
Author: danny
I have been thinking these past few days, is it possible that the recent public relations battle involving exchanges was orchestrated by a team from the non-Chinese (APAC) circles?!
Many times, it is not that you did something wrong, but rather that you did many things right, and for that you are sentenced to "guilt for possessing a treasure." Or perhaps, you did many things right, but suddenly did n things wrong, and you are no longer the person you used to be? Does it feel like you can do a hundred good deeds, but in the end, one bad deed ruins your innocence?
Introduction
In Peter Thiel's book "Zero to One," there is a point made that businesses worth a billion in market value will eventually involve politics. The subtext is that when the stakes are high enough, there is always a need to seek a "protection umbrella," to put it bluntly, it means paying a protection fee. This is even more true in the crypto industry, where every exchange is a money printing machine, making those outside the industry itch.
Public relations battles are an important part of business warfare and an extension of political lobbying.
In the commercial sector, "black public relations" activities aim to manipulate information flow and public opinion to achieve strategic intentions such as damaging competitors' brand reputations, undermining their core product market expectations, and interfering with significant business decisions (like financing, IPO listings, annual new product releases).
By destroying an opponent's social trust foundation, the attackers can seizing abnormal market shares or force targeted companies to compromise under pressure, thereby seeking excessive economic benefits or making the opponent yield.
Reading Guide
The first three chapters are the theoretical foundation, discussing why so many "people" are needed in black public relations?
The fourth chapter discusses whether Binance is currently under attack from "black public relations"?
The fifth and sixth chapters attempt to speculate on the footprints of the puppeteers?
1. Theoretical and Psychological Foundations Behind "Black Public Relations"
The reason "black public relations" can repeatedly and easily tear apart the reputation defenses of a mature enterprise and incite large-scale public opinion ferment lies deeply in its exploitation of human group psychology weaknesses and information discrepancies, weaponizing them. Tactics such as "water armies" and "occupying public opinion" of black public relations are based on the following three classic psychological foundations.
1. Digital "Crowds" — Dumbing down the masses through aggregation
Gustave Le Bon's classic "The Crowd: A Study of the Popular Mind" points out that groups of people exhibit entirely different psychological characteristics:
De-individualization: When people gather, "the individual feels an overwhelming force." This sense of power liberates the individual from the moral constraints and sense of responsibility in real life. Cyber black public relations exploit this by encouraging netizens to engage in abuse, doxxing, and moral judgment.
Intellectual degradation: No matter how rational or elite an individual is in reality, once integrated into a group, their intellectual level will significantly drop, becoming a slave to instincts and emotions. The copywriting design of black public relations often avoids complex logical arguments, instead opting for short, powerful, and inflammatory slogans (like "the ugly face of capitalists" and "the culprit of 1011"), directly appealing to the group's primal instincts.
- 2. The Reverse Operation of Agenda-Setting Function and Coercive Intervention — Controlling what the public sees?
The "agenda-setting" theory suggests that while mass media may not directly determine how people view a specific event (i.e., "how to think"), it can effectively sway what facts and opinions people focus on (i.e., "what to think") by providing information and arranging the frequency of exposure to related topics.
Attackers flood the platforms, massively pushing for public attention towards a highly controversial, inflammatory, or panic-inducing negative agenda. This agenda is often packaged as significant social events related to public safety, core consumer rights, or business ethics. Once this agenda is successfully implanted in the public’s vision, the public’s attention will be directed within this negative framework, even if the company subsequently presents concrete evidence proving the incident is completely fabricated, the public's cognitive energy has already been extensively consumed questioning, suspicion, and verification.
- 3. "Spiral of Silence" and Systematic Fabrication of False Consensus — Controlling public participation?
The "spiral of silence" theory proposed in 1972 states that society will use isolation to threaten those who disagree with the majority; hence this "fear" leads individuals to constantly assess the public opinion climate and ultimately conform to the dominant narrative.
When "black public relations" organizations register hundreds of new accounts and launch a barrage of malicious comments against the target company, they are effectively manufacturing an "absolute advantage in public opinion" in cyberspace. One can only imagine what it feels like for ordinary people logging onto a platform to be instantly surrounded by a torrent of negative accusations, abuses, and so-called "concrete evidence"?
In such an extremely oppressive and hostile artificial public opinion pressure environment, those few who maintain an objective, neutral stance or attempt to defend the company will often choose to avoid expressing their diverging opinion to prevent themselves from facing group moral judgment, online violence, or social isolation (or political correctness), thus descending into silence.
In summary, this is why one of the core tasks of black public relations is to control the public opinion output scenarios and output frequency (number of people), because a group of people together will dumb each other down, and once dumbed down, they will be more easily influenced by external public opinion, and then, due to not wanting to be isolated, they will stop voicing opinions that oppose the mainstream narrative.
2. Strategic Objectives and Evolution Model of "Black Public Relations"
From the theoretical content of the first part, it is not difficult to see that the operation of "black public relations" is a set of meticulously calculated social engineering, and after years of evolution and iteration, has formed a highly structured, multi-node collaborative assembly line operation model. This model typically presents five standardized evolution stages from infiltration to eruption to disappearance.
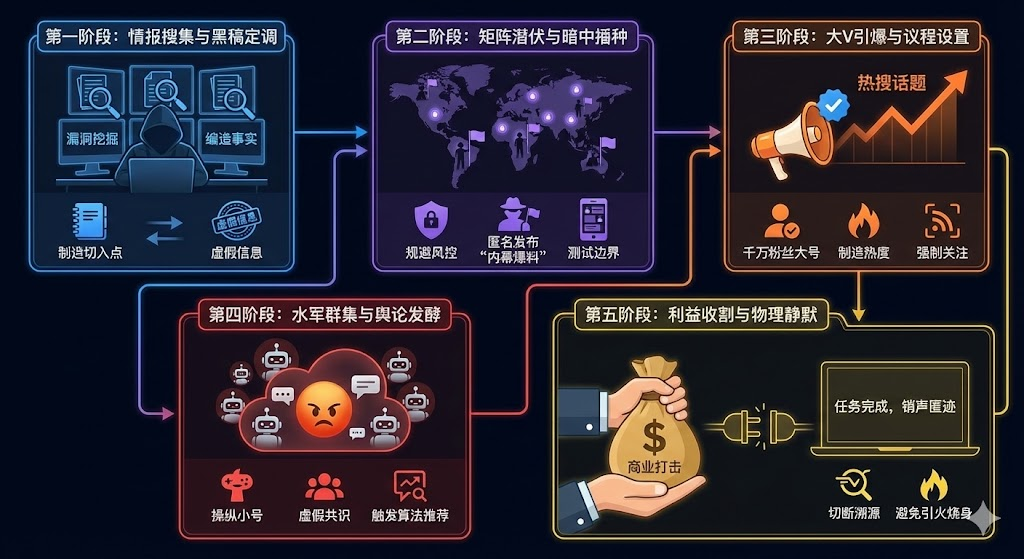
Phase 1: Intelligence Collection and Material Calibration
Deeply excavate product flaws, executive statement loopholes, or historical legacy issues of the target company. If there are no substantial problems, fabricate false facts out of thin air, or exaggerate and distort certain facts maliciously.
Phase 2: Matrix Infiltration and Secret Seeding
Utilize marginal self-media accounts, anonymous communities, or specific interest circles to publish "insider news" or suspenseful "exposés." At this stage, the information is in a latent period, primarily aimed at testing the tolerance and recommendation algorithm boundaries of different online platforms.
Phase 3: Influencer Detonation and Agenda-Setting
Engage accounts with millions or tens of millions of followers to participate, through retweets, comments, or posts featuring inflammatory soft articles, creating trending topic terms, rapidly elevating topic heat, and forcing public attention. Details involve utilizing "retweet/quote" and "hashtag" to quickly raise topic heat.
Phase 4: Gathering Water Armies and Public Opinion Fermentation
Manipulate a large number of newly registered accounts disguised as ordinary netizens to form a "mass attack" momentum in a short time. Utilize the concentrated interactions of the water army to trigger platform algorithm recommendations, forcibly pushing the negative topic to a climax across the internet, inciting real netizens to follow along and panic ("the crowd").
Phase 5: Profit Harvesting and Physical Silence
After the target company's reputation is damaged, stock price fluctuates, or sales decline, the attacking matrix will quickly deactivate large numbers of accounts or transition into a long-term silence state to cut off the technical traceability from judicial authorities to the company (this part is very important), while black market institutions complete the settlement of tail payments.
Why cut connections? Because this is a criminal act, recorded in criminal law. Therefore, to prevent being traced, execution teams generally adopt relatively discreet communication and payment methods. Digital currency payments have thus become a commonly used payment method in the industry. (This part will be examined later)
3. Common Characteristics and Identification Traits of "Black Public Relations"
This article summarizes several identification dimensions, and readers can establish a cross-identification matrix by themselves:

4. Is Binance in the Vortex of Black Public Relations?
4.1 "Zero Hour Action" Phenomenon: Are all users posting at the same time?
By analyzing the timestamps of the massive negative tweets on the x platform, we discovered an abnormal synchronization phenomenon known as "Zero Hour Action."
At specific time points (often during low market liquidity weekends or late nights in Asia), hundreds of independent accounts will simultaneously post negative content targeting Binance within seconds. These posts often contain the same keywords (such as "Insolvent," "Withdraw," "Run"), and even the use of punctuation and emojis is completely consistent.
This is a typical characteristic of a script-driven bot network, using the same set of materials, phrases, and hashtags to create the illusion that "the entire network is discussing Binance's bankruptcy/restriction on withdrawals/fleeing."
4.2 Account Matrix's "Trojan Horse" Strategy
A large number of accounts' IDs and nicknames adopt a uniform naming format, such as "BNB" suffix plus Chinese pinyin names (e.g., "Li_BNB," "Zhang_BNB"), and deliberately emphasize their identity as "old users from the China region" in their profiles. This disguise aims to exploit the identity symbols of Binance's early user base, creating a stark narrative of "the most loyal users are turning against" that is highly provocative for general community users.
These accounts were mostly silent during the real market crash in October 2025, and at that time, were even promoting competing projects like Solana or Hyperliquid. However, at the end of January 2026, they suddenly all "awoke," deleted previous content promoting competing products, and transformed into accounts focused solely on attacking Binance. This "usually lying low, activating in wartime" operation model is typical of zombie network tactics.
For this reason, cz has also written an article: https://x.com/cz_binance/status/2018949826994401464?s=20
4.3 Material Homogenization Phenomenon
The industrial traces in the content production process are equally apparent. A large number of circulated so-called "internal chat logs" and "lawyer letters" are AI-generated.
Different accounts posting screenshots of "withdrawing from Binance," "lawyer letters," or "account closures" show completely identical image resolution, cropping ratios, displayed times, and even battery percentage indications on phones. This implies that these so-called "real user feedbacks" are actually standardized promotional materials distributed from the same database.
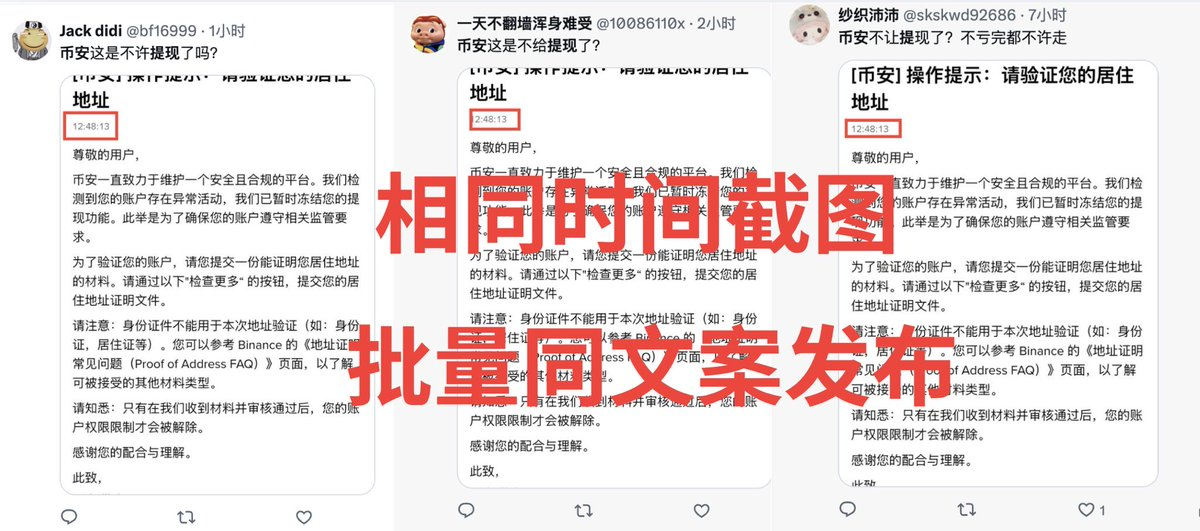
Example: https://x.com/moonkimbinance/status/2022123609343635497?s=20
4.4 Attackers' Identification Homogenization Phenomenon
Someone collected 92 accounts denouncing Binance on x and conducted data analysis on their published content, times, account histories, and activity levels (likes/retweets), ultimately concluding that as many as 71 accounts belong to high-risk accounts (bot accounts).
Reference:
https://x.com/Openai_study/status/2020873564388462982
https://openai.study/html/report_en.html
In conclusion, we do not rule out that some of the tweets' contents indeed come from real users, or that some accounts wish to seize opportunities for exposure, but considering the characteristics of "black public relations" in Chapter 3, it is evident that Binance is likely currently suffering different degrees of attacks from various aspects of black public relations operations. Even if it is not being attacked in an organized manner, many attacks of false information and amplifications of unfavorable news can be seen (for example, news about withdrawals and restrictions on withdrawals are prevalent, why is today so lively?).
5. Anatomy of the Industry Chain: Structure and Tools
Modern black public relations have departed from workshop-style operations, forming a clearly divided, explicitly priced underground industrial system.
Upstream (Financier):
Typically competitors or counterparties, who commission third parties through implicit instructions.
Midstream (MCN/PR Companies):
Core operators. Hoarding a large number of KOL resources, providing "hot search resource packages," responsible for transforming the financier's intentions into provocative narrative frameworks, and devising attack rhythms. (Formulating strategic objectives and phased implementation plans for "black public relations").
Downstream (Execution Level):
Silicon-based water armies: Utilizing group control software (one computer controls hundreds of phones) to operate zombie accounts, responsible for boosting metrics, likes, creating foundational heat.
Carbon-based water armies: Real individuals recruited through "part-time groups," using secret codes (such as "S egg," "fish pond") to take orders. They are responsible for posting emotionally charged comments, writing "recommendations/warnings" notes/tweets/experiences/analyses to launch attacks. (Example: https://x.com/moonkimbinance/status/2022123609343635497?s=20)
6. Pursuit: Who is Behind This?
The most exciting part is here, let’s speculate who the puppeteers are!
We cannot know the origins of the several "flag bearers" among the big influencers and the operations behind them; they could be spontaneous or working with agencies, but from the theories, phases, industry chain analysis, and means discussed above, we know that to perform this black public relations act well, aside from a leading star and head sheep, a group of "silicon-based water armies" is needed to stir up public opinion emotion. It is well-known that the algorithm of x has been changing, so the opponent might not be able to maintain or mass-produce such water armies over a long period, which means they need suppliers of water armies.
Therefore, we decided to start from the "supply chain" — the sources of water armies (non-influencer accounts).
It is known that the 34 high-risk x accounts mentioned in the OpenAi report are all bot accounts, and should be available in the market as "services" that can be purchased. So based on conditions (custom comments, use of digital currency payments, etc.), we filtered out 7 SMM (Social Media Marketing) platforms that meet these conditions.
The service range is as follows, providing a few screenshots for everyone to "broaden their horizons."
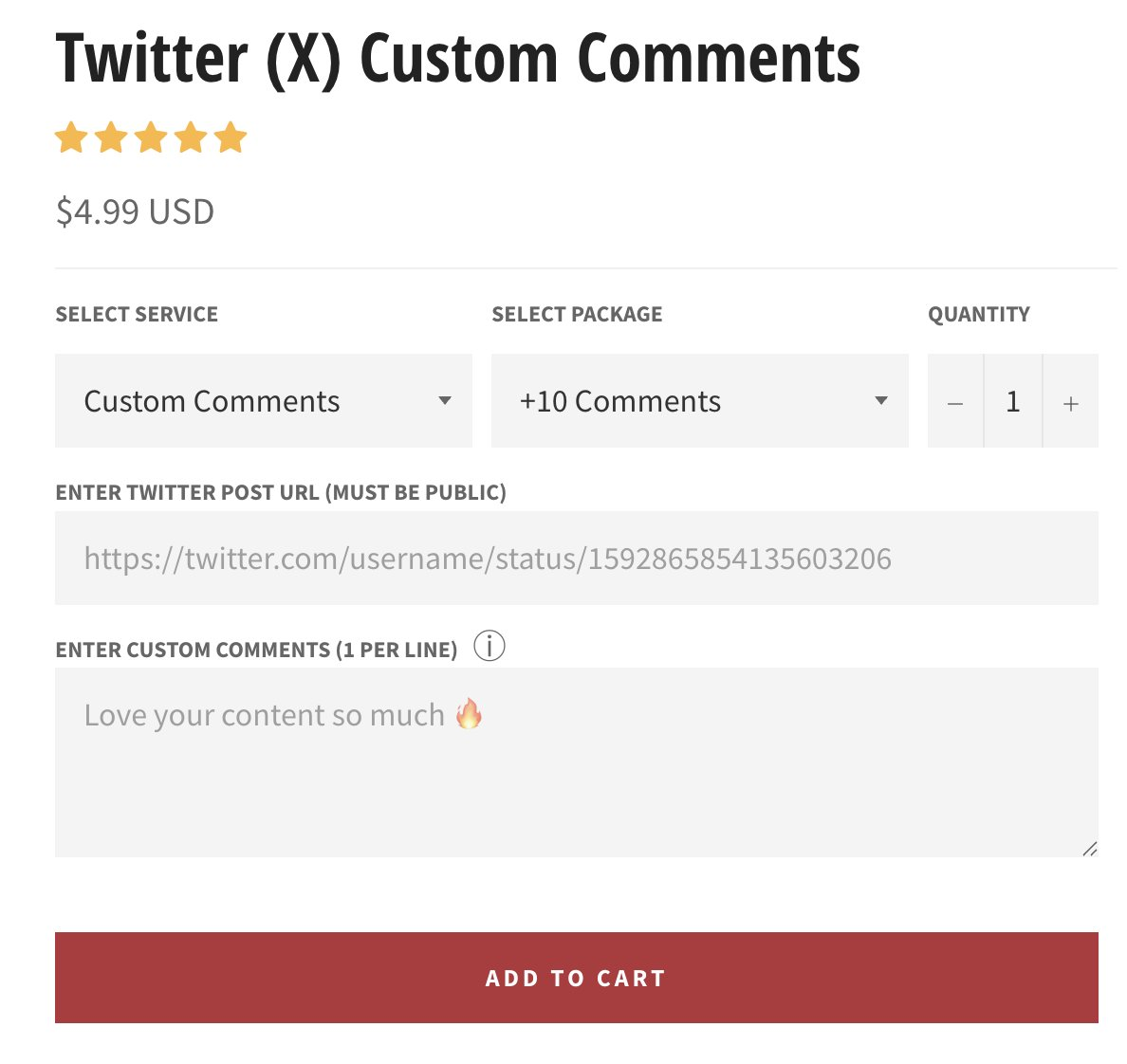
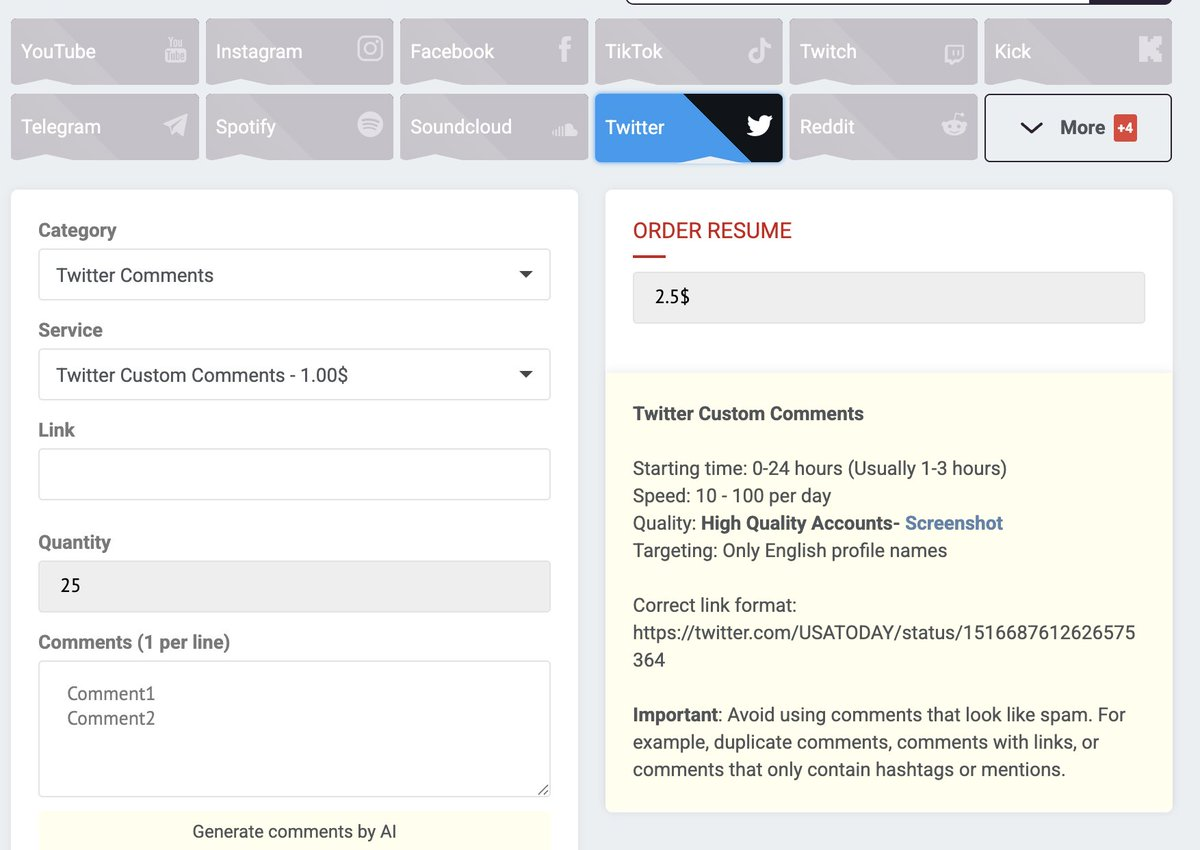
After that, we conducted tedious tests using AI and scripts, setting content-transfer-keywords-review to see if these bot accounts would engage in corresponding tweets, likes, retweets, and other behaviors. We have reasons to suspect that these bot accounts are "public goods," because shortly after, we began to see the bot accounts comment or retweet specific content according to the content guidelines, and some accounts even placed orders from different platforms, yet the same bot accounts could still output identical content.
After several rounds of testing, we roughly locked in several deployment platforms. Assuming this black public relations attack should be from experienced hands, they would ideally choose the platforms with higher "cost-performance" amongst many options. Through the wallet addresses used for recharging, we observed corresponding transaction records.
In our investigation within two weeks, we found a transaction record of 4999 u, and the exact transaction time was two weeks ago, on January 31st, precisely during the peak period when Binance was being mass-produced on x, and this platform does not have wealth management or trading functions. We suspect that this large recharge must have been used for something else.
![]()
Interestingly, this recharge was transferred out from Binance's hot wallet (can you believe it?!).
During our research, we found that during the peak period when OKX was attacked on the x platform, records of transfers from OKX's hot wallet to the deployment platform also appeared (Tron). In an instant, it felt like this matter might not be as predicted by outsiders.
![]()
This article, taking an attitude of better safe than sorry, will not disclose the corresponding wallet addresses here, nor will I share the collected information with the relevant interested parties.
No matter who you are or what your purpose is, I just hope we can stop this meaningless small action, be it Binance or OKX, whether it's 1011 or withdrawal restrictions. Exchanges certainly cannot wash their hands of responsibility, but they do not deserve to be completely abandoned or toppled by the industry. They are all pillars in the industry, not misusing user assets, and providing the best possible service from their own perspectives (even if the concepts may differ), and should not suffer a clear assault but be subjected to widespread condemnation.
For the Chinese CT to establish a foothold in the crypto market is not easy, especially since the West has always viewed the East as a "liquidity export" and covets the "vast and boundless" liquidity of the East (exchanges). Why must the pioneering industrial narrative always be transmitted from the West to the East, ultimately being paid for by the East?
It is time to change this order and rule.
But first, we must set aside our prejudices.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




