability and developer-friendly deployment mechanisms. It has currently attracted initial application attempts, showcasing a new path for EVM chain construction.
Solana ecosystem enters a high growth phase — In July, its stablecoin transfer volume increased by over half year-on-year, reaching a scale of $215 billion, indicating Solana's impressive performance in user activity and DeFi scenario reshaping, with the average number of weekly active addresses exceeding the combined total of Ethereum and other L1s.
Hedera Hashgraph mainnet upgrade completed — On July 23, a functional upgrade was completed. Although it was only a minor version, it reflects Hedera's continued emphasis on enterprise-level applications in China and the maintenance of regulatory-compliant links, with a short and smooth maintenance window.
NEAR proposes core economic model reform — The NEAR community has initiated a proposal to set the original inflation rate at 5%, now suggesting a reduction to 2.5% to enhance the resilience and sustainability of the token model, which is expected to impact the staking yield mechanism and the behavior of long-term holders.
2.3. EVM Layer 2 Summary
- Linea: Airdrop and Deflationary Economics Take Off
- Total supply is approximately 7.2 billion, with 9% allocated for airdrops (active community users from Voyage) + 1% (strategic dapp and community builders). Actual investment accounts have filtered out Sybil risks, and no smooth lock-up has been set;
- This accounts for about 22% of the initial circulation, combined with the ecological fund lock-up, and future cost-reduction and burn mechanisms (20% ETH, 80% LINEA) may drive value capture and token burning resonance.
- ZKsync Accelerates Upgrade Track
- The technical improvements of Core v29.0.0 mainly focus on current branch compatibility, such as CLI access methods and bridge model integration;
- Inclusion of the Tokenized Asset Coalition (TAC) marks its response to institutional-level asset tokenization signals, potentially linking RWA, synthetic assets, and other financial products in the future;
- Era and ZKsync Gateway become a native interoperability layer, significantly reducing transaction friction between Era-Chains and laying the foundation for applications;
- The Security Committee proposal reduces annual budget expenditures by half, introducing an algorithmic mechanism to control mint cap (related to token market capitalization), demonstrating a commitment to governance integrity.
- Optimism's Market Temperature Test
- After listing Upbit to support KRW/OP trading pairs, local Korean users quickly entered, becoming the main driving force behind OP's recent rise;
- However, OP's unlock is set for July 31, and the proportion of unlocks to total supply remains largely unknown, requiring close monitoring of on-chain liquidity and price-volume relationships during this period;
- The market response represented by OP's recent increase indicates that the Optimism ecosystem still has attention that can be reached at both retail and institutional levels; however, it remains to be seen whether selling pressure will emerge after the unlock.
### Macroeconomic Data Review and Key Data Release Nodes for Next Week
In July, non-farm payrolls added only 73,000 jobs, significantly below market expectations. At the same time, employment data for May and June was significantly revised down, totaling a reduction of 258,000 jobs. The unemployment rate rose from 4.1% to 4.2%, with the long-term unemployed population increasing to 1,826,000, indicating a substantial deterioration in the overall job market.
This week (August 4 - August 8), important macroeconomic data nodes include:
August 7: Initial jobless claims in the U.S. for the week ending August 2.
### Regulatory Policies
United States: White House Releases Digital Asset Policy Report, SEC Launches "Project Crypto"
The White House policy team released a 160-page blueprint for cryptocurrency policy, proposing a legislative roadmap for digital assets, stablecoin regulatory reforms, promoting the exploration of a U.S. central bank digital currency (CBDC), and calling for the passage of the GENIUS Act and CLARITY Act within the next six months.
The chairman of the U.S. Securities and Exchange Commission (SEC) announced the launch of "Project Crypto," aimed at simplifying the regulatory path by clarifying token attributes and trading roles, supporting the compliance of tokenized securities, and improving market uncertainty.
The House of Representatives has passed the GENIUS Act (stablecoin regulation), the CLARITY Act (clarification of token regulation), and related bills opposing the federal issuance of CBDCs.
The GENIUS Act has received support from the Senate and is expected to enter the formal signing process in August, establishing a unified federal framework for stablecoin issuance within the U.S.
European Union: ESMA Promotes Formal Implementation of MiCA Framework
The European Securities and Markets Authority (ESMA) released an assessment, requiring member states to strengthen consistency in licensing reviews under the MiCA framework to avoid regulatory arbitrage.
At the same time, ESMA issued a consumer protection announcement, warning that non-compliant products must not be misleadingly advertised as "regulated assets."
The EU has also updated cybersecurity and KYC technical standards related to digital assets as pre-compliance requirements for MiCA.
Hong Kong: Stablecoin Regulatory Ordinance Officially Takes Effect
The Hong Kong Legislative Council passed the Stablecoin Ordinance, which took effect on August 1. The ordinance requires stablecoin issuers to be locally registered, maintain 100% reserves, prohibit the issuance of algorithmic stablecoins, and includes a six-month transition buffer period.
The Hong Kong Monetary Authority (HKMA) released a draft implementation guideline, with the first batch of issuance licenses expected to be issued in early 2026.
Indonesia: Major Restructuring of Cryptocurrency Taxation System
Starting August 1, Indonesia has increased tax rates related to cryptocurrency transactions, including: transaction tax raised from 0.1% to 0.21%, miner VAT tax rate increased to 2.2%, and cross-border seller tax rate reaching 1%.
The new system also includes cryptocurrency traders in the regular tax collection framework, incorporating them into corporate income tax or personal income tax systems, marking the formal inclusion of cryptocurrency assets into a comprehensive tax framework.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




