When the loyal messenger was weaponized—mark price, this fair judge became the fuse that ignited the Hyperliquid chain liquidation storm.
In March 2025, a little-known token with a daily trading volume of less than $2 million—JELLY—triggered a multi-million dollar liquidation storm on Hyperliquid. Shockingly, the attacker neither tampered with the smart contract nor exploited traditional code vulnerabilities, but instead turned the platform's core security mechanism—mark price—into a weapon.
This was not a hacker attack, but a "compliance attack" on the system rules. The attacker utilized the platform's publicly available calculation logic, algorithm processes, and risk control mechanisms to create a "no-code attack" that was highly lethal to both the market and traders. What should have served as a "neutral and safe" anchor for the market, the mark price, transformed from a shield into a blade during this incident.
This article will analyze the systemic risks of the mark price mechanism in the perpetual contract market for altcoins from both theoretical and practical perspectives, and provide a detailed review of the Jelly-My-Jelly attack incident. This event not only revealed the structural vulnerabilities in oracle design and the double-edged nature of innovative liquidity pools (HLP Vault), but also exposed the inherent asymmetry in the current mainstream liquidation logic regarding user fund protection under extreme market conditions.
Part One: The Core Paradox of Perpetual Contracts—The Liquidation Bias from False Security
1.1 Mark Price: A Liquidation Bias from a Misguided Sense of Security in a Consensus Game
To understand how mark price became an entry point for attacks, we must first dissect its compositional logic. Although the calculation methods vary slightly across exchanges, their core principles are highly consistent—built around a three-value median mechanism centered on "index price."
- The Index Price is the cornerstone of the mark price. It does not originate from the derivatives exchange itself but is calculated through a weighted average of prices from multiple mainstream spot platforms (such as Binance, Coinbase, Kraken, etc.), aiming to provide a fair reference price across platforms and regions.
A typical mark price calculation method is as follows:
Mark Price = Median (Price1, Price2, Last Traded Price)
Price1 = Index Price × (1 + Funding Rate Basis): Anchoring the contract price to the index price while considering market expectations.
Price2 = Index Price + Moving Average Basis: Used to smooth out short-term price anomalies.
Last Traded Price = The latest transaction price on the derivatives platform.
The introduction of the median was intended to eliminate outliers and enhance price stability. However, the safety of this design is entirely based on a critical assumption: that the number of input data sources is sufficient, reasonably distributed, highly liquid, and difficult to manipulate in coordination.
In reality, the spot markets for most altcoins are extremely weak. Once an attacker can control the prices of a few low-liquidity platforms, they can "pollute" the index price, thereby injecting malicious data into the mark price through the formula legally. This type of attack can trigger large-scale leveraged liquidations at minimal cost, causing a chain reaction.
In other words, the aggregation mechanism, which is intended to disperse risk, instead creates a "centralized weakness" that attackers can control in markets with sparse liquidity. The more derivatives platforms emphasize the transparency and predictability of their rules, the more attackers can "programmatically exploit the rules" to construct a compliant path of destruction.
1.2 Liquidation Engine: The Platform's Shield, Also a Blade
When market prices move rapidly in an unfavorable direction, traders' margins will be eroded by unrealized losses. Once the remaining margin falls below the "Maintenance Margin," the liquidation engine will be activated.
In these processes, the core triggering standard is the mark price, not the latest transaction price on the platform itself. This means that even if the current market transaction price has not yet reached your liquidation line, as long as that "invisible" mark price is reached, liquidation will be triggered immediately.
What is even more concerning is the "forced liquidation" (or early liquidation) mechanism.
In many exchanges, to avoid the risk of liquidation, the risk control system often adopts conservative liquidation parameters. Once forced liquidation is triggered, even if the liquidation price is better than the actual loss-zero price, the platform usually does not return this "forced liquidation surplus," but instead injects it directly into the platform's insurance fund. This leads traders to have the illusion of "having margin but being liquidated early," resulting in their accounts being zeroed out.
This mechanism is particularly common in low-liquidity assets. To hedge its own risks, the platform will set the liquidation line more conservatively, making it easier for positions to be "liquidated early" amid price fluctuations. The logic is reasonable, but the result creates a subtle misalignment of interests between the platform and traders under extreme market conditions.
The liquidation engine should be a neutral risk control tool, but in terms of profit attribution, parameter selection, and triggering logic, it exhibits a tendency towards platform profitability.
1.3 The Failure of Mark Price Leads to Distortion of the Liquidation Engine
Under this platform's aversion to loss, the severe fluctuations in index price and mark price further exacerbate the pre-emptive (or post-emptive) nature of forced liquidation.
The theory of mark price aims to provide a fair, manipulation-resistant price benchmark through the aggregation of multi-source data and median algorithms. However, while this theory may hold when applied to mainstream assets with ample liquidity, it faces severe challenges when dealing with altcoins that have thin liquidity and concentrated trading venues.
The failure of the median: The statistical dilemma of concentrated data sources
Effectiveness in large data sets: Assume a price index contains 10 independent, highly liquid data sources. If one data source experiences an extreme quote for any reason, the median algorithm can easily identify it as an outlier and ignore it, taking the middle value as the final price, thus maintaining the stability of the index.
Vulnerability in small data sets: Now, consider a typical altcoin scenario.
Three data source scenario: If the mark price index for an altcoin only includes the spot prices from three exchanges (A, B, C). At this point, the median is the price that ranks in the middle of the three. If a malicious actor simultaneously manipulates the prices of two exchanges (for example, A and B), then regardless of how accurate C's price is, the median will be determined by the manipulated prices of A and B. At this point, the protective effect of the median algorithm is almost zero.
Two data source scenario: If the index only includes two data sources, the median mathematically equates to the average of the two prices. In this case, the algorithm completely loses its ability to eliminate outliers. Any severe fluctuation in one data source will directly and unattenuatedly transmit to the mark price.
For the vast majority of altcoins, their trading depth and the number of listed exchanges are very limited, making their price indices highly susceptible to the aforementioned "small data set" trap. Therefore, the sense of security brought by the "multi-source index" claimed by exchanges is often just an illusion in the world of altcoins. Many times, the latest transaction price is often equivalent to the mark price.
Part Two: The Oracle Dilemma: When Spot Liquidity Exhaustion Becomes a Weapon
The foundation of mark price is the index price, and the source of the index price is the oracle. Whether in CEX or DEX, oracles serve as the bridge for information transmission between on-chain and off-chain. However, this bridge, while critical, becomes exceptionally fragile in times of liquidity scarcity.
2.1 Oracle: The Fragile Bridge Connecting On-Chain and Off-Chain
Blockchain systems are essentially closed and deterministic; smart contracts cannot actively access off-chain data, such as market prices of assets. Price oracles emerge as middleware systems responsible for securely and reliably transmitting off-chain data to on-chain, providing "real-world" information inputs for the operation of smart contracts.
In core DeFi infrastructures such as perpetual contract trading platforms or lending protocols, the price data provided by oracles almost constitutes the cornerstone of their risk management logic. However, a commonly overlooked fact is that an "honest" oracle does not mean it reports "reasonable" prices. The oracle's duty is merely to accurately record the external world state it can observe; it does not judge whether the price deviates from fundamentals. This characteristic reveals two distinctly different attack paths:
Oracle Exploit: Attackers manipulate the oracle data source or protocol through technical means, causing it to report incorrect prices.
Market Manipulation: Attackers deliberately drive up or suppress prices in the external market, while the normally functioning oracle accurately records and reports this "manipulated" market price. The on-chain protocol is not breached but reacts unexpectedly due to "information poisoning."
The latter is the essence of the Mango Markets and Jelly-My-Jelly incidents: it is not that the oracle was breached, but that its "observation window" was polluted.
2.2 The Pivot of Attack: When Liquidity Deficiencies Become a Weapon
The core of this type of attack lies in exploiting the target asset's liquidity disadvantage in the spot market. For assets with thin trading, even small orders can cause severe price fluctuations, providing an opportunity for manipulators.
The attack on Mango Markets in October 2022 is a "paradigm." The attacker, Avraham Eisenberg, exploited the extreme liquidity exhaustion of its governance token MNGO (with a daily trading volume of less than $100,000 at the time) by concentrating approximately $4 million in purchases across multiple exchanges, successfully driving the MNGO price up by over 2300% in a very short time. This "abnormal price" was fully recorded by the oracle and fed to the on-chain protocol, causing its borrowing limits to skyrocket, ultimately "legally" draining the platform's entire assets (approximately $116 million).
Detailed Attack Path: Five Steps to Breach the Protocol's Defense
Target Selection: The attacker first selects the target token, usually meeting the following conditions: it has launched perpetual contracts on a mainstream derivatives platform; the oracle price comes from several known, low-liquidity spot exchanges; it has low daily trading volume, and its order book is sparse, making it easy to manipulate.
Capital Acquisition: Most attackers acquire temporary large funds through "Flash Loans." This mechanism allows borrowing and repaying assets in a single transaction without any collateral, significantly reducing manipulation costs.
Spot Market Blitz: The attacker places a large number of buy orders simultaneously across all exchanges monitored by the oracle within a very short time. These orders quickly clear the sell orders, pushing the price to a high level—far deviating from its true value.
Oracle Contamination: The oracle faithfully reads prices from the manipulated exchanges mentioned above. Even with mechanisms like median or weighted averages to resist volatility, it is difficult to withstand simultaneous multi-source manipulation. The final index price becomes severely contaminated.
Mark Price Infection: The contaminated index price enters the derivatives platform, affecting the mark price calculation. The liquidation engine misjudges the risk range, triggering large-scale "liquidations," causing significant losses for traders, while the attacker can realize arbitrage through reverse positions or lending operations.
Attackers' "Playbook": The Double-Edged Sword of Transparency
Whether in CEX or DEX protocols, the virtue of "open-source transparency" is often touted, disclosing details such as their oracle mechanisms, data source weights, and price refresh frequencies, aiming to build user trust. However, for attackers, this information becomes a "manual" for formulating attack plans.
Taking Hyperliquid as an example, its oracle architecture publicly lists all data source exchanges and their weights. Attackers can accurately calculate how much capital to invest in each of the weakest liquidity exchanges to maximize the distortion of the final weighted index. This "algorithmic engineering" makes the attack controllable, predictable, and minimizes costs.
Mathematics is simple, but humans are complex.
Part Three: The Hunting Ground—Structural Risk Analysis of Hyperliquid
After understanding the attack principles, the "attacker" next needs to choose a suitable "battleground"—Hyperliquid. While manipulating oracles is a common attack method, the reason the "Jelly-My-Jelly" incident could occur on Hyperliquid and cause severe consequences lies fundamentally in the platform's unique liquidity structure and liquidation mechanism. These designs, aimed at enhancing user experience and capital efficiency, though innovative, inadvertently provided attackers with an ideal "hunting ground."
3.1 HLP Vault: Democratized Market Makers and Liquidation Counterparties
One of Hyperliquid's core innovations is its HLP Vault—a fund pool managed uniformly by the protocol, serving dual functions. (Detailed HLP introduction:
https://x.com/agintender/status/1940261212954173716
)
First, HLP acts as the platform's proactive market maker. It allows community users to deposit USDC into the vault, participate in the platform's automated market-making strategies, and share profits (or losses) proportionally. This "democratized" market-making mechanism enables HLP to continuously provide buy and sell orders for numerous illiquid altcoins. Because of this, even tokens like JELLY, which have a small market cap and extremely low liquidity, can support leveraged positions worth millions of dollars on Hyperliquid—something traditional exchanges find difficult to achieve. (In simpler terms, it allows for position building.)
However, this design not only attracts speculators but also draws in more dangerous entities: attackers who deliberately manipulate the market.
More critically, HLP also serves as the platform's "liquidation stop-loss backup," meaning it is the final liquidation counterparty. When leveraged positions are forcibly liquidated and there are not enough liquidators willing to take over in the market, the protocol automatically transfers these high-risk positions to the HLP vault, and it does so at the oracle's price.
The consequence of this mechanism is that HLP becomes a counterparty that can be deterministically exploited, with no autonomous judgment capability. Attackers can fully predict that once their "toxic position" triggers liquidation, it will be taken over by HLP—not by random and unpredictable market counterparties, but by an automated system that executes smart contract logic and acts 100% according to the rules: the HLP vault.
3.2 Structural Defects in the Liquidation Mechanism
The Jelly-My-Jelly incident exposed a fatal flaw in Hyperliquid under extreme market conditions, rooted in the funding structure and liquidation model within the HLP vault.
At the time of the attack, there was no strict isolation mechanism between the "liquidation reserve pool," which handles liquidated positions, and other funding pools executing market-making strategies. They shared the same collateral. When the attacker’s $4 million short position was liquidated due to a spike in the mark price, that position was fully transferred to the liquidation reserve pool. As the price of JELLY continued to rise, the losses on that position also continued to expand.
The attacker only needed to trigger liquidation (actively lowering the margin) to seamlessly offload their losing position to the system's counterpart—the HLP vault. The attacker knew well: the protocol rules would force HLP to take over at the most unfavorable price moment, becoming its "unconditional buyer."
In theory, when a position's losses become so significant that they threaten the platform's system stability, an automatic deleveraging (ADL) mechanism should trigger, forcing users with positions in the opposite direction to reduce their positions to share the risk. But this time, ADL did not activate.
The reason is that although the liquidation reserve pool itself had already fallen into deep losses, it could call upon the collateral assets from other strategy pools within the entire HLP vault. The system determined that the overall "health" of the entire HLP vault was still good, thus the risk control mechanism was not triggered. This design of shared collateral inadvertently bypassed the ADL systemic risk defense line, causing losses that should have been borne by the overall market to ultimately concentrate and explode within the HLP vault.
Part Four: Case Analysis—A Complete Review of the Jelly-My-Jelly Attack
On March 26, 2025, a meticulously planned attack unfolded on Hyperliquid, targeting Jelly-My-Jelly (JELLY). This attack cleverly combined liquidity manipulation, a deep understanding of the oracle mechanism, and the exploitation of structural weaknesses in the platform, becoming a classic case for deconstructing modern DeFi attack patterns.
4.1 Phase One: Setup—A $4 Million Short Trap
This attack was not a spur-of-the-moment decision. On-chain data shows that the attacker had been testing strategies through a series of small-scale trades for ten days prior to the incident, clearly preparing for the final action.
On March 26, as JELLY's spot price fluctuated around $0.0095, the attacker began implementing the first phase. Multiple wallet addresses participated, with address 0xde96 being the key executor. The attacker quietly built a short position worth approximately $4 million in the JELLY perpetual contract market through self-trading (acting as both buyer and seller), supplemented by a total of $3 million in long counter-trading positions. The purpose of these counter-trades was to maximize the open interest (OI) of the contracts while avoiding triggering abnormal market fluctuations, thus laying the groundwork for subsequent price manipulation and liquidation inducement.
4.2 Phase Two: Blitz—Lightning Strike on the Spot Market
With the setup complete, the attack entered the second phase: rapidly raising the spot price. JELLY was the target of the manipulators' dreams. Its total market cap was only about $15 million, and the order book on mainstream exchanges was extremely weak. According to Kaiko Research data, its 1% market depth was only $72,000, far below that of other similar tokens.
The attacker exploited this weakness, launching a buying offensive simultaneously across multiple centralized and decentralized exchanges. Due to the lack of sell-side support, the spot price of JELLY was rapidly driven up in a short time. Starting from $0.008, the price surged over 500% in less than an hour, reaching a peak of $0.0517. Meanwhile, trading volume exploded. On just Bybit, the daily trading volume of JELLY exceeded $150 million, setting a new historical high.
4.3 Phase Three: Detonation—Oracle Contamination and Liquidation Cascade
The sharp rise in the spot price quickly transmitted to Hyperliquid's mark price system. Hyperliquid's oracle mechanism employs a multi-source weighted median algorithm, integrating spot data from multiple exchanges such as Binance, OKX, and Bybit. Since the attacker acted simultaneously at these key sources, the final aggregated index price became effectively contaminated, driving the internal mark price of the platform to rise in sync.
The spike in the mark price directly triggered the short position that the attacker had previously deployed. As losses expanded, the $4 million position triggered forced liquidation. At this moment, it was not a failure of the attack, but rather the core link of the attack design.
Since the HLP vault acted as the platform's liquidation counterparty, it unconditionally took over according to the smart contract logic, while the liquidation system failed to trigger the ADL (automatic deleveraging) mechanism to share the risk, causing the entire high-risk position to be directly pushed onto HLP. In other words, the attacker successfully "socialized" their liquidation losses, making the liquidity providers of HLP bear the costs of their manipulative actions.
4.4 Phase Four: Aftermath—Emergency Delisting and Market Reflection
As Hyperliquid fell into chaos, external markets also reacted complexly. Within an hour of JELLY being manipulated to a high level, Binance and OKX almost simultaneously launched perpetual contracts for JELLY. The market widely interpreted this action as a "fire sale" on the competitor Hyperliquid, further exacerbating JELLY's market volatility and indirectly increasing the potential losses for the HLP vault.
Faced with immense pressure from the market and the community, Hyperliquid's validator nodes urgently voted to implement several countermeasures: immediately and permanently delist the JELLY perpetual contract; the foundation would fund full compensation for all affected users from non-attack addresses.
According to Lookonchain data, at the peak of the attack, the unrealized losses of the HLP vault reached as high as $12 million. Although Hyperliquid officials ultimately reported that total losses were controlled at $700,000 within 24 hours, the impact of the entire incident on the platform's structure and risk control system was undoubtedly profound.
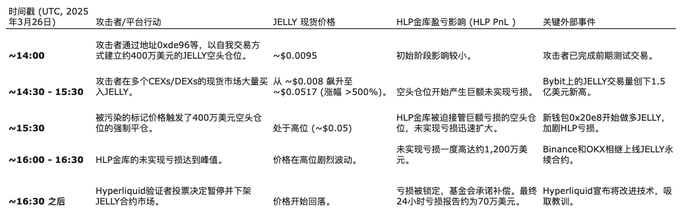
JELLY Incident Progress
Conclusion — The "Mark Price Illusion" of Perpetual Contracts and Defense Propositions
In the Jelly-My-Jelly incident, the attackers did not rely on complex contract vulnerabilities or cryptographic techniques; they simply uncovered and exploited the mathematical structural flaws in the mark price generation mechanism—small data sources, median aggregation, and fragmented liquidity—while leveraging the market's liquidation mechanism. This type of attack does not require sophisticated hacking skills, only reasonable market operations and a deep understanding of the protocol logic.
The fundamental issues with mark price manipulation are:
The high correlation of oracle data: The seemingly "multi-source" price inputs actually come from a few exchanges with severely overlapping liquidity. Once a few key exchanges are compromised, the entire price index becomes meaningless.
The aggregation algorithm's tolerance for outliers: The median is effective in large samples but nearly powerless in small samples; when the input sources are themselves "cornered," no matter how sophisticated the algorithm, it cannot save the situation.
The "blind trust" problem of the liquidation system: Almost all CEX and DeFi platforms assume that the mark price is fair, thus using it as a liquidation trigger. However, in reality, this trust is often built on contaminated data.
Establishing True "Anti-Manipulation" Between Algorithms and Games
The mark price should not be a value that is "mathematically correct but game-theoretically fragile," but rather a product of a mechanism that can maintain stability under real market pressure. The ideal of DeFi is to build trust through code, but code is not perfect; it can also solidify biases, amplify preset flaws, and even become a weapon in the hands of attackers.
The Jelly-My-Jelly incident is not an accident, nor will it be the last. It serves as a warning: without a deep understanding of the game structure, any "deterministic" liquidation mechanism is a potential entry point for arbitrage. The maturation of mechanisms requires not only faster matching speeds and higher capital efficiency but also a self-reflective ability at the design level to identify and close off these systemic risks obscured by "mathematical elegance."
May we always maintain a sense of reverence for the market.
Mathematics is simple, but humans are complex.
Only historical games are repetitive.
Know what it is, and also know why it is so.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




