# I. Outlook
1. Summary of Macroeconomic Trends and Future Predictions
Last week, the main theme of the U.S. macroeconomy was the "data repricing" following the confirmation of a policy turning point. With the December interest rate decision clearly indicating the end of the rate hike cycle, the market refocused on the fundamentals: the job market continued to cool, with new job creation and hiring demand remaining weak; consumer and manufacturing activities maintained low levels, and corporate investment sentiment was cautious; while inflation did not show a significant rebound, service prices remained sticky, causing the overall inflation decline to be slow. U.S. Treasury yields fluctuated and fell during the week, and the dollar weakened, reflecting the market's continued expectations for future easing, although risk appetite did not significantly rebound.
Looking ahead, the U.S. economy is likely entering a transitional phase of low growth, low inflation, but with a policy bias towards easing. If subsequent data continues to confirm a slowdown in employment and weakening demand, expectations for the Federal Reserve to start cutting rates in early 2026 will be further strengthened; however, if inflation shows signs of resurgence, the policy pace may remain cautious. For the market, the short-term focus will shift from "policy direction" to "speed of economic decline," and the performance of risk assets will depend more on whether the data supports a moderate slowdown rather than a rapid recession. Overall, the macro environment is no longer tight, but recovery momentum remains insufficient, and volatility may remain high from the end of the year into early next year.
2. Market Changes and Warnings in the Cryptocurrency Industry
Last week, the cryptocurrency market remained in a state of low-level fluctuations and weak rebounds. Bitcoin fluctuated around $89,000, attempting to rebound multiple times, but trading volume failed to expand, indicating that new capital remains cautious. The "dovish confirmation" following the Federal Reserve's December interest rate decision did not significantly improve market risk appetite, and ETF inflows remained low, with institutions primarily adopting a wait-and-see approach. Altcoins continued to underperform BTC overall, with most sectors continuing a slow decline, and only a few themes experiencing brief surges in the low liquidity environment at year-end, but sustainability was clearly lacking, and the market structure remained defensive.
In terms of warnings, the current cryptocurrency market still faces dual pressures of tight liquidity and year-end risk convergence. If Bitcoin cannot effectively recover and stabilize in the $95,000–$100,000 range, the market may continue to maintain a weak consolidation at year-end, or even test the low points again. Additionally, year-end institutional settlements, position adjustments, and macro data disturbances may amplify short-term volatility. Only when there is a clear indication of an earlier timeline for macro rate cuts or an overall warming of risk assets can the cryptocurrency market potentially break out of the current weak pattern; otherwise, caution is needed regarding the emotional exhaustion and further downside risks brought about by repeated bottoming at low levels.
3. Industry and Sector Hotspots
Raising $3 million, Space, a high-speed prediction market infrastructure led by ECHO and Arctic Digital, is a decentralized prediction market platform built on Solana; with total funding of $9 million, Self Protocol, a global infrastructure for the self-sovereign identity era, is a privacy-centric open-source identity protocol that uses zero-knowledge proofs (ZKP) for secure identity verification.
# II. Market Hotspot Sectors and Potential Projects of the Week
1. Overview of Potential Projects
1.1. Analysis of the $3 Million Funding, Led by ECHO and Arctic Digital—High-Speed Prediction Market Infrastructure Space Based on Solana CLOB
Introduction
Space is a decentralized prediction market platform built on Solana, where users can trade on various real-world events related to crypto, politics, sports, technology, culture, etc., and receive rewards for correct predictions.
CLOB and Order Matching
Space operates on Solana and uses a Central Limit Order Book (CLOB), allowing users to trade directly with each other.
No market makers, no intermediaries, no AMM curves—only transparent order matching and real price discovery.
1. How the Order Book Operates
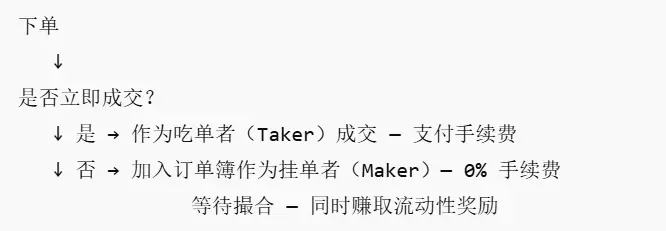
Maker: Submits limit orders, pays 0% fees, and earns rewards for providing liquidity.
Taker: Trades with existing orders, with fees dynamically changing based on market probability.
Order matching follows price priority → time priority:
Orders with better prices are executed first;
Orders at the same price are executed based on submission time.
2. Order Lifecycle
User submits a market order or limit order.
The matching engine checks for counterparty orders.
If there is a counterparty → immediate execution (Taker).
If not → the order is added to the order book (Maker).
The order remains until:
Executed
Canceled by the user
Or expires
3. Price Discovery
Prices are determined by supply and demand, and each order is publicly visible on-chain.
The order book is completely transparent—no hidden liquidity and no special privileges.
SPL Token Structure
1. How YES / NO Tokens Work On-Chain
Each market uses SPL tokens to represent positions:
YES token = the event will occur
NO token = the event will not occur
Each pair of YES + NO is backed by 1 USDC.
2. Minting and Burning Mechanism
Minting:
1 USDC → 1 YES + 1 NOBurning:
1 YES + 1 NO → 1 USDC
This mechanism ensures:
YES + NO ≈ 1 USD (price stability)
Always available base liquidity
Capital efficiency in multi-outcome markets.
When the order book lacks liquidity, you won't be stuck.
You can directly mint YES + NO for 1 USDC, sell the side you don't want, and gain instant liquidity—without relying on other traders.
3. Arbitrage Mechanism
If market prices deviate, for example:
YES = $0.65
NO = $0.40
Total = $1.05 (overpriced)
Arbitrageurs can:
Buy YES + NO for $1.05
Burn to get back $1.00
Repeat until prices return to balance
This mechanism continuously drives YES + NO ≈ $1, ensuring stable market prices.
Multi-Outcome Markets
For markets with multiple possible outcomes (e.g., "Which country will win the World Cup?"), all NO shares use the same SPL token across different outcomes.
1. Share Conversion
Example:
You hold 1,000 NO shares for Brazil.
Click to convert →
You now hold 1,000 YES shares for Argentina.
No additional funds required.
You simply convert your holdings between different outcomes in the same market.
2. How It Works
In a multi-outcome market:
Each outcome has its own YES and NO shares.
All NO shares for different outcomes use the same SPL token.
Converting NO (Brazil) → YES (Argentina) is just a metadata update, without needing to mint or burn tokens.
3. Example:
Market: "Which country will win the World Cup?"
Brazil (YES/NO)
Argentina (YES/NO)
France (YES/NO)
Germany (YES/NO)
You hold 1,000 NO shares for Brazil. This means you believe Brazil will not win the championship—another country will.
If you want to convert your holdings to Argentina:
Conversion Steps:
Burn 1,000 Brazil NO.
Mint 1,000 Argentina YES.
No additional funds required.
4. Hedging Across Outcomes
You can also diversify risk, for example:
Convert 500 Brazil NO → 500 Argentina YES.
Convert 500 Brazil NO → 500 France YES.
This way, you can cover multiple potential outcomes without increasing your capital investment.
Tron Comments
The advantage of Space lies in its high-performance CLOB architecture based on Solana, achieving a true on-chain order book, which offers higher liquidity efficiency, transparent pricing, and price discovery closer to real markets compared to traditional AMM prediction markets; the SPL mechanism of YES/NO tokens provides always available base liquidity, arbitrage stability, and capital-efficient conversion in multi-outcome markets; users can earn rewards through market making, with an overall experience close to centralized exchanges while maintaining decentralized characteristics.
Its disadvantages include: the order book and YES/NO mechanism may be complex for new users; reliance on Solana's network performance and stability; potential liquidity shortages in extreme market conditions or niche markets; and regulatory uncertainties that prediction markets may face in certain jurisdictions. Overall, Space has significant advantages in performance, transparency, and capital efficiency, but still faces challenges in user education, market depth, and compliance.
1.2. Interpretation of Total Funding of $9 Million, with Participation from Green Field and SoftBank—Global Infrastructure for the Self-Sovereign Identity Era, Self Protocol
Introduction
Self is a privacy-centric open-source identity protocol that uses zero-knowledge proofs (ZKP) for secure identity verification.
The protocol achieves Sybil resistance and selective disclosure through the use of real-world credentials (such as passports). Developers can easily verify whether a user is a real person with just a few lines of code while protecting user privacy.
Self Protocol simplifies digital identity verification through a three-step process:
Scan your passport: Use your phone's NFC reader to scan the passport.
Generate proof: Generate a zero-knowledge proof based on the passport, selecting only the fields you wish to disclose.
Share proof: Share the zero-knowledge proof with the designated application.
Architecture Overview
Self Protocol is a privacy-centric open-source identity protocol that allows users to authenticate their identity using real-world credentials (such as passports and national ID cards) in a permissionless environment, achieving Sybil resistance and selective disclosure. The team believes that leveraging existing institutional authoritative certifications is the most pragmatic and privacy-friendly path for identity verification compared to the difficult-to-scale Web-of-Trust systems or still immature biometric solutions.
The protocol consists of three main components:
Mobile application: Scans the passport chip via phone NFC and completes the necessary authentication process.
Zero-knowledge proof circuit: Verifies the validity of the passport, generates identity commitments, and supports selective disclosure of attributes.
Smart contracts: Verifies proofs, maintains the Merkle tree of identity commitments, and securely discloses data on-chain.
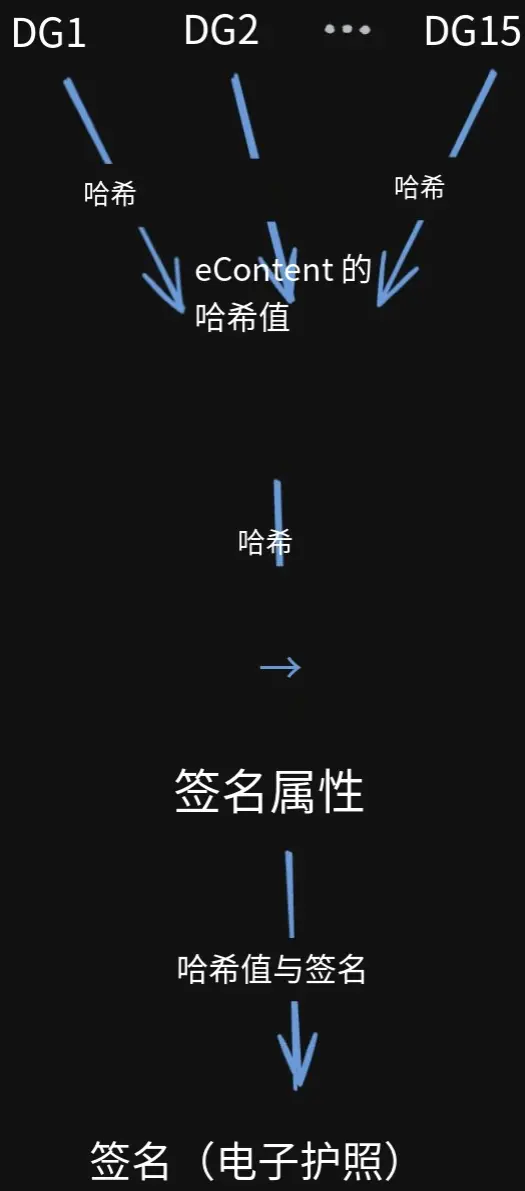
Biometric passports follow the ICAO 9303 standard and are widely adopted in over 170 countries. The passport chip contains multiple data groups (DG1 for identity information, DG2 containing photos and other high-entropy data), with its hash signed by a nationally issued certificate chain to ensure authenticity and non-repudiation.
High-Level Architecture of Self Protocol (Core Concept)
Self is a privacy-first, permissionless, and provable human identity layer built around real-world credentials (such as passports and national IDs). Through zero-knowledge proofs (ZKP), Self enables users to prove on-chain and within applications that "I am a real person" or "I meet a certain condition" without exposing their complete identity information. The core idea is that privacy-preserving proofs based on trusted roots from existing institutions (the national passport system) are the most robust, scalable, and practical path compared to the difficult-to-scale Web-of-Trust or immature large-scale biometric systems.

Workflow: Registration + Disclosure
The use of Self Protocol is divided into two phases:
1. Registration Phase
Users scan the passport NFC chip with their phone, and after verifying the trusted execution state of the TEE, send the passport data to the TEE. In the TEE, the following are generated:
Zero-knowledge proof of passport validity (verifying the DSC/CSCA certificate chain)
Identity commitment:
A hash of key passport information (DG1, etc.) + a user-generated secret.
Once this zk proof is verified by the on-chain smart contract, the identity commitment will be added to the identity pool, stored in a scalable Merkle tree.
At the same time, an attestation nullifier is generated to ensure that the same passport cannot be registered multiple times.
Generating heavy proofs through the TEE ensures performance and security, while on-chain verification guarantees that the registration process is permissionless and completely transparent.
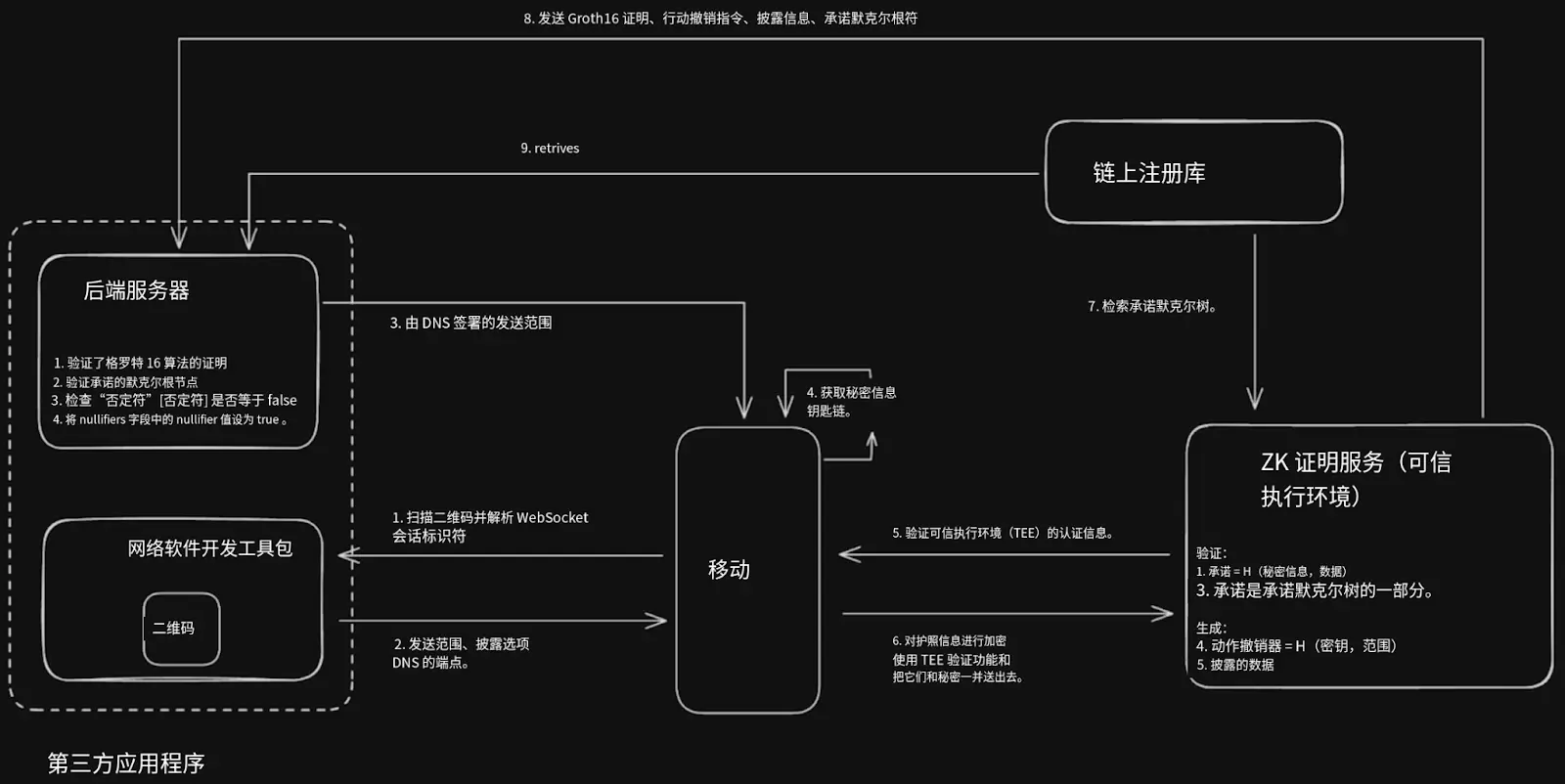
2. Disclosure Phase
When an application needs to verify identity (for example, to prove age, nationality, non-sanctioned status, or "real person status"), the user locally generates a new disclosure zk proof:
Proving that the user possesses a commitment included in the identity pool
Allowing for selective disclosure (e.g., proving "age > 18" without revealing the birthdate)
Using action nullifiers to restrict the reuse of the same identity in the same application scenario (to prevent airdrop abuse or multiple voting)
The disclosure proof can be directly bound to the user's wallet address and provided to third-party applications via a Web SDK.
This makes Self a universal, composable on-chain identity layer.
Core Mechanisms and Design Rationale
1. Separation of Registration and Disclosure to Establish an "Indirect Layer" for Privacy
This design brings two benefits:
Even if an attacker knows that a passport has been registered, they cannot track which applications the user subsequently disclosed to.
The passport validity proof circuit is large, while the disclosure proof is extremely lightweight (primarily based on Poseidon hash).
Thus, Self achieves a balance of strong privacy and efficient use.
2. Dual Nullifier Design: Preventing Duplicate Registrations & Duplicate Actions
Self employs two types of nullifiers:
(1) Attestation nullifier
A hash based on the signed attributes of the passport (signed_attr)
Prevents the same passport from registering multiple identities
Deterministically generated by passive authentication (Passive Auth)
Even if the issuing country can deduce whether a passport is registered, they cannot know the user's behavior within applications.
(2) Action nullifier
Generated based on user secret + application domain name (scope)
Prevents the same identity from being reused in the same scenario
The scope is determined by the application DNS and verified on the mobile end, avoiding applications "deceiving users" to obtain duplicate nullifiers.
3. Certificate System: CSCA / DSC Two Merkle Trees
CSCA Tree: Built on the ICAO masterlist, with each country's root certificate (CSCA) as leaves.
DSC Tree: Whenever a new DSC is discovered and proven to be issued by a certain CSCA, it is added to the DSC tree.
During registration, users only need to prove that their passport was issued by a DSC in the DSC tree, significantly reducing proof costs.
This ensures that the protocol can:
Support passports from over 170 countries
Dynamically scale
Maintain security and have "bulk revocation" capabilities in the event of certificate leaks.
4. Balancing Security and Privacy: TEE + Local Proofs
Passport validity proofs are generated in the TEE (handling large circuits to ensure performance).
Disclosure proofs are generated on the client side (lightweight, fast, with no risk of privacy leakage).
In the future, more client-side proof paths will be supported to reduce reliance on TEE's privacy trust assumptions.
5. Mitigating Timing Attacks
Self uses an identity pool (similar to Tornado Cash's mixer), which poses a risk of timing correlation attacks.
Self mitigates this by:
Reminding users to wait a period after registration before making their first disclosure.
Using random delay notifications.
This expands the anonymity set and enhances security.
6. Scalable Direction: Active Authentication (AA)
Self currently relies on passive authentication (Passive Auth), but the architecture has reserved:
Using the passport chip's private key (DG15) for challenge signatures.
Requiring signature on the on-chain block hash to ensure that the registrant must possess the physical passport.
This will further enhance security and is a direction for future development.
Tron Comments
The core advantage of Self lies in providing a highly credible identity root based on real-world credentials such as passports, combined with zero-knowledge proofs to achieve strong privacy, Sybil resistance, and selective disclosure; the architecture's separation of registration and disclosure avoids traceable behavior; the mechanism based on the DSC/CSCA certificate tree can scale to the global passport system, is friendly for application integration, permissionless, and usable without requiring users to have cryptographic knowledge.
Its disadvantages include: reliance on a nationally issued certificate system, which still poses risks of passive authentication potentially leaking registration relationships; the TEE generating heavy proofs introduces certain trust assumptions; obtaining passports/IDs and NFC scanning creates user barriers; cross-national certificate management, recovery mechanisms, and forward compatibility still need further maturation. Overall, Self achieves a relatively good balance between "privacy + practicality + trust root," but there is still room for improvement in achieving complete decentralization and trustlessness.
2. Key Project Details of the Week
2.1. Detailed Explanation of Total Funding of $16.4 Million, with Participation from Polkadot's Gavin Wood, Tezos, and Coinlist—Acurast, a Verifiable Computing Network Aiming to Turn Every Mobile Phone into a Computing Node
Introduction
Acurast is redefining computing by leveraging billions of smartphones worldwide—without data centers. This verifiable, scalable, and confidential computing network enables users to run secure applications at scale on decentralized infrastructure without sacrificing speed or privacy.
Acurast has already launched over 141,428 compute units on its incentivized testnet, making it the most decentralized verifiable computing network today. Such immense computing power is already serving critical workloads that require high security and artificial intelligence.
This is not just another DePIN protocol—it's a disruptive innovation that is redefining global computing.
Coordinator Architecture
1. Acurast Orchestrator
The Acurast Orchestrator is the core component of the consensus layer, combining processor computing resources with deployment scheduling between developers (i.e., arrangement of deployments and flow matching). The orchestrator plays a key role in defining, reaching, and executing the value exchange between processors and developers.
The orchestrator runs a flow matching engine that matches the resources provided by processors with the demands defined by developers. The orchestrator natively supports various price discovery mechanisms (e.g., auctions, advertising-style bids), making the developer experience (DevEx) more convenient and smooth.
Each protocol between processors and developers is described by an entity called a deployment. A deployment includes the following:
A series of instructions that the processor needs to execute.
Scheduling parameters for the deployment.
Settlement configurations (i.e., further processing or persistence methods for output data).
Reward mechanisms.
The reward system of the Acurast orchestrator consists of two processes:
Compute/Data Flow
Reward Flow
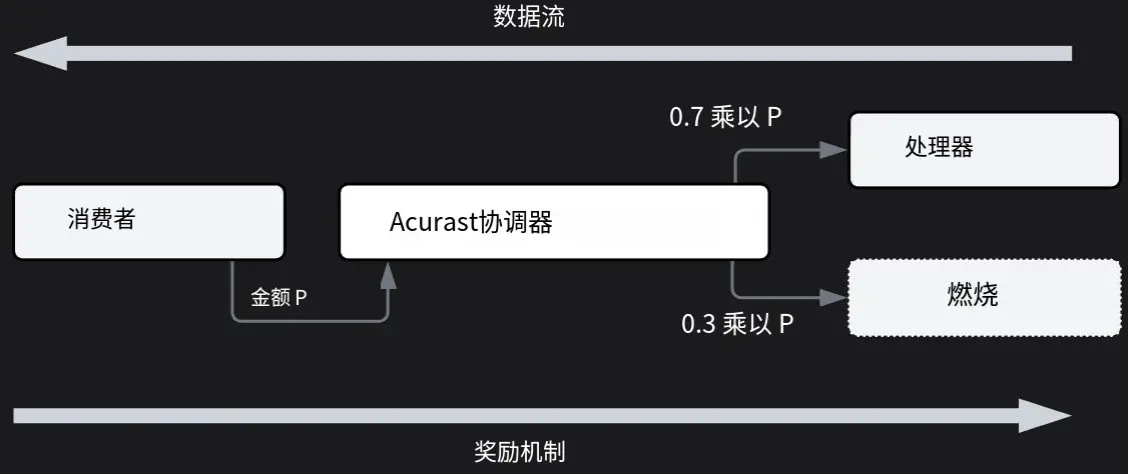
Compute/Data Flow
For example, data can come from public API data point observations, off-chain computation results, privacy-preserving queries on proprietary data (i.e., permissioned data), or a combination of the above scenarios. From the perspective of DevEx and developers, this is equivalent to defining resource requirements in public cloud service providers (such as AWS, Google Cloud, Microsoft Azure).
Reward Flow
In the reward flow, developers define a budget for the execution of the deployment. This budget can be paid using the native tokens cACU/ACU, and in the future, it may also support payments in stablecoins pegged to fiat currencies. This mechanism allows developers to make predictable financial plans for execution costs.
When a deployment is executed, the deployment fees paid by developers are burned, creating a deflationary effect on the token supply.
Processors executing the deployment gain indirect benefits in the following ways:
They receive a Deployment Execution Bonus, which increases their baseline score, allowing them to earn higher rewards in this epoch from:
Staked Compute Pool
Compute Pool
This mechanism ensures that processors are incentivized for executing deployments while maintaining a deflationary token economy for the network.
Protocol Architecture Analysis
Acurast decouples the consensus layer, execution layer, and application layer (see Figure 1). Acurast's cloud architecture fundamentally changes the design and deployment of applications. Its modular characteristics enable universal interoperability between native settlement and ecosystems, allowing for bidirectional interactions between Web3 → Web3 and Web3 → Web2.
Ultimately, Acurast serves as a decentralized application platform that provides privacy and verifiability guarantees for data without introducing any new trusted entities.

Figure 1: Acurast Architecture
Consensus Layer
The consensus layer is Acurast's permissionless foundation, where the Orchestrator matches developers' deployments to processors based on the end-to-end execution process (see End-to-End Deployment Execution).
The second core component of the consensus layer is the Reputation Engine, which ensures that the reputation scores of processors are correctly updated and incentivizes honest behavior.
Execution Layer
The execution layer consists of two key parts:
- Processor Runtimes
Acurast Secure Hardware Runtime
Acurast Zero-Knowledge Runtime
Acurast Universal Interoperability Layer
Composed of multiple modules, enabling Acurast to interact natively with different ecosystems.
Application Layer
The third layer is the application layer, where Web2 or Web3 applications run.
Although many DeFi protocols are already using Acurast, Acurast will further drive the development of new application scenarios that were previously impossible to achieve in a confidential and decentralized manner.
1. End-to-End Deployment Execution
Acurast's End-to-End Deployment Execution demonstrates the entire lifecycle of a deployment from definition, matching, execution to final completion. The process includes 5 key steps:
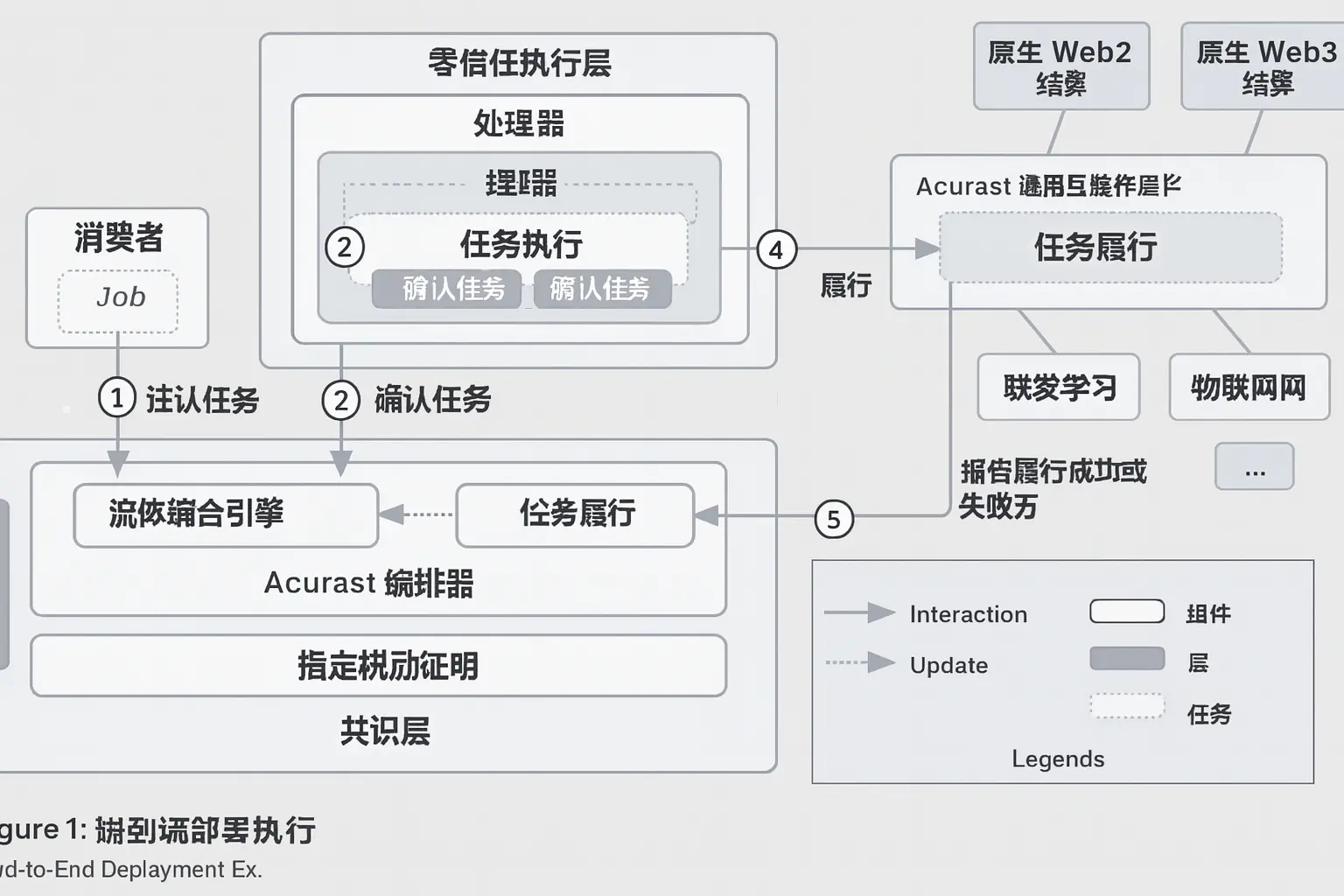
Acurast's end-to-end deployment execution model consists of 5 stages, showcasing the entire process of decentralized, verifiable, and confidential computing:
Deployment Registration: Developers define execution goals, scheduling strategies, resource requirements, reward mechanisms, and choose the type of processor (private, trusted, or public). After registration, the deployment enters the OPEN state.

Deployment Confirmation: The processor retrieves information from the blockchain, confirms it can fully execute all tasks, and submits the deployment status to the target chain if necessary. At this point, the deployment enters the MATCHED/ASSIGNED state.
Deployment Execution: The processor executes the deployment script in a secure runtime environment (such as ASHR or AZKR), ensuring confidentiality and verifiability.
Deployment Fulfillment: The execution output is sent to the designated target (Web3 chain, Web2 API, etc.). In cross-chain scenarios, the processor pays the gas fees (which the developer has pre-paid).
Deployment Reporting: The processor reports the execution results to the Reputation Engine (success includes transaction hash, failure includes error information). The deployment enters the DONE state, and the reputation system updates the processor's score to incentivize honest behavior.
2. Application Layer
In today's internet, almost every application heavily relies on auxiliary systems. Whether for external API authentication, infrastructure (hosting), or data availability, these dependencies can benefit from using confidential applications to extend or replace services and core elements, fundamentally eliminating a range of threat events. Given that today's centralized internet is highly concentrated both logically and in trust anchors, the possibilities brought by Acurast are virtually limitless.
Acurast's broad application prospects include:
Zero-Knowledge Proofs: Confidentially offloading high-intensity computations to form proof generation alliances.
Privacy-Preserving Mixed Computation: Protecting metadata of transactions and various sensitive data.
Secure Multi-Party Computation: Achieving collaborative computation of private data without a trusted third party.
Blockchain Infrastructure: Serving as a decentralized serverless backend, providing anti-corruption transaction sorting to resist MEV attacks, and extending on-chain automation capabilities beyond oracles.
Native Cross-Chain DeFi and Data Availability as a Service.
Decentralized Crawling Infrastructure: Collecting data confidentially without disclosing query party information.
Artificial Intelligence: Running large language models in a decentralized, privacy-preserving manner through its Singularity module, using methods like federated learning.
Internet of Things: Securely collecting and processing data from IoT devices through the Acurast Mesh module.
In summary, Acurast provides a foundational layer for building a new generation of internet applications that are decentralized both logically and physically, while protecting privacy.
3. Execution Layer
Acurast's execution layer adopts a modular design, allowing for flexible selection of runtimes based on use cases and deployment needs. Decoupling the execution layer from the consensus and application layers enables runtimes to evolve independently over the long term, avoiding dependency lock-in. Additionally, it ensures the highest levels of service and confidentiality, as the security model can iteratively evolve through upgrades in response to new threats or emerging needs.
Acurast natively and directly supports the rapid launch of permissioned alliances. Depending on requirements, developers can (a) directly utilize the Acurast orchestrator to select processors from the public processor pool, or (b) use dedicated processors (e.g., processors from trusted entities or self-service processors supported by developers). This composability allows developers to customize access control and define individual trust models based on the deployments they wish to execute.
Acurast's execution layer natively provides two runtimes: (1) Acurast Secure Hardware Runtime and (2) Acurast Zero-Knowledge Runtime.
Modular Design: The execution layer is decoupled from the consensus and application layers, allowing runtimes to evolve independently, avoiding dependency lock-in, and flexibly responding to new security threats and needs.
Flexible Deployment Models:
Developers can use the public processor pool.
They can also form permissioned alliances, using dedicated processors from trusted entities to achieve customized access control and trust models.
Two core runtimes:
Acurast Secure Hardware Runtime: Based on dedicated external co-processors (such as Google Titan chips), providing the highest level of confidential computing security through hardware isolation. It outperforms mainstream TEE solutions, which face risks such as side-channel attacks due to integration in the main processor (e.g., Intel SGX, ARM TrustZone).
Acurast Zero-Knowledge Runtime: Based on recursive zero-knowledge proofs, achieving verifiable computation. Its trust is rooted in cryptography rather than hardware, but it requires circuit design for specific computations, making it less performant than ASHR.
Core Comparison: ASHR provides high performance and hardware-level isolation, with trust based on hardware and proof processes; AZKR offers cryptographic guarantees of verifiability, with trust based on cryptographic schemes.
4. Consensus Layer
The permissionless consensus layer forms the foundation of the Acurast protocol, based on a variant of the nominated proof-of-stake (NPoS) algorithm. Unlike traditional proof-of-stake networks, NPoS includes both validators and nominators. Block validators are responsible for verifying transactions to include them in the next block, similar to traditional PoS block validators. The key difference is that validator nodes are not randomly selected but are nominated by another class of nodes (i.e., nominators).
- Core Mechanism: Based on NPoS, it includes two roles:
Validator: Responsible for verifying transactions and producing blocks, with a limited number elected by nominators.
Nominator: Ordinary token holders who nominate and support the validators they trust by staking tokens, with no limit on their number.
Design Advantages and Objectives:
Balance of Security and Scalability: A limited set of validators ensures the long-term scalability of consensus (which can be adjusted through governance), while unlimited nominator staking increases the total value protected by the network, thereby enhancing security.
Alignment of Economic and Reputation Incentives: Nominators' interests are tied to those of validators. Nominators receive economic rewards or penalties based on the behavior of the validators they choose, and their reputation is also linked to this. This incentivizes nominators to carefully select efficient and reliable validators.
Democratization and Competition: The limited number of validator seats creates a competitive environment, encouraging nominators to vote for the best validators, thus democratizing the election process.
Configurability: Consensus parameters (such as the maximum number of validators and minimum staking amounts) can be configured through governance decisions, reflecting the protocol's flexibility.
Tron Commentary
Acurast's advantage lies in its innovative use of a decentralized, verifiable, and confidential computing network composed of a vast number of smartphones, achieving high scalability and secure execution without the need for data centers, along with native interoperability across Web2/Web3; it provides a trusted execution environment through secure hardware and zero-trust architecture, incentivizing honest computation with a deflationary token economy and reputation system.
At the same time, its disadvantages mainly stem from reliance on the stability of user devices and hardware differences, which may face challenges such as inconsistent performance of mobile devices, fluctuations in online rates, the need for time accumulation for ecosystem maturity, and high educational costs for developers regarding mindset and toolchains.
1. Overall Market Performance
1.1. Spot BTC vs ETH Price Trends
BTC

ETH

2. Summary of Hot Sectors

### Macroeconomic Data Review and Key Data Release Nodes for Next Week
The key data released last week from the United States further reinforced the macro judgment of "cooling employment and slowly declining inflation." Data from December 16 showed a slight increase in the unemployment rate for November, with a significant slowdown in the growth of seasonally adjusted non-farm payrolls, with new jobs concentrated in the service and public sectors, and insufficient hiring momentum in the private sector, confirming the cooling trend in the labor market. The November unadjusted CPI year-on-year rate, released on December 18, continued to decline, with no rebound in inflation; falling energy prices weighed on overall inflation, but core service prices remained somewhat sticky. Overall, this set of data conveys the signal of "weakening economic momentum but inflation is not yet out of control," also confirming the macro background in which the Federal Reserve enters an observation period after the December meeting, reserving space for subsequent easing policies.
Important data to be released this week:
December 24: Initial jobless claims in the U.S. for the week ending December 20.
### Regulatory Policies
United Kingdom: Comprehensive Regulatory Framework for Crypto Assets Submitted to Parliament
This week, the UK took a key step in establishing a comprehensive regulatory system for crypto assets.
Core Bill Submitted: A statutory document titled "Financial Services and Markets Bill 2000 (Crypto Assets) Regulations 2025" was submitted to Parliament for review on December 15. This bill is seen as the first significant step for the UK to launch its regulatory system for crypto assets.
Main Content: The bill establishes broad rules, mainly including: designating the public issuance and trading platforms of specific crypto assets as "designated activities," requiring compliance with the rules regardless of whether the relevant companies are authorized by the UK's Financial Conduct Authority (FCA); applying a market abuse regulatory framework similar to that for traditional investments (such as insider trading and market manipulation) to crypto assets; explicitly listing the issuance of stablecoins as a regulated activity requiring FCA authorization.
Next Steps and Effective Date: The bill must be approved by both houses of Parliament to become law, with a full effective date set for October 25, 2027.
United States: Congress and Regulatory Agencies Progressing in Sync
This week, U.S. lawmakers and regulatory agencies separately announced new tax policy drafts and regulatory reform plans.
New Tax Law Draft Released: On December 20, two bipartisan members of the U.S. House of Representatives released a discussion draft titled "Digital Asset PARITY Act."
Tax Exemption for Small Stablecoin Transactions: The draft proposes exempting capital gains tax for qualified stablecoin transactions valued at $200 or less.
Tax Deferral for Staking Rewards: The draft proposes a compromise on the taxation timing for staking and mining rewards, allowing taxpayers to choose to defer it for five years.
SEC Plans to Launch "Innovation Exemption": The chair of the U.S. Securities and Exchange Commission recently confirmed that the agency is advancing the "crypto project" as planned, with an innovative exemption framework expected to be released in January 2026. This framework aims to allow crypto companies to more easily launch blockchain-based products in the U.S. under the condition of complying with principle-based requirements, aiming to keep innovation and economic activity within the U.S.
European Union: Member States Advancing MiCA Regulation Implementation
As the EU's Markets in Crypto-Assets Regulation (MiCA) enters the implementation phase, some member states announced specific landing arrangements this week.
Spain: Its securities regulator released a new Q&A document clarifying how to implement MiCA regulations in practice, informing cryptocurrency companies of the expected arrangements they should follow.
Other Developments: Information indicates that the European Commission plans to expand the European Securities and Markets Authority's oversight authority over crypto companies and trading venues, aiming to simplify the EU market. Meanwhile, discussions continue on whether more regulatory powers should be centralized from member states to the EU level.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




