If you are anxious and unable to sleep due to oversized investment positions, frequently checking your phone, then your capital allocation has clearly exceeded your risk tolerance.
Written by: SafePal
"The Dark Forest," a concept derived from "The Three-Body Problem," is the most naked summary of the current Web3 security landscape: There is ample room for imagination and innovative gameplay on-chain, but it is also like a "dark forest," filled with bloody and cruel zero-sum games, where ordinary investors often play the role of "prey" in an information asymmetry.
On November 16, multiple community users reported that the on-chain trading terminal DEXX was hacked. Subsequent analysis revealed significant vulnerabilities in DEXX's private key management, which even included plaintext transmission and storage. As of now, the total losses, based on incomplete statistics, exceed $20 million.
In this context, how ordinary users can improve their on-chain self-protection mechanisms has become a highly concerned topic. SafePal co-founder and CEO Veronica participated in the 137Labs-hosted 𝕏 Space event "Security Reflections Triggered by the DEXX Incident: How to Avoid 'Pits' in Crypto Investment," discussing the DEXX security incident with BlockSec founder Andy, senior trader Huise哥, 137Labs researcher OneOne, and others, providing practical security advice for crypto investors.
This article is a summary of the insightful shares from the guests during this Twitter Space, organized for readers.
The "Unbearable Weight" of Front-Running Bot Tools
In crypto investment, high returns and absolute security are often difficult to balance. Trading Bot tools like DEXX and Unibot have gained user favor due to features like one-click following and rapid fund transfers, but this convenience is built on a centralized architecture that requires users to authorize funds or provide wallet access, significantly increasing asset risk.
However, users generally underestimate the security requirements of these trading tools, habitually trusting large exchanges while ignoring the risks of smaller tool platforms. The DEXX incident exposed fatal flaws in the private key management of some trading tools—a true "non-custodial wallet" should ensure that private keys are stored only on the user's device, rather than relying on centralized servers. Even if private keys are encrypted, lacking memory-level security support (such as TEE or enclave) still does not eliminate the possibility of theft.
At the same time, the attack method was complex, with hackers dispersing and transferring funds to increase tracking difficulty. This not only makes it harder to recover funds but also suggests that similar future incidents may be more complex and difficult to prevent, leading to two possibilities: either the platform is breached due to technical vulnerabilities, or there is internal collusion or deep infiltration. If it is the latter, future risks may be even more severe.
Dune data shows that the current top five trading bots by volume are: Trojan, BonkBot, Maestro, Banana Gun, and Sol Trading Bot, with 7-day trading volumes exceeding $100 million and cumulative user numbers exceeding 300,000. Because of this, the mentality of "either making a fortune or going to zero" has led most users to overlook the potential massive risks.
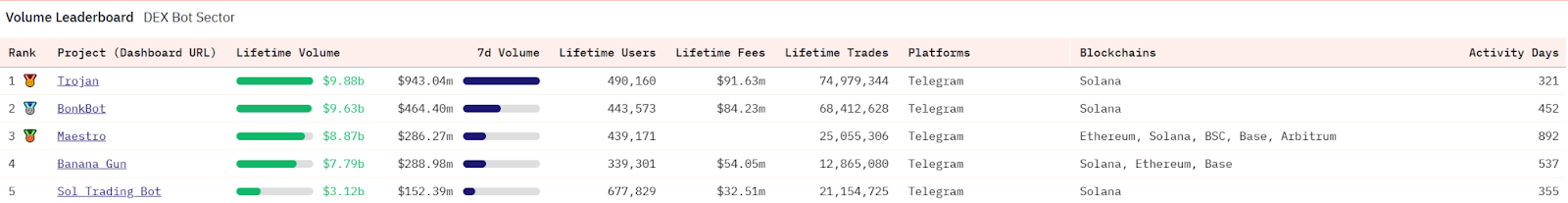
Image source: Dune
Veronica believes that almost all such "front-running" trading tools may face similar security risks. These bots can achieve ultra-fast on-chain trading and avoid manual signing each time because they sacrifice some security and non-custodial characteristics:
Typically, whether using hardware wallets, app wallets, or browser extension wallets, users need to spend a few seconds for manual signature confirmation. However, to improve trading speed and optimize user experience, these bots often compromise by minimizing the security of some private keys to achieve faster transactions.
This design is not entirely wrong, nor can it be simply said that these projects are unsafe. However, it does place extremely high demands on the development team's security capabilities. To achieve a smooth experience, if the development team cannot ensure strong security defense capabilities, the consequences of an attack will be extremely severe, and both users and project parties may face significant losses.
In addition, most trading bots currently face a significant security risk—to achieve automated trading, they typically generate and store private keys for each user. While this method facilitates automated following, it also brings extremely high security risks. If an attacker breaches the platform, all stored user private keys may be leaked, leading to asset losses.
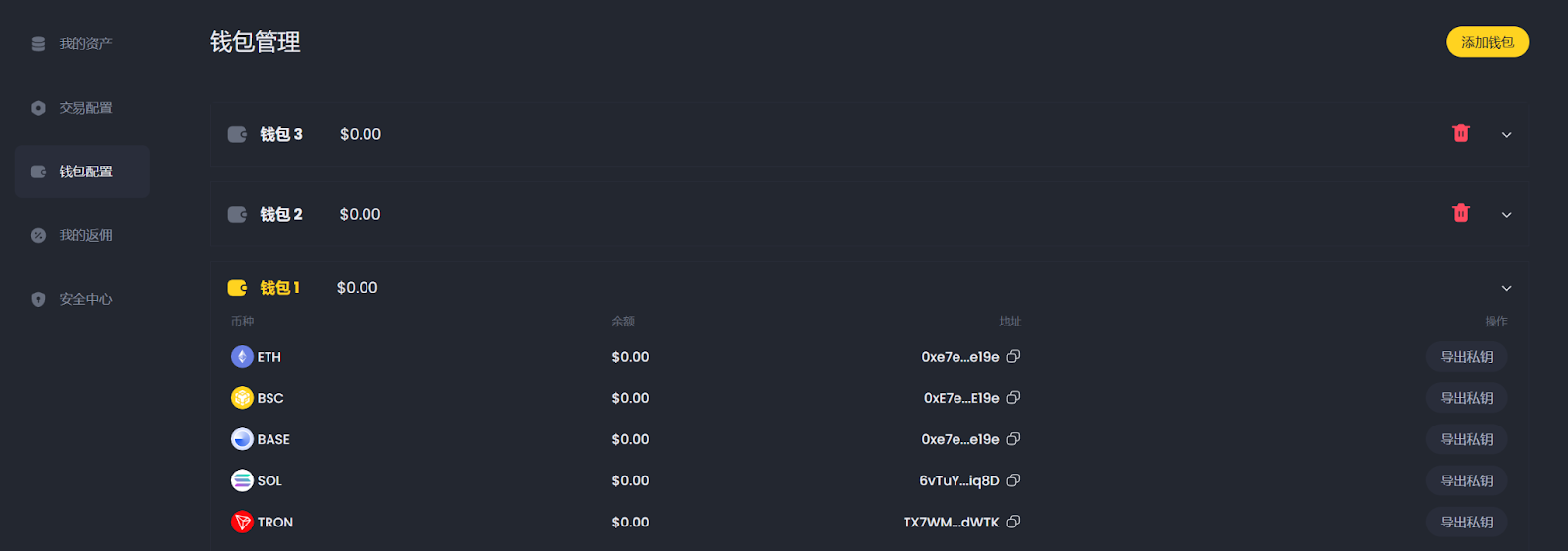
Image source: DEXX "Wallet Management" page
However, there is actually a safer trading architecture that can achieve automated trading without using user private keys:
This architecture relies on smart contracts, creating a "PDA account" associated with the user account to complete transactions without requiring user private key signatures. The platform can execute transaction instructions through a restricted "operational account," but the permissions of this operational account are strictly controlled, allowing only trading operations and preventing arbitrary transfers of user assets.
This smart contract-driven design can significantly enhance security because the user's private key is always in their control and is not stored on centralized servers. Although this design is more complex and requires higher engineering and security technology capabilities from the team, it is entirely feasible and more secure.
Currently, most users are not aware of the differences between these two design patterns or may overlook security in pursuit of convenience. However, with the frequent occurrence of security incidents, both users and development teams may increasingly value safer architectures. This advanced design solution is expected to gradually become popular in the future, reducing the occurrence of similar DEXX incidents.
From Transaction Authorization to Private Key Protection in the Web3 Security Chain
OneOne believes that on-chain security risks can currently be divided into two major categories, covering aspects from transaction authorization to private key protection.
The first common attack method is "Approve Deception." For example, sending a small amount of crypto assets or airdropping NFTs through "dusting attacks" to entice users to click and authorize transactions. This operation may allow attackers to gain access to the user's wallet permissions, thereby stealing the user's assets (including cryptocurrencies and NFTs). Users should be cautious when handling tokens and airdrops from unknown sources to avoid granting authorization easily.
Private key theft generally occurs in several ways:
- The first is "malware attacks," where some attackers pretend to invite users to test new projects, tricking them into downloading executable files containing Trojan viruses. Once infected, the user's private key and account password can be easily stolen.
- The second is "clipboard attacks," where attackers gain access to the user's clipboard through phishing websites. When users copy and paste their private keys, these sensitive information can be intercepted and exploited by attackers.
- Additionally, there are cases of "remote control attacks," where malicious remote software controls the user's computer, even stealing private keys directly while the user is resting. For example, airdrop users often use "fingerprint browsers," which typically involve cloud storage features. If breached, users' assets can be easily stolen. Many users do not set up two-factor authentication (2FA) when using these tools, further exacerbating the risk.
- Finally, there is the "input method hazard." Many users prefer using smart input methods, but these input methods may collect user input data and store it in the cloud, increasing the possibility of private key leakage. It is recommended that users try to use the system's built-in input method, which, although less functional, is more secure.
Overall, when users engage in on-chain transactions, especially when using DeFi applications or trading tools, they need to take additional security precautions, with authorization management being a highly important issue. Due to Ethereum's mechanism requiring users to grant token authorization to smart contracts, attackers can exploit this authorization mechanism for malicious operations. Therefore, users should regularly check their wallet's authorization list and promptly revoke unnecessary authorizations, especially those early authorizations that may have been forgotten, to reduce risk.
Moreover, when users choose DeFi platforms, they should review the platform's security measures, including whether there are comprehensive audit reports, ongoing automated security monitoring, and whether the platform regularly upgrades and patches vulnerabilities. When using trading bots, it is advisable for users to ensure that their assets are managed in a diversified manner, not to store large amounts of funds in accounts controlled by trading bots, and to transfer funds to safer wallets as soon as profits are made, to minimize potential losses.
Huise哥 stated that as a trader, it is crucial to be familiar with the mechanisms of trading tools and platforms. In the current environment of "meme coins," many people focus only on the excitement of price surges and drops, neglecting the security risks of trading tools. Users should set up security alerts, such as pool drain or liquidation warnings, to keep risks in check.
Veronica emphasized a simple yet important principle: there is always a compromise between efficiently chasing profits and comprehensive security. Therefore, the key advice is to ensure fund isolation. If you find yourself anxious and unable to sleep due to oversized investment positions, frequently checking your phone, it likely indicates that your capital allocation has exceeded your risk tolerance.
What Practical On-Chain Security Query Tools Are Available?
Veronica recommends that users utilize built-in security tools in non-custodial wallets like SafePal, such as the function to regularly check authorizations—users can scan all their authorization records across multiple chains and revoke unnecessary authorizations with one click to reduce the risk of being exploited by hackers.
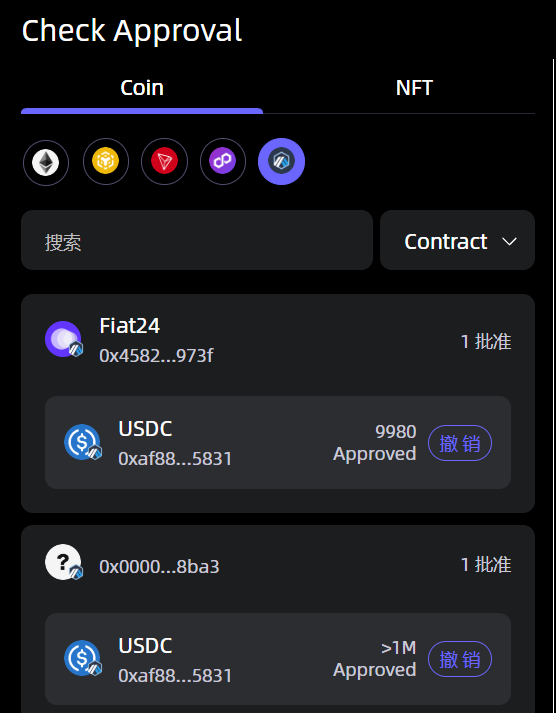
Image source: SafePal "Approval Manager" function
Additionally, scammers often disguise themselves as users' transfer addresses through small transfers to defraud funds. Currently, mainstream wallets like OKX Web3 Wallet and SafePal have added risk transaction interception services against "front-and-back attacks." Meanwhile, hardware wallets combined with passphrases (Passphrase) are a lesser-known but very practical feature, especially suitable for users with multiple trading accounts:
The passphrase acts as the 13th word, combined with the original 12 mnemonic words to generate a new wallet address. Even if someone obtains your mnemonic words, they cannot access your assets without the passphrase. This means users can create multiple wallet accounts in this way, ensuring security.
This method not only increases the security of private keys but also allows users to flexibly manage assets across multiple accounts, and the passphrase can exist only in the user's mind, further enhancing security.
Andy also emphasized that many times when users encounter security incidents, it may not only be due to risks inherent in the project but also related to the user's insufficient security habits. Even if users realize they hold a significant amount of crypto assets or are aware of the risks of investment trading, they often expose their assets to danger due to bad habits.
Users are advised to maintain a mindset and habits of security isolation, such as storing large assets in cold wallets that are only used for interaction and cannot directly transfer funds. At the same time, using a dedicated phone (like an iPhone) to manage crypto assets, only using it for cryptocurrency trading or private key management, and not installing other unrelated software or engaging in other activities on this device can significantly reduce the risk of private key leakage.
Conclusion
The DEXX security incident reveals the core dilemma in the field of on-chain trading tools: how to find a balance between convenience and security?
While pursuing efficient trading and user experience, the platform's security design cannot be sacrificed. Whether it is the centralized storage of private keys or the lack of memory-level protective technology shortcomings, both expose user assets to high risks.
"There is always a compromise between high returns and absolute security." For investors, understanding the risk logic behind trading tools and cultivating good security habits is the foundation for navigating the on-chain "dark forest." In this decentralized and uncertain ecosystem, only by controlling one's private keys can one truly control their assets and promote the healthier development of the entire on-chain ecosystem.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




