# I. Outlook
## 1. Macroeconomic Summary and Future Predictions
Last week, the core of the U.S. macroeconomic landscape focused on the implementation of policy direction and the revalidation of inflationary pressures. On January 29, the Federal Reserve maintained the upper limit of interest rates as expected, continuing the tone of "wait-and-see but no further tightening," confirming that the rate hike cycle has ended and future actions will depend on data.
Looking ahead, the macro focus will shift from "direction confirmation" to rhythm and patience. If CPI/PCE continues to gently decline and employment further cools, the Federal Reserve will gradually open up more space for a clearer shift towards easing this year; however, in the context of persistent service inflation and sticky wages, the policy rhythm is more likely to be gradual. For the market, short-term macro factors no longer pose a systemic downside risk, but it is also difficult to provide strong stimulus, and asset prices will become more sensitive to single data points. True trend changes will still need to wait for sustained resonance between inflation and employment.
## 2. Market Movements and Warnings in the Cryptocurrency Industry
Last week, the cryptocurrency market experienced a significant accelerated decline, with sentiment and prices spiraling out of control. After being long hindered by the $100,000 resistance level, Bitcoin saw concentrated selling pressure released, resulting in a series of sharp declines throughout the week, with key support levels being quickly breached. The decline exhibited characteristics of a transition from a slow drop to a rapid fall. Trading volume significantly increased during the downturn, indicating that this was not merely a correction, but a simultaneous occurrence of deleveraging and forced liquidations. Mainstream coins generally fell sharply, with altcoins and MEME sectors suffering particularly severe losses, as most tokens experienced double-digit declines, leading to a drastic contraction in market risk appetite.
In terms of warnings, this round of sharp declines marks a shift in the market from "consolidation below resistance levels" to an emotionally driven downward phase. In the short term, if Bitcoin cannot quickly reclaim key lost ground and stabilize, panic sentiment may persist, and volatility will remain high. Coupled with a cautious outlook on macro liquidity, if risk assets come under pressure overall, the cryptocurrency market may continue to amplify its declines. Overall, it is not advisable to underestimate the downward inertia at this stage; before deleveraging is fully completed, one should be wary of the risks of a secondary sharp drop or prolonged low-level consumption.
## 3. Industry and Sector Hotspots
A total of $6 million in financing, led by Hashkey, has been raised for Magma Finance, a decentralized exchange (DEX) designed specifically for blockchains based on the MOVE language; a total of $2 million in financing, led by Mint with participation from 90S, has been raised for Pheasant Network, a DeFAI project dedicated to building an interoperable protocol that realizes an AI-driven intent mechanism.
# II. Market Hotspot Sectors and Potential Projects of the Week
## 1. Overview of Potential Projects
1.1. Brief Analysis of Magma Finance, a $6 Million Financing Project Led by Hashkey—An AMM DEX Achieving CEX-Level Experience on the MOVE Chain
Introduction
Magma Finance is a cutting-edge AMM decentralized exchange (DEX) designed specifically for blockchains based on the MOVE language.
Magma focuses on building a sustainable liquidity incentive engine, aiming to create a decentralized trading platform that leads in both user experience and capital efficiency by aligning the interests of traders, governance participants, and liquidity providers.
Core Mechanism Overview
CLMM (Concentrated Liquidity Market Maker)
Magma Finance's Concentrated Liquidity Market Maker (CLMM) is a high capital efficiency automated market-making mechanism that allows liquidity providers (LPs) to concentrate liquidity deployment within specific price ranges. This approach gives LPs greater control over capital allocation and has the potential to earn higher fee revenues at the same liquidity scale.
Unlike traditional AMMs that distribute liquidity evenly from zero to infinity, CLMM allows LPs to allocate funds in the price ranges they believe are most active for trading, thereby improving capital efficiency and providing deeper liquidity for traders at key price points.
Key features include:
Concentrated Liquidity: LPs can provide liquidity within custom price ranges, enhancing capital efficiency;
Flexible Fee Tiers: Multiple fee options to compensate for different risk levels;
Transferable Liquidity Positions: LP positions are represented as NFTs, which can be traded and transferred.
1. Mechanism Core
Concentrated Liquidity: LPs can concentrate funds within specific price ranges, significantly enhancing capital efficiency and avoiding idle funds in less likely price ranges.
Price Ranges & Ticks: Prices are not continuous but consist of discrete ticks; LPs provide liquidity between the upper and lower ticks, and liquidity is only active when the market price is within that range.
Liquidity Position NFTization: Each concentrated liquidity position is unique and minted as an NFT, recording position parameters and fees, making it tradable and transferable, expanding secondary markets and advanced DeFi use cases.
2. Liquidity Supply Mechanism
Providing liquidity in Magma Finance's CLMM hinges on customizing price ranges:
Setting Price Ranges: Define the minimum and maximum prices at which liquidity becomes effective; narrow ranges enhance capital efficiency but carry higher risk, while wider ranges are more robust but less efficient.
Depositing Assets: If the current price is within the range, two types of assets must be deposited; if below the range, only the quoted asset is deposited; if above the range, only the base asset is deposited.
Minting Position NFT: An NFT representing the liquidity position is generated upon transaction confirmation, used for managing liquidity and collecting fees.
3. Swap Mechanism
Magma's Swap mechanism is based on the concentrated liquidity design of Ticks and price ranges, allowing LPs to provide active liquidity only at specific price points, thereby earning higher fees and reducing impermanent loss within target ranges.
Ticks and Price Ranges: Prices are divided into discrete ticks, and LPs can concentrate liquidity within selected tick ranges, only being effective within that range and earning higher fees.
Price Impact: Large trades can push price changes when liquidity is insufficient; the system provides impact estimates to enhance trading transparency.
Slippage: The difference between the expected price and the execution price; users can set slippage tolerance, and trades exceeding this will be rolled back.
Aggregator: Aggregates liquidity from multiple DEXs and offers optional routing to optimize prices and reduce slippage.
ALMM (Adaptive Liquidity Market Maker)
Magma's ALMM (Adaptive Liquidity Market Maker) is an evolution of traditional AMMs and CLMMs, concentrating liquidity at fixed price points based on price tiers (Bins) to form a ladder-like curve similar to an order book. Compared to CLMM's range management:
Higher Capital Efficiency: Discrete Bins eliminate ineffective price ranges, avoiding liquidity waste.
Dynamic Fees: Fees adjust adaptively with market fluctuations (unlike CLMM's fixed rates).
Simplified LP Experience: No need for complex price range management.
Zero Slippage within Ranges: Trades within active Bins execute at fixed prices.
1. Bin (Price Tier) Structure
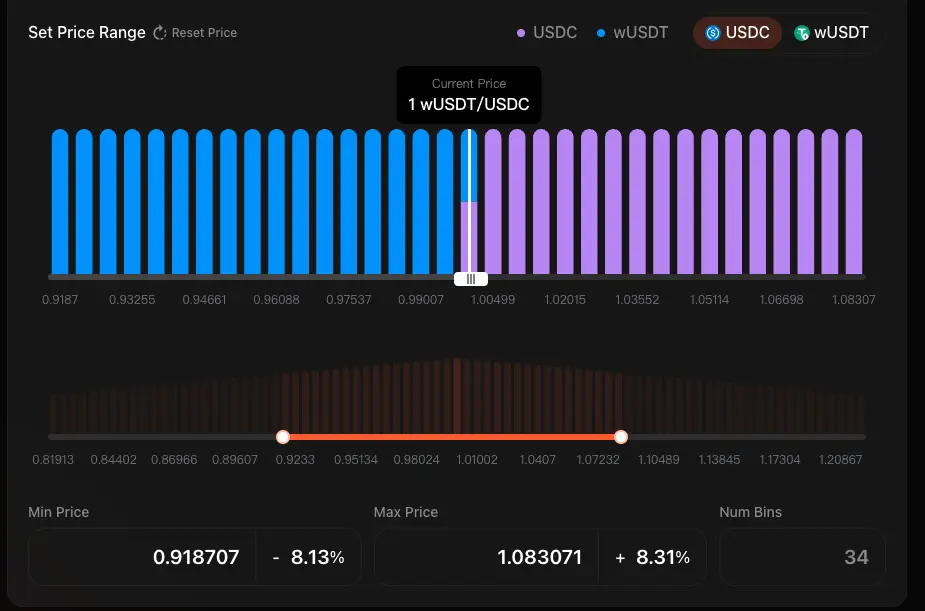
The core of Magma ALMM is the Bin (Price Tier) structure:
Bin Structure: Liquidity is divided into multiple discrete Bins, each corresponding to a fixed price point.
Fixed Price Execution: Within a Bin, constant and formulaic (X+Y=k) trading occurs at that price point with zero slippage until one asset is exhausted.
Active Bins: Only active Bins hold both types of assets simultaneously and generate trades and fees; the left and right Bins hold single assets.
Bin Step: Determines the price difference between adjacent Bins; smaller steps are more precise and managed more frequently, while larger steps are better suited for high-volatility pairs.
Concentrated Liquidity: LPs can allocate funds to Bins within selected price ranges, using capital only in high-frequency trading intervals to maximize fee revenues.
2. Trading Mechanism
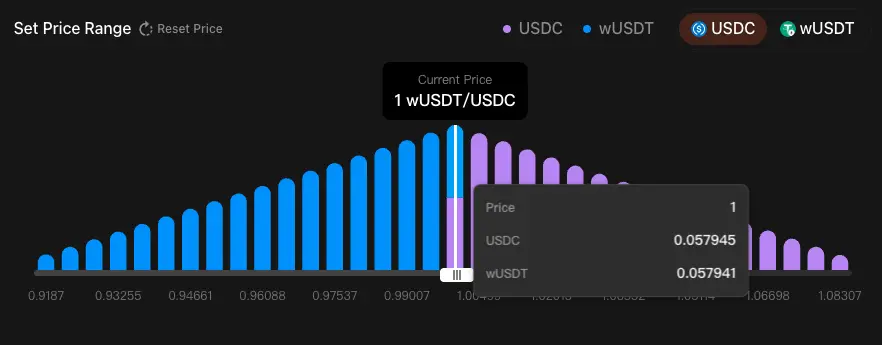
Magma's ALMM trading mechanism is based on Bins (Price Tiers):
Trading Process: First, use the liquidity of the active Bin to execute trades at fixed prices; if exhausted, switch to the next Bin.
Price Impact: Occurs only when trades push prices across Bins.
Slippage: Zero slippage within a single Bin; slippage occurs only when crossing multiple Bins.
Active Bin Mechanism: Only active Bins hold both types of assets simultaneously and support trading, using constant and formulaic (X+Y=k).
Effect: Ladder-like execution simulates a limit order book while maintaining the decentralization and composability of AMMs.
3. Liquidity Supply Mechanism
Magma ALMM allows LPs to distribute funds across multiple price Bins through different liquidity shapes, enabling a range of strategies from passive to highly active.
Liquidity Shapes: Refers to how LPs allocate liquidity within price Bin ranges to implement different strategies.
Spot (Uniform Type): Uniformly allocates liquidity within selected ranges; robust strategy, balanced risk, suitable for beginners or wide-range market making.
Curve (Curved Type): Concentrates more liquidity near the current price, gradually decreasing further away; high capital efficiency, significant fee potential, but more sensitive to price changes.
Bid-Ask / Inverse Curve: Concentrates liquidity in Bins far from the current price, often used for unilateral liquidity; can implement advanced strategies like "buy low, sell high" or DCA.
Tron Comments
The core advantage of Magma Finance lies in its advanced liquidity system built around the MOVE ecosystem, transitioning from CLMM to ALMM. By utilizing a Bin structure, zero slippage interval trading, dynamic fee rates, and programmable liquidity shapes, it significantly enhances capital efficiency and trading experience while reducing the operational complexity for LPs and maintaining order book-level precision. Its first-mover advantage on MOVE chains like Sui positions it to become a core liquidity layer in the ecosystem.
However, its disadvantage is the high complexity of the model, which requires a deeper understanding of strategies and risk management from LPs. Bin management and cross-tier price fluctuations may still amplify risks in highly volatile markets, and the overall scale and user base of the MOVE ecosystem are still small, necessitating ecological maturity to validate liquidity depth and long-term stability.
1.2. Interpretation of $2 Million Financing, Led by Mint with Participation from 90S—The DeFAI Protocol Pheasant Network, Reshaping Cross-Chain Experience with AI Intent
Introduction
Pheasant Network is a DeFAI project dedicated to building an interoperable protocol that realizes an AI-driven Intent mechanism.
This protocol seamlessly connects fragmented blockchain ecosystems while ensuring security, thereby enhancing cross-chain interoperability and simplifying cross-chain interaction processes.
Architecture Overview
Pheasant Bridge
Pheasant Bridge is a cross-chain bridge protocol centered around Intent, utilizing AI-driven AIntent logic to understand user and application goals, automatically selecting the optimal and safest cross-chain path, unifying Layer 2 infrastructure, and connecting to the Ethereum ecosystem. Its optimistic Bridge-as-a-Service (BaaS) provides developers with native integration capabilities, combining low-cost, decentralized design with real-time network adaptive optimization to deliver a smoother and more predictable cross-chain experience.
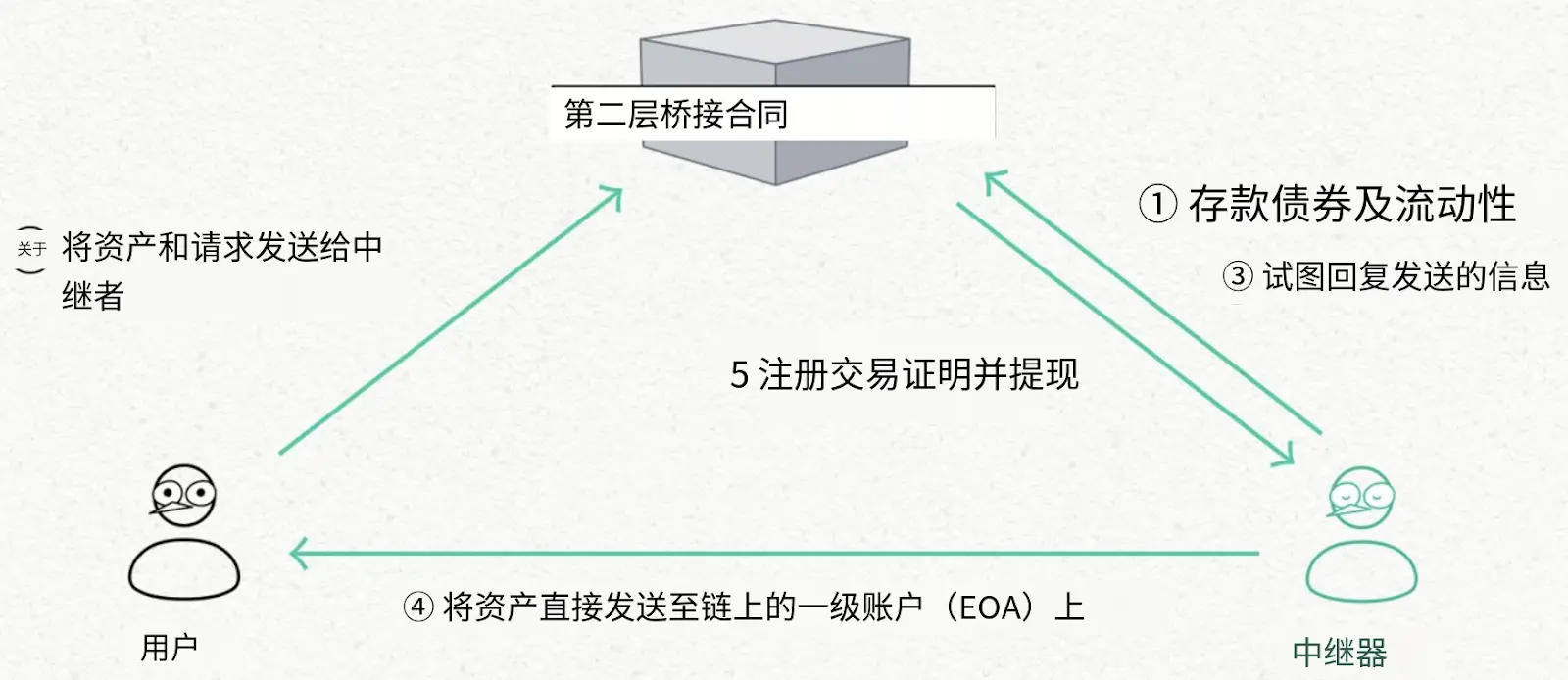
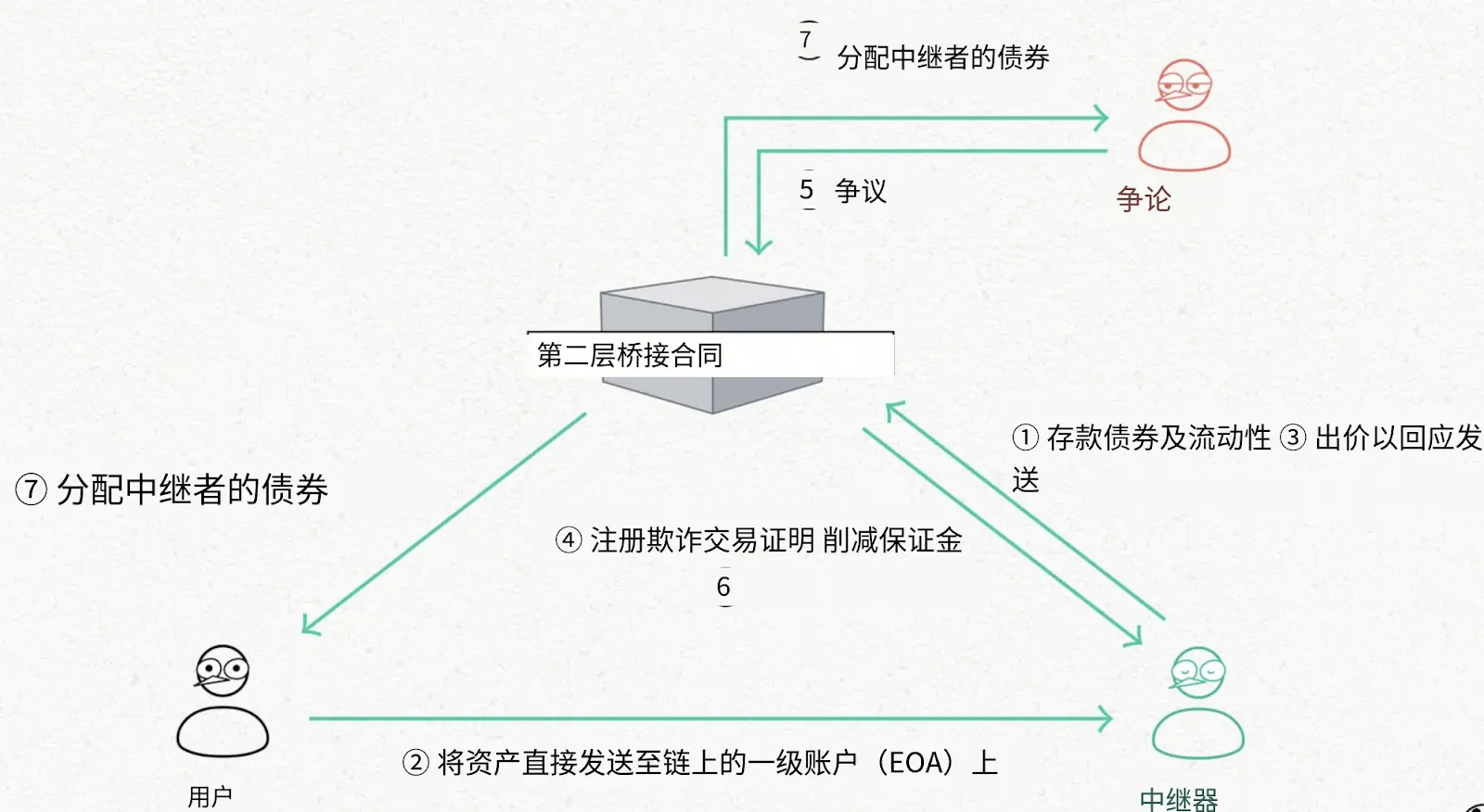
1. L2→L1 / L2→L2 Cross-Chain Uses an Optimistic Relayer Model:
Default Process: Relayers stake liquidity to the BondManager (L2 bridge contract); users submit transfer requests in the source chain contract; relayers directly transfer to user addresses on the target chain; relayers submit proof generated from the transaction hash to withdraw the user's locked assets.
Fraud Handling: Disputants stake assets to initiate challenges; relayers must submit evidence to prove their legitimacy within a specified time; if the relayer is legitimate, the disputant is penalized; otherwise, the disputant can punish the relayer and reclaim their assets.
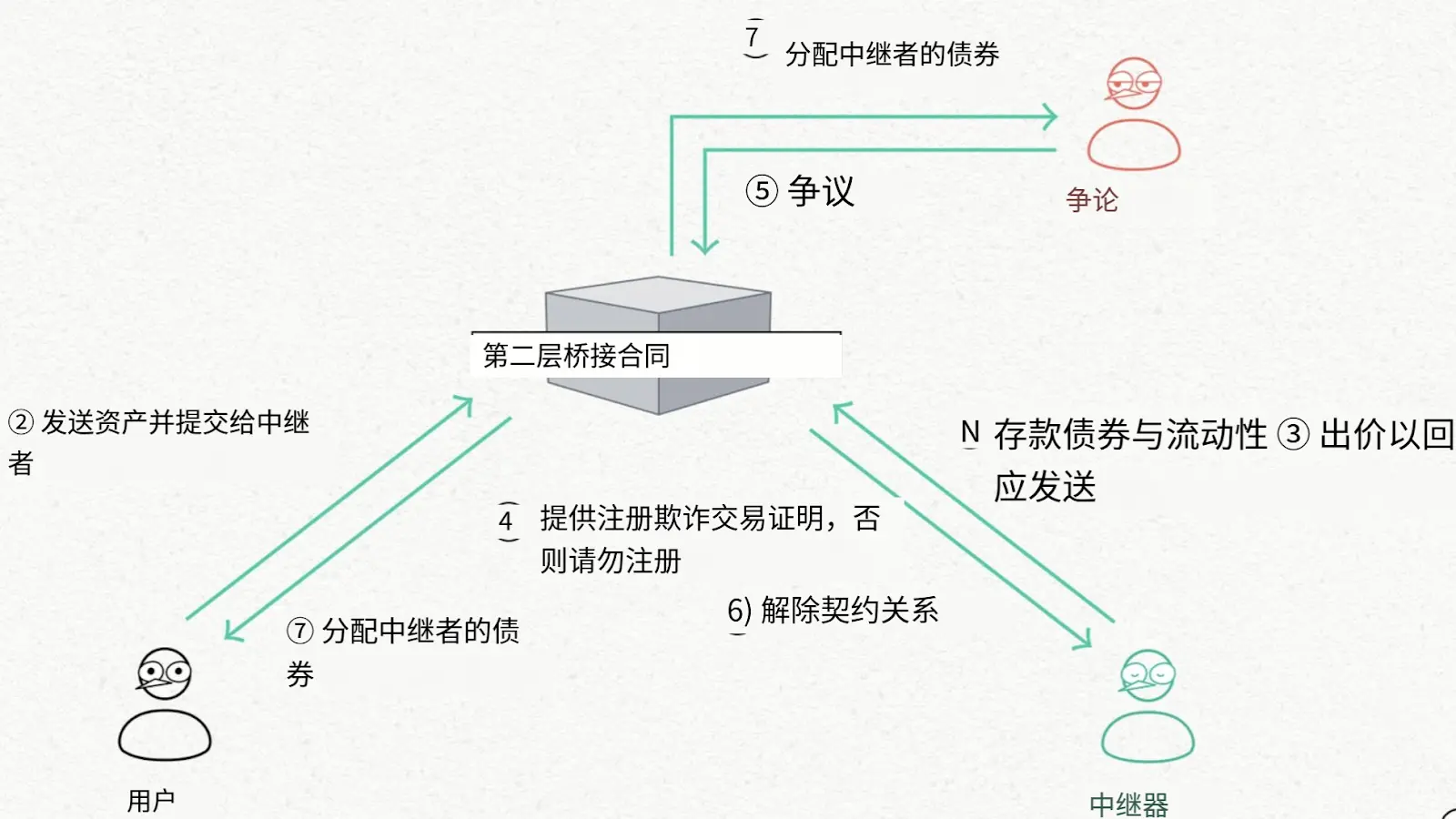
2. L1→L2 Cross-Chain
Pheasant employs a different mechanism for L1→L2 cross-chain to avoid the high costs associated with deploying custodial contracts on the L1 side.
Default Process: Relayers stake liquidity to the BondManager (L2 bridge contract); users directly transfer assets to the relayer's EOA on L1; relayers generate proof based on the transaction hash and send assets to users via the L2 bridge contract.
Fraud Handling: If relayers fail to send assets to L2 within the specified time, the system can penalize them (Slash) to protect user rights.
3. Circle's Cross-Chain Transfer Protocol (CCTP)
Pheasant Network employs a dual-track mechanism for USDC cross-chain:
Mechanism Selection: Small amounts of USDC use the optimistic protocol; large amounts of USDC automatically utilize CCTP.
CCTP Process:
Users burn (Destroy) USDC in the source chain via a contract;
Relayers request authorization from the CCTP certification service;
Upon approval, USDC is minted on the target chain;
Newly minted USDC is credited to the user's target chain account.
Pheasant Swap
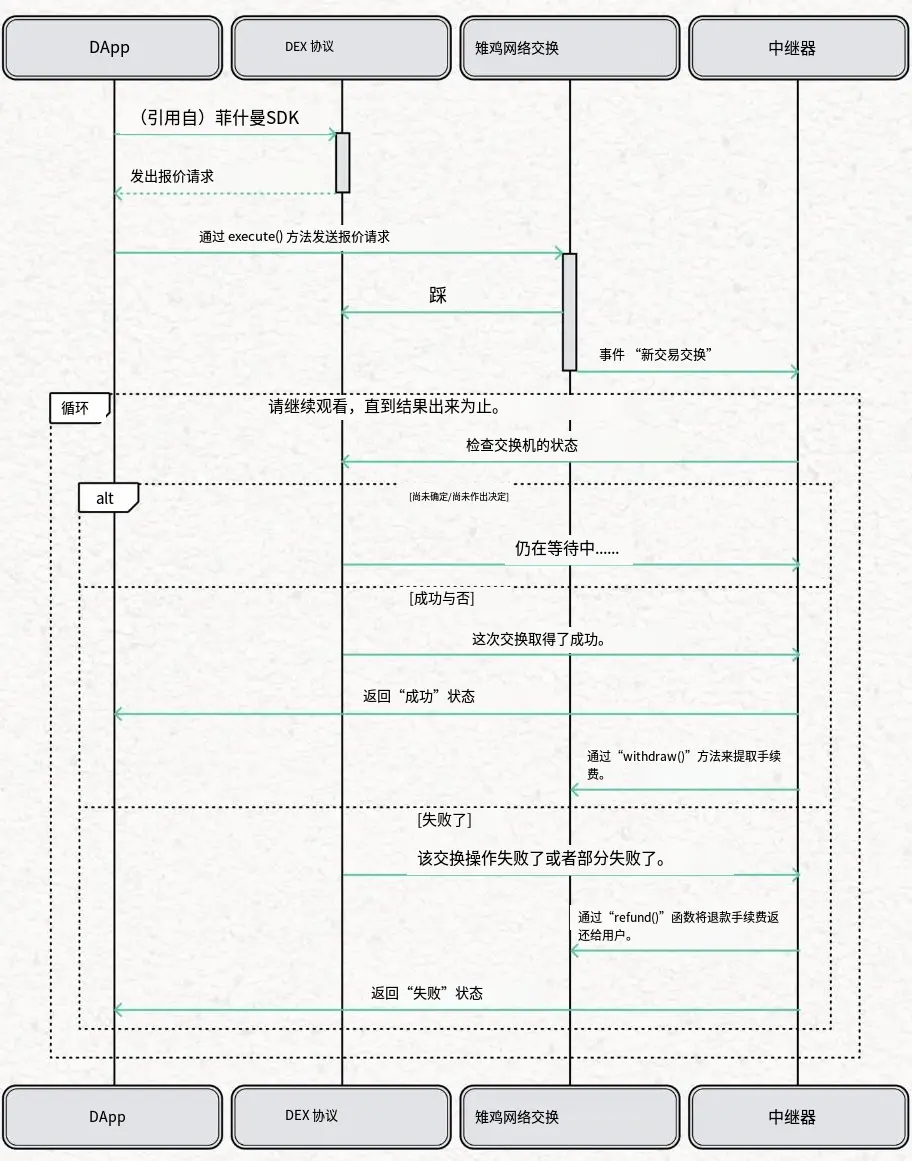
Pheasant Swap is a cross-chain exchange protocol that merges cross-chain bridging and asset swapping into a single operation, allowing users to complete cross-network asset exchanges in one transaction. This integrated design reduces liquidity and process fragmentation in multi-chain ecosystems, significantly enhancing the efficiency of cross-chain transactions and the overall user experience.
The architecture of Pheasant Swap consists of four main components:
DApp: A decentralized application with cross-chain exchange functionality. The DApp uses the Pheasant SDK to quote exchange requests and submits them to the PheasantNetworkSwap contract for execution.
DEX Protocol: A decentralized exchange protocol integrated with Pheasant Network that receives exchange requests from the PheasantNetworkSwap contract, completes transactions, and returns results to the DApp.
PheasantNetworkSwap Contract: A smart contract responsible for coordinating and executing the exchange process, routing requests to the appropriate DEX protocol.
Relayer: Tracks the entire process of the exchange from initiation to completion; if the exchange is successful, the relayer collects the corresponding fee; if it fails, the relayer refunds the transaction fee to the user.
Tron Comments
The core advantage of Pheasant Network lies in its AI-driven Intent architecture, integrating cross-chain bridging and cross-chain swapping into one, automatically selecting the optimal path through AIntent, achieving a lower-cost, higher-efficiency, and more user-friendly cross-chain experience in L1↔L2 and L2↔L2 scenarios. Its optimistic relayer model, punitive mechanisms, and dual-track USDC solution with CCTP dynamically balance speed and security while providing developers with modular Bridge/Swap as a service capabilities, significantly reducing the complexity of multi-chain integration.
However, its disadvantage is the overall complexity of the system architecture, which relies on the activity of the relayer network, the effectiveness of the game theory mechanisms, and AI path selection. Early-stage stability in liquidity depth, network coverage, and extreme scenarios still needs to be validated through scaled operations and time.
2. Key Project Details of the Week
2.1. Detailed Explanation of $48.5 Million Financing, Led by Polychain and Dragonfly, with Follow-On Investment from VanEck—DAWN, a Bandwidth Market Protocol Breaking Internet Retail Price Gaps with Token Incentives
Introduction
DAWN is a protocol driven by token incentives, utilizing cutting-edge technology to build a new "ultimate internet," with goals including:
Directly connecting users to Internet Exchange (IX) centers without any trusted intermediaries;
Narrowing the gap between wholesale and retail internet prices by up to 100 times;
Enhancing network resilience by eliminating reliance on a single path through the use of distributed home nodes.
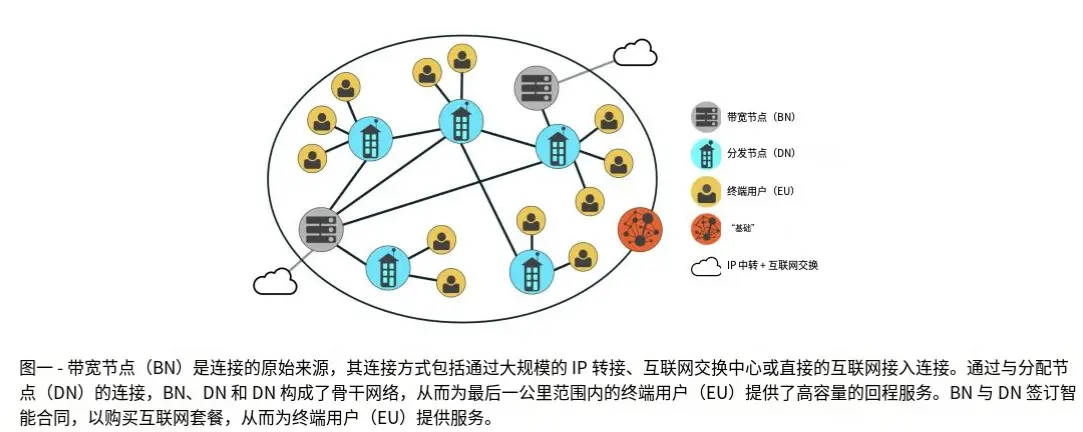
This new last-mile internet consists of three core components:
Incentive Mechanism: Rewards participants based on their contributions and performance to the network, covering roles such as data centers, building owners, and network equipment deployers;
Decentralized Consensus Mechanism: Such as "Proof of Bandwidth" and "Proof of Location," providing cryptoeconomic guarantees for network performance;
Bandwidth Market: Allows node operators to buy and sell network connection capabilities, enabling home nodes to achieve substantial returns by saving internet costs and reselling bandwidth, turning network deployment into a profitable investment.
DAWN Architecture Overview
The DAWN protocol aims to build a self-healing, multi-gigabit, autonomous last-mile wireless network through the deployment of rooftop robotic radio devices.
Its core goal is to create a decentralized fixed internet connection method, fundamentally liberating users from dependence on traditional Internet Service Provider (ISP) monopolies.
1. Node Types
Participants in the DAWN network must play at least one of the following roles:
① Bandwidth Node (BN)
Must possess resalable wholesale-level internet bandwidth (such as IP Transit or Internet Exchange access);
Deploy DAWN-certified >1Gbps point-to-multipoint radio devices;
Provide connections downstream within a maximum line-of-sight range of 5 miles;
A single BN can serve 15–100 receiving nodes.
② Distribution Node (DN)
Typically a commercial or residential building;
Connects to one or more BNs via rooftop robotic antenna systems (RAS);
Can simultaneously connect in real-time with multiple BNs or other DNs;
Forms the core layer of the DAWN programmable, self-healing wireless network.
③ End User (EN)
- The final user who obtains and uses bandwidth from the DN.
④ Foundation
Controls the core smart contracts of DAWN through multi-signature;
Responsible for key functions at the global network layer, including:
Node identity and authentication
Blockchain and node communication
Compliance and regulation
QoS (Quality of Service) monitoring
Payment, settlement, and transaction processing, etc.
2. Wireless Devices and Robotic Antenna Systems (RAS)
Vendor-agnostic: DAWN does not bind to specific hardware suppliers;
Initially focuses on supporting multi-gigabit wireless technologies such as 60GHz millimeter wave and 6GHz frequency bands;
BN and DN combine point-to-multipoint + point-to-point radios and antennas;
Dynamically propagates connections in the last mile through electromechanical beam steering.
This entire set of hardware and software systems is referred to as the Robotic Antenna System (RAS), characterized by:
Support for any future generation of wireless hardware;
Deployable without professional human intervention;
Low-cost, self-healing, and rapid scalability;
Suitable for trustless decentralized environments.
3. Routing and Network Layer Design (Routing Elements)
DAWN does not use traditional dedicated routing hardware but adopts:
General-purpose computing devices + Cloud-Native Routing;
Future home routers will evolve into general-purpose home servers rather than closed MIPS/ARM devices;
Software routing solutions such as VPP, Quagga, BIRD, and FRR are used based on node performance requirements.
Network Protocol Selection
IPv6 as the primary Layer 3 protocol;
IPv4 supported in a dual-stack manner, introducing a staking mechanism to reflect the scarcity of IPv4 addresses;
Uses eBGP and its security features to manage network traffic;
Each node logically acts like an independent Autonomous System (AS), naturally compatible with internet backbone design.
Network Trust and Verification Mechanism
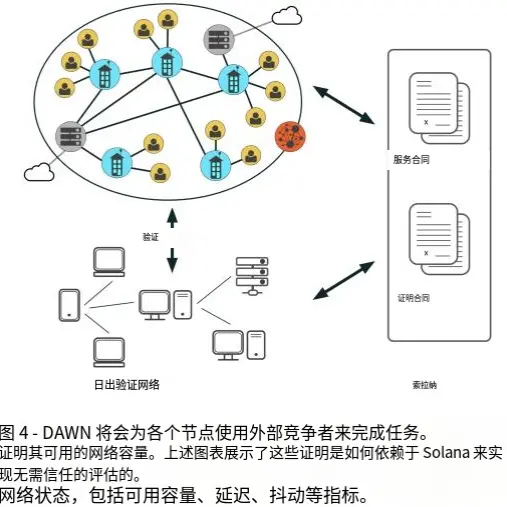
A key feature of DAWN is the use of a trustless cryptoeconomic incentive mechanism to replace the reputation system and manual accounting found in traditional centralized networks.
In the wireless network scenario, this means that performance cannot rely on operators' self-reported metrics but must be objectively measured through "Proofs of Network Resources," with the core being Proof of Bandwidth.
DAWN chooses to access the decentralized proof network provided by the Witness Chain:
The Witness Chain has built a mature proof system for bandwidth, data usage, location, etc.;
This network is secured by re-staked ETH (with a scale reaching tens of billions of dollars);
DAWN directly subscribes to these proofs for network settlement and incentives.
1. Three Types of Service Contracts in DAWN (Service Contracts)
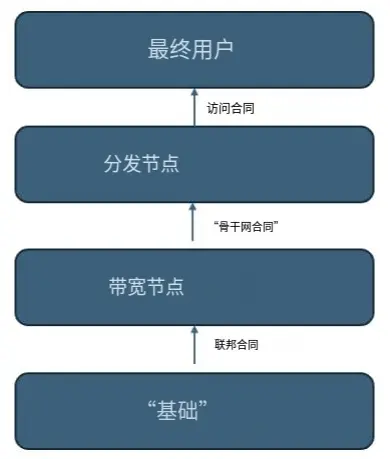
The DAWN protocol defines three core contract relationships, all settled in DAWN Tokens:
Federal Contracts
From Foundation → Network Nodes;
Used for global incentives, subsidies, and guiding network expansion.
Backbone Contracts
Bandwidth Node (BN) ↔ Distribution Node (DN);
Represents the protocol between wholesale-level bandwidth and downstream distribution.
Access Contracts
Distribution Node (DN) ↔ End User (EN);
Represents the bandwidth usage agreement for end users.
2. Network Resource Proof System (Proofs of Network Resources)
DAWN abstracts "network performance" into verifiable resource proofs, mainly including the following categories:
1. Proof of Backhaul
Essentially a decentralized speed measurement system;
Challenger nodes send packets to BN/DN to measure:
Throughput
Latency
Results are used to determine:
Bandwidth reservation amounts
Oversell ratios
Completely decentralized, without relying on operator self-reporting.
2. Proof of Service
A decentralized data measurement and settlement system;
Used to replace traditional ISPs' centralized billing systems;
Both parties (supplier and user) submit signed usage data;
The system automatically deducts fees and settles after reconciliation;
Achieved through permissionless payment channel contracts.
3. Proof of Location
Used to ensure that nodes are genuinely located at their declared geographical positions, employing a two-layer verification mechanism:
First Layer (Wired Location Proof):
Based on network latency and path characteristics;
Uses the challenge node network of the Witness Chain;
Combines internet latency-distance curve models to verify the approximate location of BN.
Second Layer (Wireless Precision Location):
Based on decentralized radio triangulation;
GNSS (such as GPS) as a backup solution;
Suitable for precise positioning of BN and DN.
4. Proof of Frequency
Used to address spectrum coordination issues for unregulated frequency bands like 60GHz:
Nodes must stake tokens to gain exclusive rights to a certain frequency band;
Neighboring nodes will scan the spectrum to verify the absence of interference;
Verifiers receive rewards through smart contracts;
The Foundation provides:
Terrain/obstacle data (Clutter Data)
GIS challenge tasks
Nodes verify based on encrypted local data:
Signal strength (RSSI)
Whether the propagation model is reasonable
Ultimately forming a trustless wireless propagation heatmap to determine available frequency bands.
Tron Comments
The core advantage of DAWN lies in its foundation on cryptoeconomics, combining decentralized verification mechanisms such as Proof of Bandwidth, Proof of Location, and Proof of Frequency to construct a trustless last-mile internet network. This allows homes, buildings, and data centers to directly participate in network construction and revenue distribution, structurally breaking the monopoly of traditional ISPs, significantly reducing internet access costs, and enhancing network resilience. Its self-healing wireless architecture, vendor-agnostic design, and Solana-based high-performance settlement provide good scalability and capital efficiency.
However, its disadvantages include a high entry threshold, strong reliance on hardware deployment, line-of-sight conditions, and local regulations. Service quality may be unstable in the early stages when network density is insufficient. Additionally, the complex proof system and multi-role collaboration mechanisms increase the costs of system design, operation, and user understanding, requiring time and continuous incentives for large-scale promotion.
### Industry Data Analysis
1. Overall Market Performance
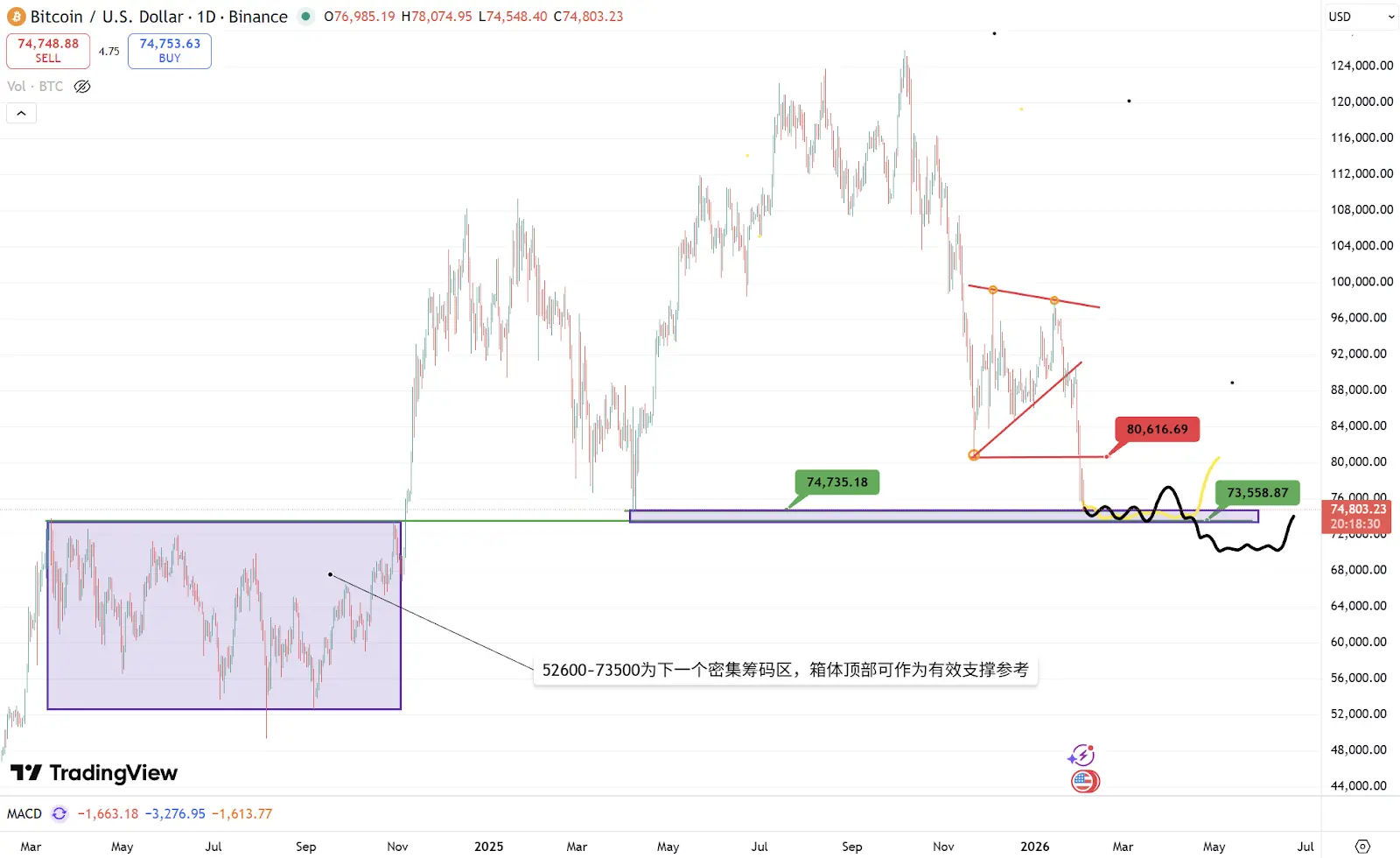
1.1. Spot BTC vs ETH Price Trends
BTC
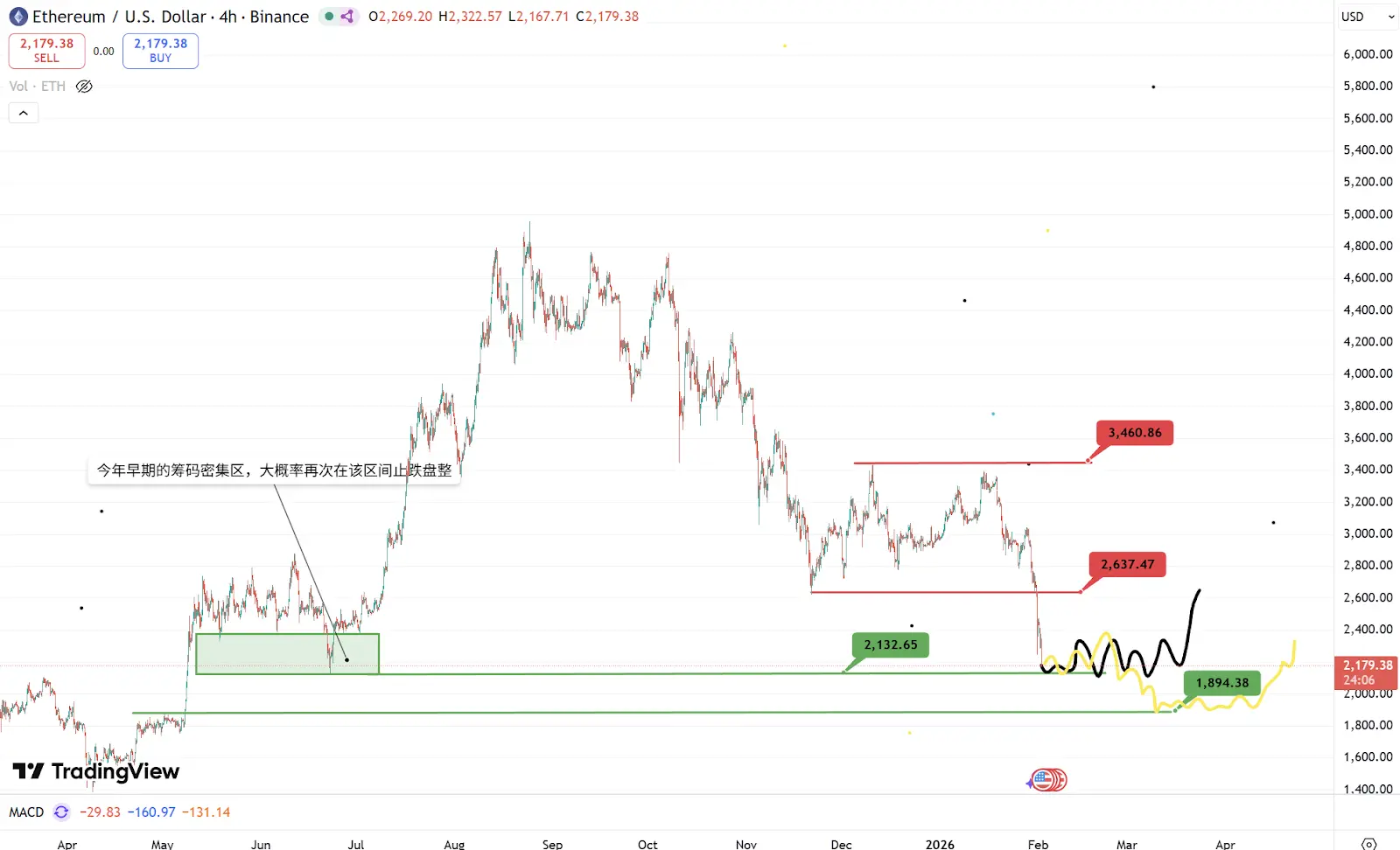
ETH
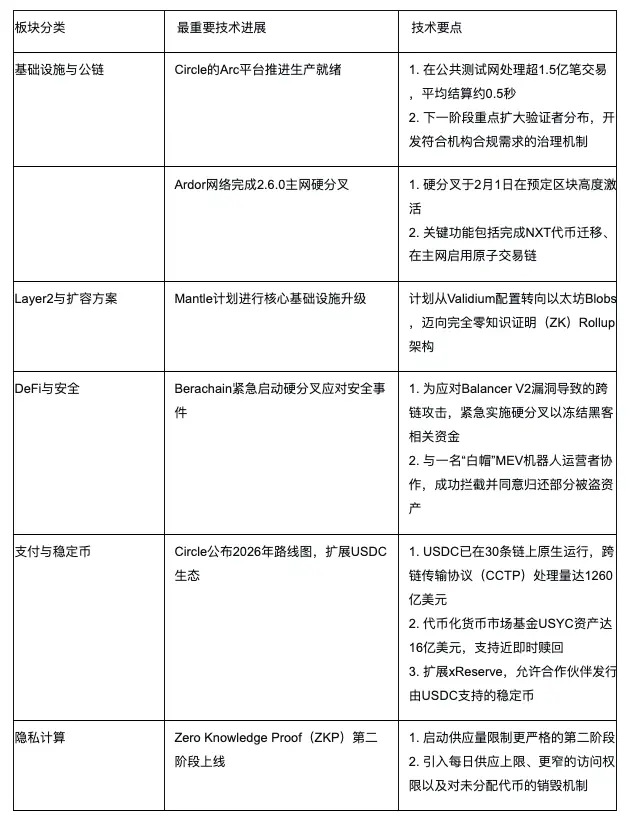
2. Summary of Hot Sectors
### 3. Macroeconomic Data Review and Key Data Release Points for Next Week
On January 29, the Federal Reserve's interest rate decision maintained the upper limit unchanged as expected, which did not bring any surprises at the policy level. The market was more focused on "no more hawkish," consistent with the backdrop of falling inflation and cooling employment. The decision reinforced a neutral dovish tone of "the rate hike cycle has ended, but rate cuts still need to wait for data." U.S. stocks reacted positively but restrained, with indices oscillating at high levels, indicating that funds recognized the direction of the policy turning point but did not significantly increase positions, maintaining existing long positions instead.
The December PPI year-on-year data released on January 30 continued to weaken, confirming that upstream price pressures are easing and not transmitting new inflation risks to the CPI side. This data further alleviated concerns about inflation rebound and left room for the Federal Reserve's subsequent policies. U.S. stocks interpreted this data positively, with risk appetite receiving marginal support, but the gains remained limited, reflecting that the current market is more concerned about growth and profitability rather than uncontrolled inflation.
Overall, these two events jointly solidified an environment of "no further tightening in policy, controllable inflation," allowing U.S. stocks to maintain resilience at high levels rather than entering a trend of significant rise or fall.
Important macroeconomic data to be released this week:
February 6: U.S. January unemployment rate; U.S. January seasonally adjusted non-farm payrolls.
### 4. Regulatory Policies
United States
Legislative Progress: On January 21, the U.S. Senate Agriculture Committee released an updated legislative text for the "Digital Commodity Exchange Act" (the text was discussed within the relevant time window). This text establishes a framework for digital commodity intermediaries (such as exchanges and brokers) to register with the U.S. Commodity Futures Trading Commission (CFTC) and introduces an expedited registration process. Additionally, Congress is advancing a broader cryptocurrency market structure bill.
Regulatory Dynamics: The U.S. Securities and Exchange Commission (SEC) approved a rule change submitted by the Nasdaq BX exchange, lifting restrictions on certain crypto assets. This change took effect immediately after being submitted on January 26.
European Union
Implementation of New Tax Regulations: The EU directive DAC8, aimed at enhancing tax transparency, officially came into effect on January 1, 2026. This directive requires crypto asset service providers to collect users' tax information and report transactions. If users fail to provide the required information within 60 days, service providers must forcibly block them from conducting reportable transactions.
Member State Actions: Germany has transposed DAC8 into domestic law through the "Crypto Asset Tax Transparency Act," with core obligations including customer due diligence, annual transaction reporting, and registration with the Federal Central Tax Office.
Dubai
- New Regulatory Framework in Effect: The Dubai International Financial Centre launched a revamped regulatory framework for crypto tokens in mid-January. Key changes include: a clear prohibition on trading privacy coins (such as Monero); a strict and narrowed definition of fiat-backed stablecoins; and the transfer of token approval responsibilities to licensed institutions.
Japan
- International Tax Compliance: Japan will officially implement the "Crypto Asset Reporting Framework" (CARF) established by the OECD starting January 1, 2026, aimed at sharing crypto asset transaction information internationally to enhance tax transparency. Domestic exchanges have begun notifying users to submit information such as their tax residency.
China
- Regulatory and Risk Warnings: The Central Political and Legal Affairs Work Conference proposed to proactively study legislative suggestions regarding new issues such as virtual currencies, marking a new phase in the governance of virtual currencies. Concurrently, regulatory authorities in multiple regions, including Heilongjiang, Hebei, and Hunan, have issued risk alerts, warning against illegal financial activities under the guise of virtual currencies and RWA (Real World Asset tokenization), and exposing common scams, pyramid schemes, and money laundering tactics.
Welcome to join the ChainCatcher official community
Telegram Subscription: https://t.me/chaincatcher;
Official Twitter Account: https://x.com/ChainCatcher_
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




